2016-12-14 Malspam Leads to New Version of Locky
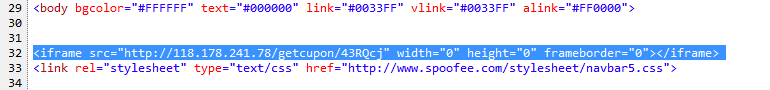
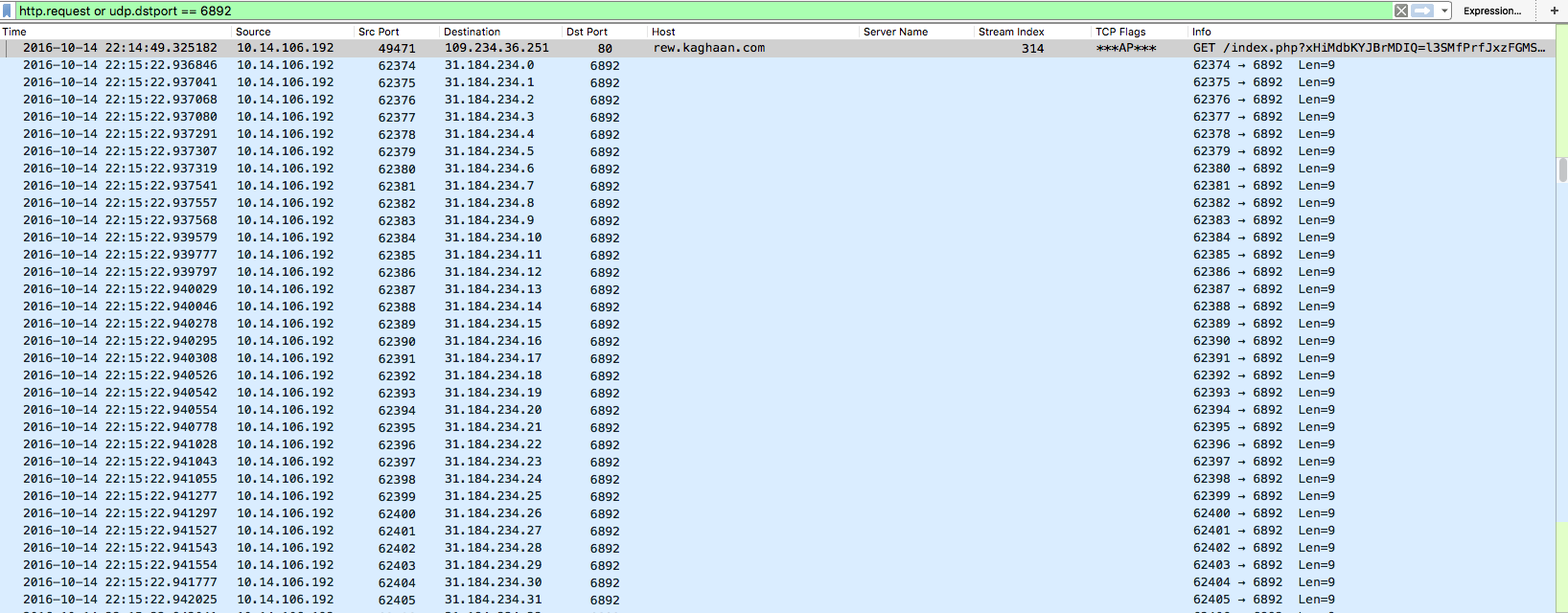
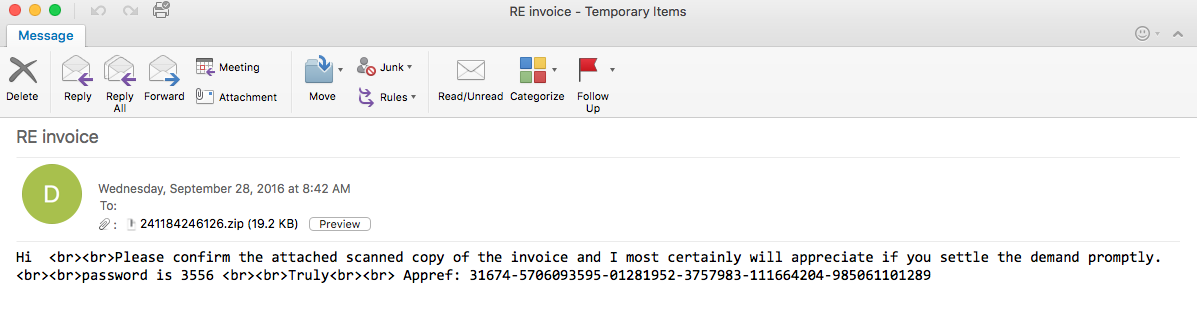
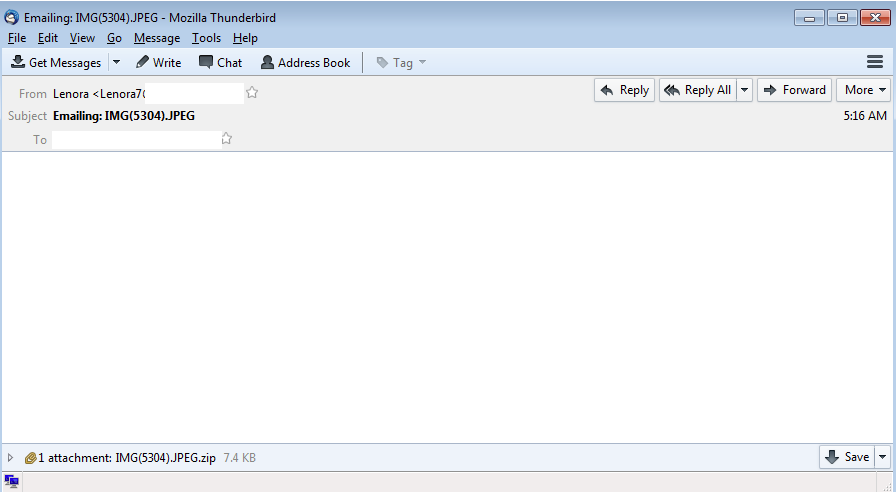
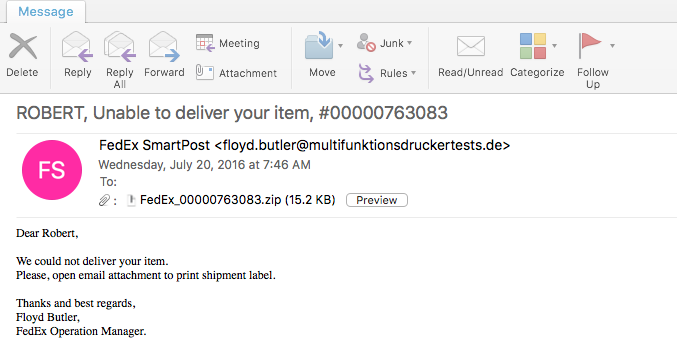
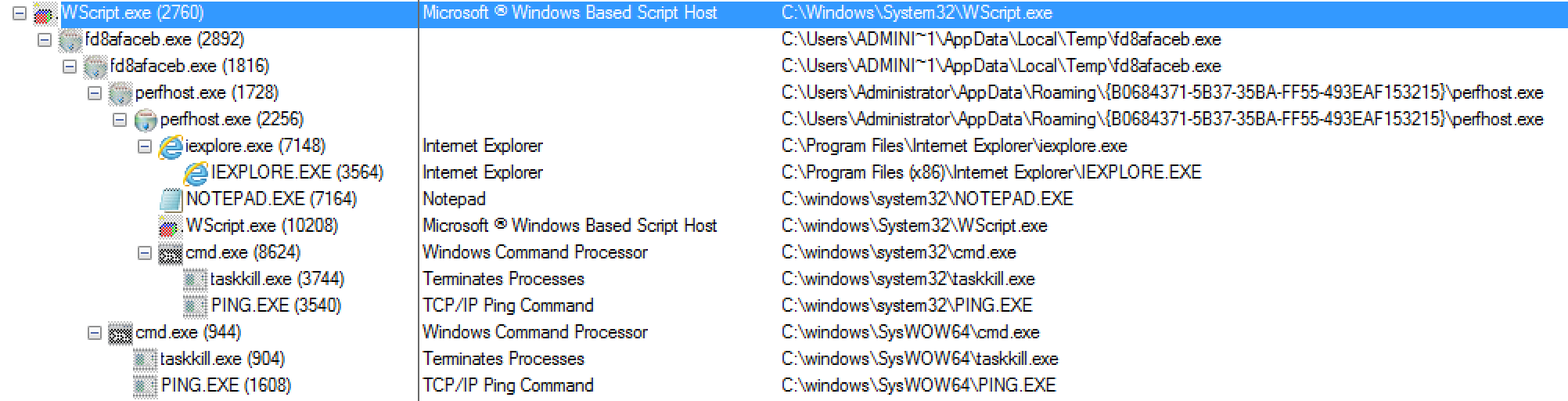
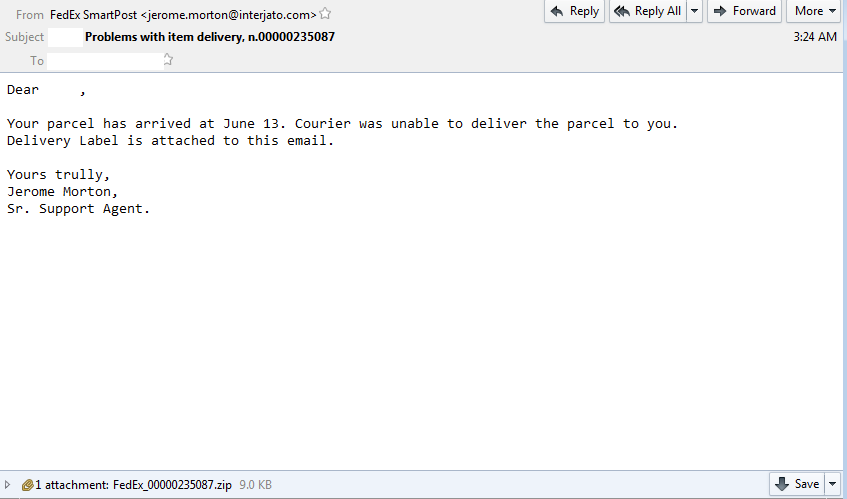
