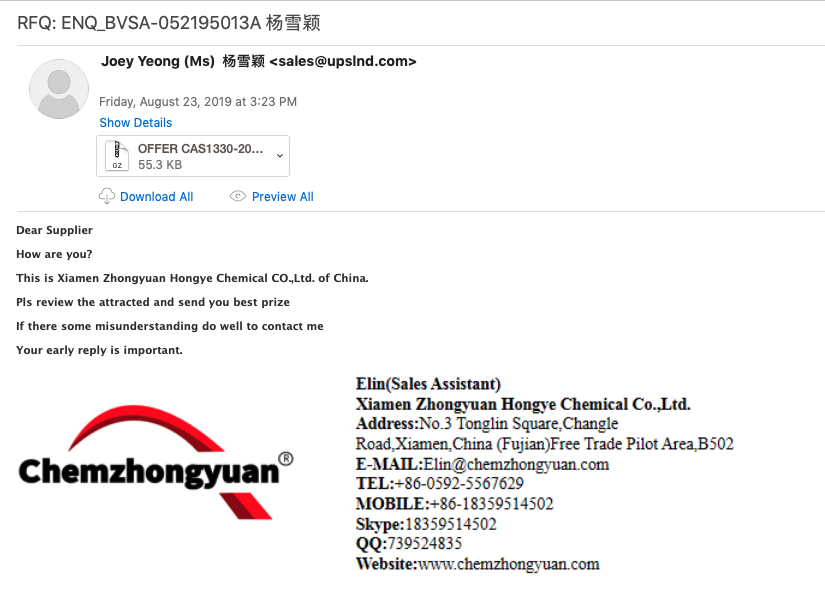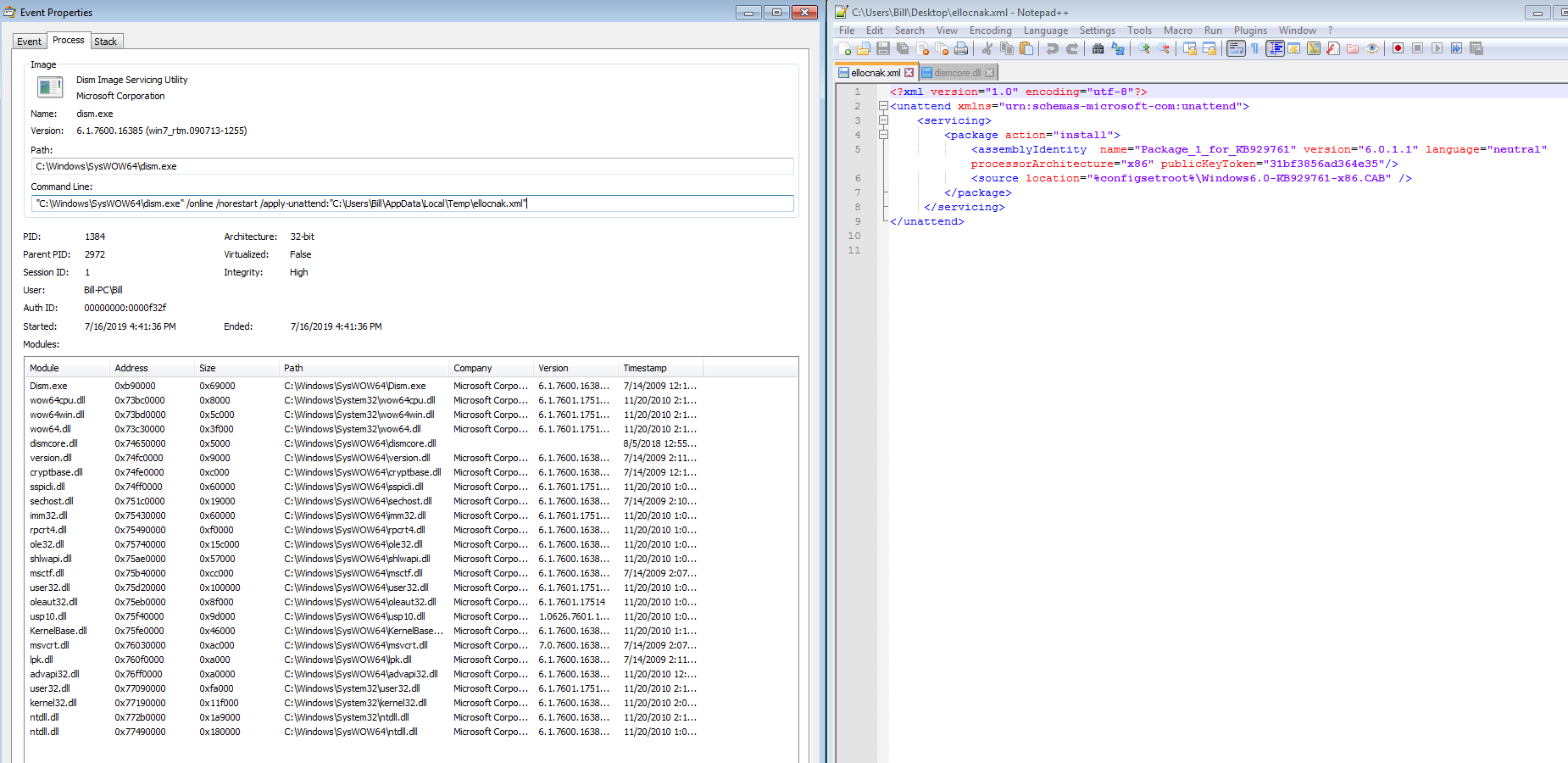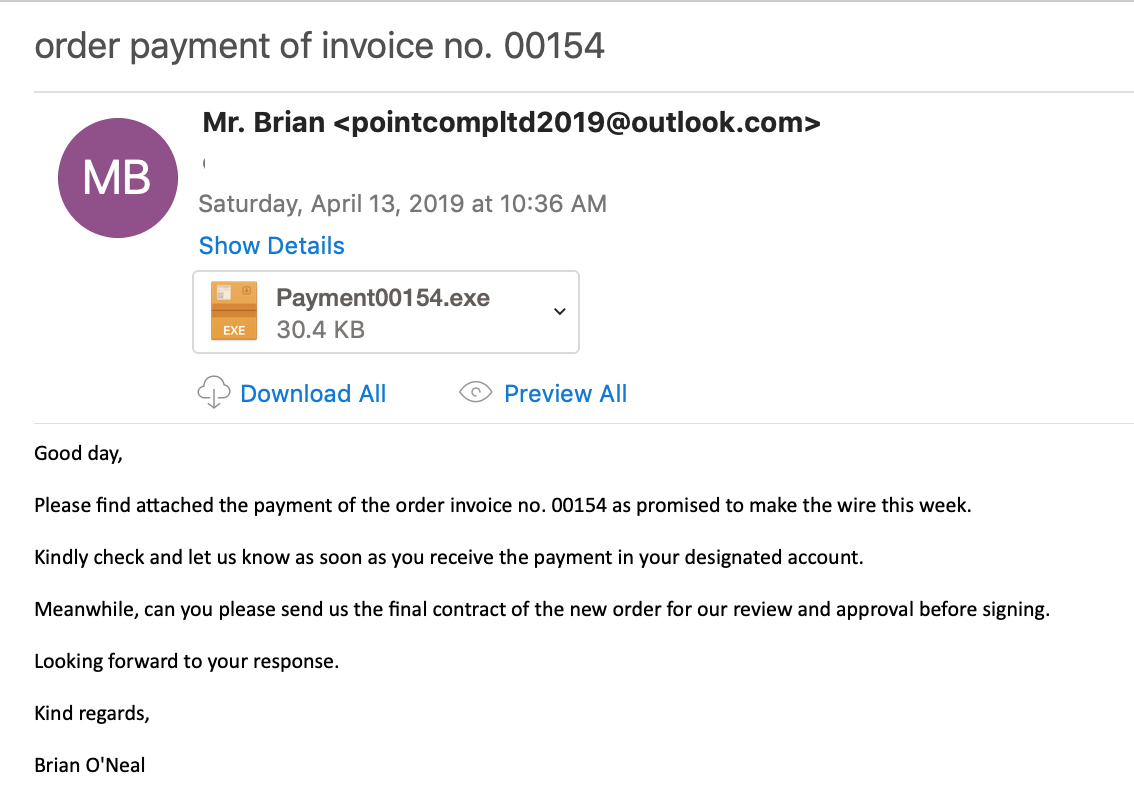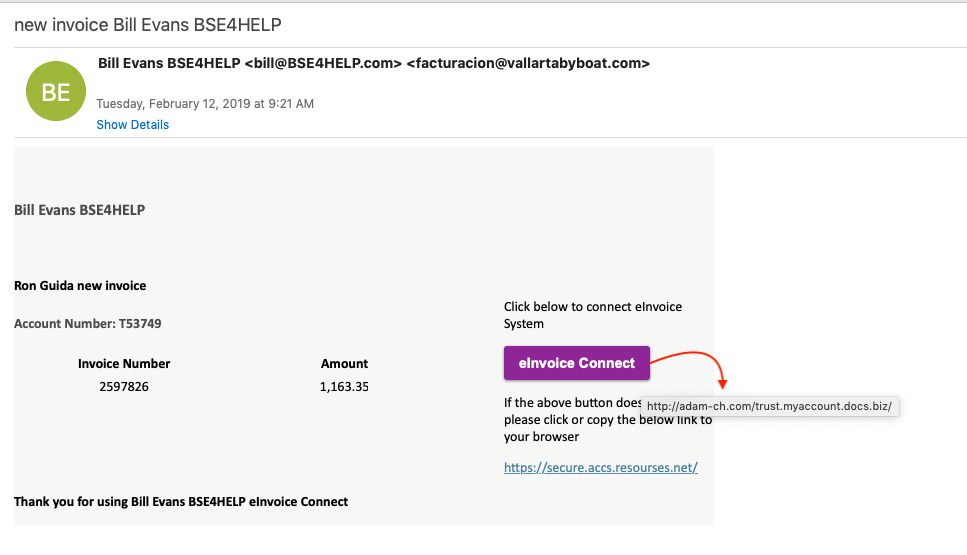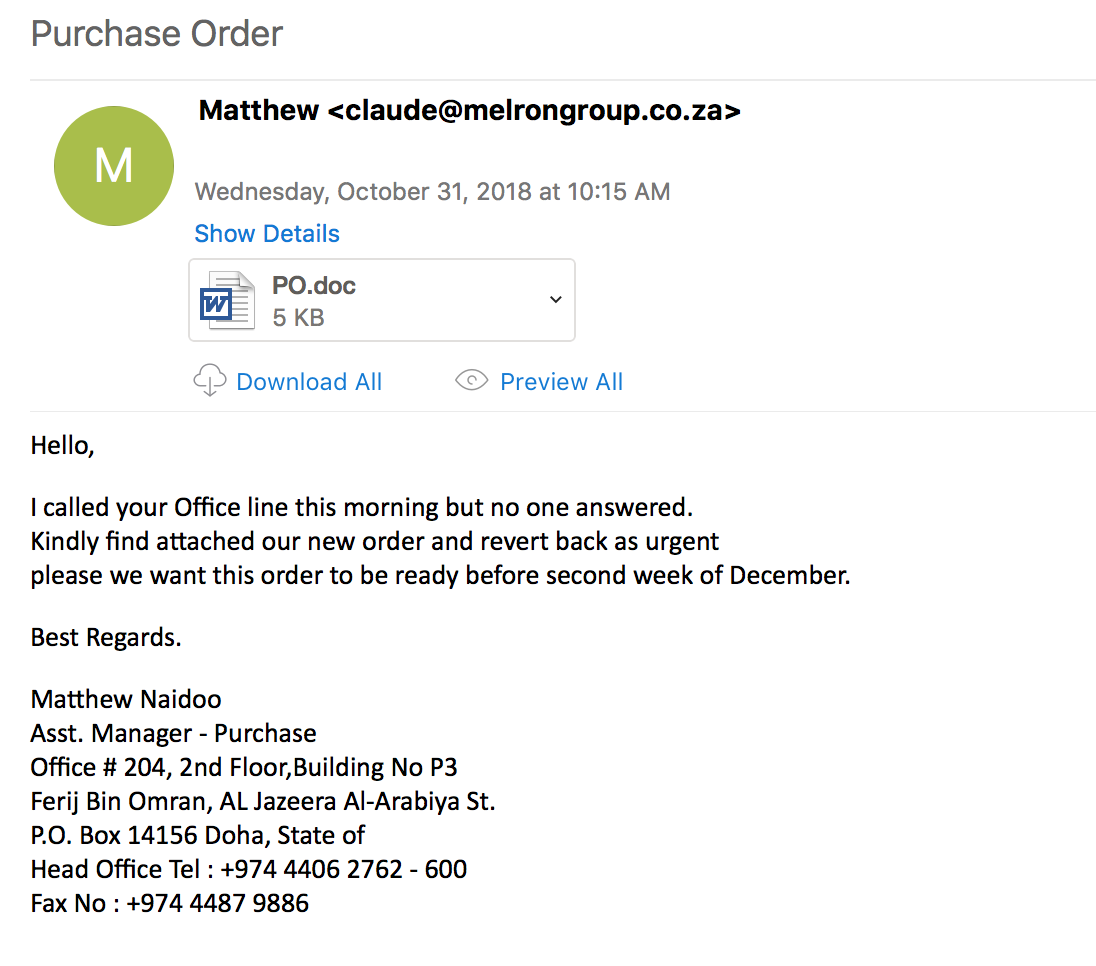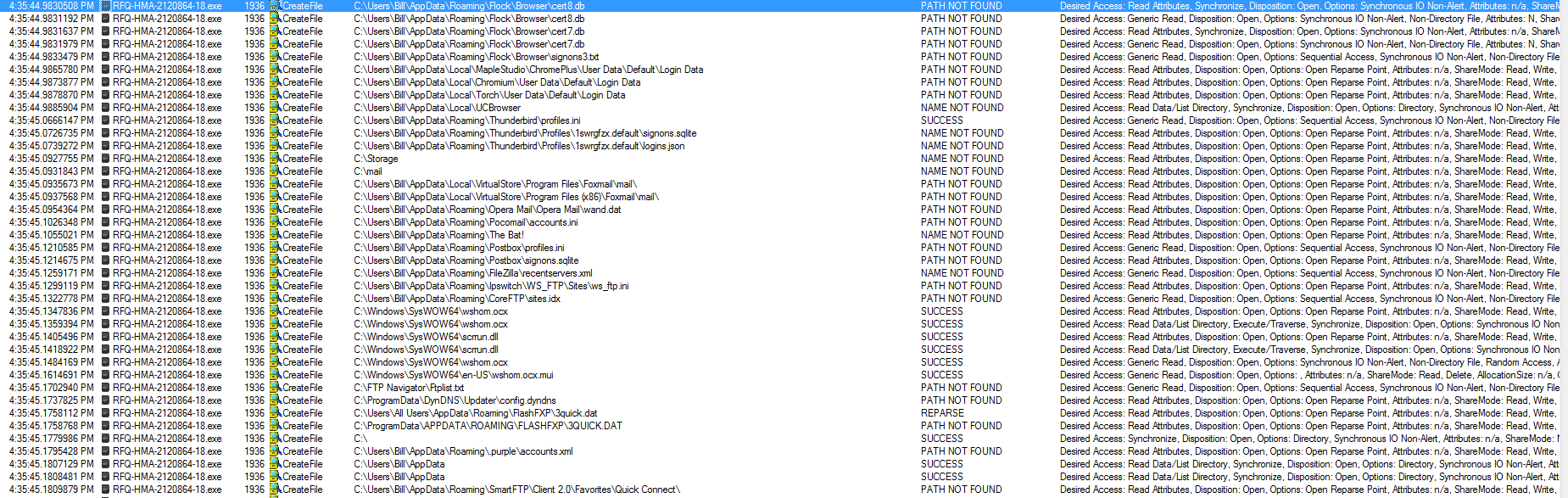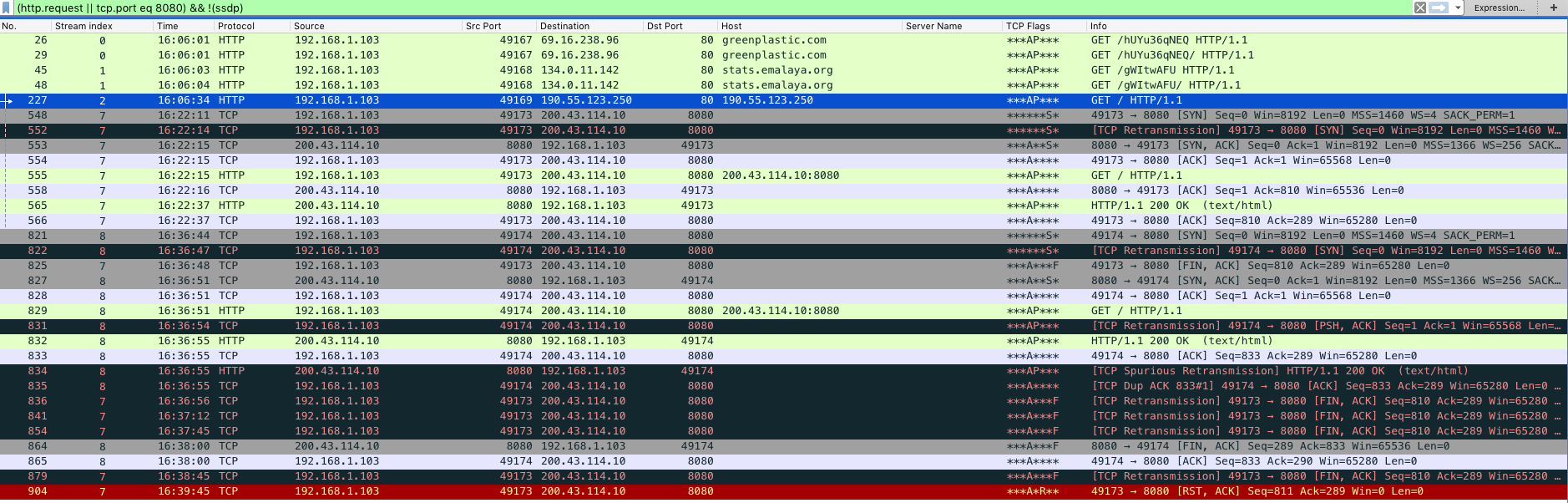
