IoC from this investigation:
============================
myson123456[.]ddns[.]net
178.32.72.136:2550
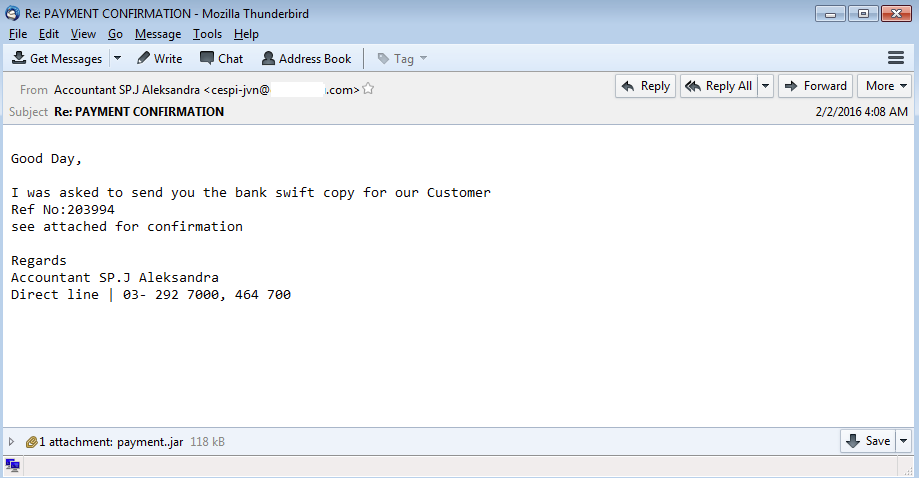
Here is another example of an email that most users get claiming that they (the user) has something that they need to action on. In this case it is a malicious Java file. Thankfully most email gateways block these types of files from every reaching the user base. Let’s dig in.
The Java file has the following characteristics:
File Name: payment..jar
Size: 118KB
MD5: f4b463e4df4ef274a198bfb07ed3e6cd
SHA256: f4c93ab532e53274bd97c00fccba3b231de0832e743879380f7af7bf81aef60fVirustotal Link: http://www.virustotal.com/en/file/f4c93ab532e53274bd97c00fccba3b231de0832e743879380f7af7bf81aef60f/analysis/
Detection Ratio: 25 / 54
First Submitted: 2016-02-07 21:28:02 UTCMalwr link: http://malwr.com/analysis/Y2FmYjEwNGM0MjM5NDBmYWI3YTdjYjJkOTRjY2M5OWY/
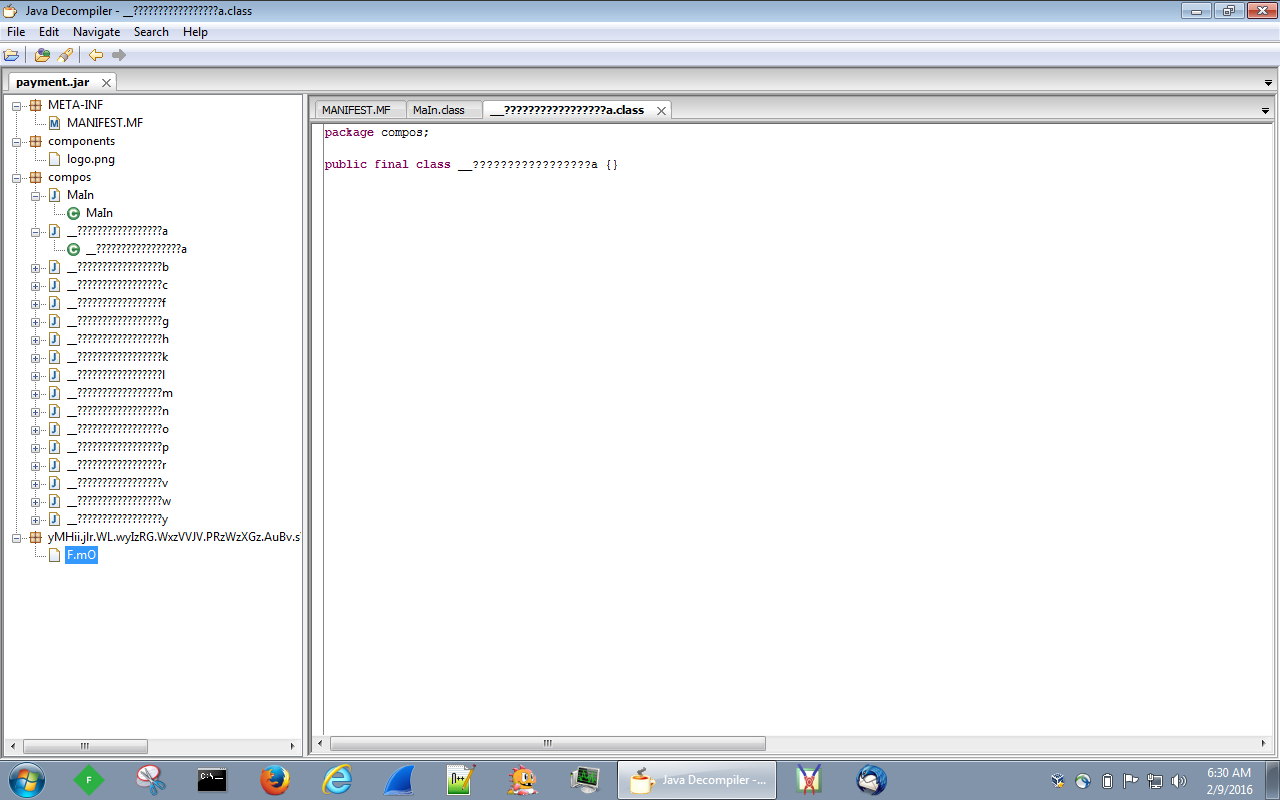
Since this is a Java file, I usually like to try and open these up using Java Decomplier to see if there is anything that I can gather or understand. Unfortunately in this case there was nothing that was coming back as you can see:
