I came across this sample yesterday via my usual method – the email filters. The email is your pretty standard stuff acting as a proposal for an order. Once you open the zip file, there is an executable. From here, the fun began. For the artifacts/logs/PCAP from this analysis, please see my Github repo for this here.
IOCs:
=====
respainc.duckdns.org / 79.134.225.51:28 (TCP)
8.8.8.8:53 (TCP)
Artifacts:
==========
Microsoft.exe/Quotation.exe
a07a5a3100544aceeade42e743218e6a
http://www.virustotal.com/gui/file/a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee/detection
First Submission 2019-07-16 10:12:09
28/67 engines detected this file
Path: C:\Users%USERNAME%\AppData\Roaming | %TEMP%
dismcore.dll
6b906764a35508a7fd266cdd512e46b1
http://www.virustotal.com/gui/file/fc0c90044b94b080f307c16494369a0796ac1d4e74e7912ba79c15cca241801c/detection
First Submission 2018-10-24 20:23:05
51/70 engines detected this file
Path: %TEMP%
ellocnak.xml
427eb7374887305b72f5c552837c9036
http://www.virustotal.com/gui/file/b3f421780a49cbe680a317259d4df9ce1d0cdaca3020b4df0dc18cc01d68ccbb/detection
First Submission 2017-02-27 03:31:58
No engines detected this file
Path: %TEMP%
Munin Check:
============
Online Hash Checker for Virustotal and Other Services
Florian Roth – 0.13.0 April 2019
[+] Found results CSV from previous run: check-results_Desktop.csv
[+] Appending results to file: check-results_Desktop.csv
[ ] Processing .DS_Store …
[ ] Processing ellocnak.xml …
[ ] Processing dismcore.dll …
[ ] Processing Microsoft.exe …
[ ] Processing Quotation.exe …
[+] Processing 5 lines …
1 / 5 > Clean
HASH: d65165279105ca6773180500688df4bdc69a2c7b771752f0a46ef120b7fd8ec3 COMMENT: .DS_Store
TYPE: – FILENAMES: –
FIRST: – LAST: 2019-07-16 07:07:44 COMMENTS: 0 USERS: –
RESULT: 0 / 57
[!] Sample on ANY.RUN URL: http://any.run/report/d65165279105ca6773180500688df4bdc69a2c7b771752f0a46ef120b7fd8ec3
2 / 5 > Clean
HASH: b3f421780a49cbe680a317259d4df9ce1d0cdaca3020b4df0dc18cc01d68ccbb COMMENT: ellocnak.xml
TYPE: – FILENAMES: –
FIRST: – LAST: 2019-06-24 21:38:28 COMMENTS: 0 USERS: –
RESULT: 0 / 55
[!] Sample on ANY.RUN URL: http://any.run/report/b3f421780a49cbe680a317259d4df9ce1d0cdaca3020b4df0dc18cc01d68ccbb
3 / 5 > Malicious
HASH: fc0c90044b94b080f307c16494369a0796ac1d4e74e7912ba79c15cca241801c COMMENT: dismcore.dll
VIRUS: Microsoft: Trojan:Win32/CryptInject / Kaspersky: Trojan.Win32.Agentb.jiad / McAfee: Trojan-UACByPass.a / CrowdStrike: win/malicious_confidence_100% (W) / TrendMicro: Trojan.Win32.ANTIAV.AB / ESET-NOD32: Win32/AntiAV.NIZ / Symantec: Trojan Horse / F-Secure: Trojan.TR/RedCap.ghjpt / Sophos: Troj/AntiAV-P / GData: Win32.Trojan.Agent.Y9LRWZ
TYPE: – FILENAMES: –
FIRST: – LAST: 2019-06-24 21:37:51 COMMENTS: 0 USERS: –
RESULT: 51 / 70
[!] Sample on ANY.RUN URL: http://any.run/report/fc0c90044b94b080f307c16494369a0796ac1d4e74e7912ba79c15cca241801c
4 / 5 > Malicious
HASH: a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee COMMENT: Microsoft.exe
VIRUS: Microsoft: Trojan:Win32/Wacatac.B!ml / Kaspersky: UDS:DangerousObject.Multi.Generic / McAfee: Artemis!A07A5A310054 / CrowdStrike: win/malicious_confidence_80% (D) / ESET-NOD32: a variant of Win32/Kryptik.GUQJ / GData: Gen:Variant.Sinowal.1
