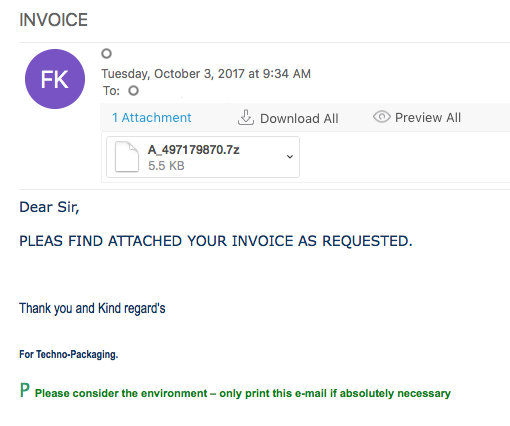
2018-02-16 Emotet Maldoc
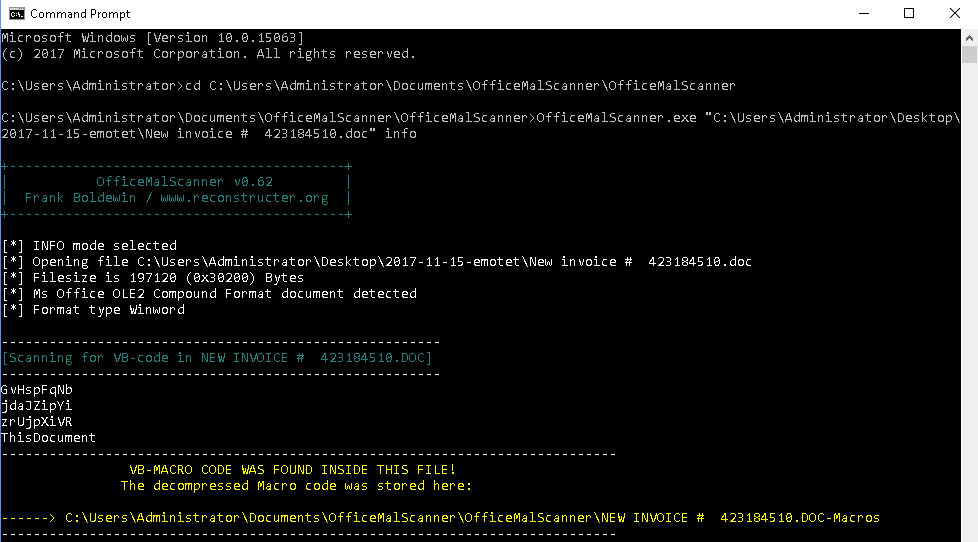
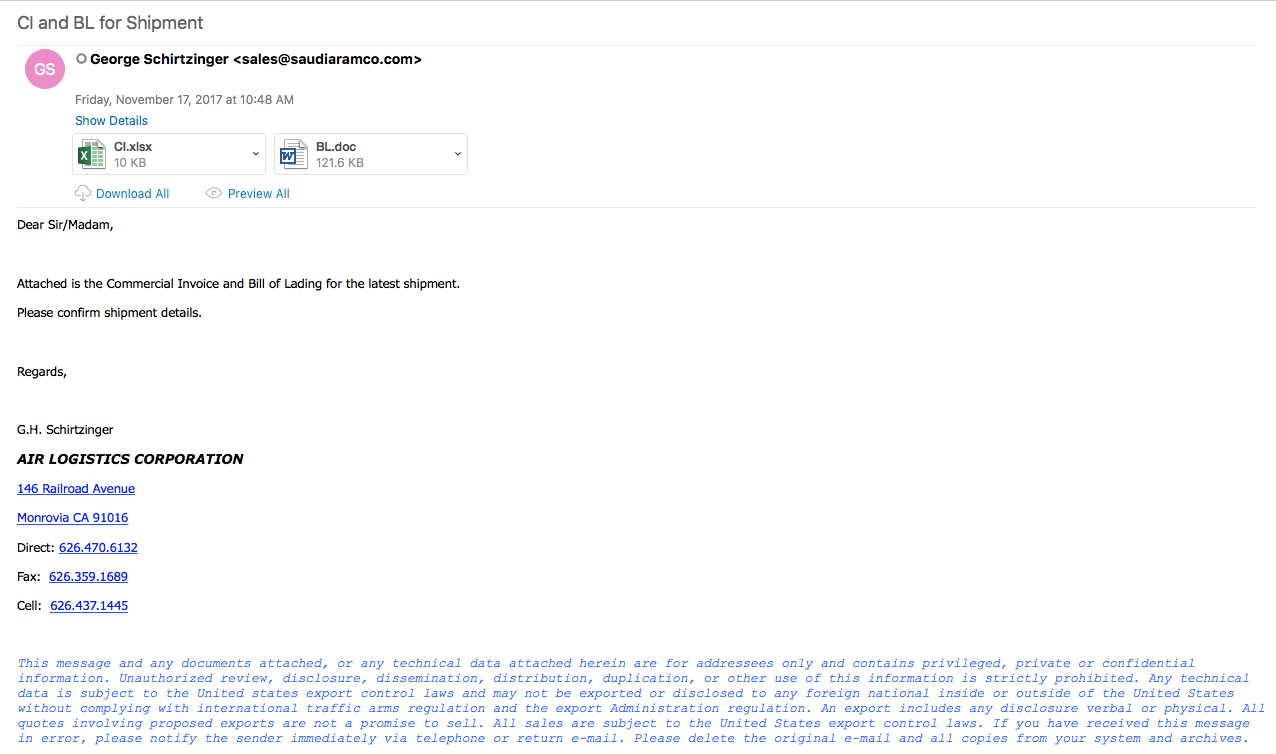
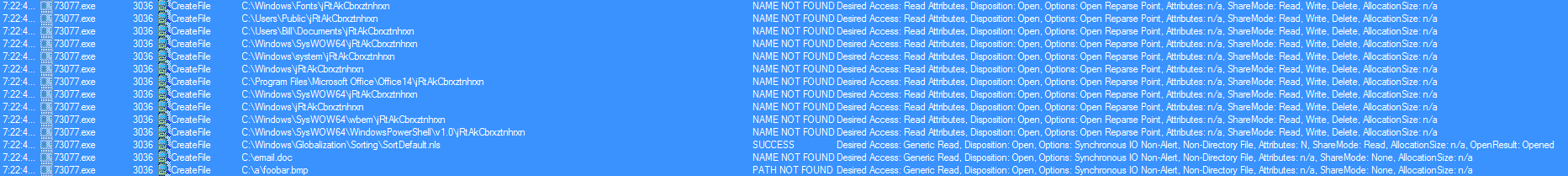
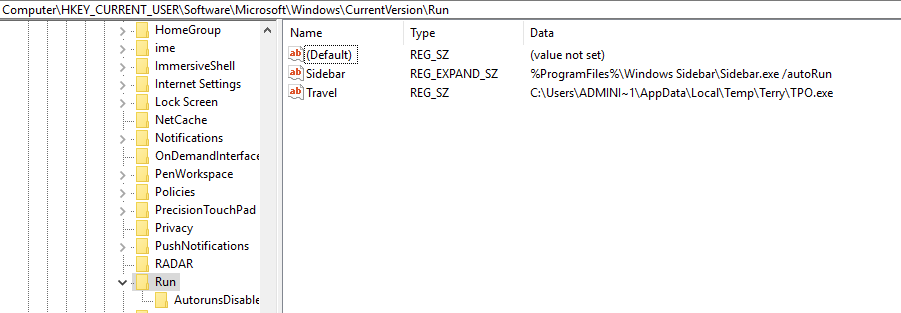
Here is a quick writeup for another Emotet maldoc that I saw. Unfortunately I did not get a copy of the email but it did have a link in it which lead to the maldoc. There were two things in this sample that I saw that were different: 1) no communications over TCP port 8080, and 2) the POST actually returned a status 200 and not the usual status 400. Outside of that, this was pretty much the same emotet that I have seen in the past. Nothing over how to walk through the script this time outside of a…