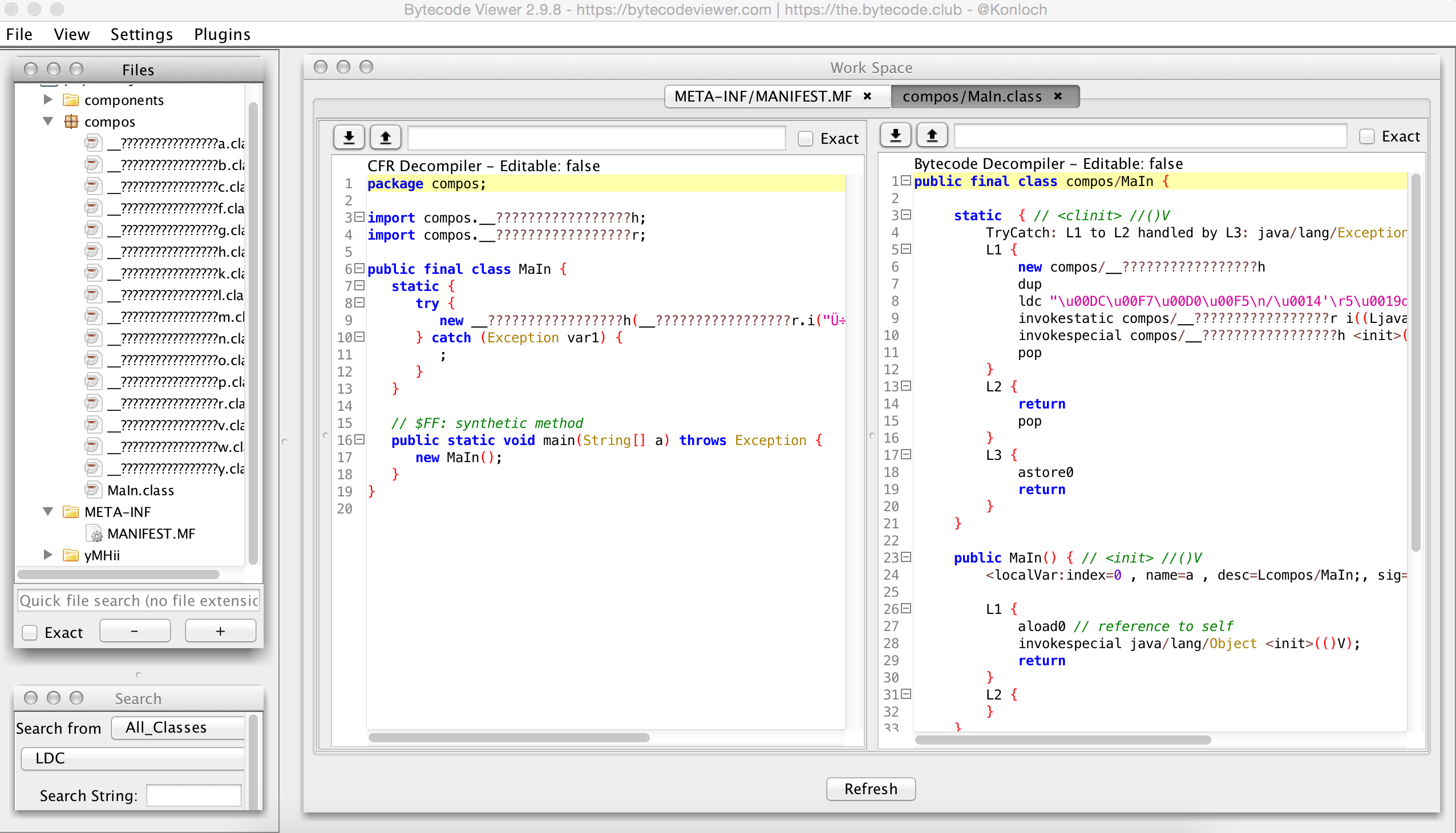
So after some Googling around looking for a Java deobfucation tool I came across this one: http://bytecodeviewer.com/. I did not really play around much with this tool (or any other RE suite for that matter), but this one did give me some more information about the JAR file that JD-GUI did not:
Just skimming thorugh the file I am not seeing alot that I understand, but some that I do. Using one of the plugins from Bytecode Viewer (the Malicious Code Scanner plugin), I did get back these two lines (which I did see while looking through all the parts of the JAR file):
Found Method call to java/net/URLClassLoader.<init>(([Ljava/net/URL;)V) at compos/__?????????????????l.<init>(([Ljava/net/URL;)V) Found Method call to java/lang/reflect/Method.invoke((Ljava/lang/Object;[Ljava/lang/Object;)Ljava/lang/Object;) at compos/__?????????????????y.i((Ljava/lang/reflect/Method;)V)
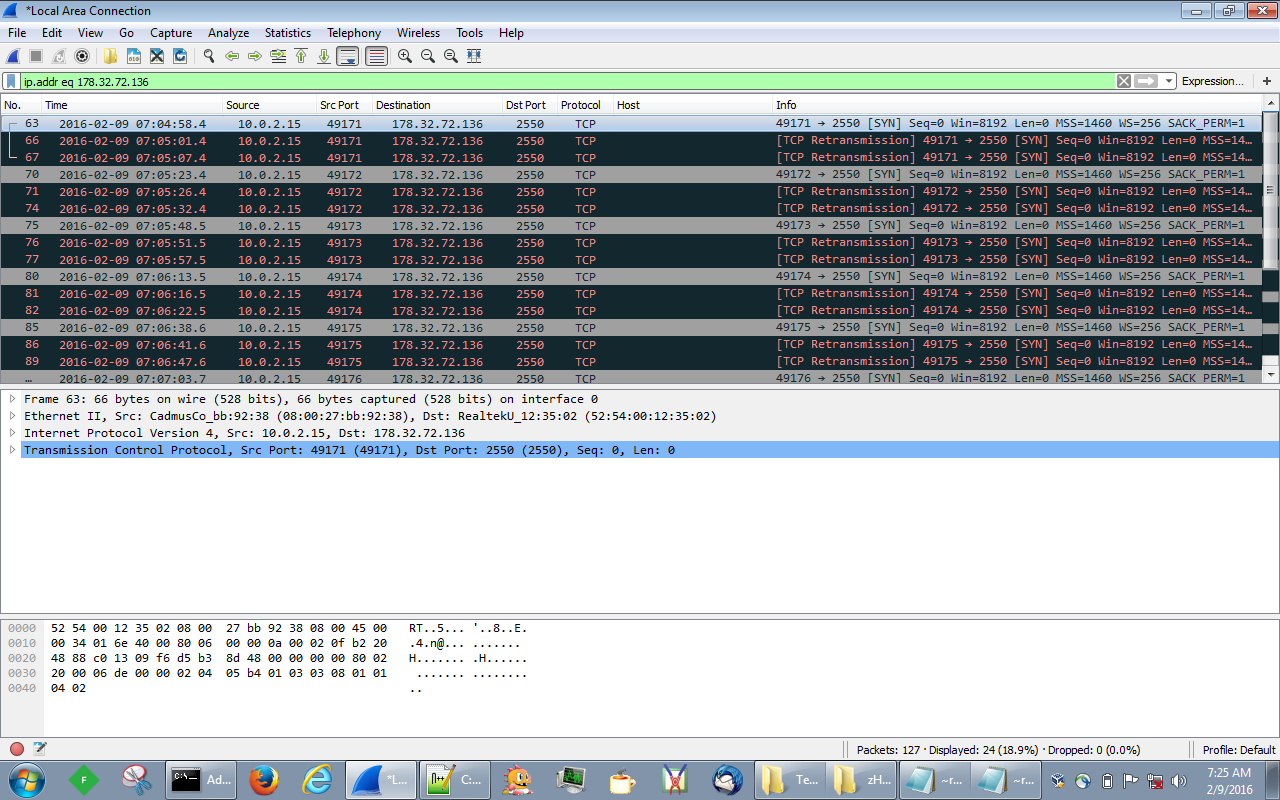
Since I did not see any URL’s or anything of that sort, it is time to run this in my VM and see what the traffic looks like. Initially there is a DNS lookup for the domain of ‘myson123456[.]ddns[.]net’ which points to the IP address of ‘178.32.72.136.’ That IP is registered for the OVH ISP in France:
