2022-05-13 Quick Remcos Deobfusction
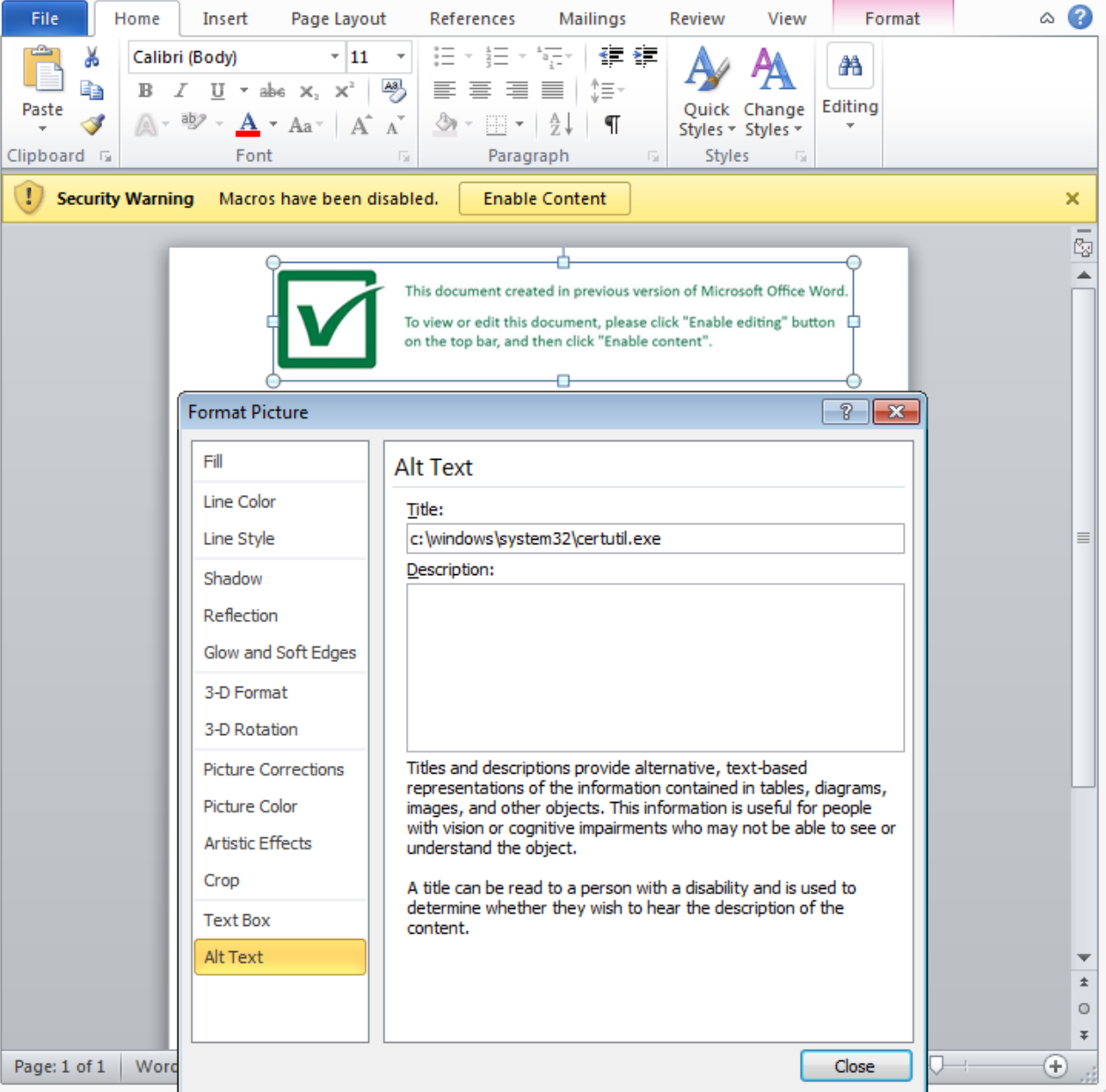
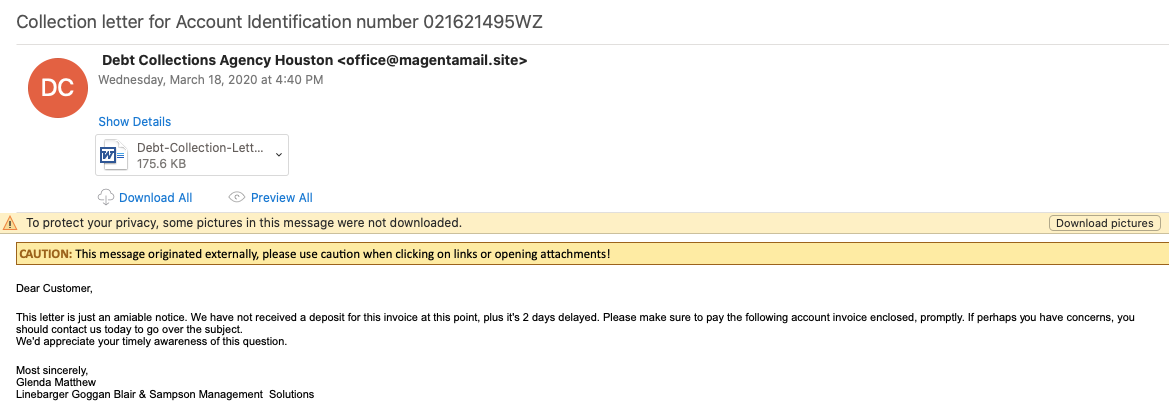
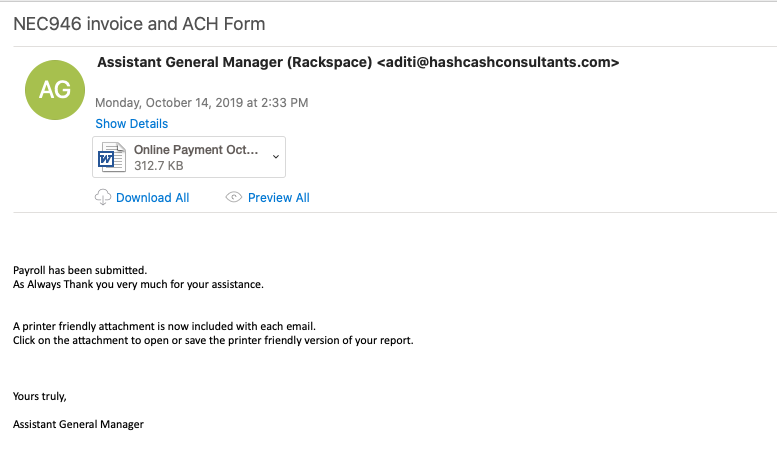
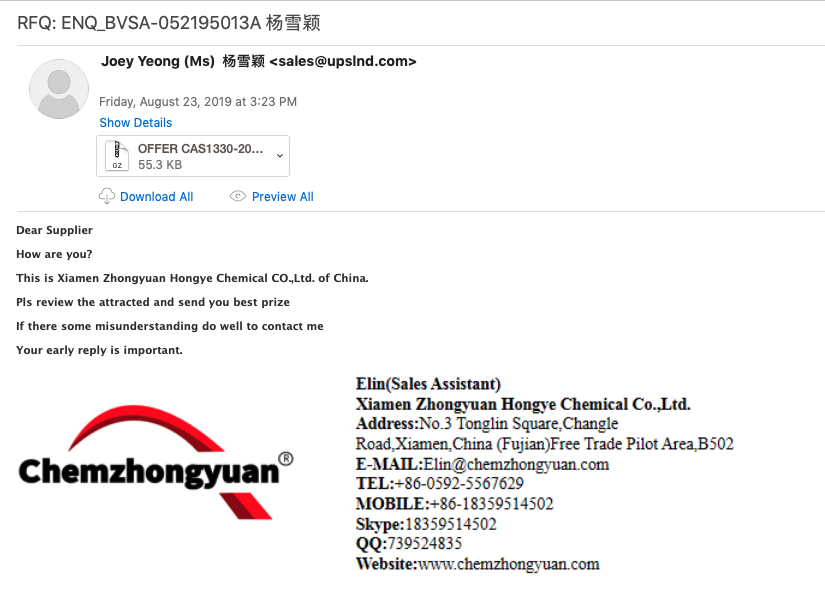
Summary ========= Decided that I would take a crack at trying to deobfuscate the VBScript that was in a sample of Remcos malspam since I haven’t been doing it for a long while. The VBScript can be found over at Any.Run inside a zip file (malspam attachment). I’ll do a post going over the analysis in the coming days since it seems pretty straight forward. The link to the scripts can be found at my Github. NOTE: Wherever there is a “&” it is meant to be just the & symbol. Analysis ========= The script is a LONG one and…