So here is my answers for the latest exercise from Brad. This one threw me off a bit as I thought that I was missing something when reviewing the PCAP since I was not seeing the “usual” things that I have come to expect from Brad when doing these exercises. It reminded me of when I was in school and would get through an exam with plenty of time to spare. I would then look around and see that the rest of the class was still chugging through the test. Then self-doubt would kick in. Did I miss something, or did I rush through this? And then I would spend the rest of the time double checking my answers and second-guessing myself.
So here are my results from this exercise. Hopefully I did not miss something…
About the Investigation
=======================
– Date and time range of the traffic you’re reviewing.
> First packet: 2016-04-15 23:50:49 / Last packet: 2016-04-16 00:01:19
– IP address, MAC address, username, and host name.
> 172.16.155.254 / 00:0b:46:7f:9e:22 / manny.lehman@mailinator.com / MANNY-PC
– Description of the activity (what happened, if the host became infected, any details, etc.).
> Based on what I am seeing in the PCAP, the user used Bing to find the website “billinggoldspal[.]com.” The site landed the user on a fake login page for what looks like an Apple page. The user then proceeded to enter their information into this fake site. Outside of that, there does not look to be anything malicious in the traffic or anything malicious downloaded to the user’s system.
– A conclusion with recommendations for any follow-up actions.
> User education on what to look for when it comes to phishing sites asking for the user’s information would be a great start. I would also block this IP/FQDN at the perimeter to make sure that the user cannot visit this site again from the corperate network.
– Indicators of Compromise (IP, FQDN, etc…)
> 91.194.91.203 / billinggoldspal[.]com
About the Investigation
=======================
– Date and time range of the traffic you’re reviewing.
> First packet: 2016-04-15 23:50:49 / Last packet: 2016-04-16 00:01:19
– IP address, MAC address, username, and host name.
> 172.16.155.254 / 00:0b:46:7f:9e:22 / manny.lehman@mailinator.com / MANNY-PC
– Description of the activity (what happened, if the host became infected, any details, etc.).
> Based on what I am seeing in the PCAP, the user used Bing to find the website “billinggoldspal[.]com.” The site landed the user on a fake login page for what looks like an Apple page. The user then proceeded to enter their information into this fake site. Outside of that, there does not look to be anything malicious in the traffic or anything malicious downloaded to the user’s system.
– A conclusion with recommendations for any follow-up actions.
> User education on what to look for when it comes to phishing sites asking for the user’s information would be a great start. I would also block this IP/FQDN at the perimeter to make sure that the user cannot visit this site again from the corperate network.
– Indicators of Compromise (IP, FQDN, etc…)
> 91.194.91.203 / billinggoldspal[.]com
Notes from the investigation:
=============================
Performing the usual steps for when I look at these types of PCAPs (Statistics –> Protocol Hierarchy and Conversations) showed that most of the communication was over TCP and via ports 80 and 443. There was no evidence of any callbacks on strange ports or anything like that. I also noticed that the DNS of the system was setup for Google’s DNS servers and not the local ISP’s DNS or the router that the system was sitting behind. From there I used the filter of “http.request” to see what sites were found in the PCAP while also looking at the HTTP Objects as well to see what types of files are in the PCAP. Nothing stood out here.
