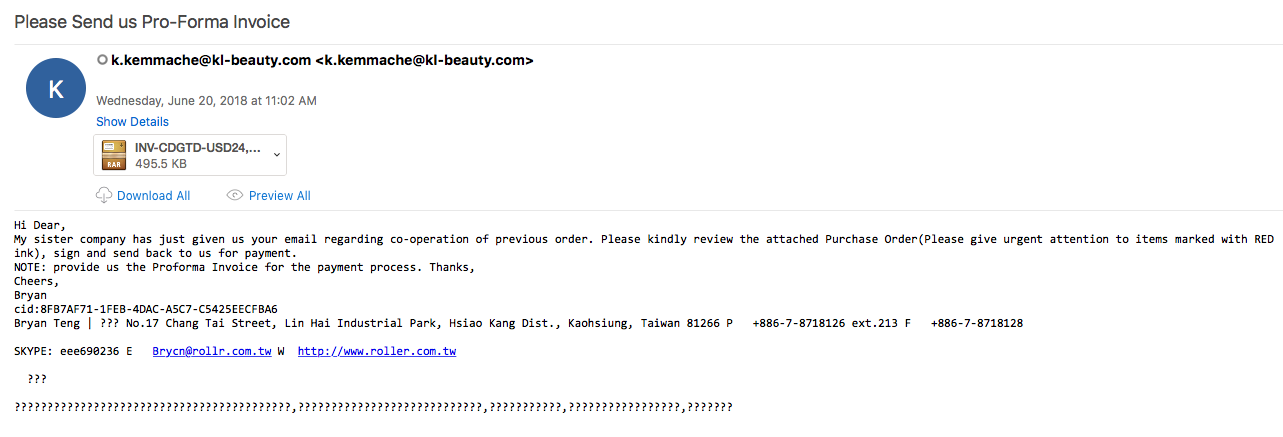
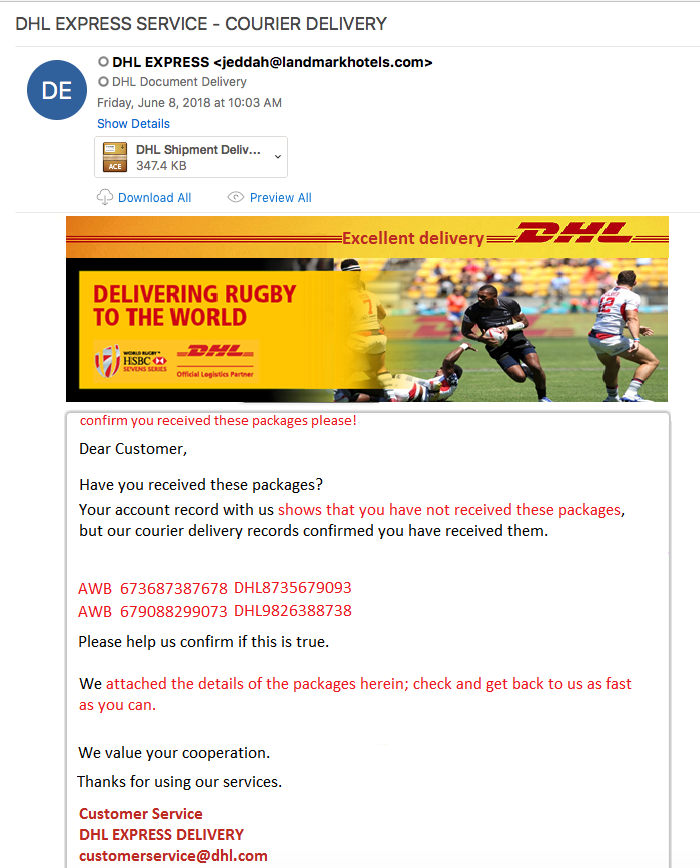
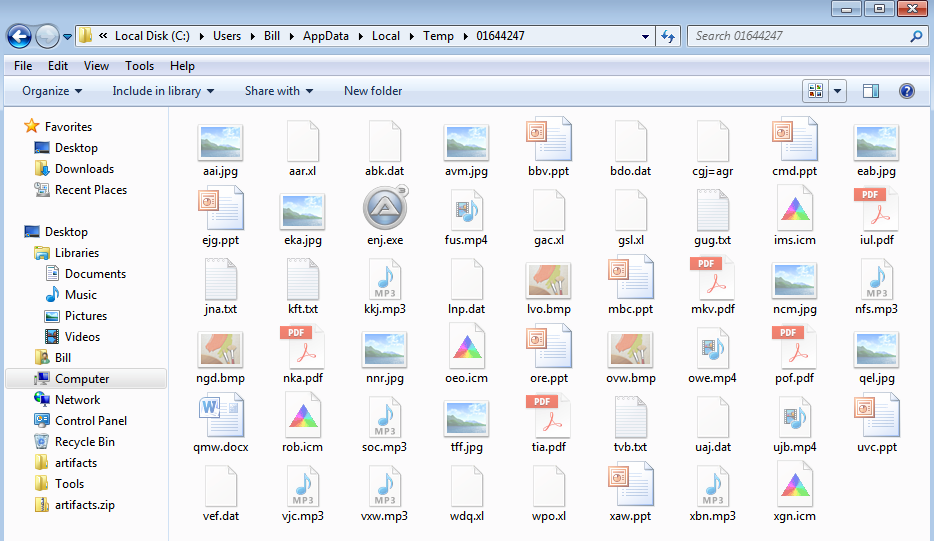
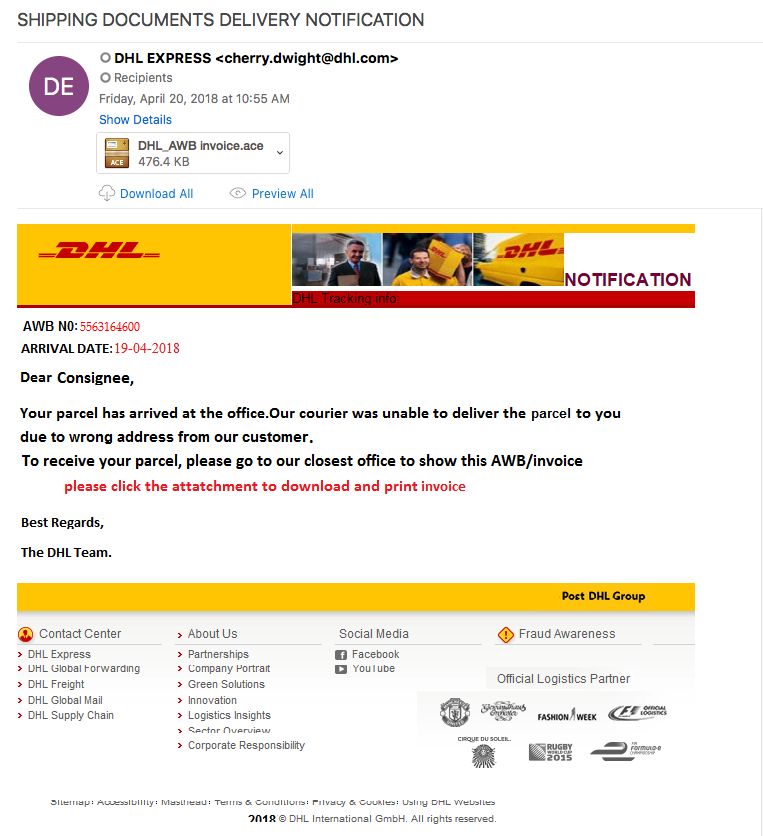
2018-09-18 Emotet maldocs labeled as “Invoices”
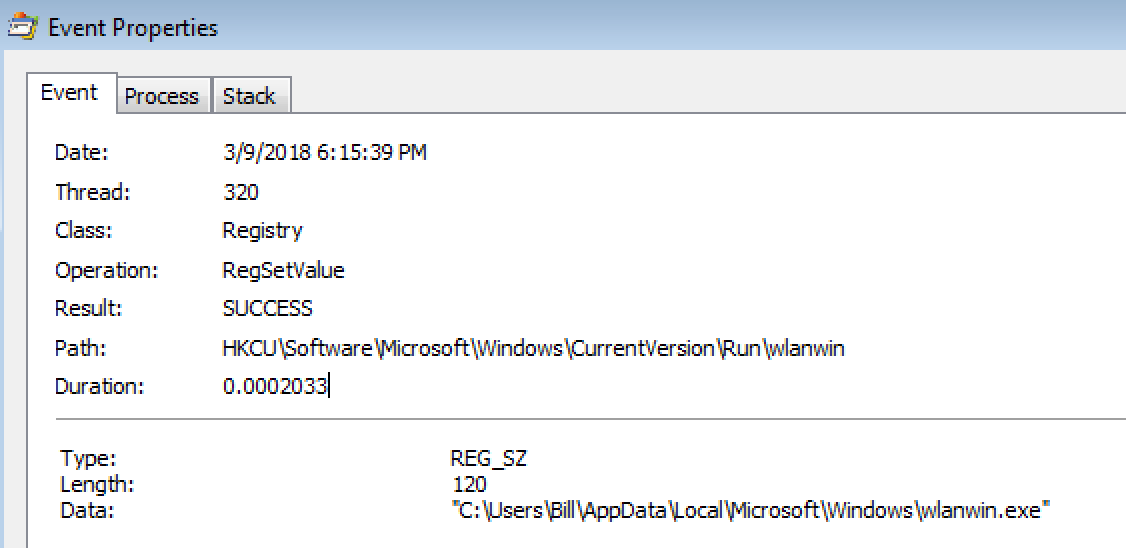
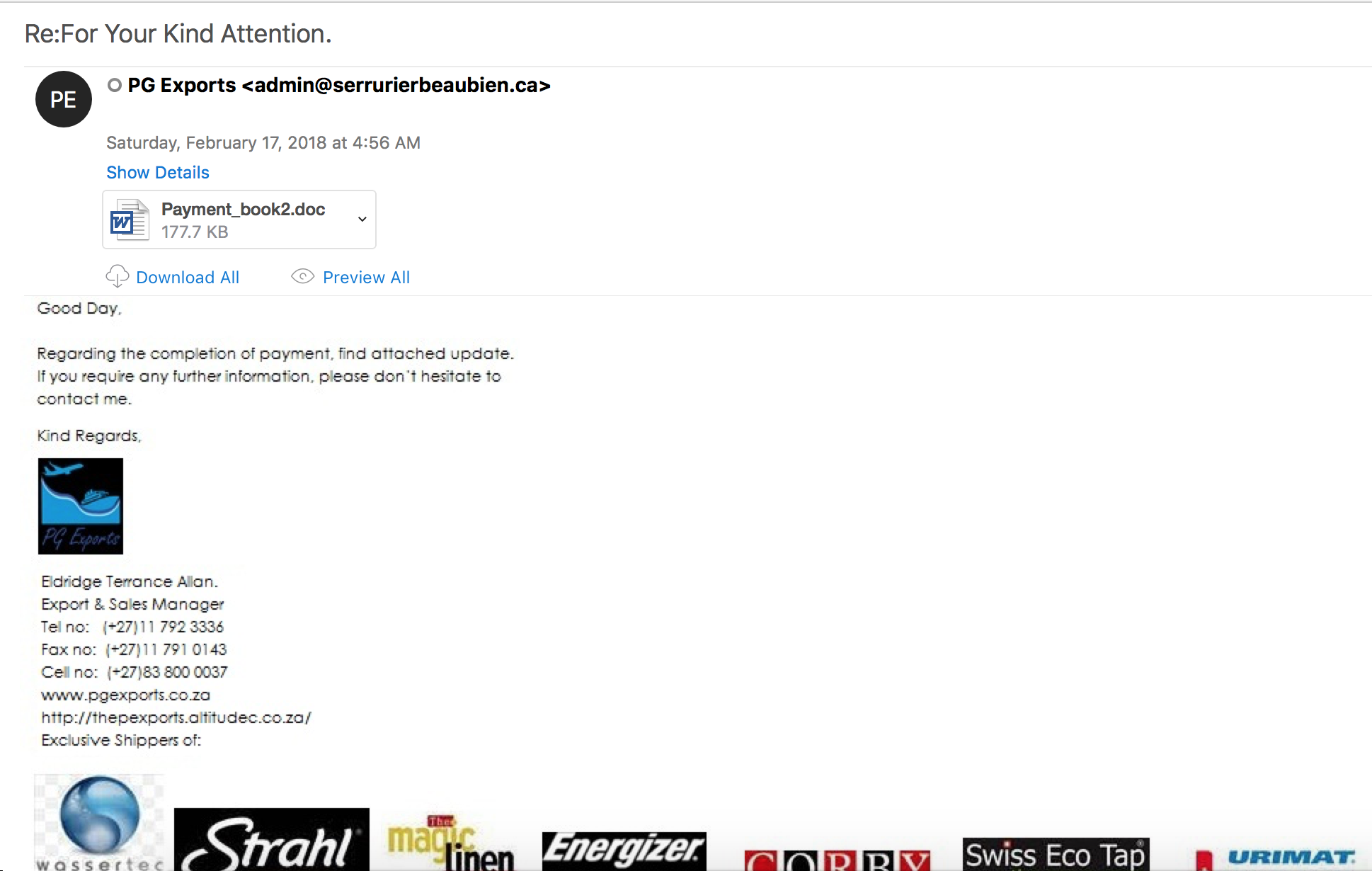
Looking through the email filters in on the 18th of September, I managed to find a small batch of emotet emails from the same sender. The emails themselves tried to spoof email addresses, but Outlook ended up displaying both emails (the spoof and the true sender). Looking through the small batch of emails, there were 2 different sets of hashes for the attachments. Below is the table showing the MD5 hashes associated with the maldoc: The artifacts from this can be found over in my Github found here. Another security researcher that has been activly maintaining emotet data (http://twitter.com/ps66uk/status/1042004723866509313) and…