For this post, I was able to find some Formbook malspam within the email filters. Formbook malware is considered to be a data theft/form grabber with some other add-ons under it’s tool belt. Based on the following deep dives into Formbook from FireEye (http://www.fireeye.com/blog/threat-research/2017/10/formbook-malware-distribution-campaigns.html) and ThisIsSecurity (http://thisissecurity.stormshield.com/2018/03/29/in-depth-formbook-malware-analysis-obfuscation-and-process-injection/), this malware sample follows the patterns described pretty closely (pay particular attention to the process injection section from FireEye).
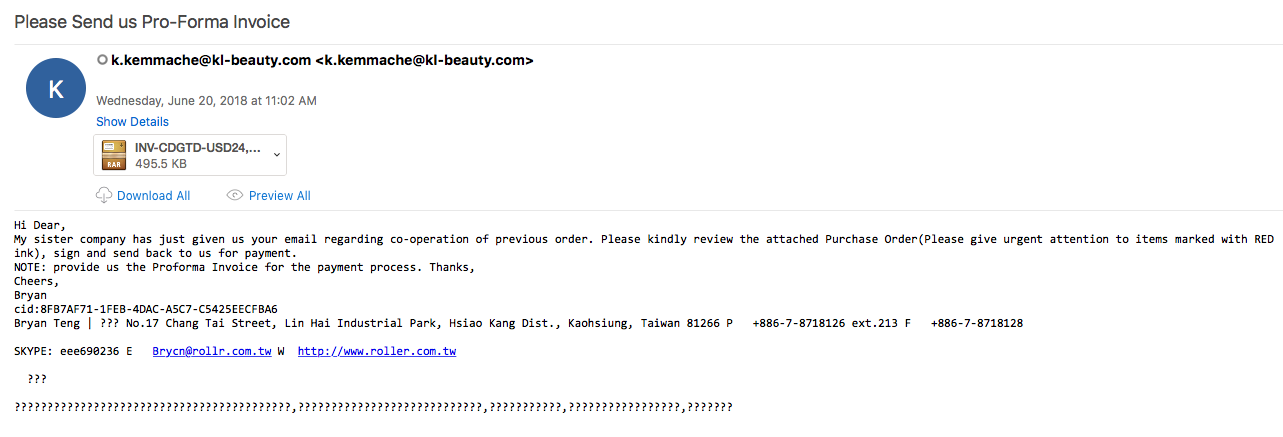
The email itself was about an invoice that needed to be reviewed. There was a RAR file as an attachment which, un-compressed, showed there was an EXE file inside. This is the file that starts the infection chain for a system. Note that the sample did not execute in my VM. I ran the sample through Any.Run before I ran it on my VM. I am suspecting since there was a couple of hours between the runs that the sites were taken down.
For the artifacts from this infection, please see my Github repo located here.
IOCs:
=====
199.192.19.10 / www.mudscript.com
185.199.108.153 / www.sadathetoure.com
141.8.224.93 / www.avaxt.com
198.185.159.145 / www.birdstreetbrewing.net
198.54.116.33 / www.macscloset.com
52.55.168.146 / www.onsemate.com
198.49.23.145 / www.squaredsites.com
116.196.79.203 / www.shaomg.com
185.149.101.223 / www.mirbedirhanhoca.com
52.220.246.251 / www.51meiry.com
217.160.230.166 / www.hmuon.com
185.53.178.7 / www.aigofx.com
117.21.246.43 / www.ncsay.com
Artifacts:
==========
File name: INV-CDGTD-USD24,876.rar
File size: 366KB
File path: NA
MD5 hash: bc0748270922a8ab68a30a465206e63b
Virustotal: http://www.virustotal.com/#/file/211c6c2b22af07776831abdc2a1e37e741753e23ff60a440c2810a5f6b596635/detection
Detection ratio: 12 / 62
First Detected: 2018-06-20 13:40:22
File name: INV-CDGTD-USD24,876-1.exe
File size: 443KB
File path: NA
MD5 hash: 048584be7ace5ebcc3e8dd96c62b947f
Any.Run: http://app.any.run/tasks/a7d9a466-48e7-44ee-b47a-5cadaa6b5723
File name: *.ini (numerous files)
File size: 40 B – 1.16 KB
File path: C:\Users\admin\AppData\Roaming\9KRM6P1E\
File name: 9KRlogim.jpeg (screen grab of the VM’s desktop)
File size: 65.31 KB
File path: C:\Users\admin\AppData\Roaming\9KRM6P1E\
Analysis:
=========
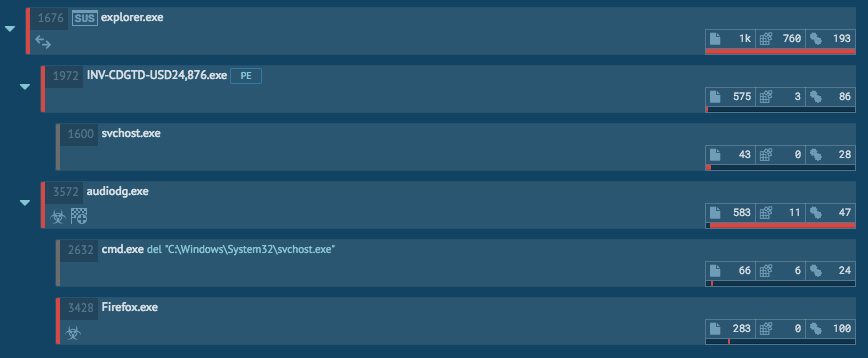
Overall, the blogs mentioned above do a great job at digging into this malware and how the malware works. As seen from Any.Run, this sample is pretty straight forward. The malicious executable makes a call to svchost.exe which does nothing during the run in Any.Run.