TYPE: – FILENAMES: –
FIRST: – LAST: 2019-07-16 10:12:09 COMMENTS: 0 USERS: –
RESULT: 28 / 67
[!] Sample on ANY.RUN URL: http://any.run/report/a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee
5 / 5 > Malicious
HASH: a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee COMMENT: Quotation.exe
VIRUS: Microsoft: Trojan:Win32/Wacatac.B!ml / Kaspersky: UDS:DangerousObject.Multi.Generic / McAfee: Artemis!A07A5A310054 / CrowdStrike: win/malicious_confidence_80% (D) / ESET-NOD32: a variant of Win32/Kryptik.GUQJ / GData: Gen:Variant.Sinowal.1
TYPE: – FILENAMES: –
FIRST: – LAST: 2019-07-16 10:12:09 COMMENTS: 0 USERS: –
RESULT: 28 / 67
[!] Sample on ANY.RUN URL: http://any.run/report/a52f455f897f54af3e3d1505e686d391171d2f981ba7971b63cc491708b12fee
Machinae Check:
===============
prompt:~$ machinae 79.134.225.51
[.] Requesting http://www.ipvoid.com/ip-blacklist-check (POST)
[.] Requesting http://malc0de.com/database/index.php?search=79.134.225.51 (GET)
[.] Requesting http://abuseipdb.com/check/79.134.225.51 (GET)
[.] Requesting http://ransomwaretracker.abuse.ch/host/79.134.225.51 (GET)
[.] Requesting http://isc.sans.edu/api/ip/79.134.225.51 (GET)
[.] Requesting http://freegeoip.io/json/79.134.225.51 (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=79.134.225.51 (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/ip-address/report?ip=79.134.225.51&apikey=XXX (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=79.134.225.51 (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/ip/default.aspx?ip=79.134.225.51 (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/79.134.225.51/events/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/79.134.225.51/domains/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/79.134.225.51/urls/ (GET)
[.] Requesting http://www.threatcrowd.org/searchApi/v2/ip/report/?ip=79.134.225.51 (GET)
********************************************************************************
Information for 79.134.225.51
Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘6775′, ’79[.]134.224.0/19’, ‘2007-10-24’, ‘ripencc’, ‘CH’)
[-] Network Information: (’79[.]134.225.0/26′, ‘BASEL-HOSTING-225-0′, ’79[.]134.225.0 – 79[.]134.225.63’)
[-] Registration Info: (‘2016-04-17’, ‘2016-04-18’)
[-] Registration Locality: CH
[-] No IPVoid Results
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No RansomwareTracker Results
[-] No SANS Results
[!] Error from freegeoip.io: 503 Server Error: Service Temporarily Unavailable for url: http://freegeoip.io/json/79.134.225.51
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2019-07-12’, ‘evapimp[.]dynu[.]net’)
[-] pDNS data from VirusTotal: (‘2019-07-09’, ‘konto2[.]ddnsking[.]com’)
[-] pDNS data from VirusTotal: (‘2019-07-16’, ‘respainc[.]duckdns[.]org’)
[-] pDNS malicious URLs from VirusTotal: (‘2019-07-09’, ‘(hXXp)://konto2[.]ddnsking[.]com/’)
[-] pDNS malicious URLs from VirusTotal: (‘2019-07-09’, ‘(hXXps)://konto2[.]ddnsking[.]com/’)
[-] pDNS malicious URLs from VirusTotal: (‘2019-07-04’, ‘hXXps://79[.]134.225.51/’)
[-] pDNS malicious URLs from VirusTotal: (‘2019-07-03’, ‘hXXp://79[.]134.225.51/’)
