Malware Exercise 2015-08-31 – What’s the EK? What’s the payload?
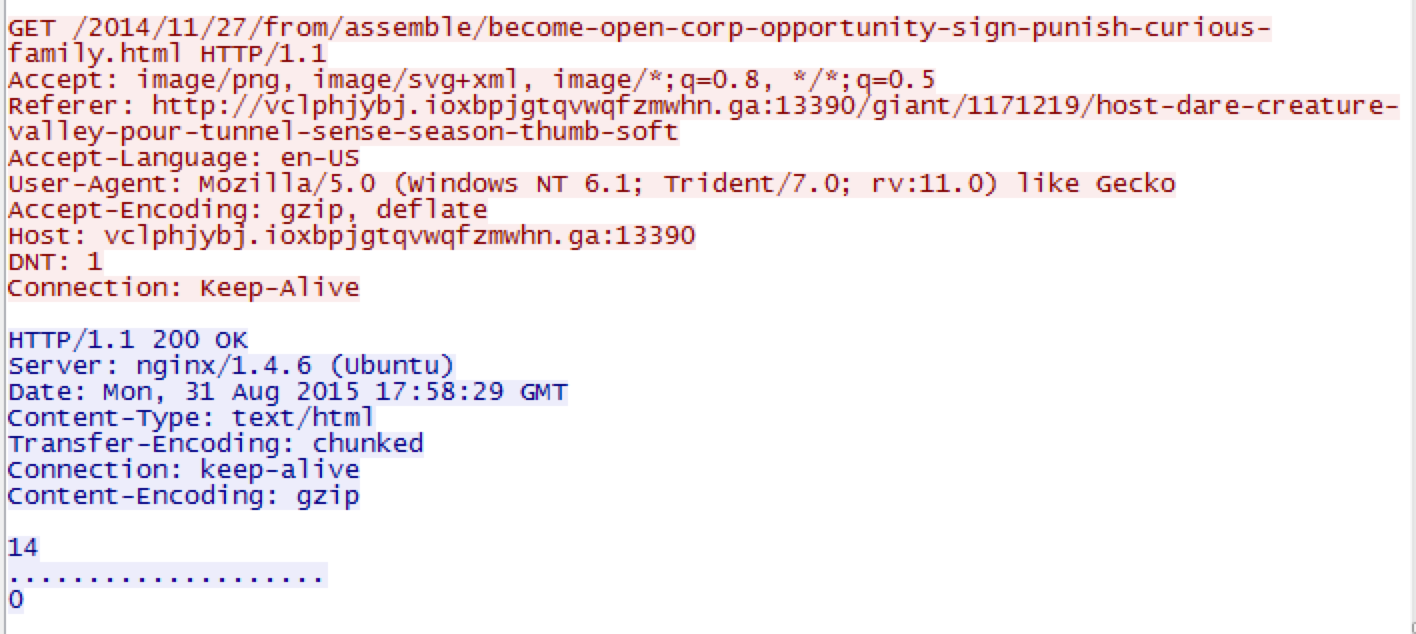
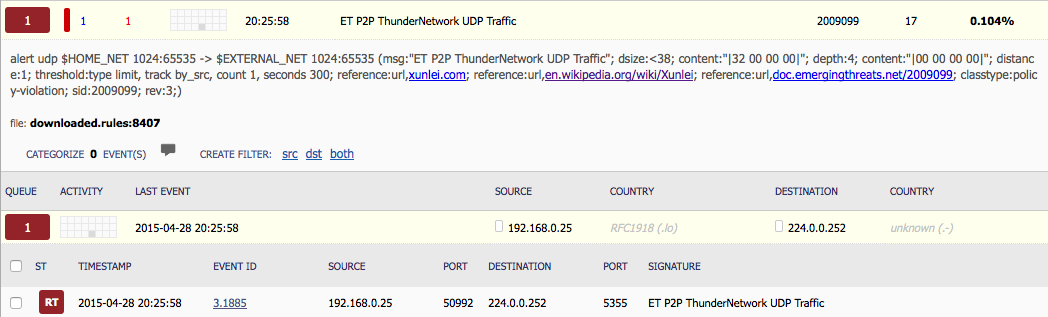
TL;DR Basically this is one of Brad’s typical spot the malware within the PCAP from a drive-by infection. Nothing exciting like the previous one, but still good practice. Unfortunately I did get some of this one wrong (stupid me for not updating Snort rules in Security Onion). Also, one thing to note about this one that threw me for a loop. Trying to export objects in Wireshark did not work for me. I ended up using CapTipper’s “dump” command to export all the objects from the PCAP into a directory. My Results IP address of the Windows computer that was…