The bulk of this infection stems from the process “audiodg.exe” and “explorer.exe.” The “audiodg.exe” process writes the persistence via the “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” key and the value of “C:\Program Files\Sbv14dbmx\audiodg-zbxn.exe.” It is also the process that creates the various “ini” files and the screen grab as well in the “C:\Users\admin\AppData\Roaming\9KRM6P1E\” directory. The now hijacked “explorer.exe” process is the process responsible for calling back out to the many different domains via a GET request or a POST request. Based on the run in Any.Run, it looks like most of the sites were already taken down. Below is a list of the requests made during this run with a hit count.
1 - hxxp://www[.]51meiry[.]com/th/?ATg4aR5=AxbWMFMHDw4EBVF1B7BCDa9YvjaqjNryUnLX8/Vi/2zeaphvG8mDFy4YVW7gL5yfZRDOIQ==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]aigofx[.]com/th/?ATg4aR5=YgJn6M23O184JITVxCH4t/A6dUK3QzatpvWIa52uJi07q+EHFU9TM+zLCDIlYBLc4Y93mQ==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]avaxt[.]com/th/?ATg4aR5=Em5eipXC+A2rxop0YwcdUPq/svqQgZuXTWOt2jFA/0BWWMZcK8CmzkzZmgxY0QBiEYjliQ==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]birdstreetbrewing[.]net/th/?ATg4aR5=wE+jSZkoT4i2e3JnW/nxBxQonnxMGGQqLkwhHN3bdjRlHjqhsE877V5sgQm7UhpUYU/IDg==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]hmuon[.]com/th/?ATg4aR5=T8F2pkaEKre0S/s4HGBFiETgDvK0MN1mS2kyEBPVy49PisPBb7n2N0qYMHiu4noBOAlEsA==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]macscloset[.]com/th/?ATg4aR5=vAqRS9A/EqMZoM7xHj+j3kuIBa6PjqWGs8dkL7BkjDXB5CYqN0fgu8Me5XqximC4na0AMQ==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]mirbedirhanhoca[.]com/th/?ATg4aR5=c33cIB+JWIiB2NhXN/+swPXPYo2Bo67Rhl5YXZS3si6DP49a1rRNS78DgdUcgE/J8qYQ6g==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]mudscript[.]com/th/?ATg4aR5=VuBe39zCByKcbrr5O7Uanufpt/+dg1gZW6HYrMLjT28gqoOb75gZzvkClklYXrcgMsXctA==&4hG=vDzxV4Kx-27pYLM (GET) 1 - hxxp://www[.]ncsay[.]com/th/?ATg4aR5=55semPEhYYF7HuiSi7kakHQUOeYPK380LGHvSOhGOFvDIH0QAjKiSL+GMEhA2mQLDU3AIQ==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]onsemate[.]com/th/?ATg4aR5=Qs2NO/ubEQTSbK8yFdklFGL1OCjqfVmyQksysplU0KOKI6+0M5Kj4YPR5Af73voi3xD9hg==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]sadathetoure[.]com/th/ (POST) 1 - hxxp://www[.]sadathetoure[.]com/th/?ATg4aR5=f+Zm2Ciu5+aHNOHXocw2SUt+MQwcumEns8o4PY6drS3OODfITuh5HuydDYViqJ++tdPfLA==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]shaomg[.]com/th/?ATg4aR5=dsfu96VtAt0weO7NxW8JQ3l4aOEdSx/YEa7XXrempzV6nYFRbTGvogMj+T7vDAFNlInisA==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 1 - hxxp://www[.]squaredsites[.]com/th/?ATg4aR5=25+8Kf8r0A+1Rcg7v0m83q+66JQN/FtBl478Lu+zNBQePNH2ZPIr13clC+cvlqstIBLcVA==&4hG=vDzxV4Kx-27pYLM&sql=1 (GET) 2 - hxxp://www[.]51meiry[.]com/th/ (POST) 2 - hxxp://www[.]aigofx[.]com/th/ (POST) 2 - hxxp://www[.]avaxt[.]com/th/ (POST) 2 - hxxp://www[.]birdstreetbrewing[.]net/th/ (POST) 2 - hxxp://www[.]hmuon[.]com/th/ (POST) 2 - hxxp://www[.]macscloset[.]com/th/ (POST) 2 - hxxp://www[.]mirbedirhanhoca[.]com/th/ (POST) 2 - hxxp://www[.]onsemate[.]com/th/ (POST) 2 - hxxp://www[.]shaomg[.]com/th/ (POST) 2 - hxxp://www[.]squaredsites[.]com/th/ (POST)