[-] pDNS malicious URLs from VirusTotal: (‘2019-07-03’, ‘(hXXp)://respainc[.]duckdns[.]org/’)
[+] Reputation Authority Results
[-] Reputation Authority Score: 85/100
[-] No McAfee Threat Results
[!] Error from Cymon.io IP Events: HTTPSConnectionPool(host=’cymon.io’, port=443): Max retries exceeded with url: /api/nexus/v1/ip/79.134.225.51/events/ (Caused by NewConnectionError(‘: Failed to establish a new connection: [Errno 8] nodename nor servname provided, or not known’))
[!] Error from Cymon.io IP Domains: HTTPSConnectionPool(host=’cymon.io’, port=443): Max retries exceeded with url: /api/nexus/v1/ip/79.134.225.51/domains/ (Caused by NewConnectionError(‘: Failed to establish a new connection: [Errno 8] nodename nor servname provided, or not known’))
[!] Error from Cymon.io IP URLs: HTTPSConnectionPool(host=’cymon.io’, port=443): Max retries exceeded with url: /api/nexus/v1/ip/79.134.225.51/urls/ (Caused by NewConnectionError(‘: Failed to establish a new connection: [Errno 8] nodename nor servname provided, or not known’))
[-] No ThreatCrowd IP Report Results
prompt:~$ machinae respainc.duckdns.org
[.] Requesting http://www.urlvoid.com/scan/respainc.duckdns.org (GET)
[.] Requesting http://www.toolsvoid.com/unshorten-url (POST)
[.] Requesting http://malc0de.com/database/index.php?search=respainc.duckdns.org (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=respainc.duckdns.org (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/domain/report?domain=respainc.duckdns.org&apikey=XXX (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=respainc.duckdns.org (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/domain/default.aspx?domain=respainc.duckdns.org (GET)
[.] Requesting http://cymon.io/api/nexus/v1/domain/respainc.duckdns.org (GET)
********************************************************************************
Information for respainc.duckdns.org
Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2019-03-13’, ‘173[.]46.85.71’)
[-] pDNS data from VirusTotal: (‘2019-05-11’, ‘178[.]239.21.188’)
[-] pDNS data from VirusTotal: (‘2019-05-09’, ‘185[.]165.153.137’)
[-] pDNS data from VirusTotal: (‘2019-06-27’, ‘185[.]244.29.52’)
[-] pDNS data from VirusTotal: (‘2019-01-21’, ‘185[.]244.30.121’)
[-] pDNS data from VirusTotal: (‘2018-12-07’, ‘213[.]183.58.27’)
[-] pDNS data from VirusTotal: (‘2019-07-16′, ’79[.]134.225.51’)
[-] pDNS data from VirusTotal: (‘2019-05-09′, ’91[.]192.100.14’)
[-] pDNS data from VirusTotal: (‘2019-05-21′, ’91[.]192.100.25’)
[-] pDNS data from VirusTotal: (‘2019-05-28′, ’91[.]193.75.93′)
[+] Reputation Authority Results
[-] Reputation Authority Score: 85/100
[+] McAfee Threat Results
[-] McAfee Web Risk: Minimal
[-] McAfee Web Category: Personal Pages,Internet Services
[-] McAfee Last Seen: 2019-07-16
[!] Error from Cymon.io Domain Lookup: HTTPSConnectionPool(host=’cymon.io’, port=443): Max retries exceeded with url: /api/nexus/v1/domain/respainc.duckdns.org (Caused by NewConnectionError(‘: Failed to establish a new connection: [Errno 8] nodename nor servname provided, or not known’))
Analysis:
=========
The binary acted pretty much the same way as it did within the Any.Run application as evidenced in the screen shots below.
