Meta
=====
From: World Health Organization
Subject: COVID 19: Passaggi Medici Per Essere Sicuri
Link in the email: hxxps://onedrive[.]live[.]com/download?cid=265DAF943BE0D06F&resid=265DAF943BE0D06F%21177&authkey=AIGcwdd1XE_CXLM
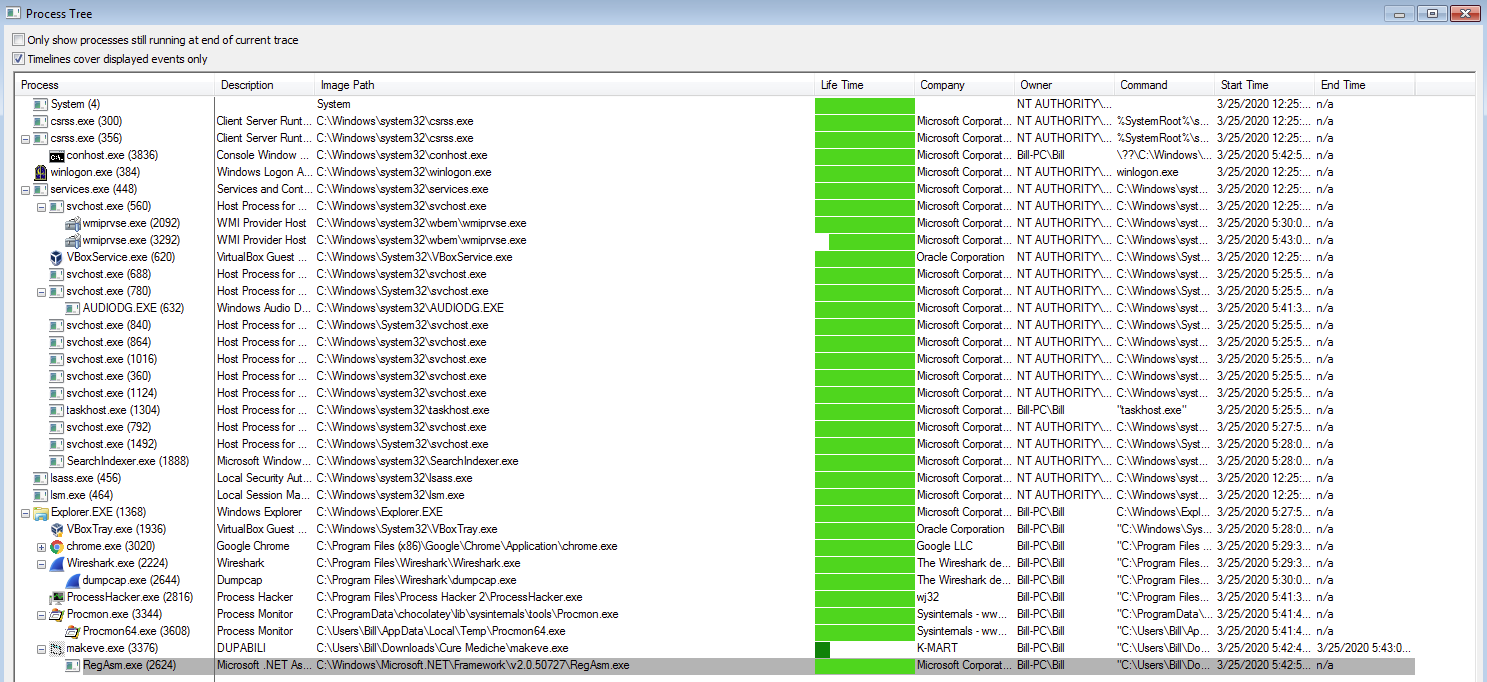
Unlike the other one that I documented here I could not find any method of persistence in this infection. Also, once the EXE from the ISO has been extracted and executed, it created a child process of “RegAsm.exe” to do the heavy lifting while terminating itself as you can see in the below image. This is the process that made the callouts to the couple of IP addresses seen (including data exfil via port 587).
Outside of that this was your normal run of Agent Telsa. Artifacts and PCAP can be found over in my Github repo located here.
