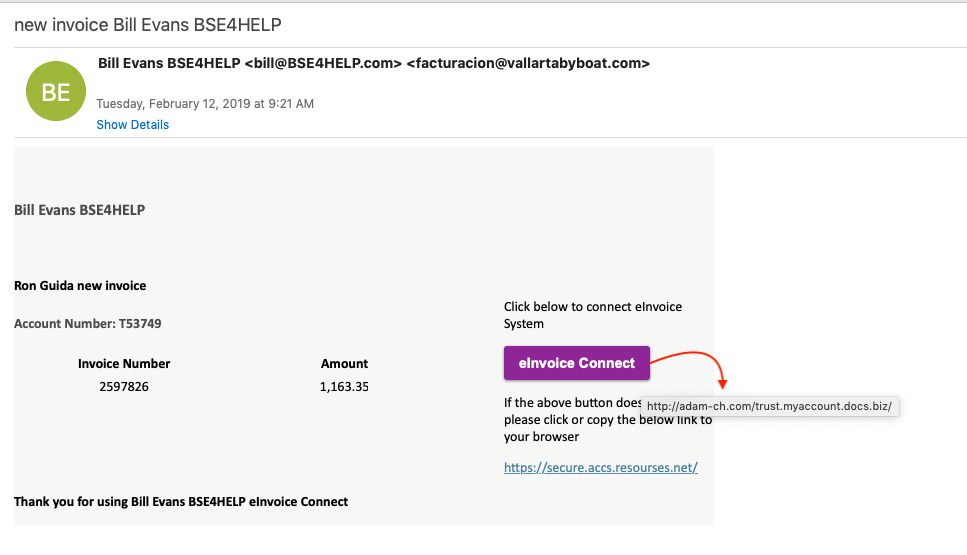
2022-02-13 Breaking out the WD40! First Stage Downloader For Remcos RAT
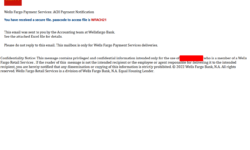
It has been a while since I have played with any malware or tried to RE a script of some sort. So here goes nothing… Shout out to David Ledbetter for the assist. Solid work as usual! This post will cover the downloader script from a Remcos maldoc that I was playing with from the beginning of the month. The email itself was your standard fare – a Wells Fargo phishing email that had an Excel XLSB attachment that was encrypted. The Excel XLSB can be found over at Any.Run or over at my Github here. A special shoutout to…