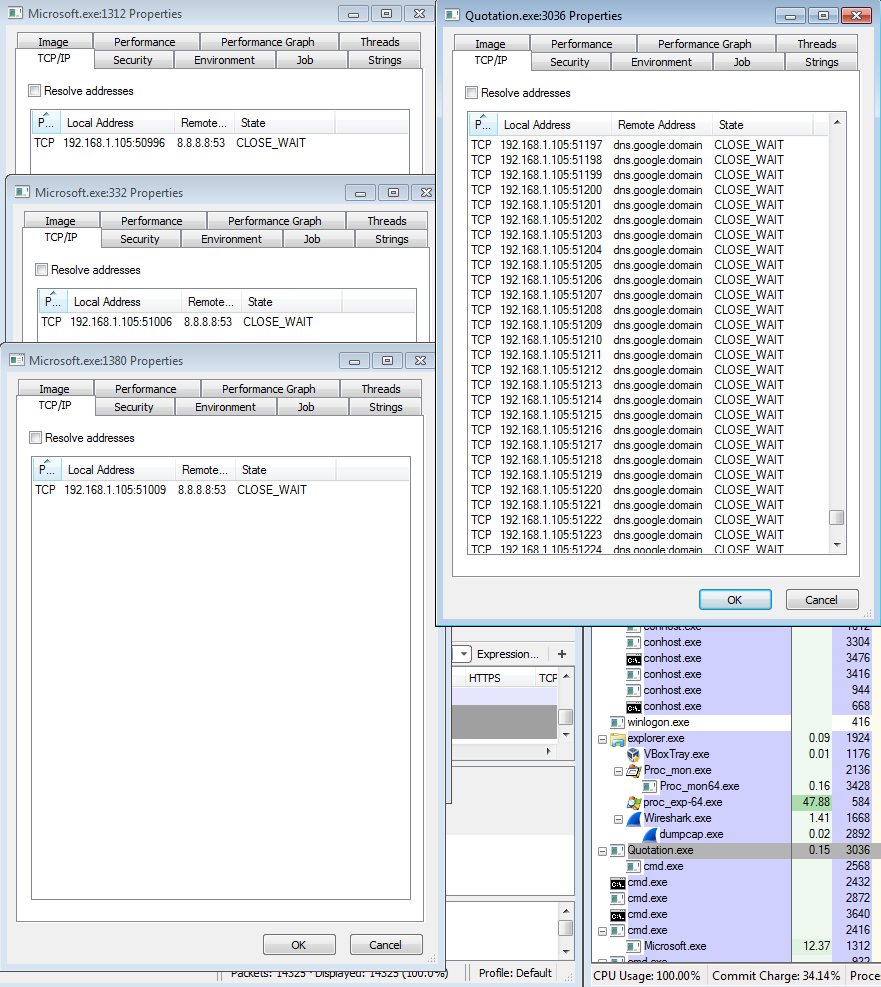
The interesting thing with this sample was the fact that it took a couple of minutes to actually get up and running. As you can see in the PCAP, it starts off making calls to 8.8.8.8 over port 53 TCP. Looking at these packets, I was not able to see any patterns or anything that stood out to myself. At this time I am not sure why it was making these calls, unless it was a time-bomb of sorts for automated malware analysis systems. It was not until about 2 minutes later that we get our first call to 79.134.225.51 over port 28 TCP. From the looks of it, this traffic is encrypted or encoded.
We can also see based on the stats from Wireshark how this malware works from the network perspective and that it does not callout to any other IP addresses.
