A quick write-up on this Remcos malspam. Some other previous entries that I have done aboutr Remcos can be found below:
http://www.herbiez.com/?p=1106
http://www.herbiez.com/?p=1073
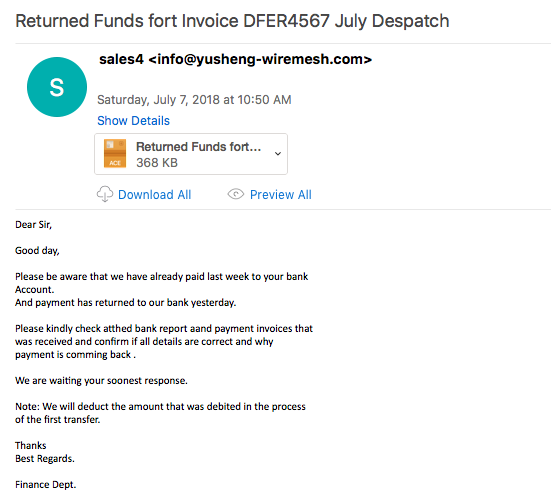
All the emails seem to come from the sender info@yusheng-wiremesh.com with the subject of “Returned Funds fort Invoice DFER4567 July Despatch.” The malspam also comes with an ACE attachment, that when extracted out, gives us the following binary: “Returned Funds fort Invoice DFER4567 July Despatch.exe.” A quick glance at some of the emails shows that they are all being sent from this IP address: 185.163.111.81 which shows a rDNS entry of “sv2.sendomail.eu” out of Romania.
One thing to note here is that this sample did not reach back out when I ran this in Any.Run. Yet when looking at my VM, I got consistent callbacks to the C2 server.
For the artifacts from this investigation, please see the repo here.
IOCs:
=====
77.48.28.227:2442 (TCP)
Artifacts:
==========
File name: Returned Funds fort Invoice DFER4567 July Despatch.ace
File size: 272KB
File path: NA
MD5 hash: 00b683bb28daca30ce497a150622b1e3
Virustotal: http://www.virustotal.com/#/file/b0a643049639f302e83d7bf10821d1fee0e9cf9e9cba036ba349fe54fc71b011/detection
Detection ratio: 8 / 60
First Detected: 2018-07-07 07:08:09
File name: Returned Funds fort Invoice DFER4567 July Despatch.exe / notepad.exe
File size: 615KB
File path: NA
MD5 hash: 79457a7242ec2d7942ace7c4f1229cfc
File path (notepad.exe): C:\Users\%username%AppData\Roaming\windows
Any.Run: http://app.any.run/tasks/f9b778a3-7f2a-4e7d-9f4d-3533dcb71e7c
File name: windows.vbs
File size: 121B
File path: C:\Users\Bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\
MD5 hash: e0a8777bd0b5123f8f42626d80326a45
Analysis:
=========
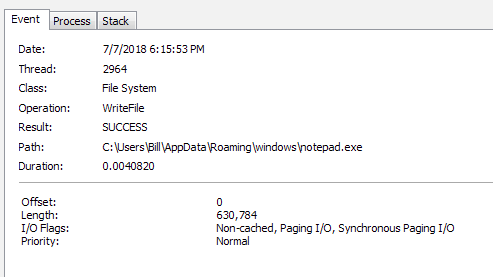