I then used the alerts found Suricuta which gave me a clue:
Count:1 Event#3.13546 2016-04-15 23:34:01 ETPRO CURRENT_EVENTS Successful Paypal Phish Dec 8 M2 172.16.155.149 -> 91.194.91.203 IPVer=4 hlen=5 tos=0 dlen=634 ID=0 flags=0 offset=0 ttl=0 chksum=47435 Protocol: 6 sport=49273 -> dport=80</code> Seq=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=3 chksum=0
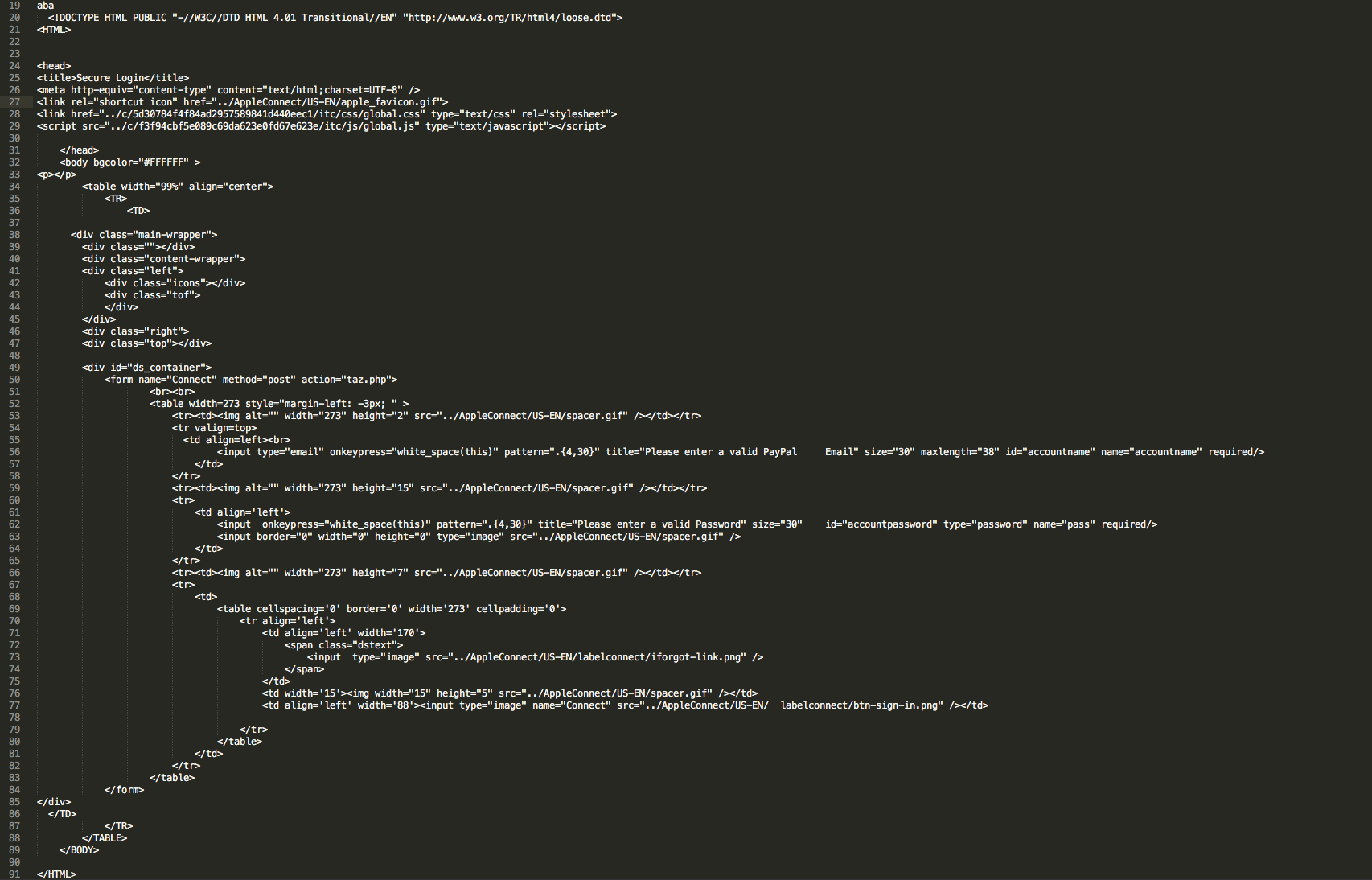
Looking at the page via the filter “http.host == “billinggoldspal.com”” I then proceeded to see what looked to be a fake Apple site as you can see below:
