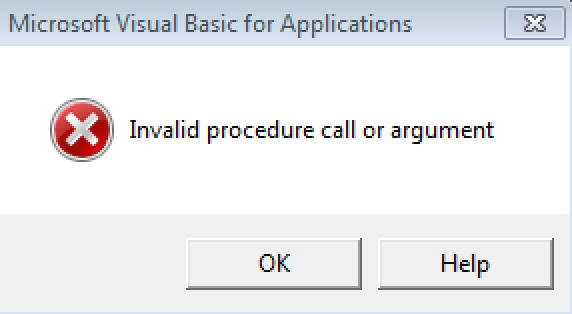
Today while investigating the normal events of the day we got some employees that got sent some phishing emails (related to the latest round of Dridex) with a Word document attached. The email is shown below:
The attached Word document has the following properties:
Name: INV19 - 778810.doc Size: 23.6KB MD5 Hash: 5fc9c03c42b2060050347d92758237d3 SHA256 Hash: 965c1e785b2fd3866b40d2d0046f6e6e6eb43e60f101f3bec1ed7eed9281060d VirusTotal Link: http://www.virustotal.com/en/file/965c1e785b2fd3866b40d2d0046f6e6e6eb43e60f101f3bec1ed7eed9281060d/analysis/</a>
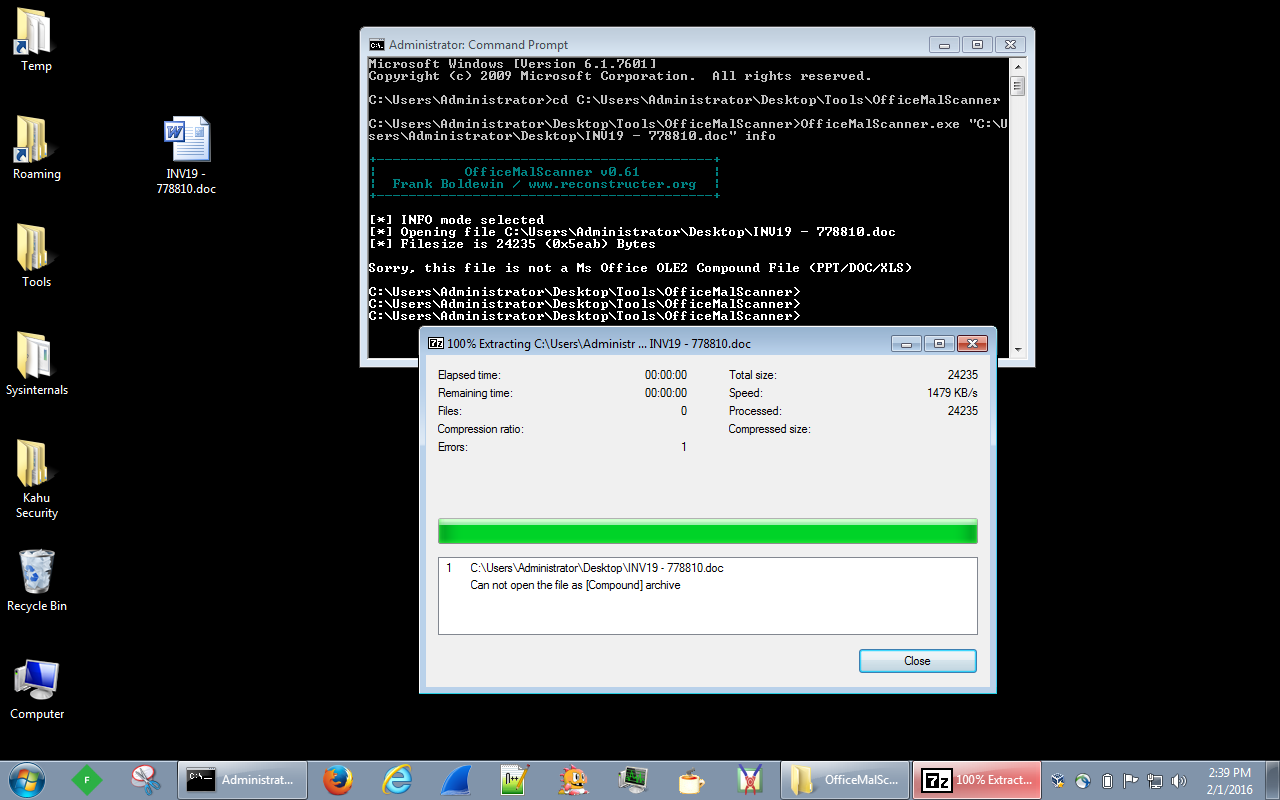
The interesting thing about this Word doc, and a couple of the others that came in as well, was the fact that I could not extract the contents from the doc via 7Zip, and OfficeMalScanner did not recognize it as an OLE file either as you can see below:
So I opened it up in Notepad++ to get a better idea of what I am dealing with and at the top of the page is the following in Russian:
Данный документ является веб-страницей в одном файле, также называемой файлом веб-архива. Если вы видите это сообщение, значит, данный браузер или редактор не поддерживает файлы веб-архива. Загрузите браузер, поддерживающий веб-архивы, например Windows® Internet Explorer®
Tranlated:
This document is a web page in a single file , also called the Web archive file . If you see this message , it means that the browser or editor does not support Web Archive files . Download a browser that supports web archives, such as Windows® Internet Explorer®.
