This is my last post about this particular malicious email that I got in the mail sometime last week. If you have not read the other posts about this email (looks to be in the Dyre malware family), please see part one here and part two here.
To recap, the only thing that I had not taken a look at was the PDF that was sent from the only server that my vulnerable VM connected to as you can see below:
CT> info 5
Info of conversation 5:SERVER IP : 209.235.144.9:80
HOST : dipford.com
URI : /mandoc/info22.pdf
REFERER :
RESULT NUM : 200 OK
RESULT TYPE : application/pdf
FILE NAME : info22.pdf
LENGTH : 431558 BCT> head 5
Displaying header of object 5 (info22.pdf):HTTP/1.1 200 OK
Date: Sun, 25 Jan 2015 21:02:55 GMT
Last-Modified: Wed, 21 Jan 2015 07:29:23 GMT
Accept-Ranges: bytes
Content-Length: 431558
Content-Type: application/pdf
Set-Cookie: TS0194eee0=0187bed8eabec43d67d7d84e5e396e8b0176d0ce65ccdf1666265c0a8569af316a9945f507; Path=/
At this time I had reverted the Windows VM back to an original state just to make sure that nothing else was installed on the system and that I would have a clean slate to run this malware sample from. Below are the details of the “Info22.pdf” file:
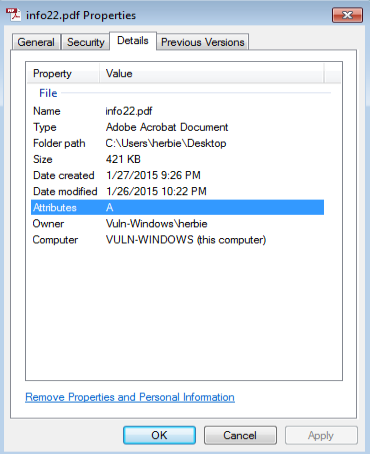
As you can see above, the size of the file (421KB) is a wee bit different than what was actually transferred in the PCAP (431KB). I am not sure why there is a loss here to be honest.
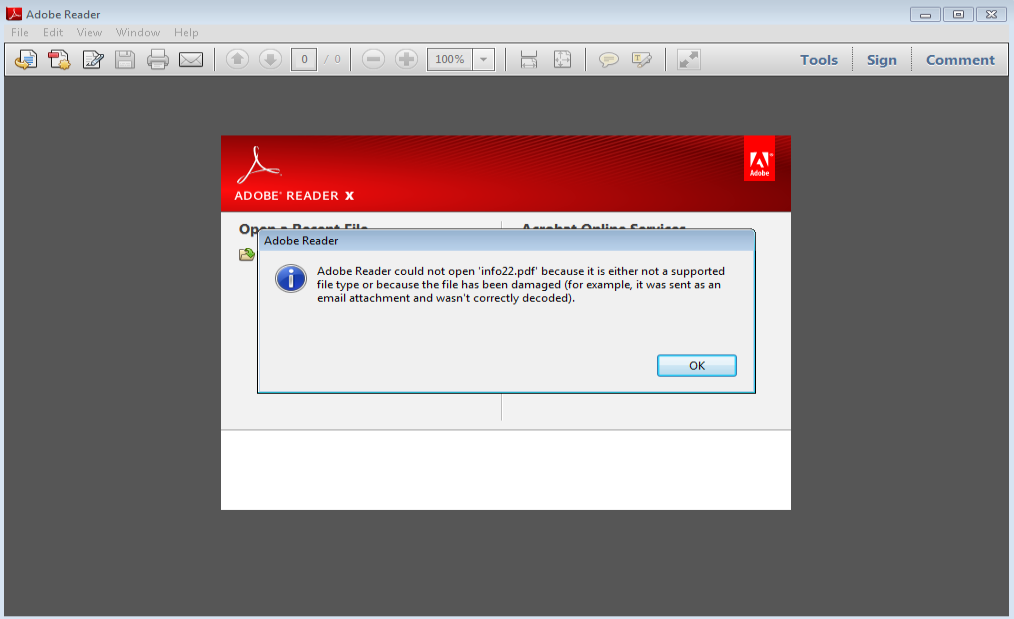
Now the fun part – running this and seeing what traffic comes back. I had a sneaking suspicion that I would not find much in this considering the VirusTotal run from last night came back pretty clean and unfortunately my hunch was correct. Looks like the PDF file is corrupt or something. Maybe that is why the file size is different between the PCAP and the size of the file above. As you can see below, opening this PDF in Acrobat gives me an error message:
I also followed up with Malwr and submitted this to their sandbox. Unfortunately the result was the same in their sandbox as it was in my test VM. For the results of this file in Malwr, check it out here.
Based on some other posts about the Dyre malware, the above should have made some additional callbacks. Once again, I am thinking that since the size of the PDF was different once saved out to disk versus what was reported in the PCAP, this may have affected things. As you can see in the PhishMe post about Dyre, these is definitely more to this than what I have covered here.
So with that said, this concludes my first public blog posting about malware analysis. Let me know what you think or if there are any errors/questions/comments that you may have. Look for other posts as I get more into this side of the house.