Just a quick post about some emotet malspam from this morning. Pretty standard from what I can tell. For the artifacts, ProcMon log, and PCAP, please see the repo here. IOC: ===== http://kcespolska.pl//Details/2019-01 69.16.238.96:80 / hxxp://greenplastic.com/hUYu36qNEQ 134.0.11.142:80 / hxxp://stats.emalaya.org/gWItwAFU hxxp://innio.biz/rg1n590 hxxp://kiot.coop/yzc2cJzANO hxxp://atkcgnew.evgeni7e.beget.tech/HkHe3fKTc 200.43.114.10:8080 TCP Artifacts: =========== File name: 190118-Untitled-1653.doc File size: 127KB File path: NA MD5 hash: 1ce19abf935240c42b5f2959861c3ccc Virustotal: http://www.virustotal.com/#/file/3553ff9236d640518f6293464d195c54e09923c8ff3778b6d396b269db26d221/detection Detection ratio: 12 / 57 First detected: 2019-01-18 14:51:05 Any.Run: http://app.any.run/tasks/c066703c-130e-4f78-bd1c-18c9f300cb98 File name: ipropwfp.exe File size: 148KB File path: C:\Users\%username%\AppData\Local\ipropwfp MD5 hash: 4ca746d87cf1b5f6135c9f99e7044b2d Virustotal: http://www.virustotal.com/#/file/8a60dc9876ad042a6c957db6414918f33b932aa1fa0bc56799100968d2a992ab/detection Detection ratio: 25 / 69 First detected: 2019-01-18 15:05:53 Any.Run: http://app.any.run/tasks/2b777d77-06bc-430d-85f9-4d4a7abea5c1 / http://app.any.run/tasks/2842a89d-1db7-4993-a2aa-c098311fcd26 / http://app.any.run/tasks/e21438cb-3261-4611-b071-abe0f20d0ca1
Continue reading