So looking around the web I started to see some links talking about how malware authors use a certain vulnerability in Word to evade detection from AV software back in 2012. To read more about that check out these links here, here, and here. While some aspects of the file that I am looking at holds true (file paths mentioned here and there), there is nothing in the file mentioning any class IDs at all. Further research into this also led me here and how this is a MHT (MIME HTML) file format which is basically a MIME container similar to an email. So trying “OLETOOLS” to see if I can get a little more information about this file failed as you can see below:
./oleid.py INV19\ -\ 778810.doc Filename: INV19 - 778810.doc +------------+-------+ | Indicator | Value | +------------+-------+ | OLE format | False | +------------+-------+ [~/Downloads/oletools-0.41/oletools] : ./olevba.py INV19\ -\ 778810.doc olevba 0.41 - http://decalage.info/python/oletools Flags Filename ----------- ----------------------------------------------------------------- MHT:-------- INV19 - 778810.doc (Flags: OpX=OpenXML, XML=Word2003XML, MHT=MHTML, M=Macros, A=Auto-executable, S=Suspicious keywords, I=IOCs, H=Hex strings, B=Base64 strings, D=Dridex strings, V=VBA strings, ?=Unknown) =============================================================================== FILE: INV19 - 778810.doc Type: MHTML No VBA macros found.
So at this point I guess I will try to do this the old fashion way – run this manually on my test VM and see what happens…. YAY!
So when trying to run this from my test VM, I immediately get a pop-up stating the following:
And then it dies… Looking at the PCAP the only thing that I can see is the following call:
GET /indiana/jones.php HTTP/1.1 Connection: Keep-Alive Accept: */* User-Agent: Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5) Host: 31.41.45.23 HTTP/1.1 404 Not Found Server: nginx/0.7.67 Date: Mon, 01 Feb 2016 21:51:37 GMT Content-Type: text/html; charset=iso-8859-1 Connection: keep-alive Vary: Accept-Encoding Content-Length: 292 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>404 Not Found</title> </head><body> <h1>Not Found</h1> <p>The requested URL /indiana/jones.php was not found on this server.</p> <hr> <address>Apache/2.2.16 (Debian) Server at 31.41.45.23 Port 80</address> </body></html>
Well drat – that was anti-climatic all around. Dang server admins fixing their site before I could have my fun. Below are the files that I was able to obtain:
The file “yFUYIdsf.exe” is located in the “C:\Users\Administrator\AppData\Local\Temp” folder and has the following properties:
Name: yFUYIdsf.exe Size: 292 bytes MD5 Hash: 81a9bef11f1d64437f3c51b7aa65fd0e SHA256 Hash: 97dc0e15afed062bd6c4ec71bdcd6ef358522f30c49125cf668f3ab1ee52a381 VirusTotal Link: NA
Considering that the vulnerability has been out for some time now, I wondered if my install of Word has this patch or not. Also, I am seeing that there is a KB that seems to break macros. I found that link when looking around for what a “MSForms.exd” file was. Unfortunately, I am not seeing any updates to my copy of Office that would impact it.
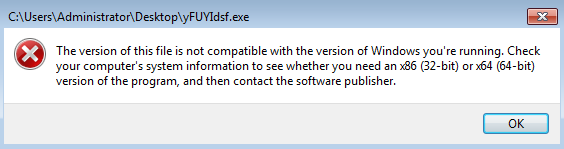
When I tried to run this executable in my restored VM, I got the following message:
When looking into this file further via PEStudio, I noticed in the strings section that the file had been modified by our email filtering appliance. Well that would explain why the file did not run correctly. To see what this looks like when it runs and works like it should, check out Brad Duncan’s post about this.