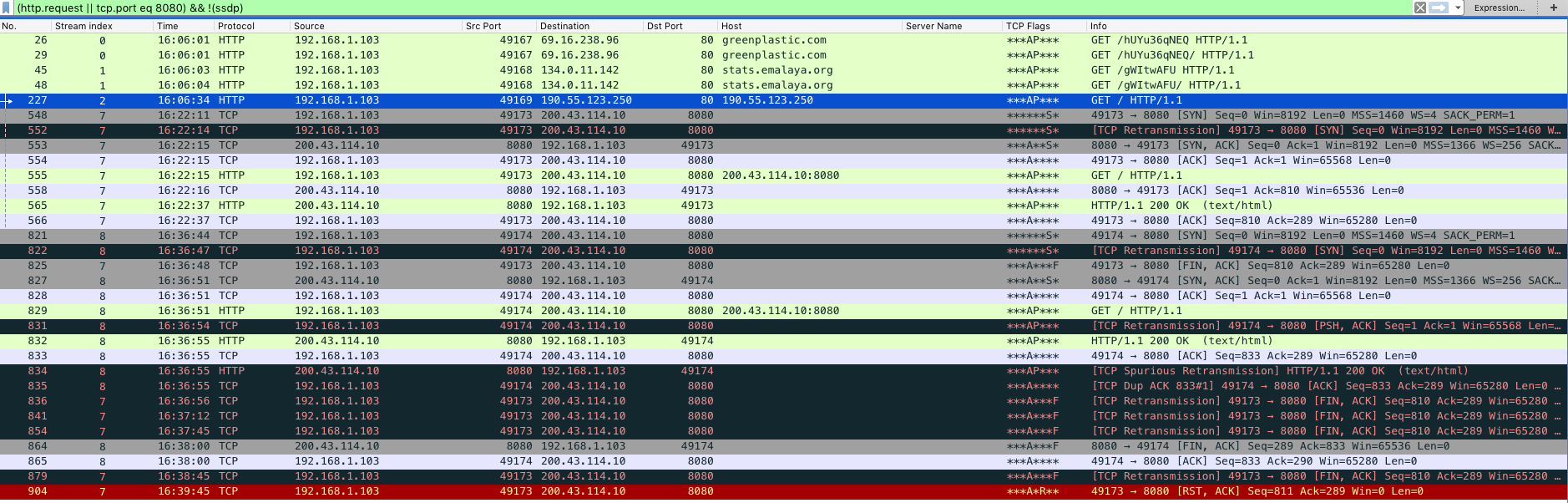
2020-04-06 Qealler RAT Malspam
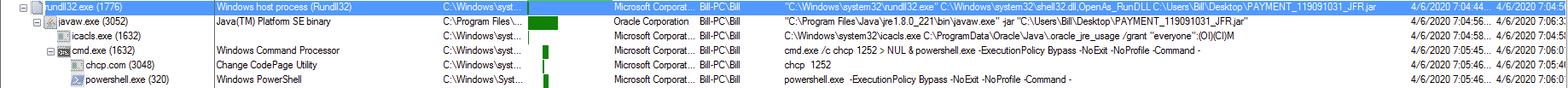
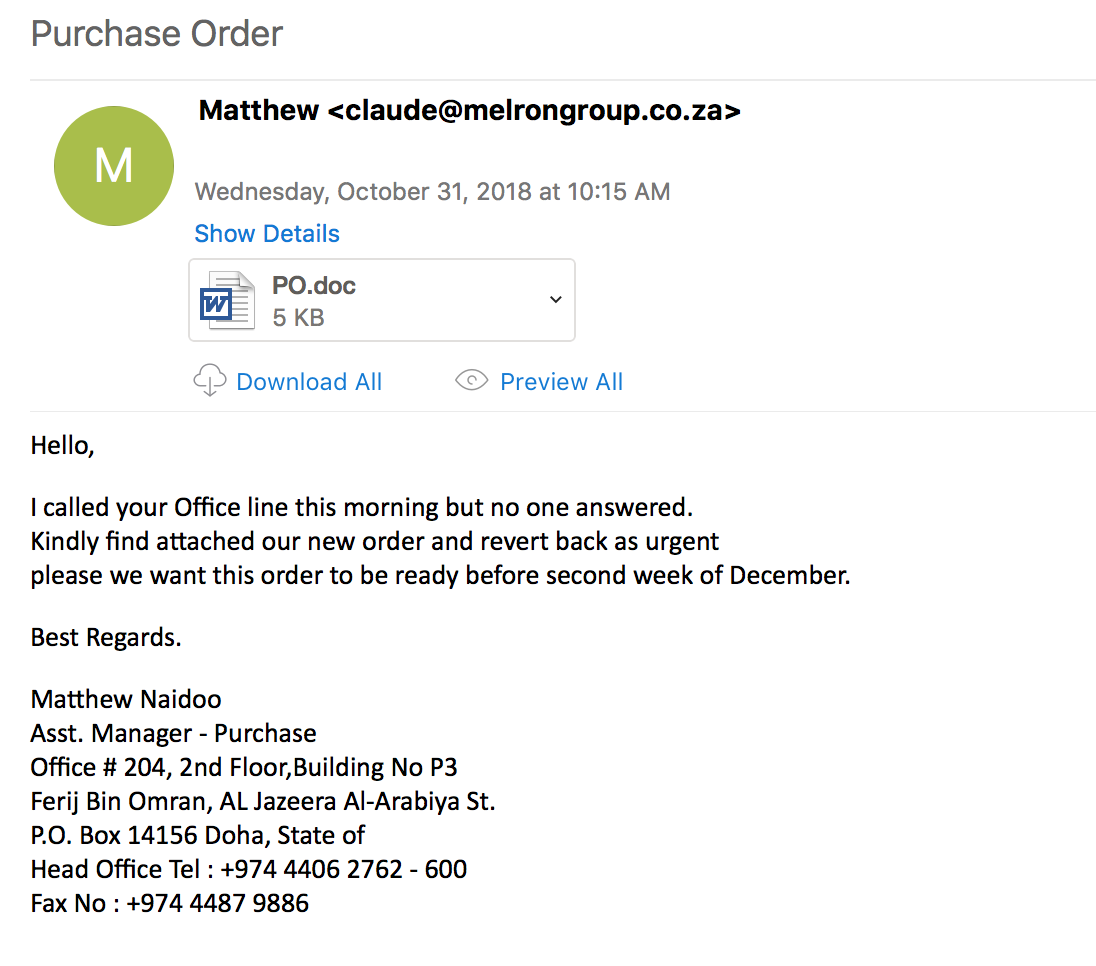
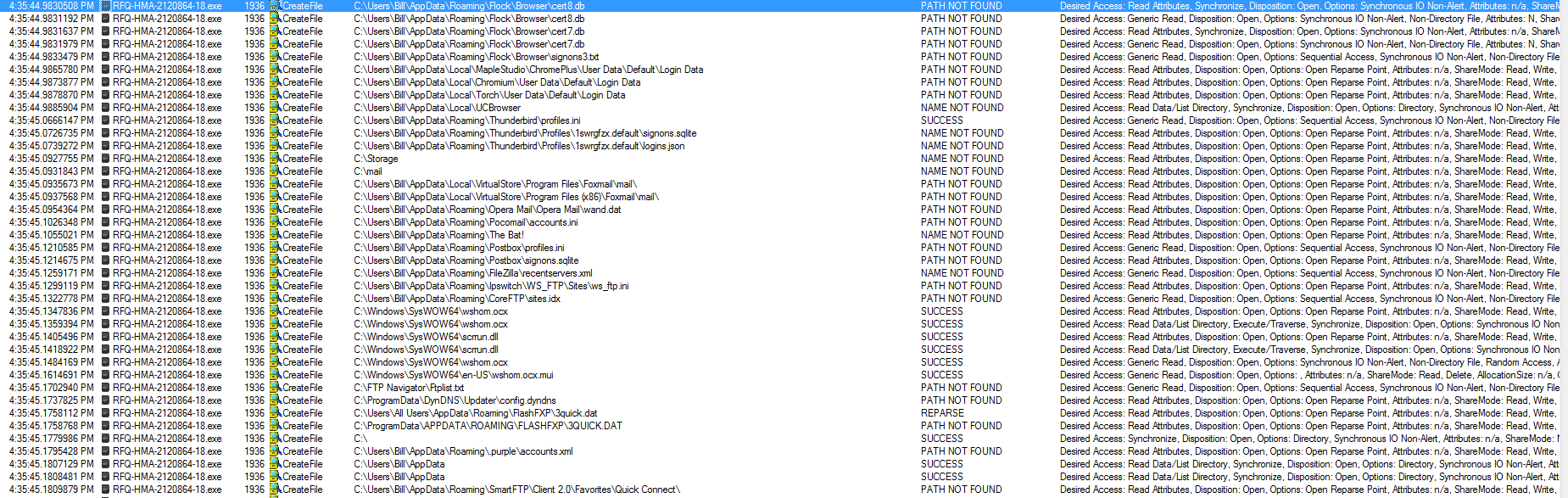
Meta ===== From: Bharti Ladwa Subject: EFT Supplier Number: 0003697 Link in the email: hxxps://jfreecss.co.uk/ Malware type: Qealler ———————- Basically this is a Java RAT. Below are some additional resources that explain how this type of malware works. http://www.zscaler.com/blogs/research/qealler-new-jar-based-information-stealer http://securityboulevard.com/2019/10/hiding-in-plain-sight-new-adwind-jrat-variant-uses-normal-java-commands-to-mask-its-behavior/ http://www.securityinbits.com/malware-analysis/pyrogenic-infostealer-static-analysis-part-0x1/ Earlier today I came across a phishing email that had contained an embedded image which had a malicious link in it. Once it was clicked on, the site automatically redirected to another site which then proceeded to download a JAR file. I tried to deobfuscate the Java code in my VM but did not get anywhere fast. Knowing that…