Reference
==========
Malshare: http://malshare.com/sample.php?action=detail&hash=9fed11cd0c0bc367b30b08650dfba78f
MalwareBazaar: http://bazaar.abuse.ch/sample/c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a | http://bazaar.abuse.ch/sample/b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752
AnyRun: http://app.any.run/tasks/8279e4d7-9f37-4f8c-8f50-3f41f4ffc425
Triage: http://tria.ge/reports/200325-ajbtfx9qy2/static1
VT: http://www.virustotal.com/gui/file/b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752/detection | http://www.virustotal.com/gui/file/c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a/detection
Artifacts
==========
IOCs
—–
onedrive[.]live[.]com/download?cid=265DAF943BE0D06F&resid=265DAF943BE0D06F%21177&authkey=AIGcwdd1XE_CXLM – 13[.]104[.]42[.]13:443 (TCP)
gqa9cw[.]dm[.]files[.]1drv[.]com – 13[.]104[.]42[.]12:443 (TCP)
63[.]250[.]44[.]99:587 (TCP)
Email hashes
————-
98f1d11511f6bdaaf3a172b28a0684652bb19ea39c9c03226b329808cf06b483 — babsha925411157092.eml
71a3cf41a223f6acdb9af74c0727b83519cddd4d18dc9d598bd73ff41d022cde — fqhitf034619157093.eml
c1166cb7826c73bd58df1cc9861fbf803493048e2482f82175b7872d8f35810a — gsfvxr304743157094.eml
d1f3f9a54b2436dc3295f44f691955b67db26adf023f995223430f9e9c2e1442 — lkjtis506730157094.eml
9a964c0881dc9304bd8e84a4b5f93cf6364015b497f95713e5014ca4b32cc56f — lpiepe270366157094.eml
a0887c28ea0e3813030955c8406186bd8e3ce3fa8a607e5e9de2dc28e1833f95 — nqcwpx366703157091.eml
b1d74fa576870db5b03e8f975b339f641454e6b337527367520c01caab38600e — ousuxu199249157094.eml
2f2a5a968573b732c316c72100fe84083da1258624983d737f35467826994596 — phwhop078067157093.eml
766e00a8c35d5c5f3da6b04fb99ac68a6410e7cdaea5621cce5ec7a2da3b3f7f — pnfyxv576698157094.eml
0077b9ca2b884f617fa12e19b924ea70b5bd9a4740a1c7b779ee4bc803d66979 — sztvxy079777157096.eml
022cf2f0c7a8ead023f3766283d0e80bc7bdcb94b28d6d26683f5f94380285fc — uoplrc973765157092.eml
3f9451cf771ef7105ba46077818bedf6bedc24545e5949b4d720e64fde1b804e — wkqfxw145898157093.eml
6d7bec87cf26bd7cead8a60f09cd48b03c71bd96552ccd0a3dd6cd6ccce5e13e — xvqnoj876256157092.eml
8e0cd347a19c08320db17214831be9bb2d493ecaed4d71845a9c64845e57a803 — yahguq810702157092.eml
ae6e7bb9994c4485d6ece2d184b41c2b1f09f4d98debca3259dd2136221acfc3 — zrszrs625922157094.eml
File hashes
————
b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752 — Cure Mediche.iso
c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a — makeve.exe
Machinae results
—————–
$ machinae b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752 c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a
[.] Requesting http://www.virustotal.com/vtapi/v2/file/report?apikey=XXX&resource=b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752 (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/file/report?apikey=XXX&resource=c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a (GET)
********************************************************************************
* Information for b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-03-25 12:19:32
[-] Detected engines: 5
[-] Total engines: 60
[-] Scans: (‘BitDefenderTheta’, ‘Gen:NN[.]ZevbaF.34104[.]im0@aK1S9Cmi’)
[-] Scans: (‘TrendMicro-HouseCall’, ‘Possible_GENISO-4B’)
[-] Scans: (‘TrendMicro’, ‘Possible_GENISO-4B’)
[-] Scans: (‘Microsoft’, ‘Trojan:Win32/Wacatac.C!ml’)
[-] Scans: (‘Ikarus’, ‘Trojan-Spy[.]Keylogger[.]AgentTesla’)
********************************************************************************
* Information for c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-03-25 12:19:41
[-] Detected engines: 8
[-] Total engines: 71
[-] Scans: (‘Qihoo-360’, ‘HEUR/QVM03.0.1EED[.]Malware[.]Gen’)
[-] Scans: (‘Cylance’, ‘Unsafe’)
[-] Scans: (‘APEX’, ‘Malicious’)
[-] Scans: (‘Trapmine’, ‘suspicious.low[.]ml[.]score’)