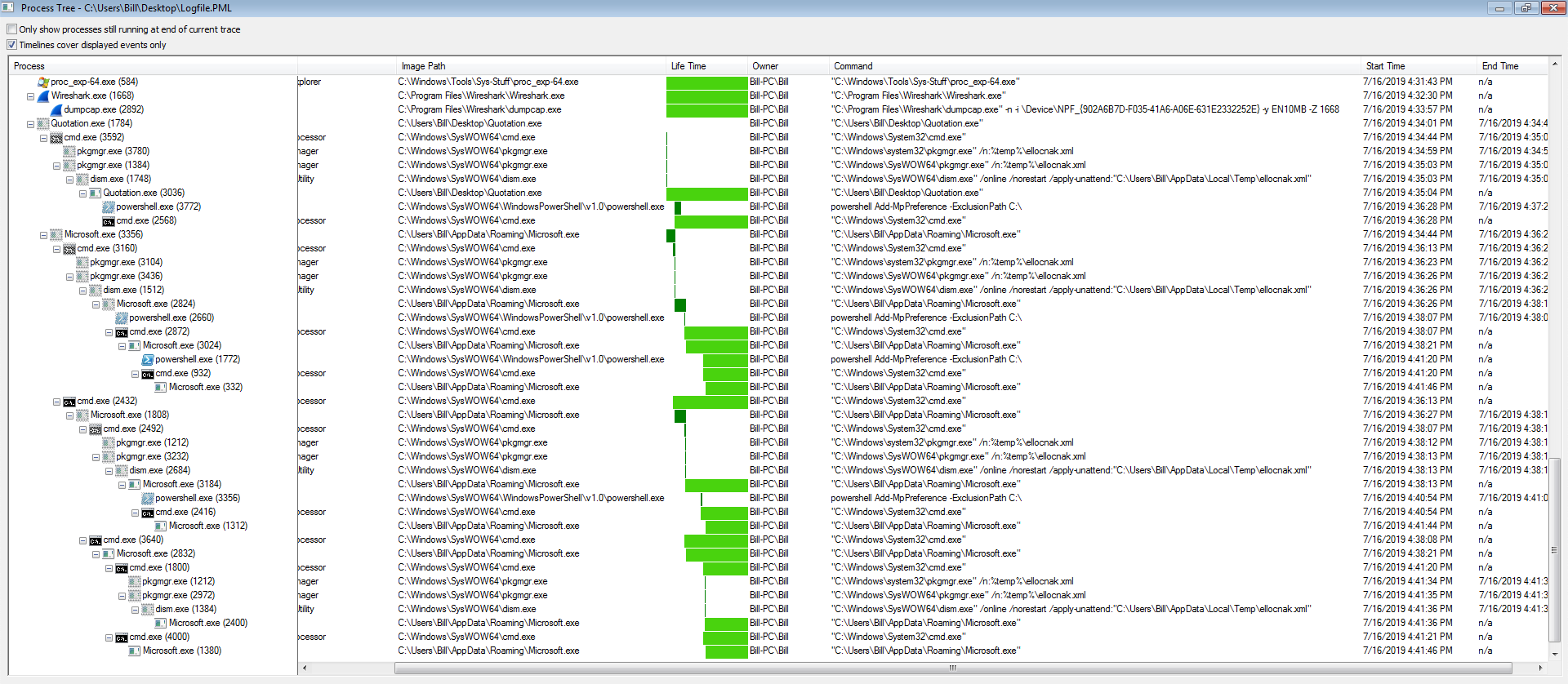
Shifting from the network side of things to the file side of this infection, things got pretty interesting. When looking at the Any.Run results or the process tree from ProcMon, you can see that the files called “Microsoft.exe” and “Quotation.exe” (which are the same files, just in different locations – AppData\Roaming\ and %TEMP%) start making calls and creating children processes. No big deal right as most malware does this type of thing. I could also see that these processes were making some interesting outbound calls as seen below.
