2024-10-12 Async RAT
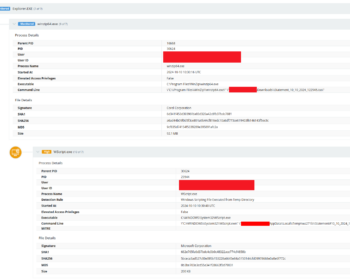
Intro ========= So much for keeping New Years resolutions and posting things. ¯\_(ツ)_/¯ With that out of the way let’s get into taking a look at our friend ASync RAT. As usual, the link to the artifacts from this can be found over at my Github here. **Note: Process Monitor and Wireshark were running at the same time that I was playing around with the “MenToffice” binary by itself and also running the WSF script. So the data logged are conflated in each tool’s saved logs (Process Monitor files and PCAPs).** Analysis ========== So this started as an alert for…