http://www.robtex.com/en/advisory/ip/178/32/72/136/ inetnum: 178.32.72.128 - 178.32.72.159 netname: OVH_45490887 descr: OVH country: FR org: ORG-JD14-RIPE admin-c: OTC2-RIPE tech-c: OTC2-RIPE status: ASSIGNED PA mnt-by: OVH-MNT created: 2013-07-01T15:35:19Z last-modified: 2013-07-01T15:35:19Z source: RIPE # Filtered
I looked around to see if there was anything more on the web for this IP address and I did managed to find some hits over at Malwr – unfortunately nothing that shared the same hash was found. Moving on, once the DNS query had completed, it then tried to connect the malicious site on port 2550 which it looks like may have been fixed since the callback is never fully realized as you can see below:
Now even though my system never made contact with the malicious server from above, I did get some interesting artifacts left on the system. As you can see from the results of the RegShot run, some files/folders/regkeys were created. The ones that stood out to me are:
HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Microsoft\Windows\CurrentVersion\Run\ASHBmwvDjsJ: ""C:\Users\Administrator\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\Administrator\zHOYGzgpAKk\FkJvAfWLwXQ.STRnwH"" C:\Users\Administrator\zHOYGzgpAKk\FkJvAfWLwXQ.STRnwH C:\Users\Administrator\zHOYGzgpAKk\ID.txt
The file “ID.txt” only has the following in it: “{“UUID”:”24f3cf4e-c2d9-4194-9251-4a3dc3cfe709″}.” Looking around I was not able to figure out what exactly this ID means. Maybe something to do when the whole infection chain is up and running.
The other file (FkJvAfWLwXQ.STRnwH) that was created under the “zHOYGzgpAKk” folder looks to be the same Java file as the “payment..jar” file just named differently. The size of both files and the hashes are identical. Once again, why the Java file would be pulled out like it has is beyond me at this time.
Also, when running the Java file, the only process that seemed to kick off was “C:\Users\Administrator\AppData\Roaming\Oracle\bin\javaw.exe -jar C:\Users\Administrator\zHOYGzgpAKk\FkJvAfWLwXQ.STRnwH” as you can see below in the video.
To check out the Java file to see if you can de-obfuscate it and the PCAP for this example please click here. The password for the zip archive is “herbiegoesbananas.” Enjoy!