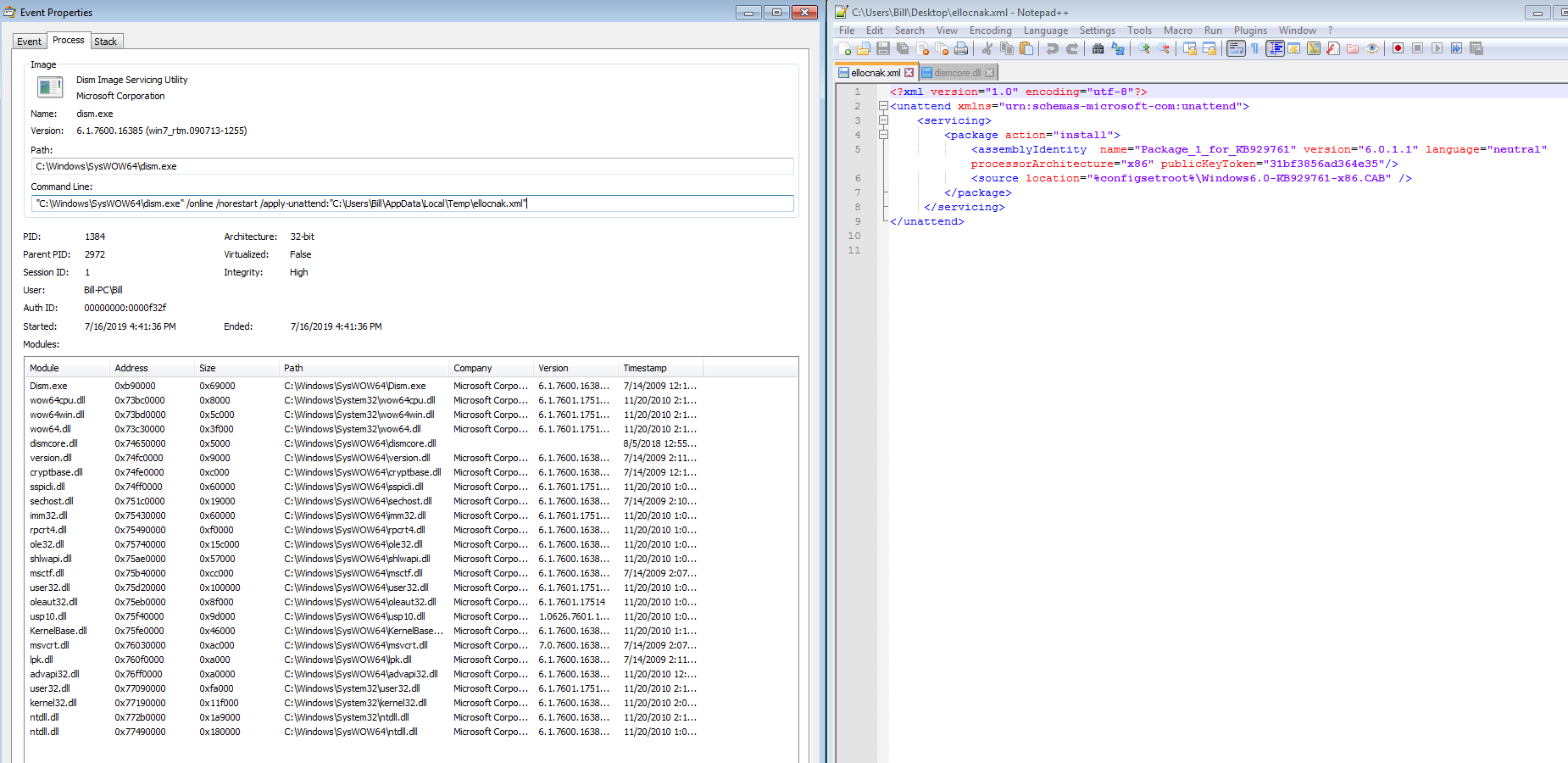
The one thing that I thought that was weird/strange was the creation of an XML file in the %TEMP% directory.
<?xml version="1.0" encoding="utf-8"?>
<unattend xmlns="urn:schemas-microsoft-com:unattend">
<servicing>
<package action="install">
<assemblyIdentity name="Package_1_for_KB929761" version="6.0.1.1" language="neutral" processorArchitecture="x86" publicKeyToken="31bf3856ad364e35"/>
<source location="%configsetroot%\Windows6.0-KB929761-x86.CAB" />
</package>
</servicing>
</unattend>
Looking into this more and trying to understand what this XML file is doing, I came across the following forum post discussing some interesting UAC bypass tricks. About 1/2 way down the forum post (look for “Live example #2. Exploiting g_lpAutoApproveEXEList”) there is a post discussing the same XML file that I saw on my VM. The XML file helps aid the malware in bypassing UAC as seen in the ProcMon Process Tree which is ultimately running in an elevated privilege via the pkgmgr.exe –> dism.exe processes. This would also explain why there was the “dismcore.dll” in the %TEMP% folder as well.
Persistence was obtained via a registry key in HKCU\Software\Microsoft/Windows\CurrentVersion\Run pointing to the “Microsoft.exe” file located in the C:\Users%USERNAME%\AppData\Roaming as seen below.