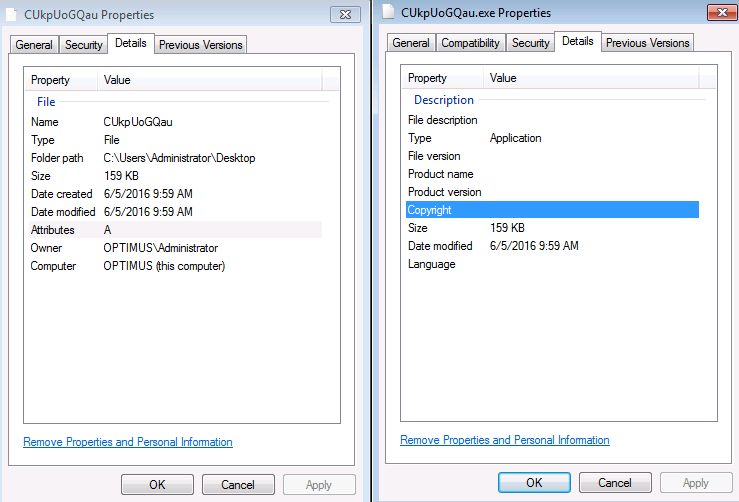
Here is another example of of the latest version of Locky that I saw being delivered via some malspam. This time the email poses as a certificate for a parcel being sent. For more information about this new version of Locky, please see the article over on Bleeping Computer or Google it as there are a lot of resources out there talking about it. For the artifacts found from this infection, please see my Github repo here. Indicators of Compromise ======================== 74.208.1136.182 / mintthaicafe.com 86.110.117.155 Artifacts From Investigation ============================ File Name: q82iGnKI5 File size: 168KB MD5 hash: 996d8e3da574021232469243cf006eb3 Virustotal: NA…