2016-05-10 Locky Infection From MalSpam
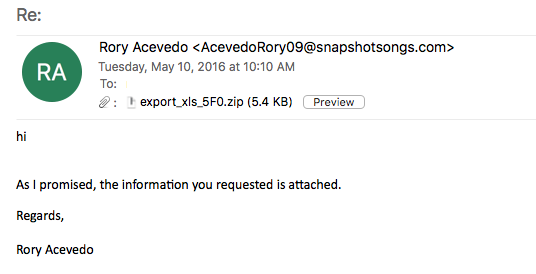
This post is covering some Locky malspam that I was able to find while working in the SOC the other day. For the artifacts and such from this post, please see the Github repo located here. IOCs: ==== 5.39.70.7 / cmobilier.com 193.124.185.87 File name: export_xls_5F0.zip MD5 hash: 11e29168d188a4af060772422bb8a1d2 Size: 8KB VirusTotal: http://www.virustotal.com/en/file/88ba0118c53b1c9119084bd0700db0c01f39cfe1f2b5d71ed10c4c14bd93c42f/analysis/ Detection ratio: 11 / 57 First submission: 2016-05-10 09:10:35 UTC Within the zip archive there are 3 javascript files that look identical. The 3 files have the following characteristics: File name: transactions 4337328.js / transactions 4337328.js – copy.js / transactions 4337328.js – copy (2).js SHA1 hash (same hash…