2020-09-22 Deobfuscating Emotet Script
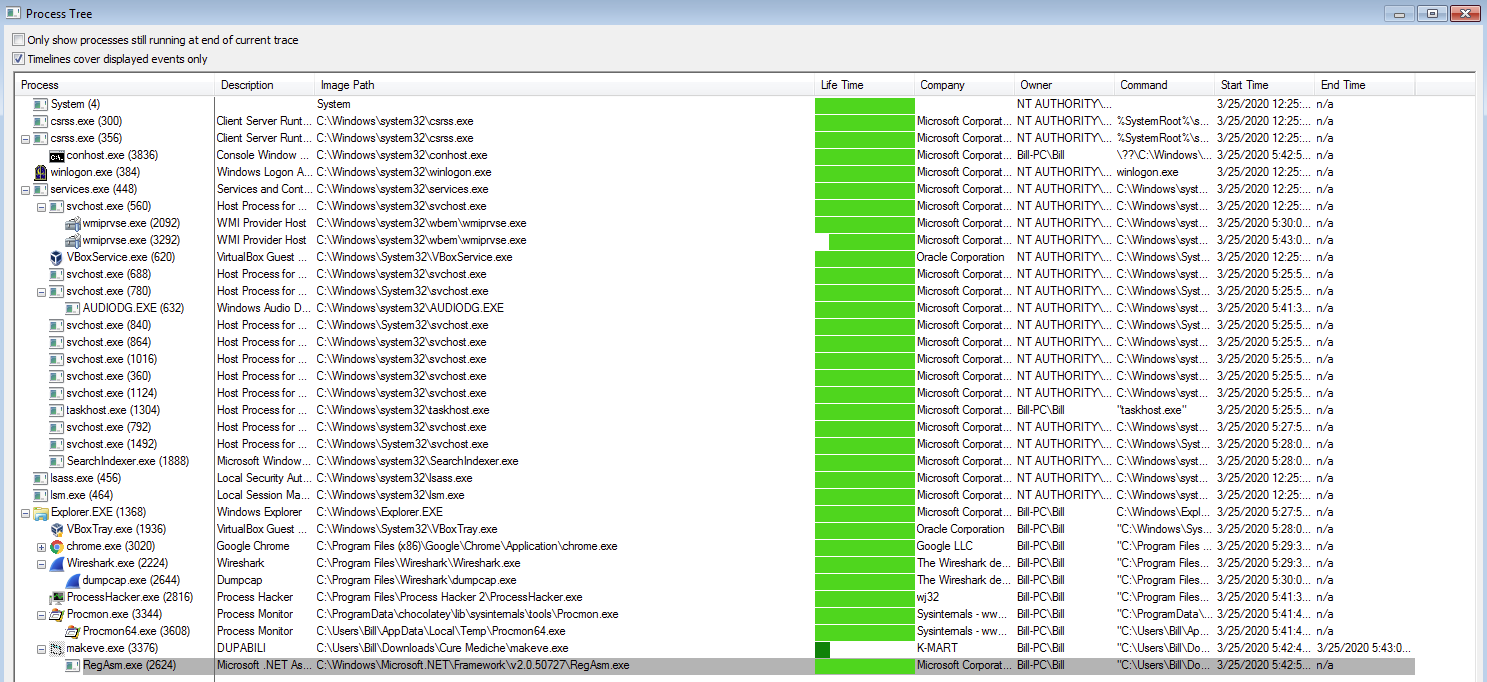
Summary ========= In this post I am going to cover how I managed to to deobfuscate the macro for this Emotet (Epoch 2) sample. The maldoc can be found here. Analysis ========== With this, I started off with the tried and true OleTools suite to see if I could get anything from this sample. Unfortunately I got a lot of Python errors when trying to run this. I then tried to run it through OfficeMalscanner and got nothing back as well. Looking at the Word doc via “file” I could see that there was a macro in the file and…