So last week I came across some malspam that used a PDF with an embedded Word document in it that encrypted my test VM with Jaff ransomware which I discussed here. Trying to figure out how the script worked, I came across some aspects/things that I had not seen done before. Here is my walk through of this script.
I started with the cleaned up scripts that made up the macro by using OfficeMalScanner against the Word document. Once I had the scripts, I walked through the code starting with the “ThisDocument” script. This is where the malicious macro will start from since the “autoopen” subroutine is listed here. What you will want to look for are calls to other sub-routines or functions in the various script files – in this case there is a function called Synomati and it passed the parameter “a4833.”
Sub autoopen() SignIn_Fish = 0 Synomati "a4833" End Sub
Looking for “Synomati” in all the scripts, you will see there are multiple hits for it in Module1 and Module2. Start with Module1 and you will see the following function.
Public Function Synomati(Comps) GoTo l12 strComputer = Comps If InStr(1, strCaption, "Windows 7", vbTextCompare) Then Synomati = "Win7" End If If InStr(1, strCaption, "XP", vbTextCompare) Then Synomati = "XP" End If l12: Dim c As STRIX Set c = New STRIX CallByName c, LocalBrowser.T2.Text, _VbMethod End Function
You will immediately go to ‘l12’ which then proceeds to set some variables (one of which is the script STRIX), and calls a function in the STRIX script (LocalBrowser.T2.Text). **Note: this script uses GOTO statements throughout it. When looking through the STRIX script for the function LocalBrowser.T2.Text, I could not find it, but did notice that there was a function called “setAsMainTarget.”
Public Function setAsMainTarget() As String
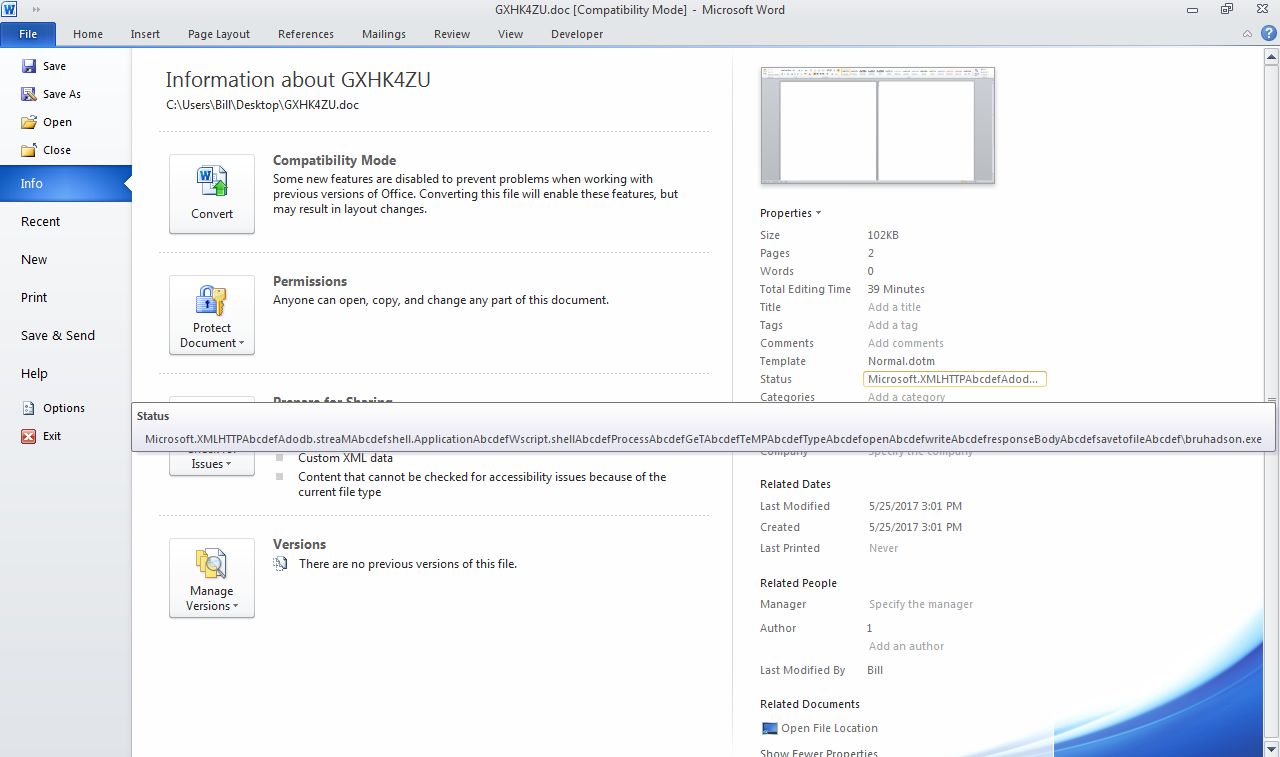
tt = ThisDocument.BuiltInDocumentProperties("Content status").Value
MotoGP = Split(tt, "Abcdef")
privateProbeName = MotoGP(Quubo * 3)
privateProbe
setAsMainTarget = ""
End Function
This got me thinking – why are there statements throughout the scripts called “LocalBrowser.” and in this one something being referenced in “ThisDocument” and it’s properties (especially the content status value)? After some time and some research, I came across the fact that the “ThisDocument.BuiltInDocumentProperties(“Content status”).Value” is actually found within the file information for the Word document itself.
Also, while looking at the code within the builtin VB editor in Word, I noticed that there was a form called “LocalBrowser.” Within this form there were other details that the scripts referenced as you can see below.
LocalBrowser.T2.Text -> setAsMainTarget LocalBrowser.Label1.Caption -> rundll32.exe LocalBrowser.Command.Caption -> V LocalBrowser.ZK.Caption -> http:// LocalBrowser.OptionButton1.Tag -> Open LocalBrowser.ToggleButton1.Caption -> Send LocalBrowser.Label2.Caption -> File
Now that the values for LocalBrowser. are known, and the fact that other values could be referenced from within the actual Word document itself, I could really start walking through the code. The cleaned up code can be found here.
***Note: The functions High4 / WidthA and possibly Subfunc, I believe, deal with encrypting the download of the binary from the compromised website since the PCAP has the repeated string of “6WLms4bGcHU5iDixvWv6Wmuql3ILxV8S” in it.