Malware Exercise 2015-10-13 – Halloween-Themed Host Names
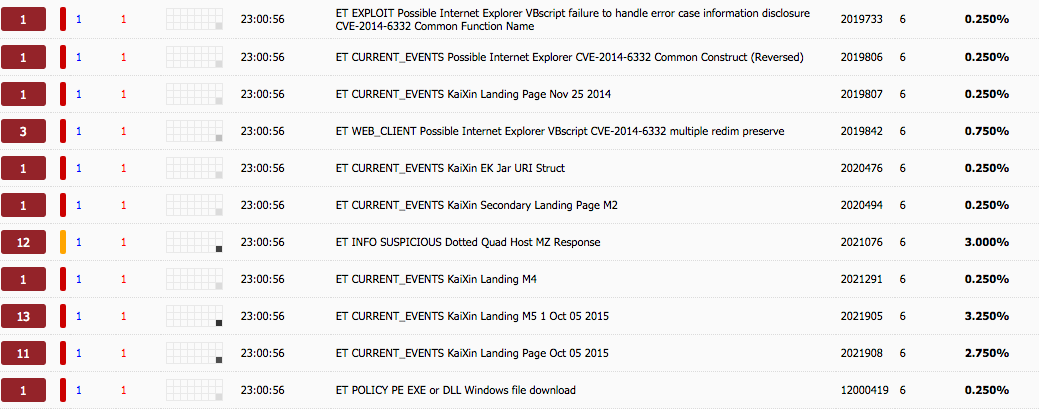
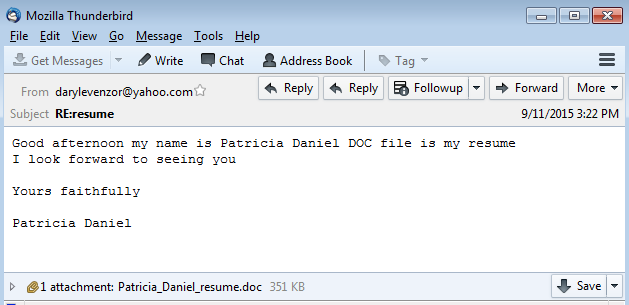
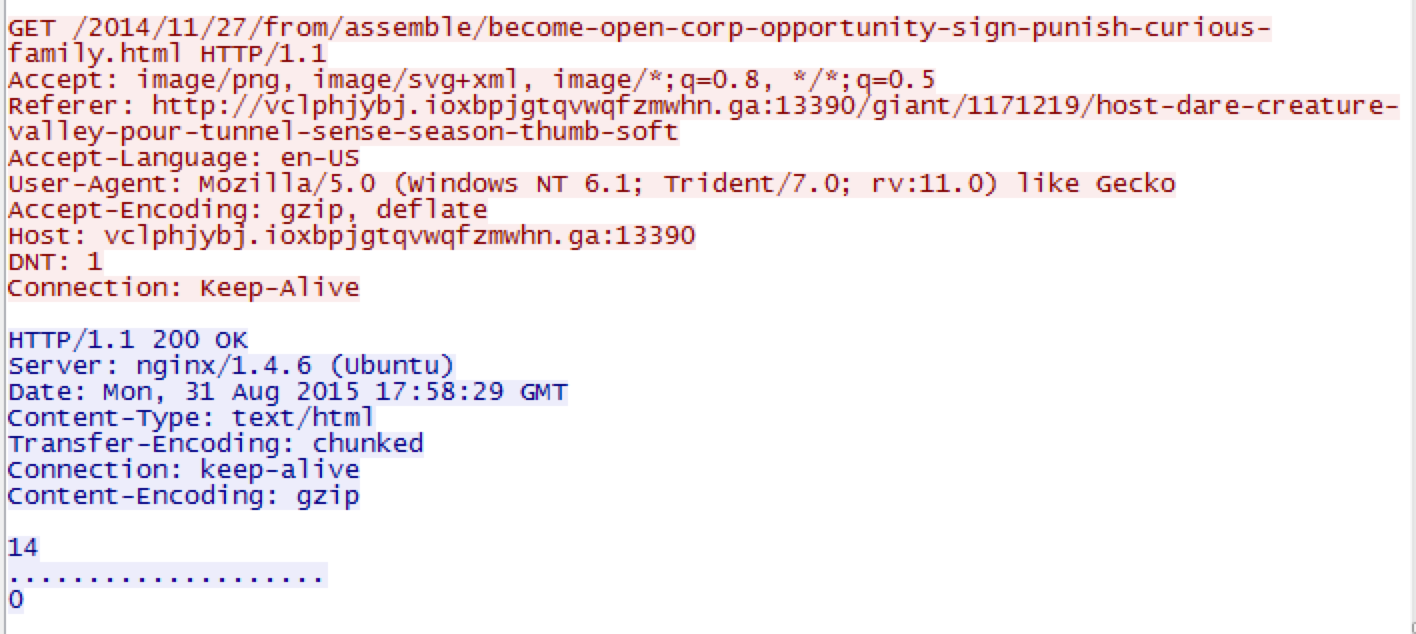
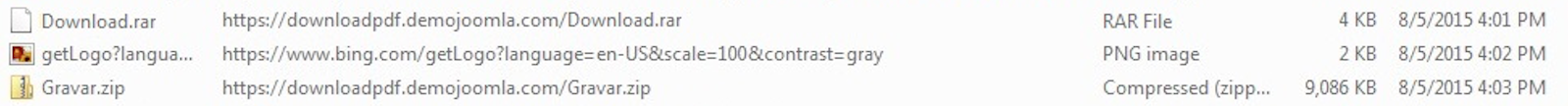
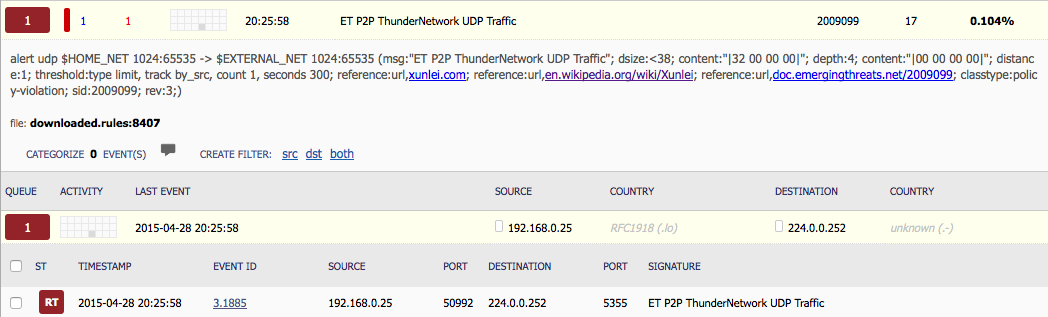
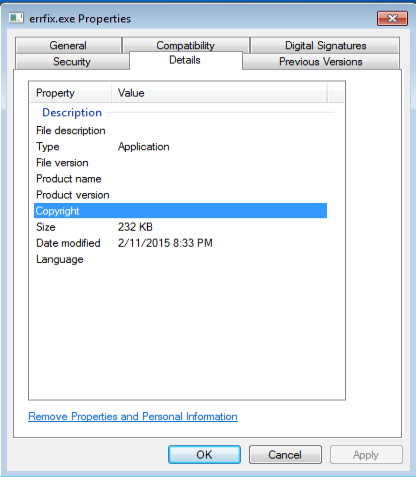
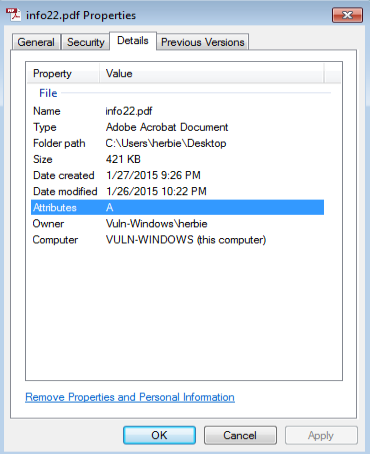
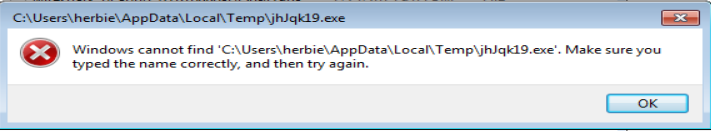
Just posting my write-up of another one of Brad’s exercises. You can find the answers to this exercise from Brad here. The other interesting bit that I came across while researching different aspects from this exercise was another researcher that had worked on the same one as well. Check out his blog here, or his Twitter feed here. Here are my results from this exercise. – Date and time of the activity. > User1 = 10.12.2015 18:55 – 19:10 > User2 = 10.12.2015 23:30 – 23:39 – The infected computer’s IP address. > User1 = 10.0.15.202 > User2 = 172.16.95.97…