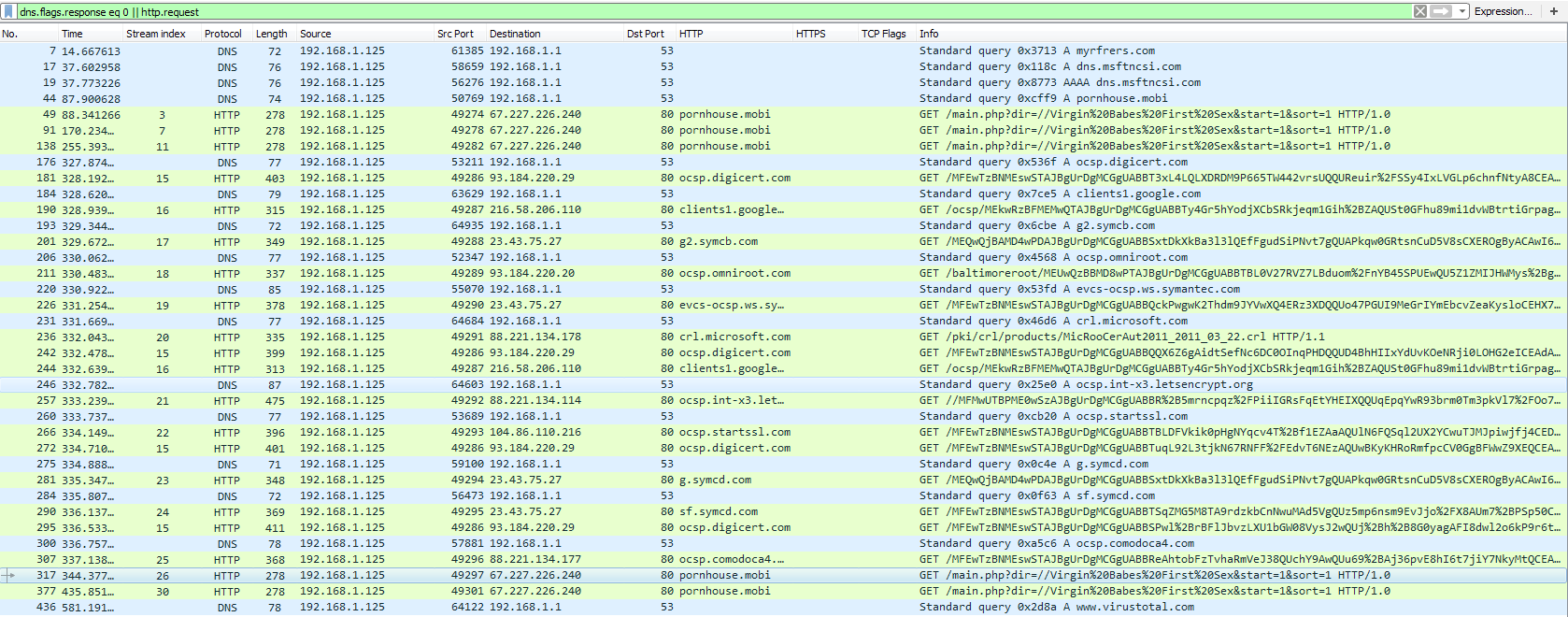
Found some malspam that looks to be Pony/Fareit related. Generally speaking, Pony/Fareit deals with credential stealing varying from FTP to email clients and any other credential that it may be able to obtain. The results that I got from my VM are different than what I got from Any.Run and Payload Security. For example, on my VM it did not reach out to “myrfrers[.]com” domain, nor did the Any.Run sample try to reach out to the “pornhouse[.]mobi” domain. I also did not see anything from the limited run of ProcMon relating to any FTP sites, or anything trying to obtain credentials. Makes me wonder if this was, possibly, VM aware perhaps. Anyways…
The artifacts from this investigation can be found over at my Github repo located here.