[-] Scans: (‘Microsoft’, ‘Trojan:Win32/Sonbokli.A!cl’)
[-] Scans: (‘Acronis’, ‘suspicious’)
[-] Scans: (‘eGambit’, ‘Unsafe[.]AI_Score_97%’)
[-] Scans: (‘BitDefenderTheta’, ‘Gen:NN[.]ZevbaF.34104[.]im0@aK1S9Cmi’)
$ machinae 63.250.44.99
[.] Requesting http://www.ipvoid.com/ip-blacklist-check (POST)
[.] Requesting http://malc0de.com/database/index.php?search=63.250.44.99 (GET)
[.] Requesting http://abuseipdb.com/check/63.250.44.99 (GET)
[.] Requesting http://ransomwaretracker.abuse.ch/host/63.250.44.99 (GET)
[.] Requesting http://isc.sans.edu/api/ip/63.250.44.99 (GET)
[.] Requesting http://freegeoip.io/json/63.250.44.99 (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=63.250.44.99 (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/ip-address/report?ip=63.250.44.99&apikey=XXX (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=63.250.44.99 (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/ip/default.aspx?ip=63.250.44.99 (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/63.250.44.99/events/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/63.250.44.99/domains/ (GET)
[.] Requesting http://cymon.io/api/nexus/v1/ip/63.250.44.99/urls/ (GET)
[.] Requesting http://www.threatcrowd.org/searchApi/v2/ip/report/?ip=63.250.44.99 (GET)
********************************************************************************
* Information for 63.250.44.99
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[!] Error from IP Whois: ‘IPWhois’ object has no attribute ‘lookup’
[-] No IPVoid Results
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No RansomwareTracker Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Not Rated
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-02-24’, ‘popeorigin[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-03-25’, ‘popeorigin5[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-25’, ‘popeorigin6[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-25’, ‘popeorigin7[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-24’, ‘webmail[.]popeorigin[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-03-25’, ‘webmail[.]popeorigin5[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-25’, ‘webmail[.]popeorigin6[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-24’, ‘www[.]popeorigin[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-03-25’, ‘www[.]popeorigin5[.]pw’)
[-] pDNS data from VirusTotal: (‘2020-02-25’, ‘www[.]popeorigin6[.]pw’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-03-20’, ‘hXXp://popeorigin7[.]pw/’)
[+] Reputation Authority Results
[-] Reputation Authority Score: 50/100
[-] No McAfee Threat Results
Munin results
————–
1 / 2 > Suspicious
HASH: b0d9703714cc221faaba6dd5c4089f5866e2c2dcc8b342e7dfdd647e29ab4752 COMMENT: Cure Mediche.iso
VIRUS: Microsoft: Trojan:Win32/Wacatac.C!ml / TrendMicro: Possible_GENISO-4B
TYPE: ISO image SIZE: 196.0 KB FILENAMES: Cure Mediche.iso, Cure Mediche.iso
FIRST: 2020-03-25 12:19:32 LAST: 2020-03-25 12:19:32 SUBMISSIONS: 1 REPUTATION: 0
COMMENTS: 0 USERS: – TAGS: CONTAINS-PE ISOIMAGE
RESULT: 5 / 60
2 / 2 > Malicious
HASH: c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a COMMENT: makeve.exe
VIRUS: Microsoft: Trojan:Win32/Fareit.AE!MTB / Kaspersky: Trojan.Win32.Vebzenpak.kbd / McAfee: Artemis!9FED11CD0C0B / CrowdStrike: win/malicious_confidence_80% (W) / ESET-NOD32: a variant of Win32/Injector.ELFS / GData: Win32.Trojan.Agent.5YQ2H5
TYPE: Win32 EXE SIZE: 136.0 KB FILENAMES: Enterophth8.exe, Enterophth8, Enterophth8.exe, makeve.exe
FIRST: 2020-03-25 12:19:41 LAST: 2020-03-25 23:24:54 SUBMISSIONS: 1 REPUTATION: 0
COMMENTS: 1 USERS: VMRay TAGS: PEEXE RUNTIME-MODULES DIRECT-CPU-CLOCK-ACCESS CHECKS-USER-INPUT
RESULT: 21 / 71
[!] Sample on ANY.RUN URL: http://any.run/report/c7c2e3e6dc40ec793635b6f18e44223d8cbf9fb621ee0d5b374b709510fe2d9a