From the host perspective, the user is tricked into opening this file by posing to need the user to check the “atthed [sic] bank report aand payment invoices” to kick off the infection chain. Once that happens, the process kicks off (Returned Funds fort Invoice DFER4567 July Despatch.exe – PID 2896), which proceeds to copy itself with a rename operation (renamed to notepad.exe) to the path of C:\Users\%username%AppData\Roaming\windows (PID 1660).
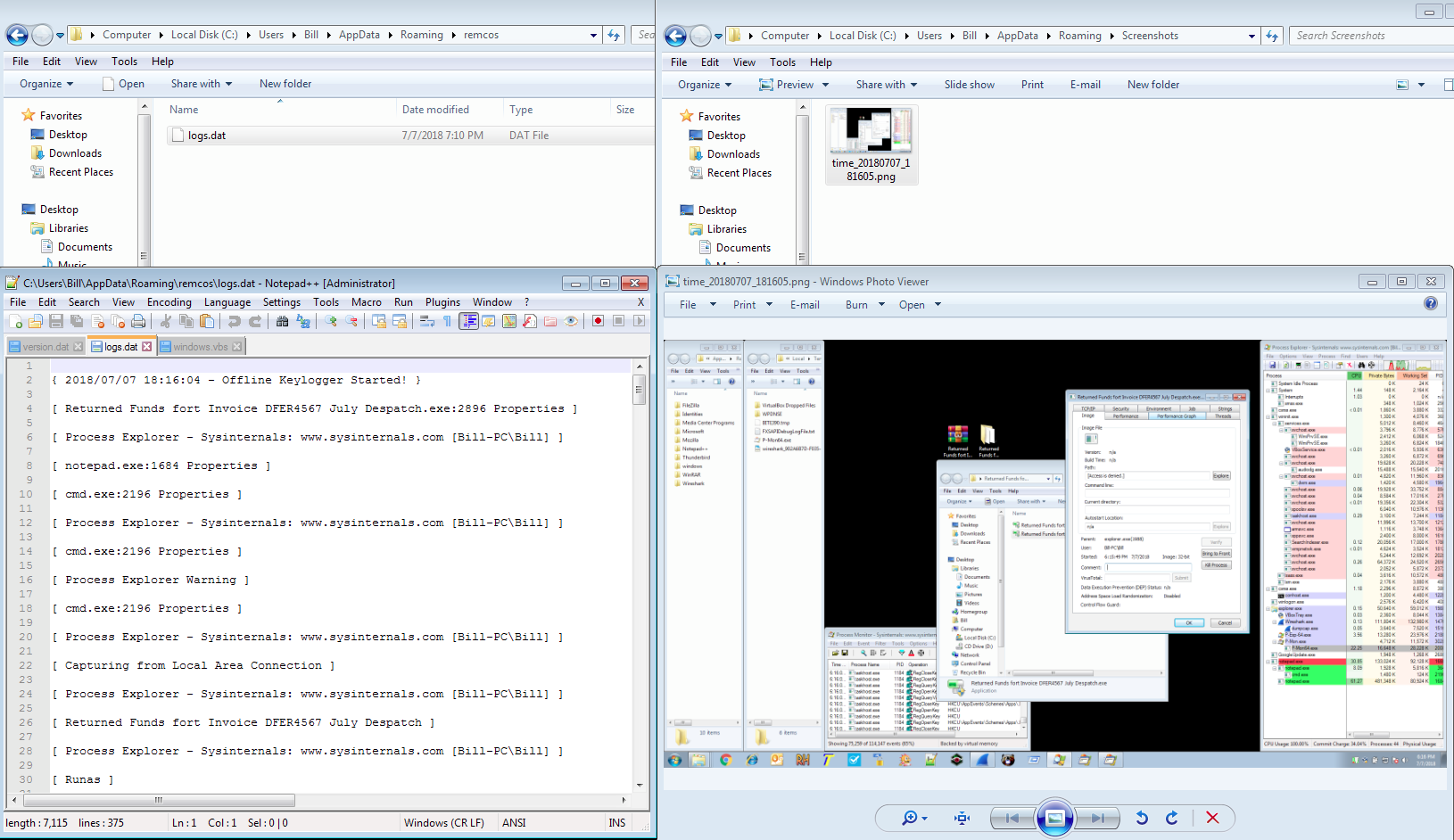
From here, notepad.exe (PID 1660) creates two other instances of itself with one of them spawning a cmd.exe (PID 2196) and reg.exe (PID 2672) processes to add the following registry key: “C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f.” The other notepad.exe process (PID 1660) creates the Windows startup VBS file in “C:\Users\Bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\”, a key log file, and also what takes screen caps of the desktop as well. The location of those files are “C:\Users\Bill\AppData\Roaming\windows” (this is for the screen shots) and “C:\Users\Bill\AppData\Roaming\remcos” (this is for the key logging file).
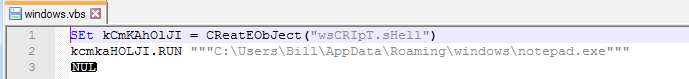
As far as persistance is concerned, that is obtained via the “windows.vbs” file created above which points to the malicious “notepad.exe” file.
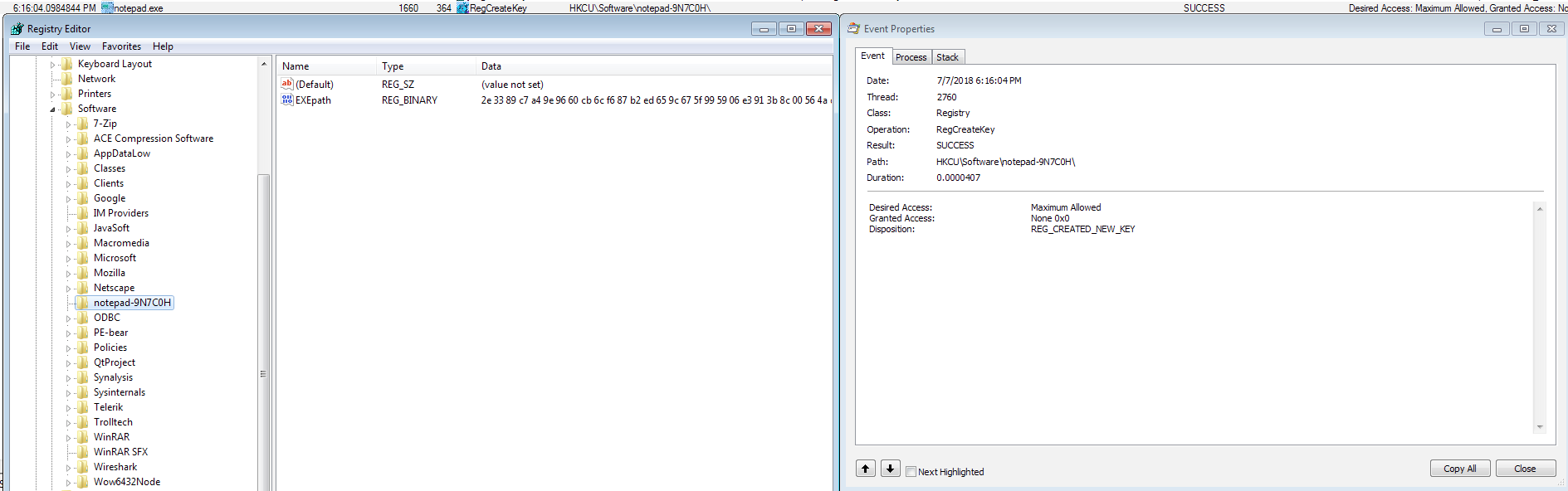
I also came across the the following registry key, but I am not sure what exactly this is for. Possibly the hex encoded path to the malicious “notepad.exe” file.
From a network perspective, there is not much to this infection. Once the binary is run, it connects to the IP address of 77.48.28.227 on port 2442 (TCP). The communication looks to be encoded/encrypted so nothing can be made from looking at the different streams. Considering that there was only this callback being made, I can safely assume that the infected system was sending the updated key stroke logs and the screen caps to the c2.