As the title suggest, this is the continuation of my investigation into a malicious Dyre email that I received a while back. If you did not see my initial post (and mind you, first blog about malware analysis), then you can find that here. The other thing that I am going to do is use a new tool created by Omri Herscovici called CapTipper. For more information about this tool, check out his page here.
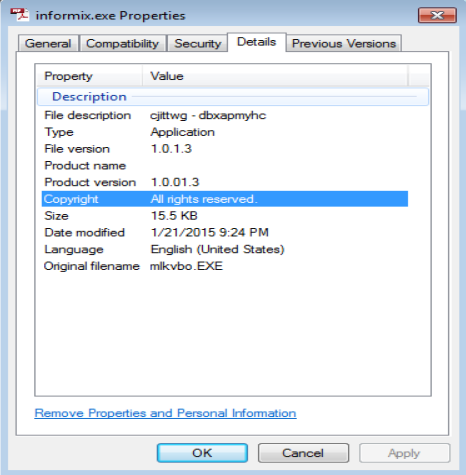
Last time, I had clicked the link and had received the file that was masked as a PDF but was really an executable and ran that. One of the artifacts that was left from that run was a file called informix.exe as you can see below:
Now let’s see what happens when I run this file on my VM and what Security Onion comes back with.
So after clicking on the above EXE, I did see that there was outbound traffic from the VM. And very quickly I saw a file being written the to %TEMP% folder and then deleted (along with the Informix.exe file too). I was not able to make a copy of this file as you can see here:
So with a saved PCAP file from this run in hand, I fired up CapTipper to start the analysis:
mine:~ guido$ captipper Downloads/CapTipper-master/ex2.pcap
CapTipper v0.1 – Malicious HTTP traffic explorer tool
Copyright 2015 Omri Herscovici <omriher@gmail.com>[A] Analyzing PCAP: Downloads/CapTipper-master/ex2.pcap
[+] Traffic Activity Time: Sun, 01/25/15 21:01:56
[+] Conversations Found:<redacted>
4: /2101uk22/VULN-WINDOWS/1/0/0/ -> (4.html) [ B]
5: /mandoc/info22.pdf -> application/pdf (info22.pdf) [431558 B]
6: /2101uk22/VULN-WINDOWS/41/7/4/ -> (6.html) [ B]
7: /2101uk22/VULN-WINDOWS/0/61-SP1/0/ -> (7.html) [ B][+] Started Web Server on http://localhost:80
[+] Listening to requests…CapTipper Interpreter
Type ‘open <conversation id>’ to open address in browser
type ‘hosts’ to view traffic flow
Type ‘help’ for more options
The above command takes the PCAP and starts off by looking at what “conversations” have been established (from what it looks like this is synonymous with the tcp.stream in Wireshark). As we can see, there was not many conversations from this malware sample. This is also further substantiated by typing ‘host’ at the command line:
CT> hosts
Found Hosts:202.153.35.133:44154
├– /2101uk22/VULN-WINDOWS/1/0/0/ [4]
└– /2101uk22/VULN-WINDOWS/0/61-SP1/0/ [7]dipford.com
└– /mandoc/info22.pdf [5]202.153.35.133:44111
└– /2101uk22/VULN-WINDOWS/41/7/4/ [6]
The pages from the IP 202.153.35.133 (conversations 4, 6, and 7) don’t seem to load anything since CapTipper is saying their is no size in bytes associated with them. Doing a simple ‘head 7’ or ‘body 7’ does not yield anything. So opening the PCAP up in Wireshark I see the following associated with conversation 7:
GET /2101uk22/VULN-WINDOWS/0/61-SP1/0/ HTTP/1.1
User-Agent: Mazilla/4.0
Host: 202.153.35.133:44154
Cache-Control: no-cache
Once again, we can see that the name of the VM is being passed to the destination server. Based on some other reading of the Dyre malware that I have done, I am assuming that this is a GET request for a script tailored to the OS the VM is running. Unfortunately nothing was returned. The only connection that seemed to be made was in conversation 5 as you can see below:
CT> info 5
Info of conversation 5:SERVER IP : 209.235.144.9:80
HOST : dipford.com
URI : /mandoc/info22.pdf
REFERER :
RESULT NUM : 200 OK
RESULT TYPE : application/pdf
FILE NAME : info22.pdf
LENGTH : 431558 BCT> head 5
Displaying header of object 5 (info22.pdf):HTTP/1.1 200 OK
Date: Sun, 25 Jan 2015 21:02:55 GMT
Last-Modified: Wed, 21 Jan 2015 07:29:23 GMT
Accept-Ranges: bytes
Content-Length: 431558
Content-Type: application/pdf
Set-Cookie: TS0194eee0=0187bed8eabec43d67d7d84e5e396e8b0176d0ce65ccdf1666265c0a8569af316a9945f507; Path=/
So now let’s pull the PDF out of the PCAP, check VirusTotal for any results the PDF may have, and save that for the final post:
CT> dump 5 Downloads/pcap_pdf.pdf
Object 5 written to Downloads/pcap_pdf.pdfCT> vt 5
VirusTotal result for object 5 (info22.pdf):Detection: 0/56
Last Analysis Date: 2015-01-23 17:05:06
Report Link: http://www.virustotal.com/file/0a7b28753a7d3eafea885551b6495ae55ce75042203f8a1a92631b9b219a8893/analysis/1422032706/
With that said, next time we will take a look at the last part of this, the PDF, and see what happens. Stay tuned.