GET /cola/153b7ff4a55eb44e549bcd88c8c11368/index/web/Login/index.php HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: billinggoldspal.com DNT: 1 Connection: Keep-Alive HTTP/1.1 200 OK Date: Fri, 15 Apr 2016 22:55:03 GMT Server: Apache/2.4.18 (Unix) OpenSSL/1.0.1e-fips mod_bwlimited/1.4 X-Powered-By: PHP/5.5.33 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Transfer-Encoding: chunked Content-Type: text/html
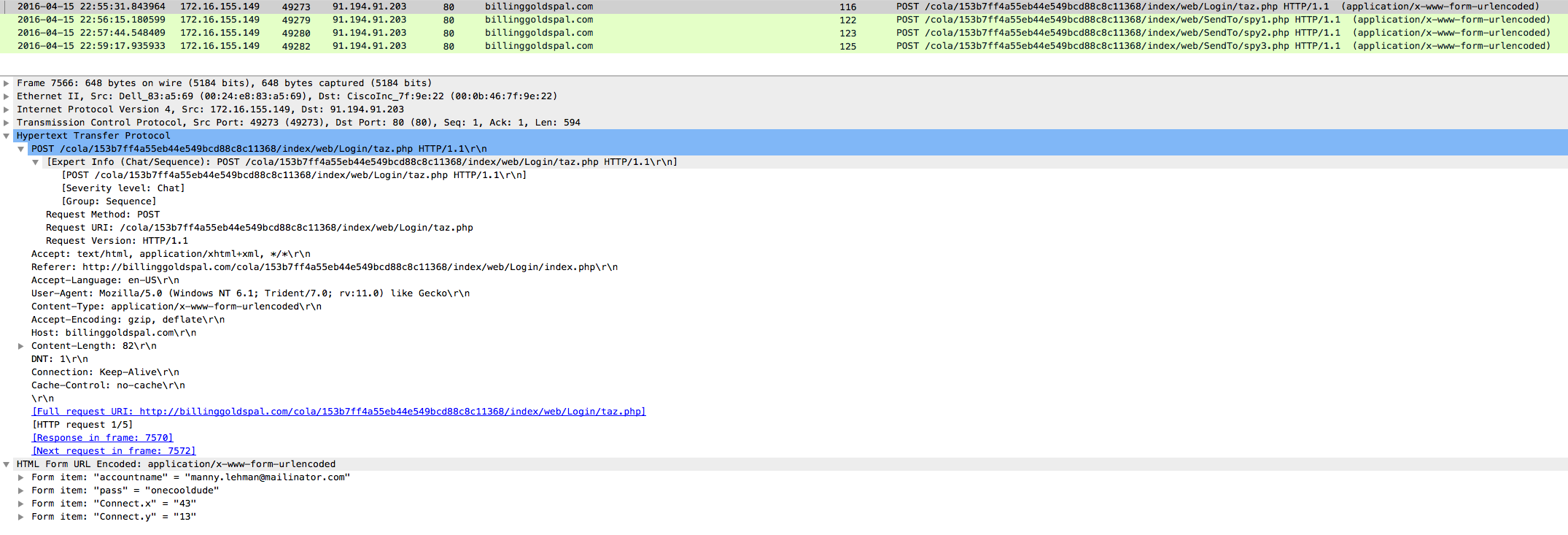
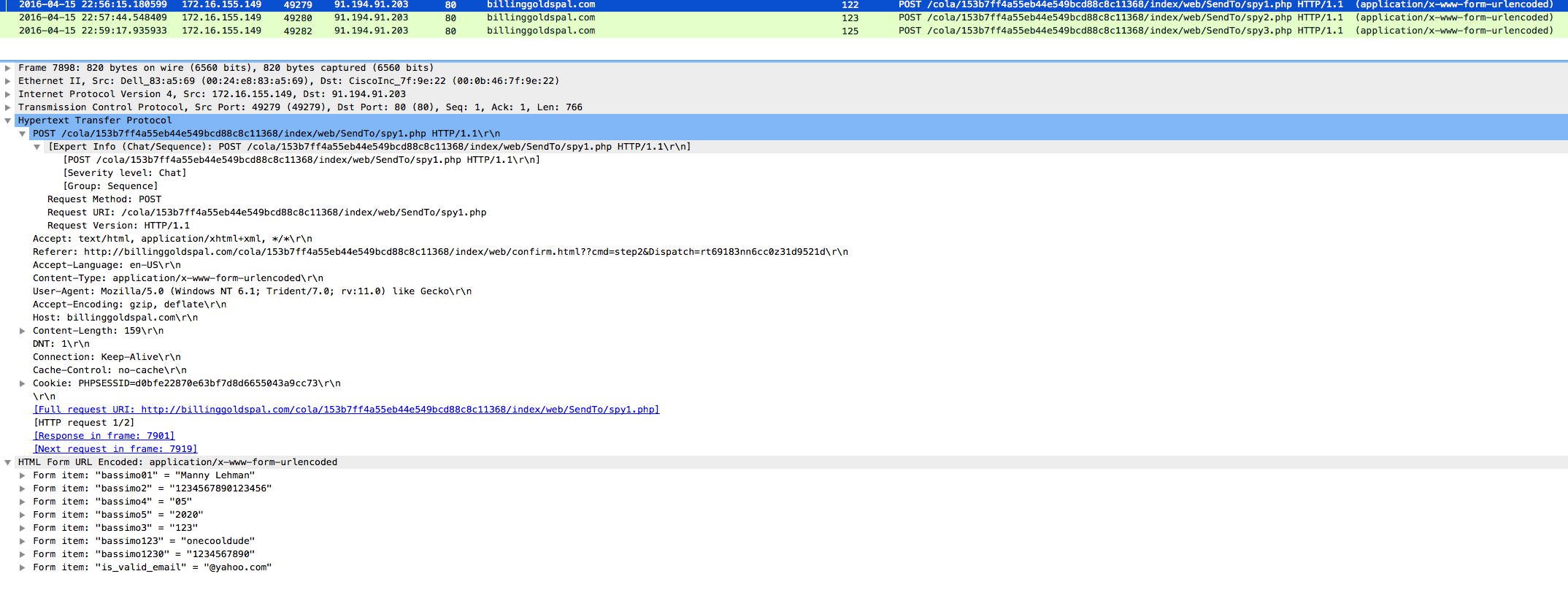
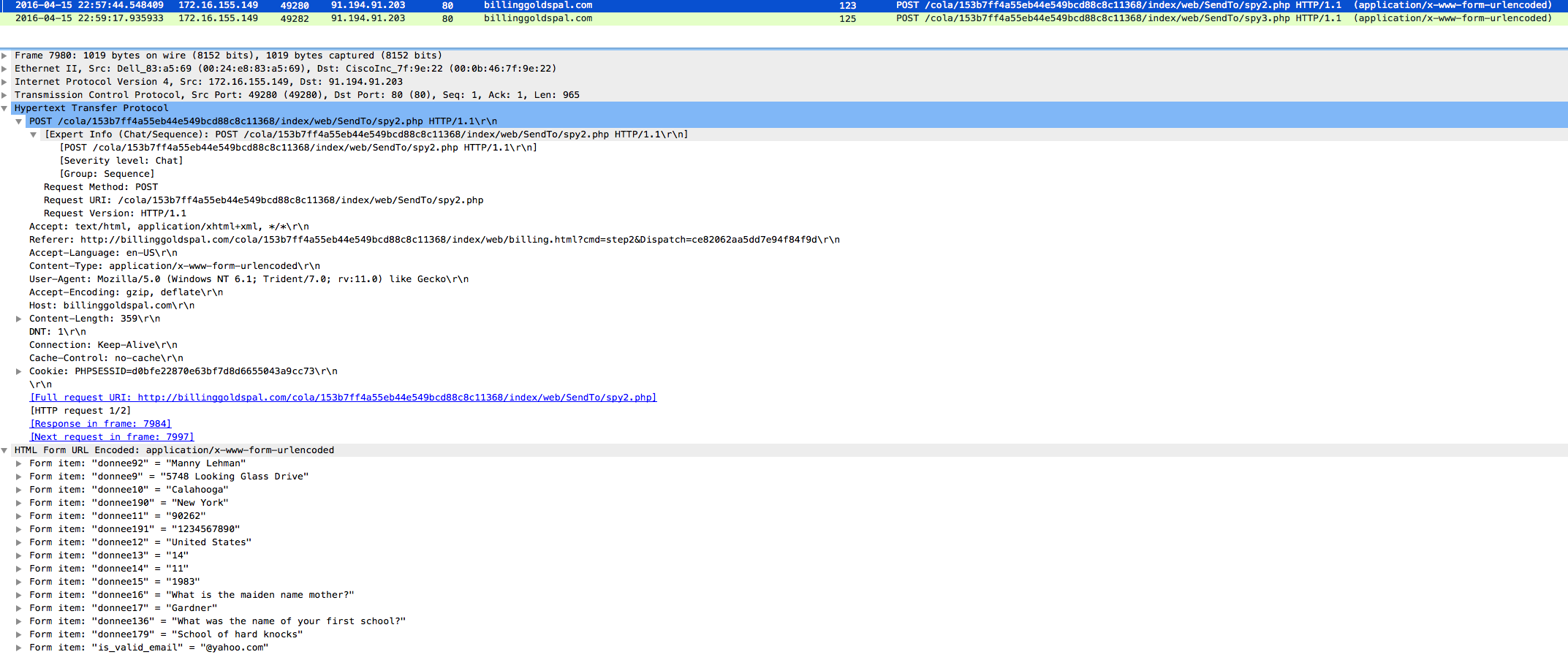
I also see that there are some POSTS as well to this site. Using the “http.request.method == “POST”” filter, I see that the user did believe that this was a legit site and gave the actor all the information that they were wanting as you can see below:
From there I am not seeing anything else malicious in traffic. Checking Virustotal for this site, I am seeing that this has been labeled as a malicious site:
URL: hxxp[:]//billinggoldspal[.]com/cola/153b7ff4a55eb44e549bcd88c8c11368/index/web/Login/index.php
First Submission: 2016-04-15 23:45:44 UTC
Detection ratio: 8 / 67
Virustotal link: http://www.virustotal.com/en/url/2b235f9d2e960accdb6803f75dad149c679815328ce933d0fcc94a083352ea0c/analysis/