IOCs:
=====
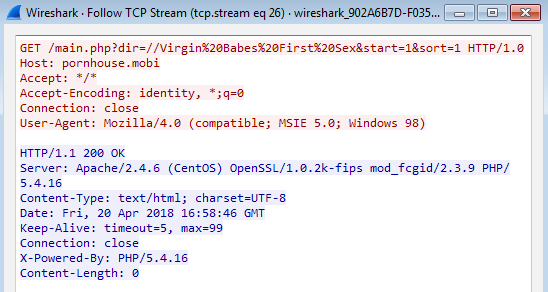
67[.]227.226[.]240 / pornhouse[.]mobi (GET /main.php?dir=//Virgin%20Babes%20First%20Sex&start=1&sort=1 HTTP/1.0)
Artifacts:
==========
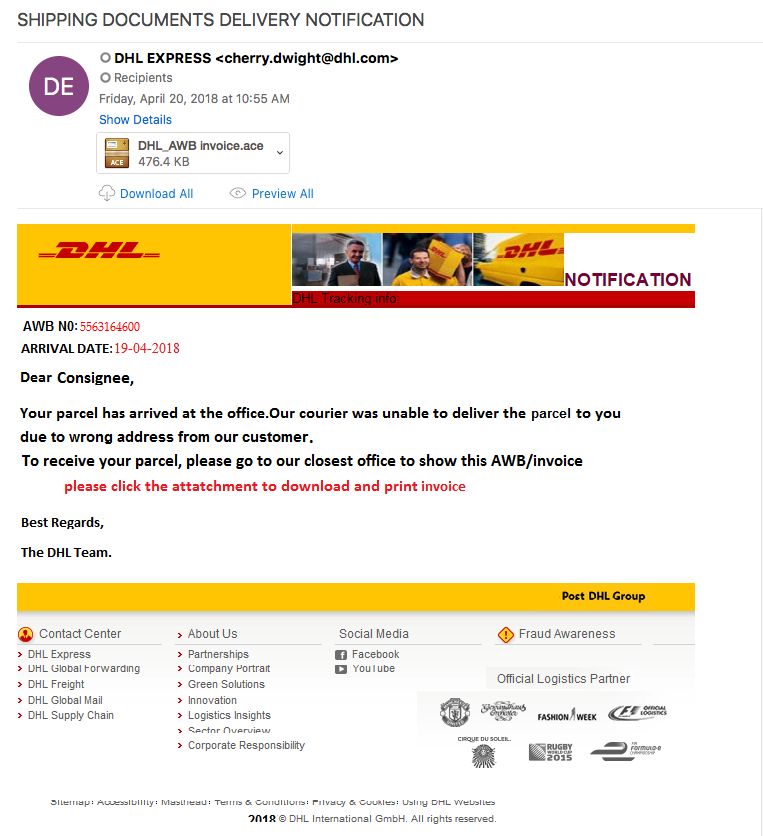
File name: DHL_AWB invoice.ace
File size: 361KB
File path: NA
MD5 hash: 1a8b1c6a01679c78b0bb0ec701a17299
Virustotal: http://www.virustotal.com/#/file/3b04d16d9bdad64afd5acfeca0e94d228ba481d00535ba9622daa111d81fa20b/detection
Detection ratio: 2 / 59
First Detected: 2018-04-20 11:02:07
Hybrid Analysis: NA
File name: DHL_AWB invoice.scr
File size: 830KB
File path: NA
MD5 hash: 2df397766a1d4c2cfc0878d0f06e017c
Virustotal: NA
Hybrid Analysis: http://www.hybrid-analysis.com/sample/0161db0f1201509c9a5ab91ce20974f4d239a3d55915fd81e39177835f2af623?environmentId=100
Any.Run: http://app.any.run/tasks/f798e581-cfb9-4225-866f-48870e8db8de
File name: 2207875.bat
File size: 94B
File path: C:\Users\%username%\AppData\Local\Temp
MD5 hash: 3880eeb1c736d853eb13b44898b718ab
Virustotal: http://www.virustotal.com/#/file/936d9411d5226b7c5a150ecaf422987590a8870c8e095e1caa072273041a86e7/detection
Detection ratio: 26 / 60
First Detected: 2012-12-18 22:56:31
Hybrid Analysis: http://www.hybrid-analysis.com/search?query=3880eeb1c736d853eb13b44898b718ab
Analysis:
=========
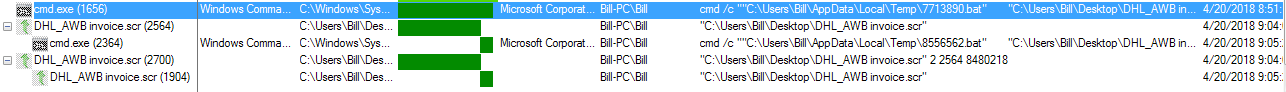
This was a simple infection that stemed from extracting out the malicious screensaver file from the ACE archive. Once the malicious screensaver was ran, less than a minute later went by and the process terminated itself while starting up some child processes (process hollowing). Once the malware took foot, what I saw was the screensaver run, then terminate, while then creating a new thread for “cmd.exe” as seen below.
Once the “cmd.exe” process had started, I noticed that there was a new file in the %TEMP% folder as well. The following is a cleaned up version of one of the batch files creeated.
:ktk del %1 if exist %1 goto ktk del %0
Timing the creation of the batch files with the PCAP, it looks like it may have been reaching out to the “pornhouse[.]mobi” site at the same time.
Letting this run for a bit, the same pattern continued with several of the same batch files, albeit random names, being created.
The interesting thing with this one was the fact that I could not run anything from SysInternals on my VM. If I ran either ProcMon or Process Explorer and then executed the malware, the binary would spawn a new process and then terminate quickjly afterwards. If I executed the malware and then started ProcMon, or Process Explorer after the fact, the malware would run for a while and then terminate.